On July 28, 2021, SOC Prime released the latest Threat Detection Marketplace version 4.15.0 introducing new features and improvements for a more insightful platform experience. This update brings in a number of content quality enhancements to Azure Sentinel, Chronicle Security, Splunk, the Elastic Stack, and SentinelOne, adds to a more streamlined search experience on the Detections view mode, as well as introduces major localization updates for a more intuitive experience with the platform capabilities. Also, we are happy to announce the beta release of a brand-new Uncoder CTI functionality enabling fast and easy generation of IOC queries.
Content Quality Enhancements
At SOC Prime, we’re constantly looking for ways to enhance the content quality when translating behavior-based detections written in the generic Sigma language to various language formats tailored to the organization’s SIEM & XDR stack.
Azure Sentinel Improvements
For a seamless threat detection experience of our Microsoft customers, we’ve made the following translation enhancements to the Azure Sentinel Rules:
- Improved the logic for single and double quotes to make sure they are used correctly for different cases
- Fixed the issues with missing dots in regular expressions
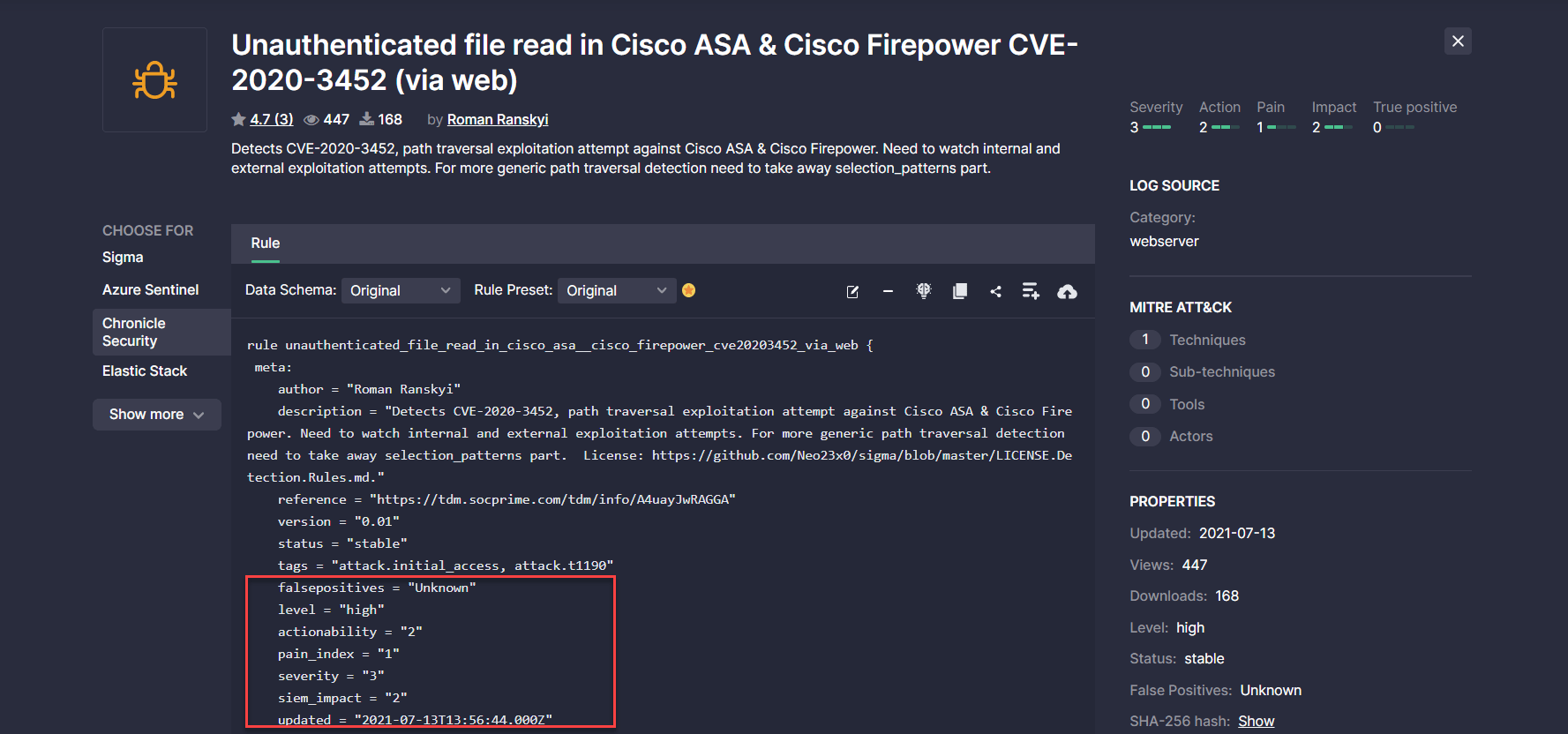
Chronicle Security Translation Improvements
With this latest release v.4.15.0, we’ve enriched the list of fields displayed as metadate for Chronicle Security translations. Now Sigma rule metrics can also be converted to the YARA-L format and are displayed in the meta block unless they are empty:
- metadata.actionability
- metadata.pain_index
- metadata.severity
- metadata.siem_impact
- metadata.true_positive_rate
- updated
Hash Fields Based on Letter Number for Azure Sentinel and Elastic
To deliver the most intuitive threat detection experience to our customers, we’ve added the ability to indicate the hash type based on the letter length for more accurate mapping of the Hashes field in the original Sigma rule. The following hash types are available that will be used to translate Sigma rules with the Hashes field to Azure Sentinel and Elastic Stack language formats:
1. For Azure Sentinel
- FileHashMd5
- FileHashSha1
- FileHashSha256
- FileHashSha512
2. For Elastic Stack
- file.hash.md5
- file.hash.sha1
- file.hash.sha256
- file.hash.sha512
- File.hash.ssdeep
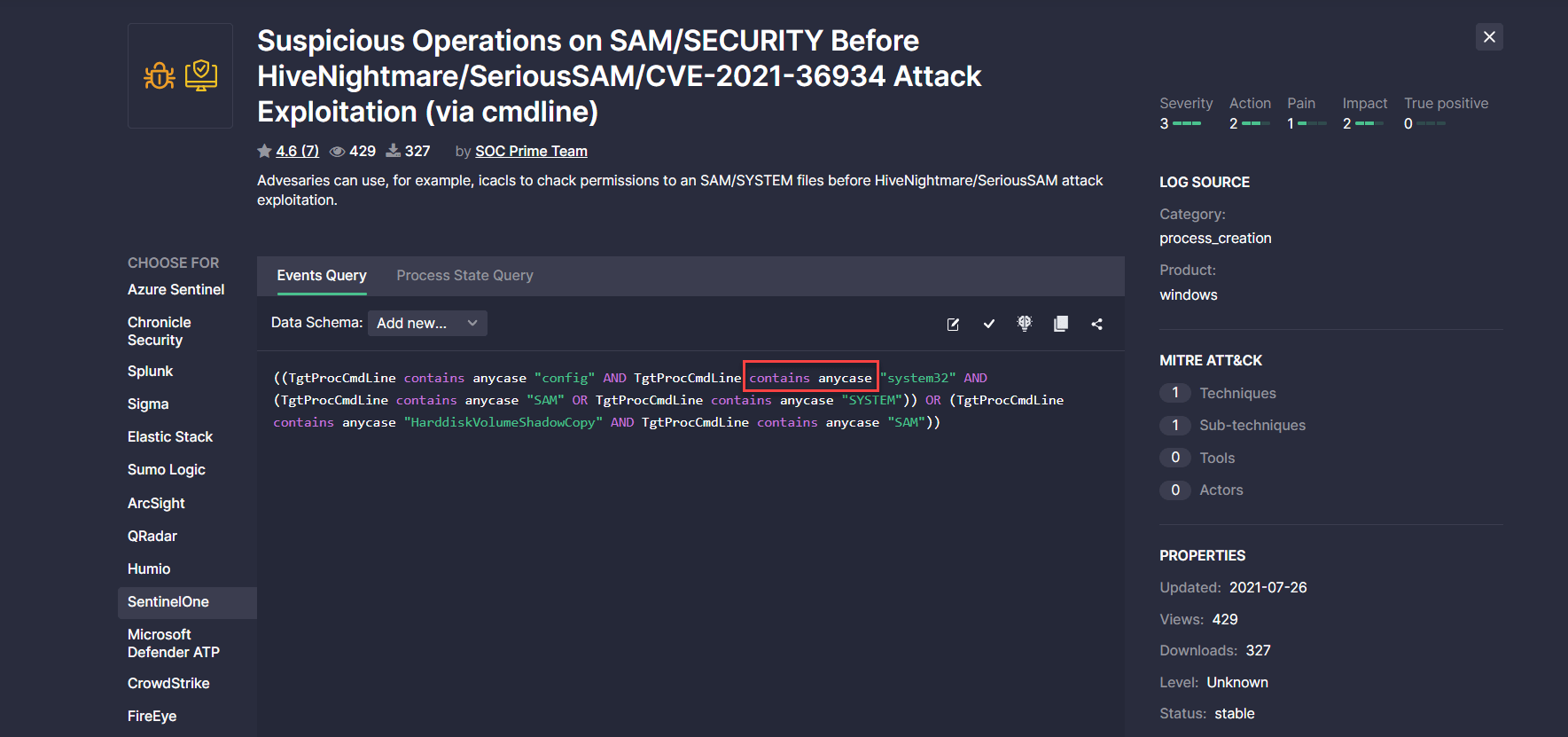
SentinelOne Translation Improvements
With this latest platform update, we’ve made the following enhancements to the SentinelOne translations:
- Regenerated all translations to prevent syntax errors
- Updated mapping
- Added the ability to define the hash type
- Replaced the contains operator with contains anycase due to the platform case-sensitive syntax peculiarities
Splunk Translation Improvements
This latest release v.4.15.0 introduces a couple of translation improvements to the Splunk language format, more specifically:
- The newly added ability to insert a log source (index) for each Splunk Query. This value is defined in the configuration file and depends on the specific log source
- Resolved the translation issue with the use of a $ character in the selection block that is now replaced by $$
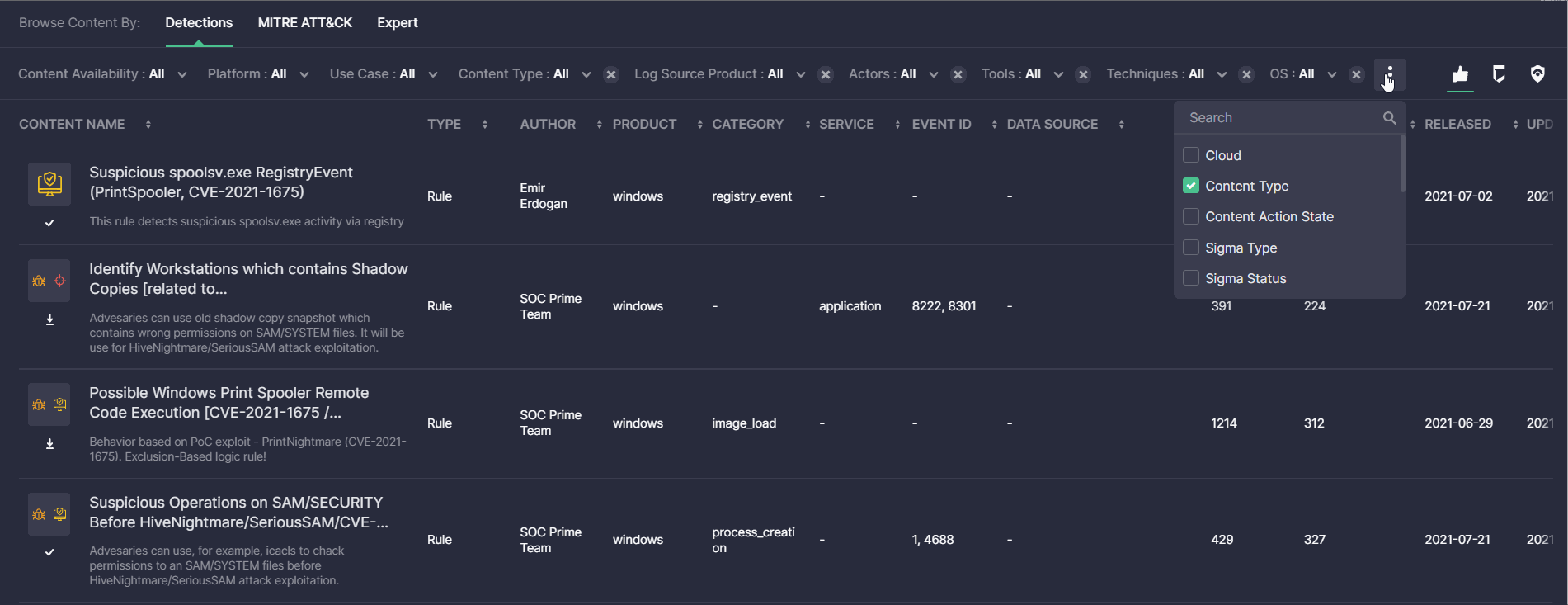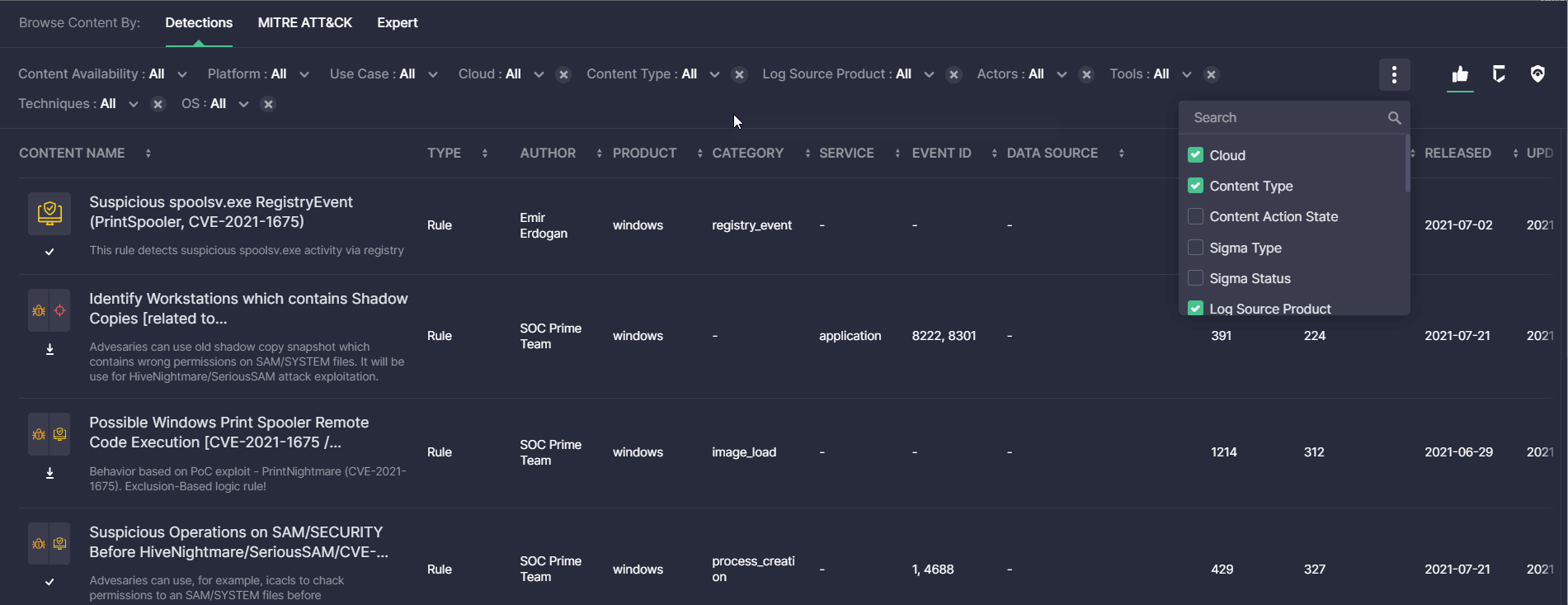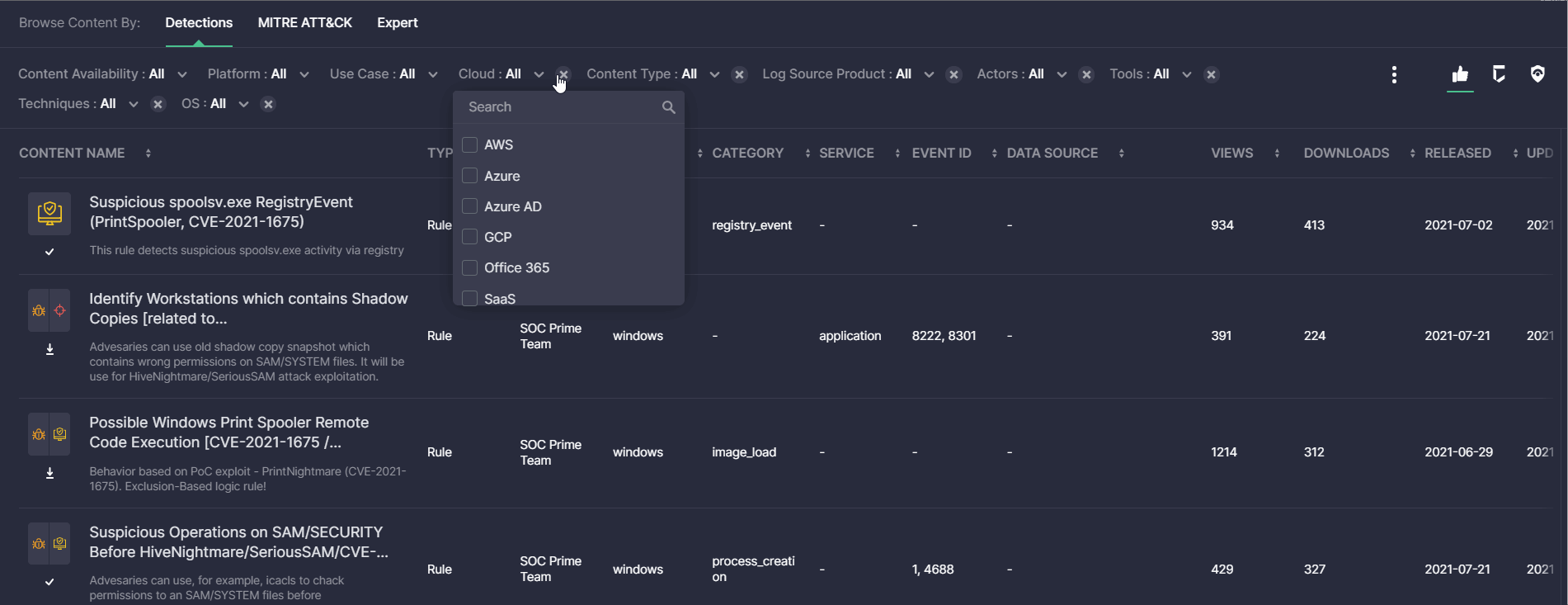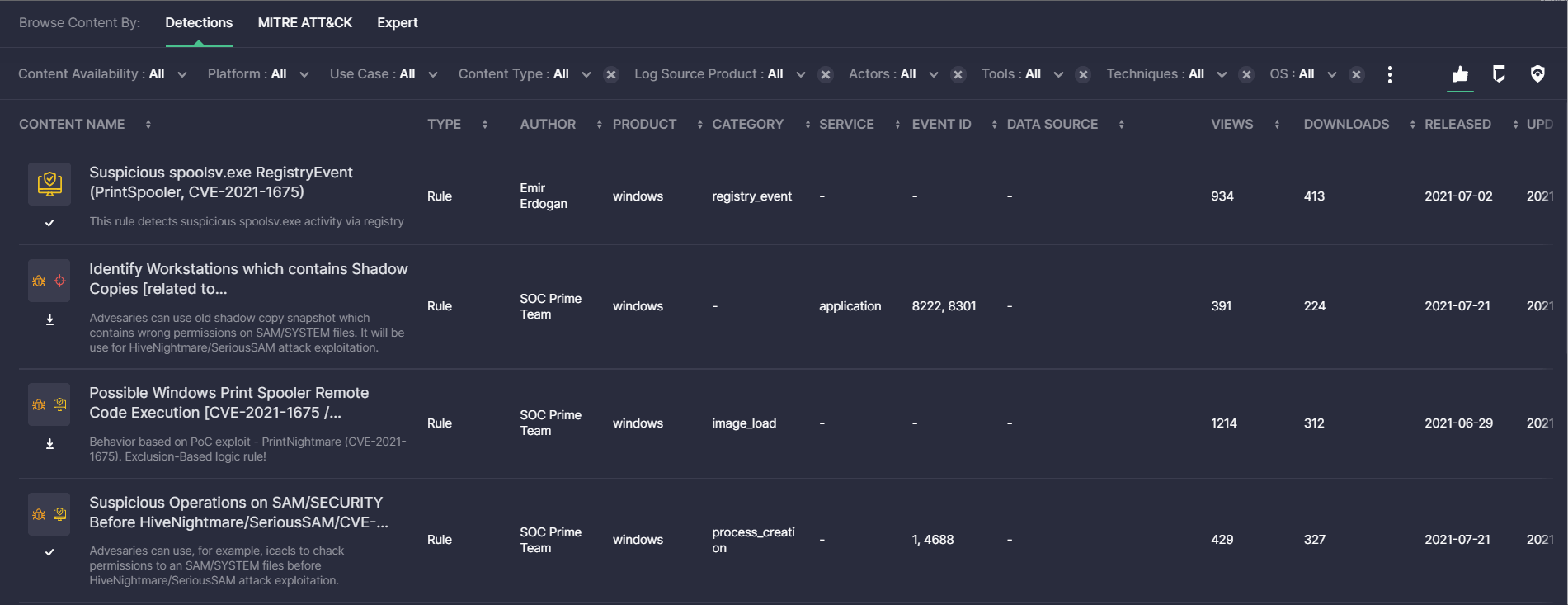
Detections View Mode: User-Facing Improvements
For a more streamlined search experience with the Content page, this latest platform update brings in the ability to remove applied filters in the Detections view mode with a just single click. Detection Engineers can now seamlessly click the X button next to the applied filter to remove it on the fly and update the content search results accordingly.
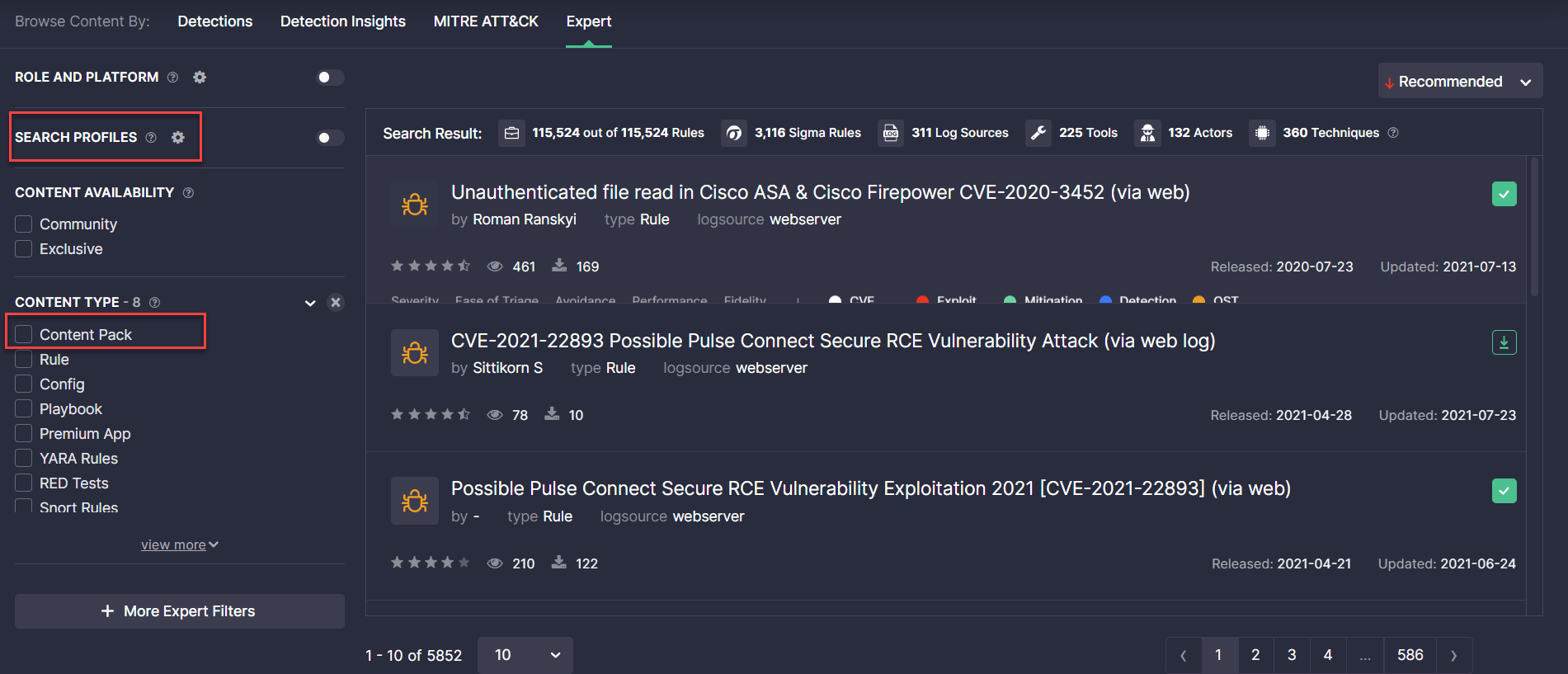
Localization Updates
This latest Threat Detection Marketplace release introduces a number of major localization updates applied across the entire platform functionality to deliver the most intuitive and consistent experience to our clients. These localization updates are as follows:
- Rule Master → Search Profiles
- Rule Packs → Content Pack
- API Profile → Environment
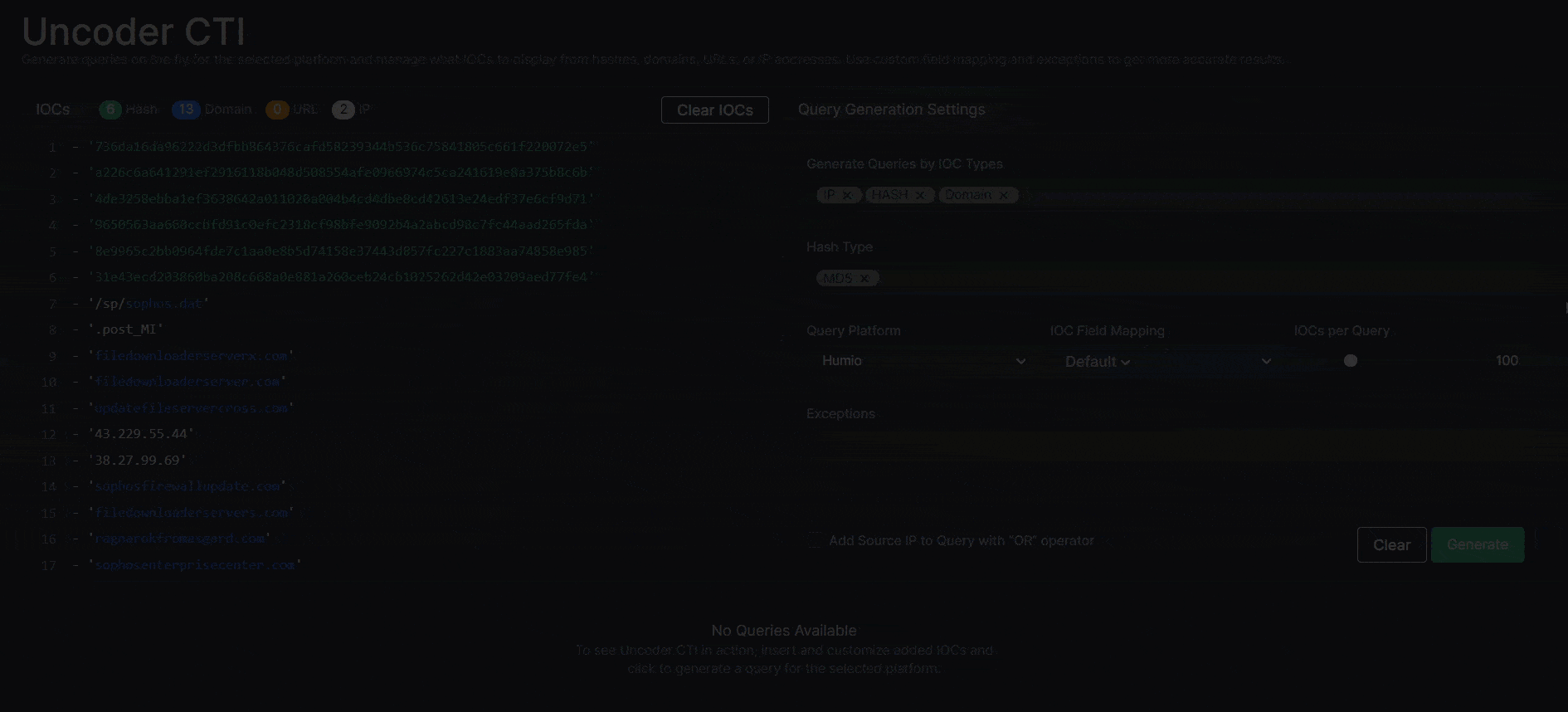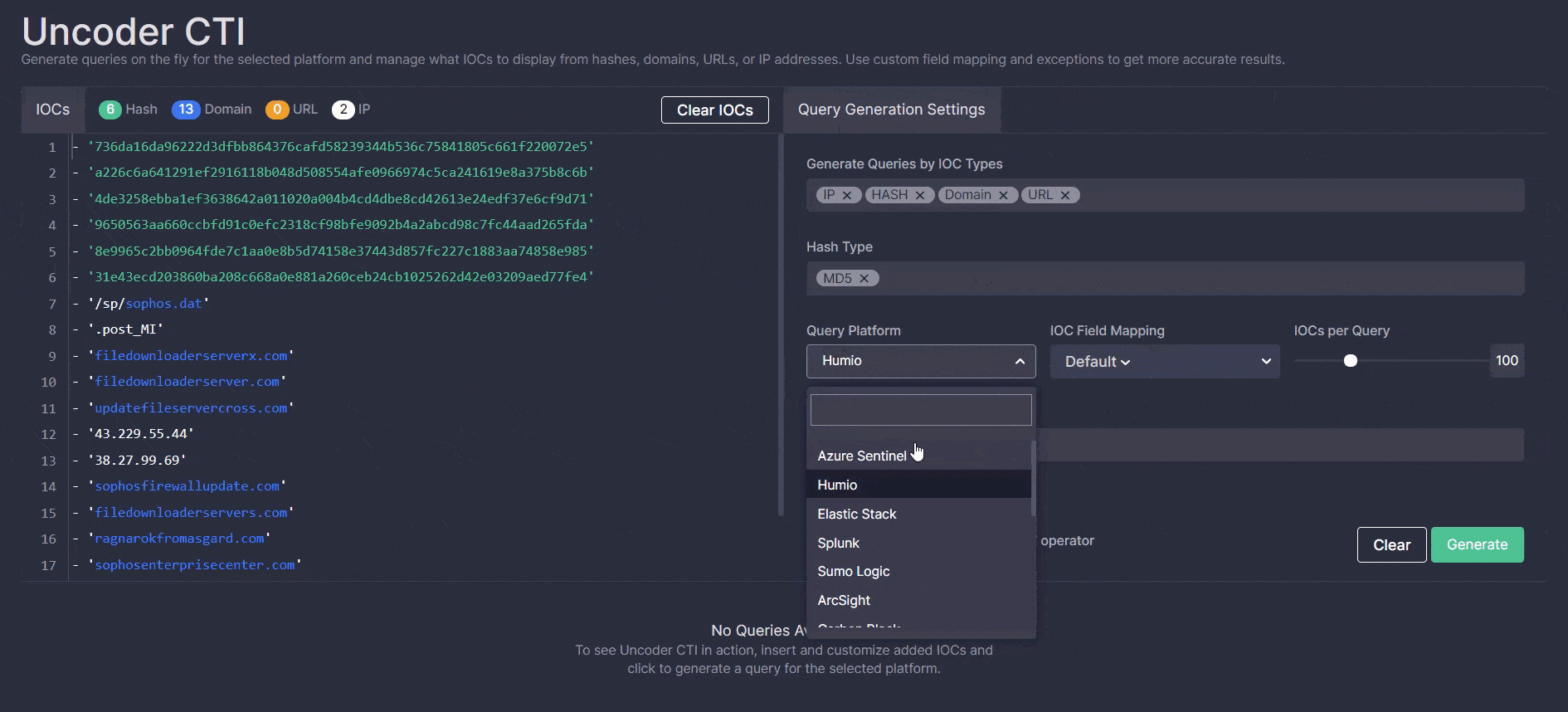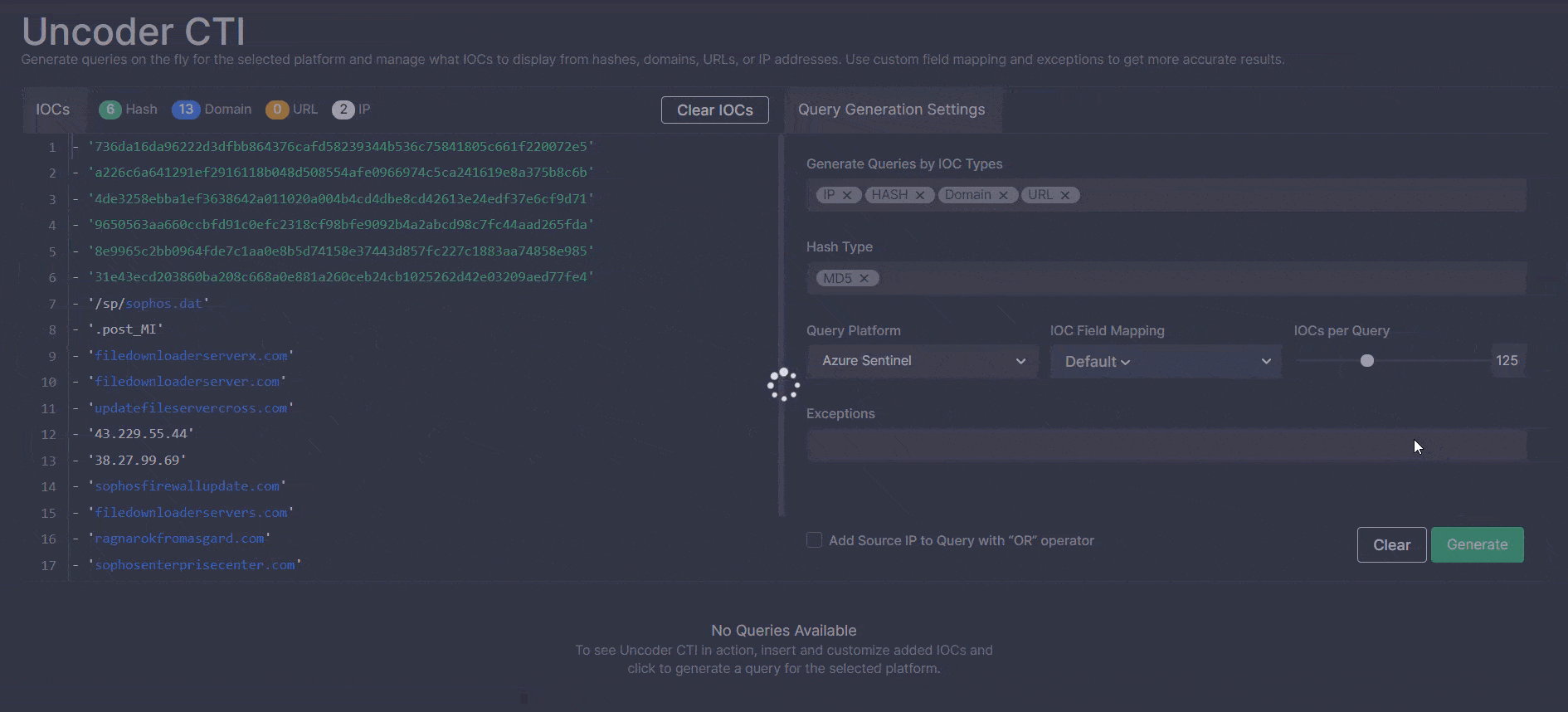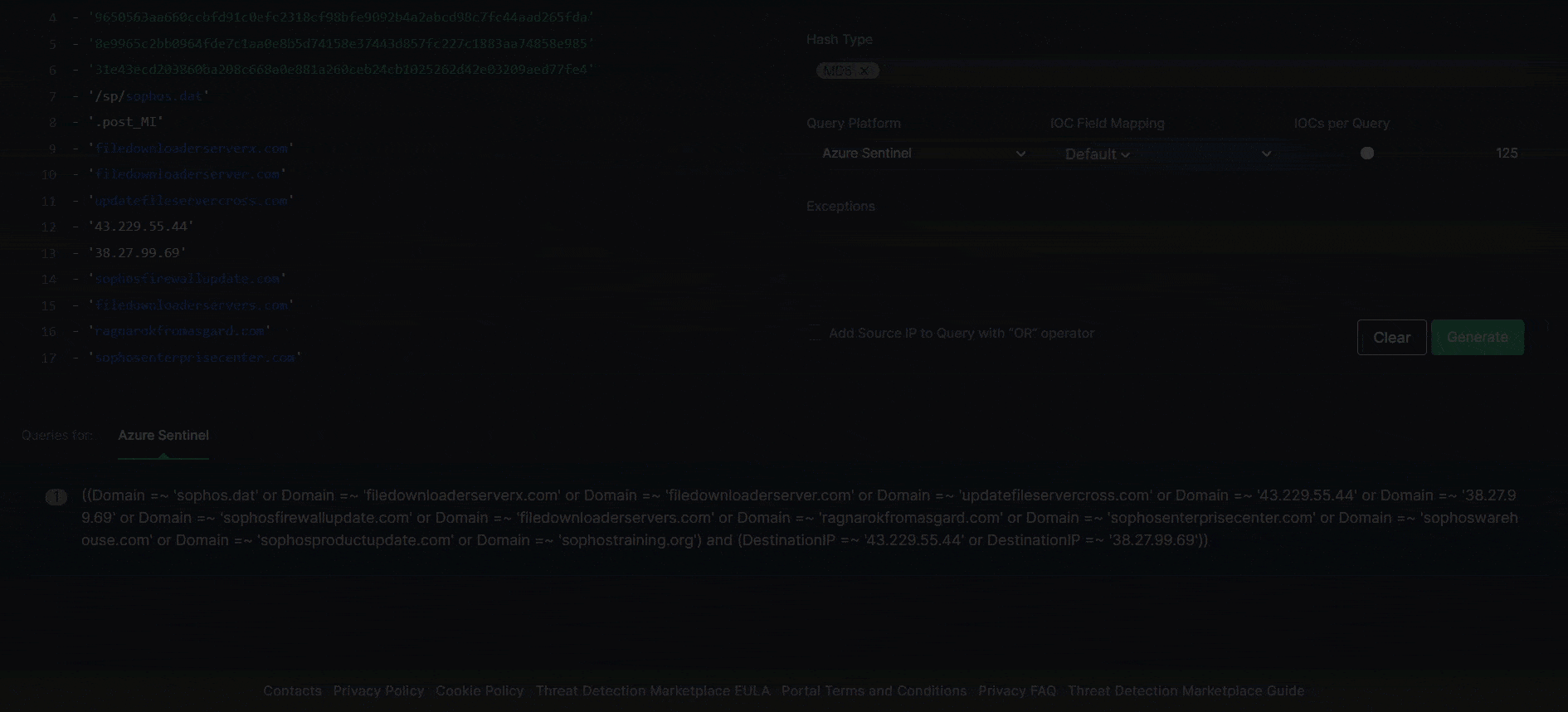
Uncoder CTI Beta Release
With this most recent Threat Detection Marketplace update, we’ve launched a unique Uncoder CTI beta version, which allows generating IOC queries on the fly and seamlessly drilling down to hunt for threats in the customer’s environment. Leveraging Uncoder CTI, Threat Hunters can save hundreds of hours by generating custom IOCs in a matter of seconds based on the uploaded reports and other files that contain IOC data, which normally takes a great deal of time and manual efforts.
To take advantage of the Uncoder CTI functionality, security performers simply need to upload the files with IOCs in the CSV, JSON, or TXT format, or insert the file content right into the left panel of the tool interface.
Before generating a query, it can be customized for maximum performance and infrastructure requirements by specifying the following:
- Certain IOC types, such as hash, domain, URL, or IP, as well as hash types
- The platform to which a query is tailored
- IOC field mapping settings
- Number of IOCs per query
- Exceptions
After clicking the Generate button, the successfully generated custom IOC query is ready for hunting in the selected environment.
The final Uncoder CTI release is coming soon.
Key Bug Fixes & Improvements
With this latest release v.4.15.0, we’ve made the following key bug fixes and improvements to Threat Detection Marketplace:
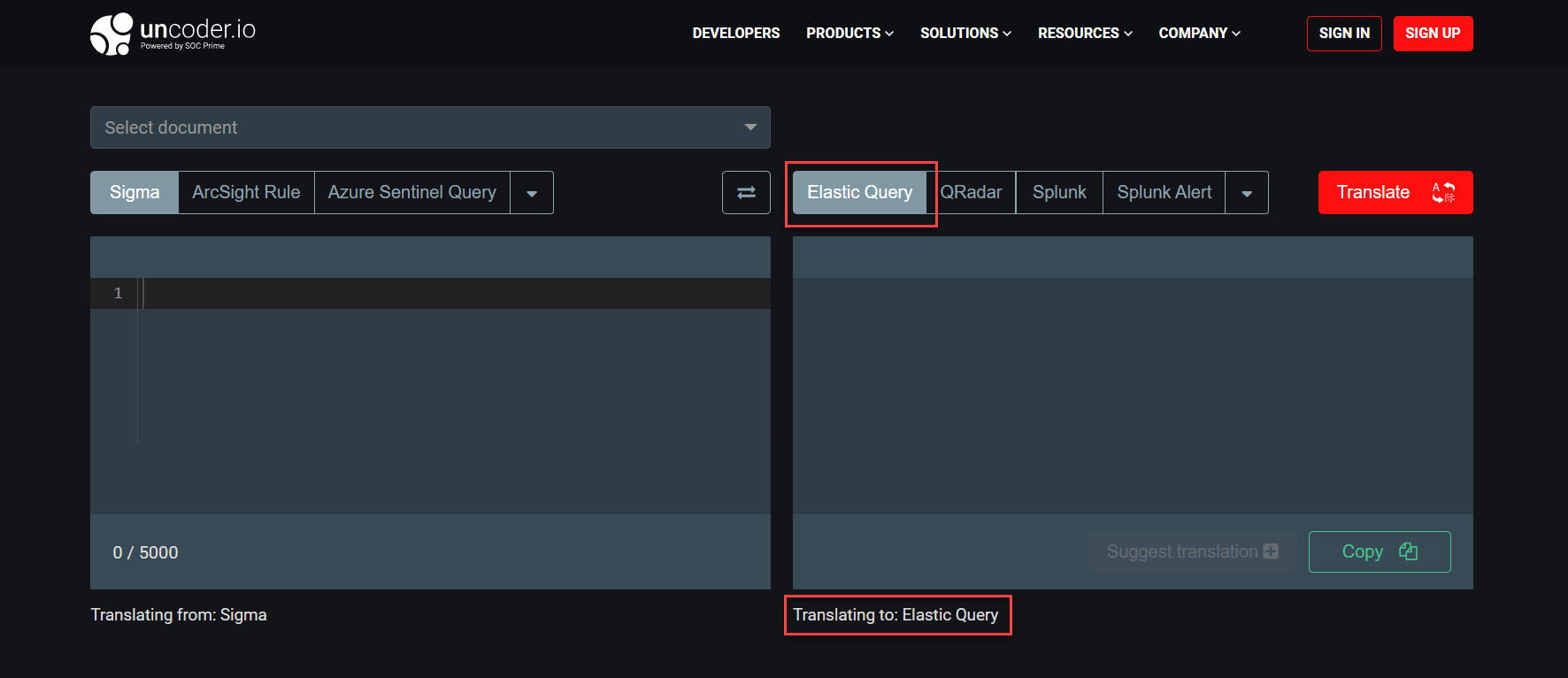
- Fixed the issue with the wrong platform value displayed in the default settings of the Uncoder.IO tool. When opening the Uncoder.IO page, “Translating to: Sigma” was indicated instead of “Elastic Query” on the translation tab. After making improvements, “Elastic Query” is properly indicated below the window with the source code matching the default platform tab.
- Fixed the issue with sorting on the Content page when switching from the Expert to the Detections view mode. Before the update, when applying sorting by Type in the Expert view mode and then moving to the Detections view mode, content was already arranged according to the applied sorting option. After making improvements, both view modes work as independent instances with their own sorting functionality.
- To make ATT&CK Sub-techniques stand out from the related Techniques, we’ve improved their alignment in the left hand-side filtering panel of the Expert view mode.
Looking for ways to boost your cyber defense capabilities with custom SOC content tailored to the SIEM & XDR stack in use? Get started with SOC Prime Threat Detection Marketplace to reach cross-tool detection and response content matching the organization’s threat profile. The content base of over 100,000 detections is constantly thriving backed by our dedicated community of 300+ security performers and researchers who contribute to the platform growth on a global scale. Want to be among our content contributors? Join the industry-first Threat Bounty Program!