In September 2025, the CERT-UA team uncovered a series of targeted cyber attacks against members of the Ukrainian Officers Union, using the CABINETRAT backdoor spread via Excel XLL add-ins shared over Signal to exfiltrate sensitive information and maintain long-term access to compromised systems. Given the novelty of the tactics, techniques, and procedures—aside from previously observed use of XLL files in UAC-0002 (Sandworm, APT44) attacks against Ukrainian critical infrastructure—this activity has been assigned a separate identifier, UAC-0245.
Detect UAC-0245 Activity Using CABINETRAT Backdoor
According to CERT-EU’s 2024 Threat Landscape Report, 44% of reported incidents involved cyber espionage or prepositioning activities typically associated with state-sponsored actors, aimed at data exfiltration and establishing long-term, stealthy access. In 2025, CERT-UA already observed an increase in cyber-espionage activity against Ukraine attributed to UAC-0200, UAC-0219, and UAC-0226. The recent CERT-UA#17479 alert underscores the ongoing operations of UAC-0245, which deploys the CABINETRAT backdoor for targeted cyber espionage.
SOC Prime Platform curates a dedicated collection of detection algorithms to help Ukrainian and allied organizations proactively thwart cyber-espionage attacks by UAC-0245. Click Explore Detections to access relevant Sigma rules enriched with actionable intelligence, aligned with MITRE ATT&CK®, and compatible with multiple SIEM, EDR, and Data Lake solutions.
Security teams can also search SOC Prime’s Detection-as-Code library for relevant content by using the corresponding tags “CERT-UA#17479” and “UAC-0245” to timely spot adversary activity.
Security engineers also use Uncoder AI acting as an AI co-pilot, supporting detection engineers end-to-end while streamlining workflows and enhancing coverage. With Uncoder, defenders can instantly convert IOCs into custom hunting queries, craft detection code from raw threat reports, generate Attack Flow diagrams, enable ATT&CK tags prediction, leverage AI-driven query optimization, and translate detection content across multiple platforms. For instance, below is the Attack Flow diagram based on the latest CERT-UA alert on UAC-0245.
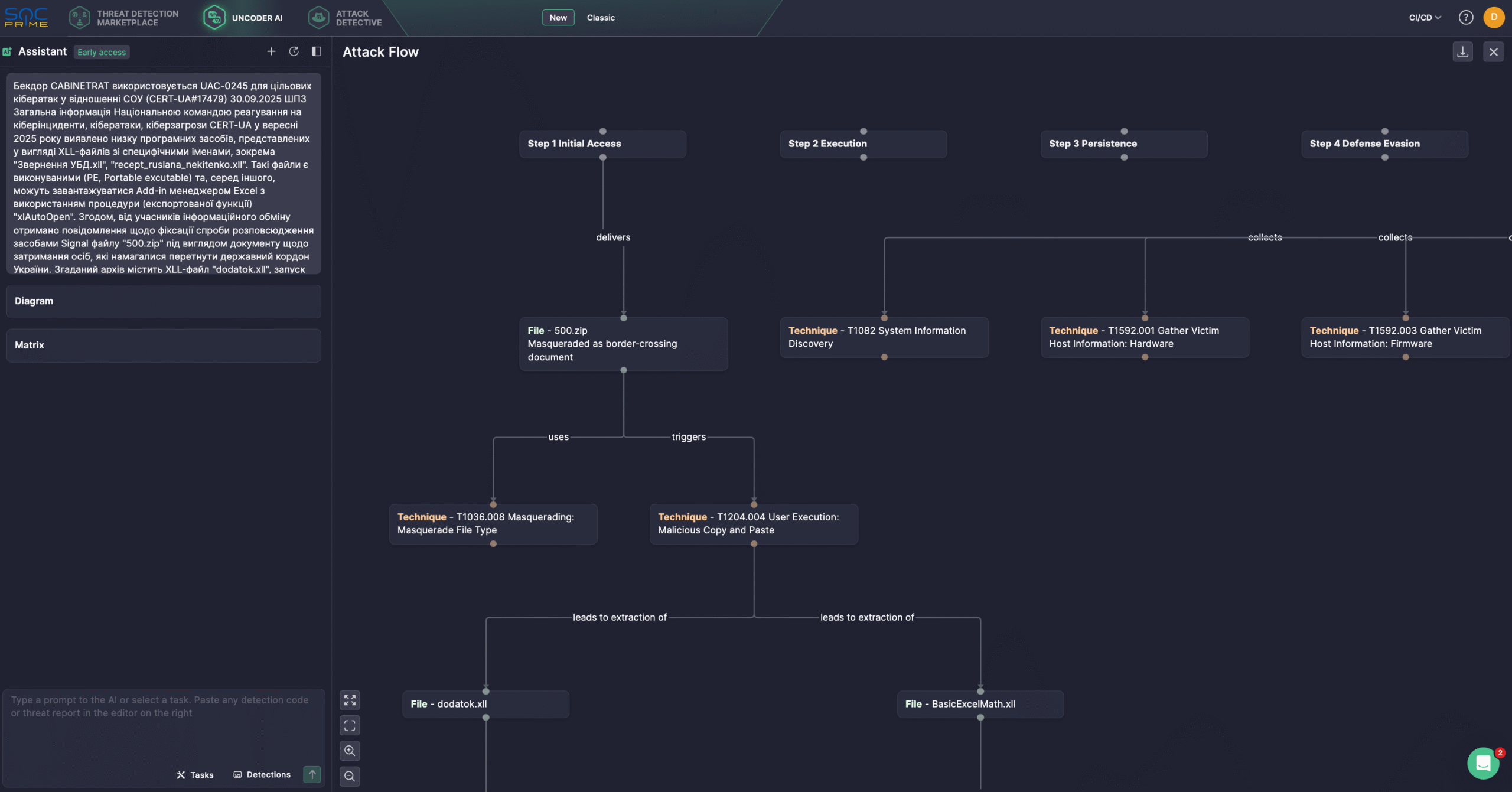
UAC-0245 Activity Analysis
In September 2025, CERT‑UA identified a targeted campaign against members of the Ukrainian Officers Union that used malicious Excel XLL add‑ins to deliver the CABINETRAT backdoor. Early samples carried deceptive names (for example, recept_ruslana_nekitenko.xll), and some of them were discovered to be bundled in a Signal‑shared archive called 500.zip disguised as a detention notice for individuals who had attempted to cross the Ukrainian border.
That archive contained dodatok.xll, which, when run, drops multiple components on the targeted machine, including a randomly named EXE placed into the Startup folder, an XLL loader called BasicExcelMath.xll copied into %APPDATA%\Microsoft\Excel\XLSTART\, and an image file Office.png that hides shellcode.
To maintain persistence of the EXE file, Windows Registry modifications are made. Also, the dropper checks HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\EXCEL.EXE while removing entries from HKCU\Software\Microsoft\Office\{14,15,16}.0\Excel\Resiliency\DisabledItems to prevent the add‑in from being disabled. The dropped EXE launches EXCEL.EXE in hidden mode using the /e (embed), and automatically loads the previously installed BasicExcelMath.xll. The XLL reads the bundled Office.png, extracts embedded shellcode, and transfers execution to it (using VirtualProtect + CreateThread). This shellcode has been classified as the CABINETRAT backdoor.
CABINETRAT, C-based backdoor delivered as shellcode, provides broad espionage functionality. It enumerates system and installed‑software information, runs commands and returns results, lists directories and reads or exfiltrates files, captures screenshots, deletes files or folders, and can fetch files from a remote server.
The observed UAC-0245 activity indicates the evolving and persistent nature of this cyber threat. These developments highlight the critical need for robust cybersecurity measures, as the group’s ability to remain undetected poses a persistent threat to targeted organizations. Rely on SOC Prime’s complete product suite backed by AI, automated capabilities, and real-time threat intel to proactively defend against emerging threats of any scale and sophistication.
MITRE ATT&CK Context
Using the MITRE ATT&CK offers detailed insight into the latest UAC-0245 operations leveraging the CABINETRAT backdoor. The table below outlines all relevant Sigma rules mapped to the associated ATT&CK tactics, techniques, and sub-techniques. Tactics Techniques Sigma Rule Initial Access Phishing: Spearphishing Attachment (T1566.001) Execution Scheduled Task/Job: Scheduled Task (T1053.005) User Execution: Malicious File (T1204.002) Persistence Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001) Office Application Startup (T1137) Office Application Startup: Add-ins (T1137.006)

