Threat Detection Marketplace Version 4.14.0 Is Released
On July 14, 2021, SOC Prime released Threat Detection Marketplace version 4.14.0 to enhance the platform capabilities and deliver an even more streamlined experience to our customers. With this latest update, we introduce the ability to deploy Azure Sentinel Workbooks and Sumo Logic CSE Rules, add more content quality enhancements to Azure Sentinel, Chronicle Security, and QRadar, implement the international date and time format across the entire platform functionality, and improve user experience with integrations for Chronicle Security, Sumo Logic, and Humio.
Enhanced Content Deployment Capabilities
At SOC Prime, we’re constantly enriching the platform SIEM & XDR stack, as well as the range of supported content types for various language formats. With this release, we’ve added the ability to deploy Azure Sentinel Workbooks and Sumo Logic CSE Rules powered by the platform Integration Service.
Azure Sentinel Workbooks
Security performers can now deploy Azure Sentinel Workbooks using the Deploy to Azure Sentinel button right from the Rule Pack page. The Continuous Content Management (CCM) support for on-the-fly streaming of Azure Sentinel Workbooks directly to the customer’s SIEM instance is coming soon to make content deployment even more streamlined and scalable.
Sumo Logic CSE Rules
With this release, Sumo Logic CSE Rules can also be seamlessly deployed to the customer’s environment. Once Sumo Logic CSE integration is properly set, security performers just need to click the Deploy to Sumo Logic CSE button from the action menu on the CSE Rule tab. If the content matches all syntax requirements, it will be deployed on the fly to the customer’s Sumo Logic CSE instance.
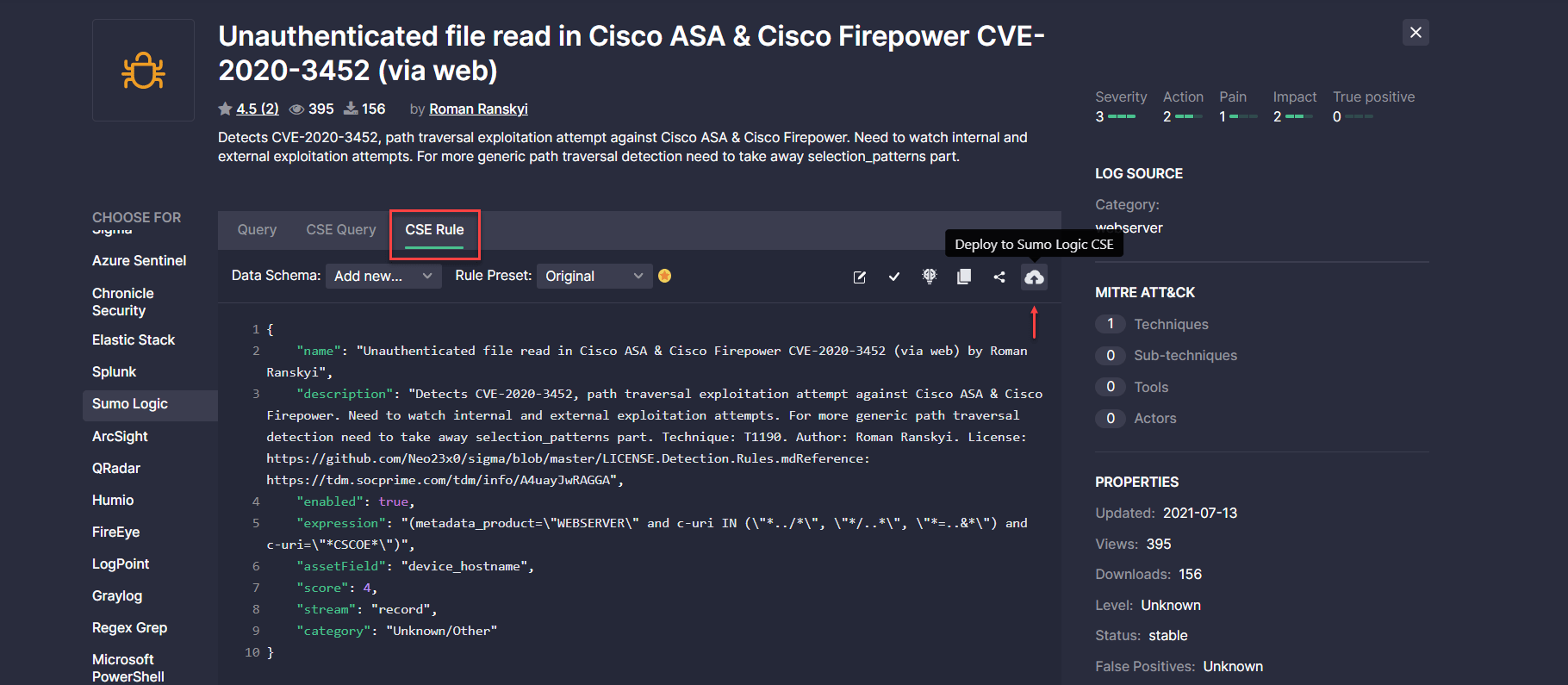
Content Quality Enhancements
With each platform release, we’re striving to improve the content quality when translating Sigma behavior-based detections to 20+ SIEM, EDR, and NTDR solutions. With this release, we’ve improved the translation quality for our Azure Sentinel customers, as well as made field mapping improvements to the Chronicle Security and QRadar language formats.
Azure Sentinel Translation Improvements
This latest release brings in an important improvement to the Sigma rule translations to the Azure Sentinel language format. Before the update, Sigma behavior-based detections that contained the code with the and not operator in the condition block, such as condition: selection and not filter, were converted based on the and operator, which caused translation issues. Now the corresponding Azure Sentinel translations containing the and not operator are properly generated using a special symbol.
Field Mapping Updates
With this Threat Detection Marketplace release, we’ve updated field mapping for the following security solutions to improve translation generation:
- For Chronicle Security, replaced the custom protocol field with network.ip_protocol
- For Qradar, added the Commandline: Process CommandLine custom field
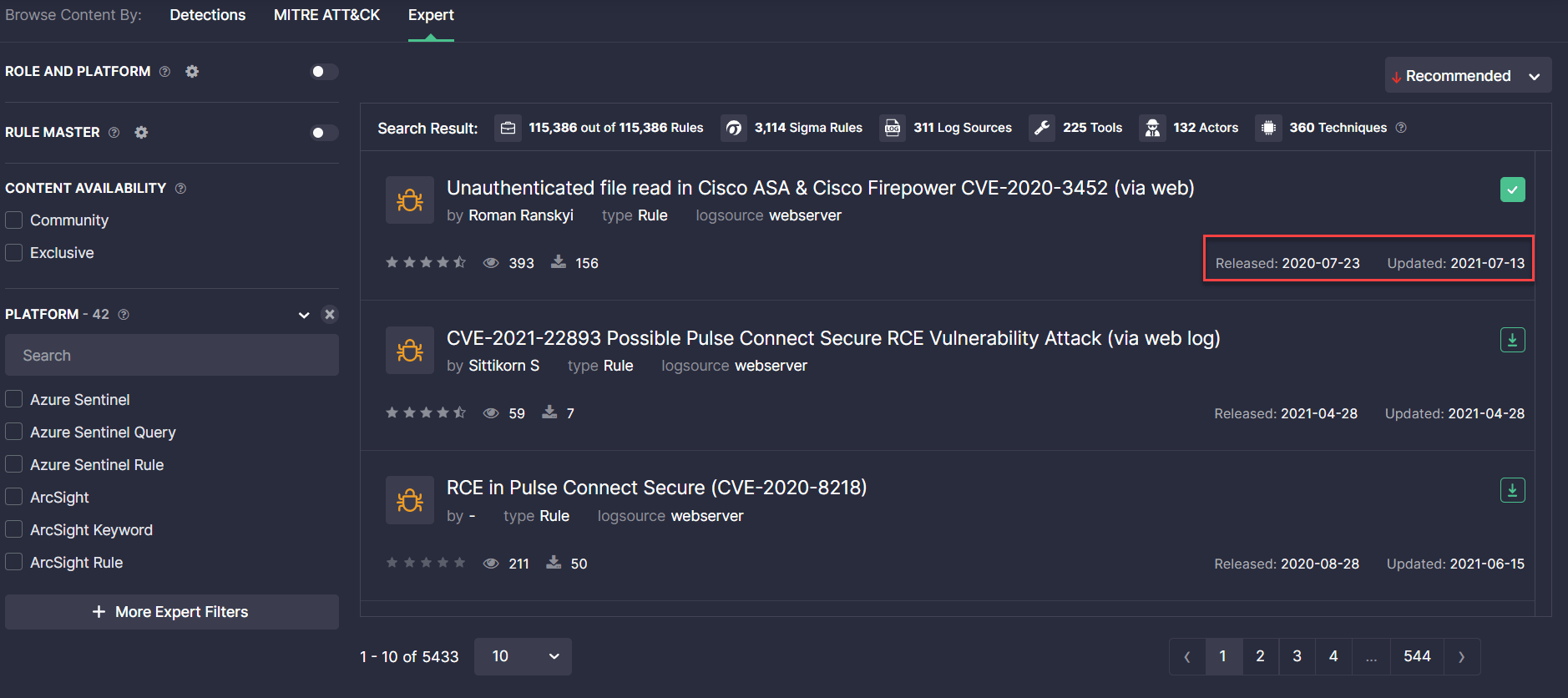
International Standard for Date and Time Formats
With this latest release, we’ve applied the international ISO 8601 standard for date and time formats across the entire functionality in Threat Detection Marketplace. The date is now displayed in the YYYY-MM-DD format when providing the content item details, like information on the rule release and update, within content reviews, and other platform functionality that includes a timestamp.
Integration Configuration Improvements
We’re constantly looking for ways to make the user experience with the integration settings even more intuitive and streamlined. With this latest platform release, we’ve introduced a couple of improvements to the Chronicle Security integration settings, as well as added how-to integration guides for Sumo Logic and Humio to make the setup process fast and simple.
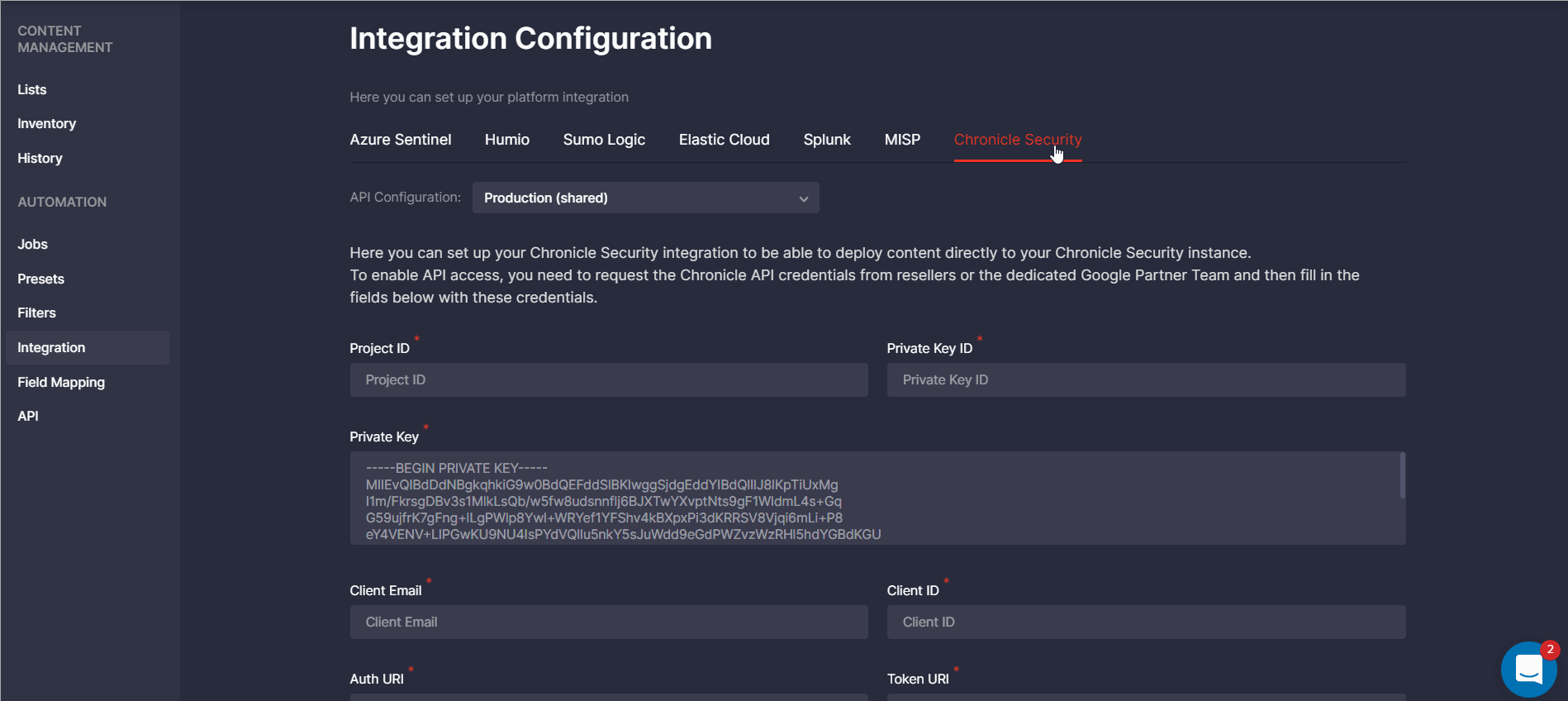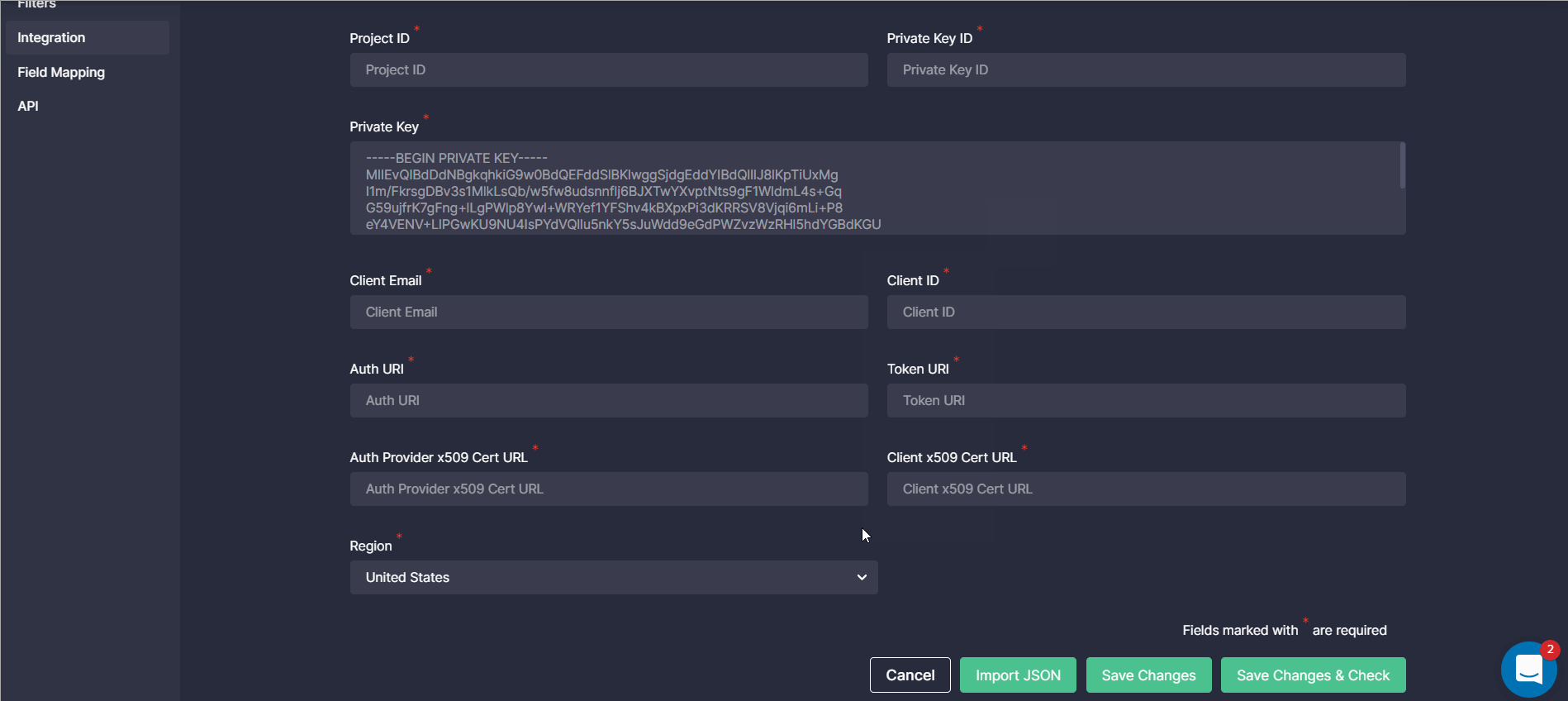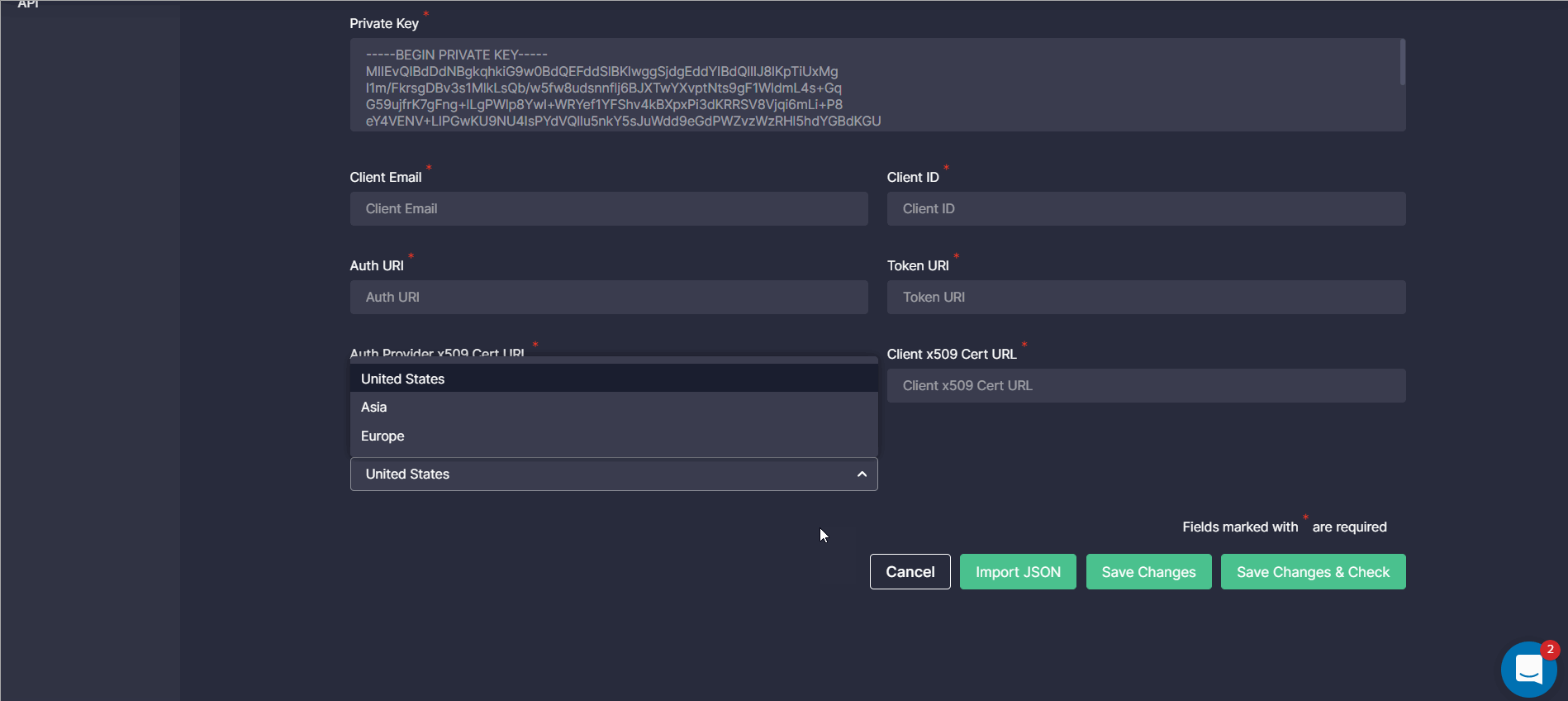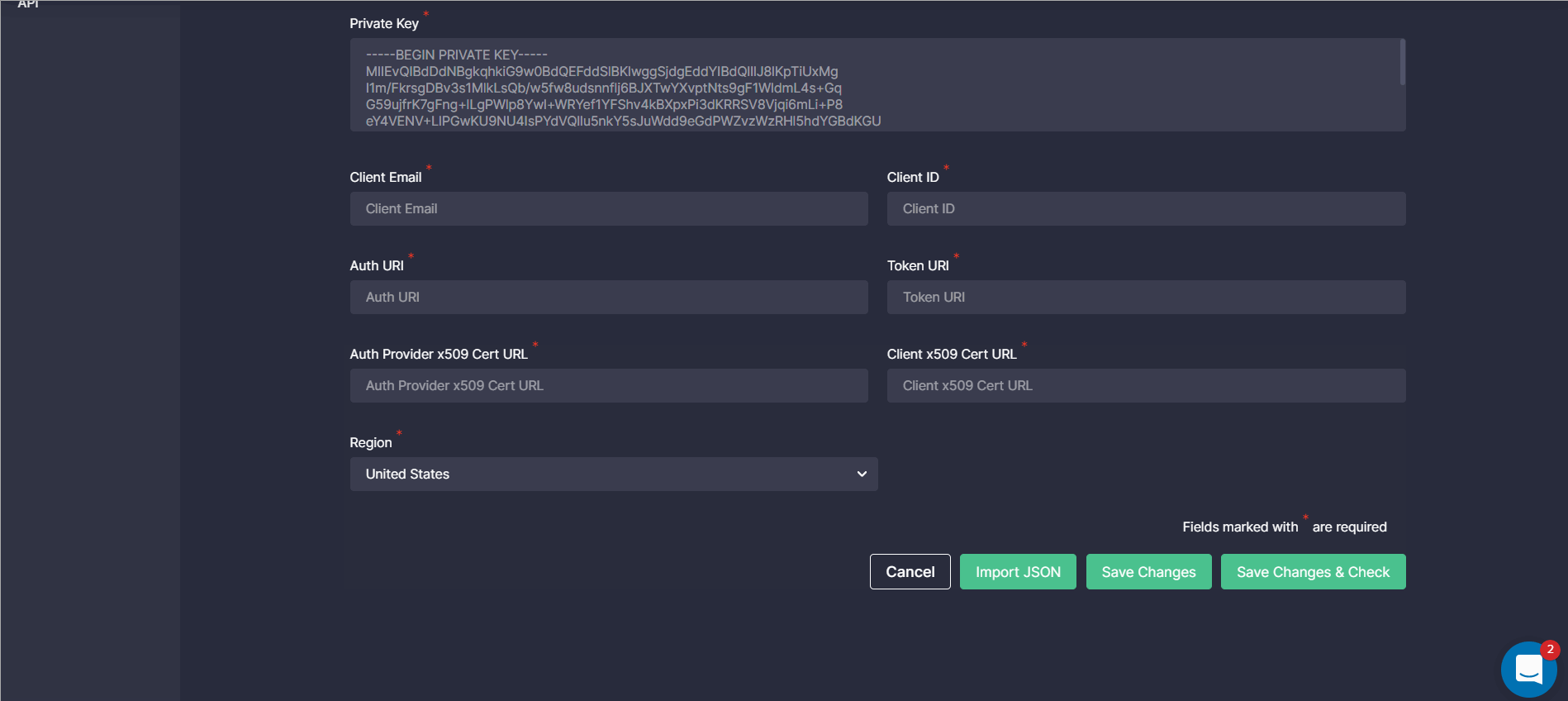
Chronicle Security Integration Updates
To ensure the most intuitive experience for Google customers leveraging Threat Detection Marketplace, we’ve recently made the following improvements to the Integration Configuration page for Chronicle Security:
- Added the Region field
- Added the ability to import and parse the JSON file with API credentials
Region Field for API Configuration
To seamlessly stream content directly into the customer’s Chronicle Security environment, we’ve recently added the Region field to the platform settings, which is required for proper API configuration. The default field value is United States, but it can be changed to other available options when needed:
- Asia
- Europe
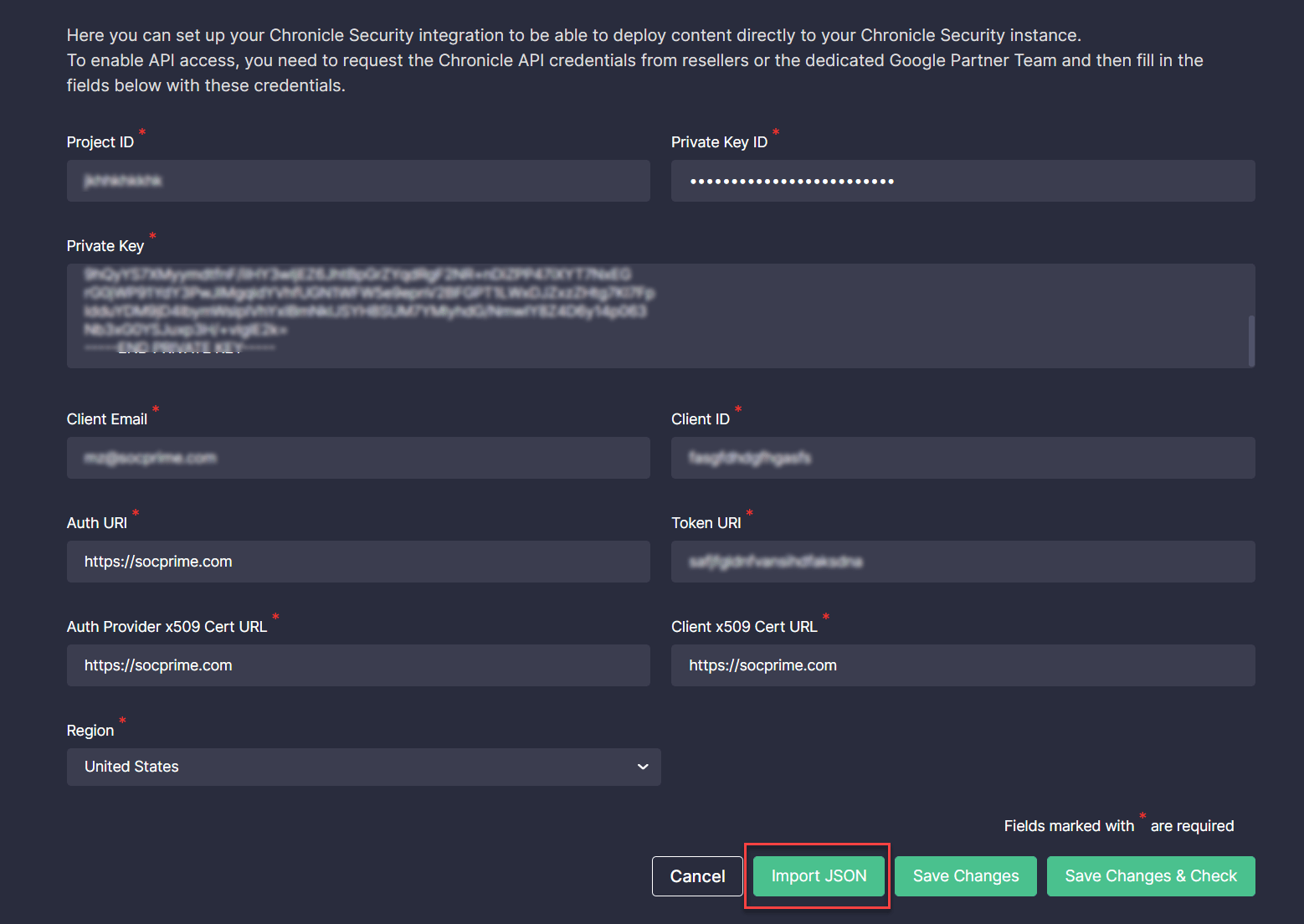
Importing and Parsing API Credentials in the JSON Format
With this latest platform update, we’ve added the ability to import the Chronicle API credentials received from resellers or the dedicated Google Partner Team from the corresponding JSON file. This JSON file import has certain restrictions to make sure Chronicle Security customers add only valid files, including:
- The file format restrictions
- Size restrictions
- Requirements for the fields this file should contain — only specific fields can be imported, while the system ignores any additional fields within the file
The JSON file with API credentials is being parsed on the fly, which adds to a more streamlined integration configuration process. To save the settings after parsing the received JSON file with the Chronicle API credentials, Threat Detection Marketplace users need to click the Save Changes button, and they are all set for streaming the latest Chronicle Security content.
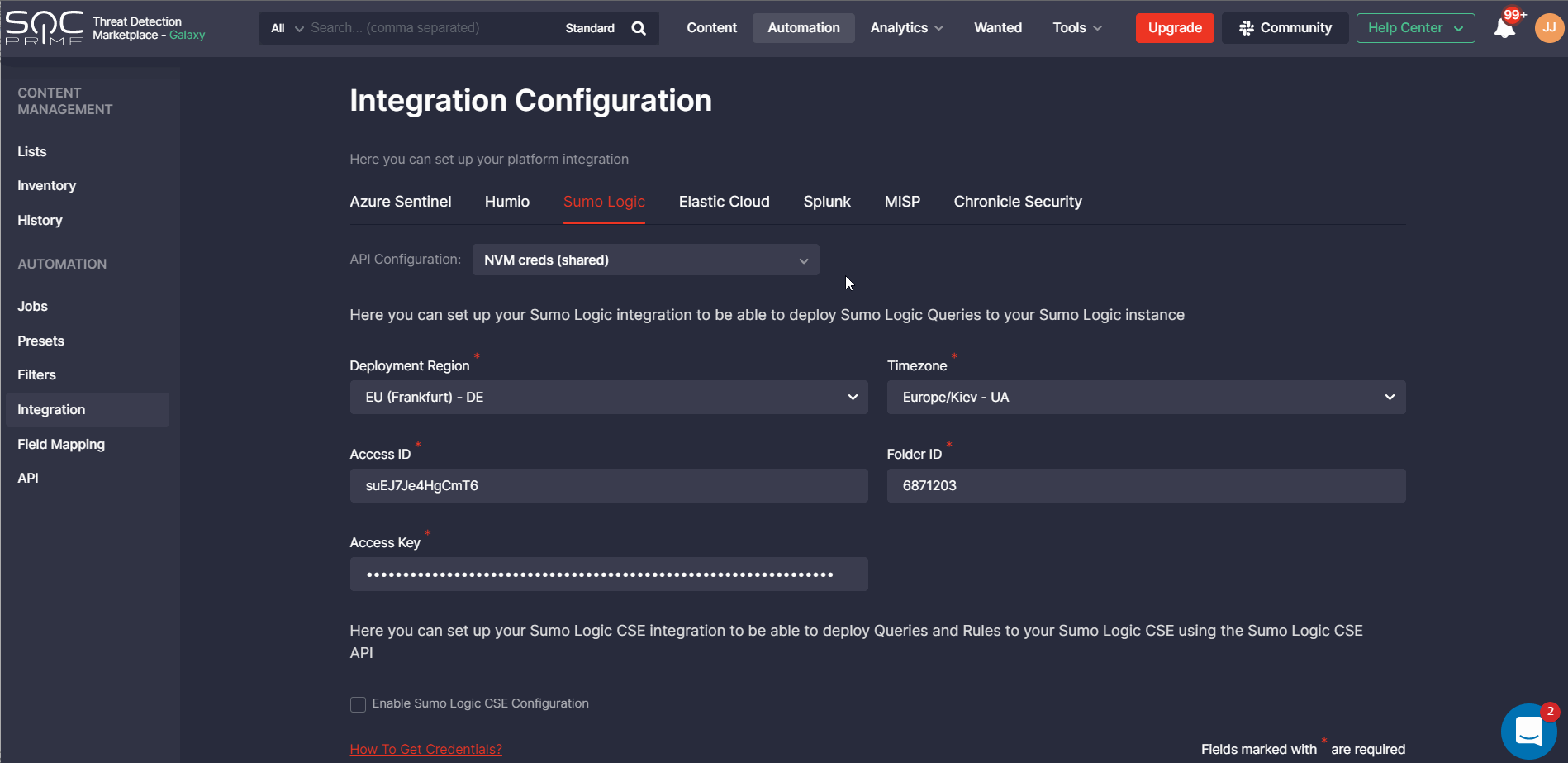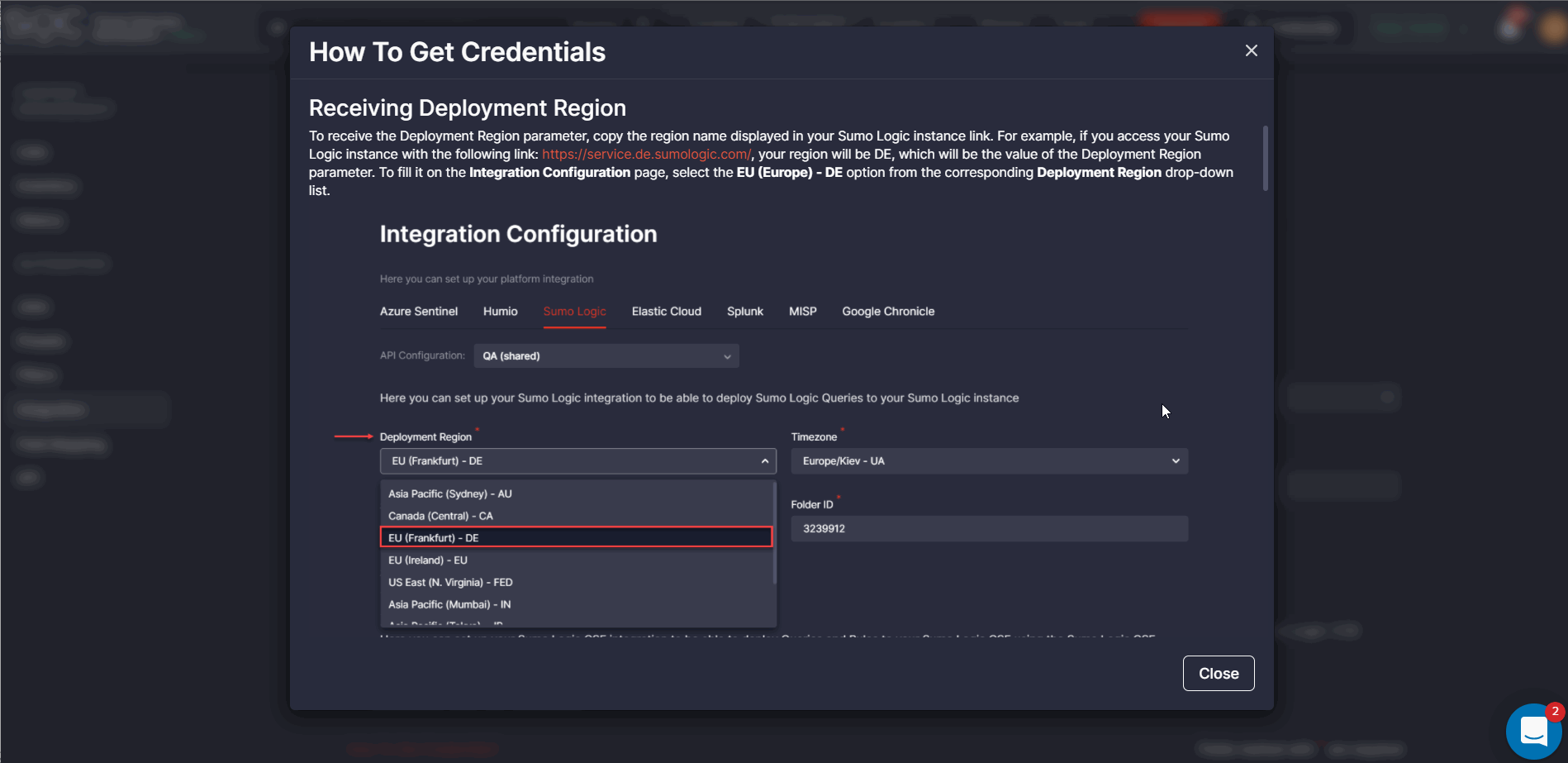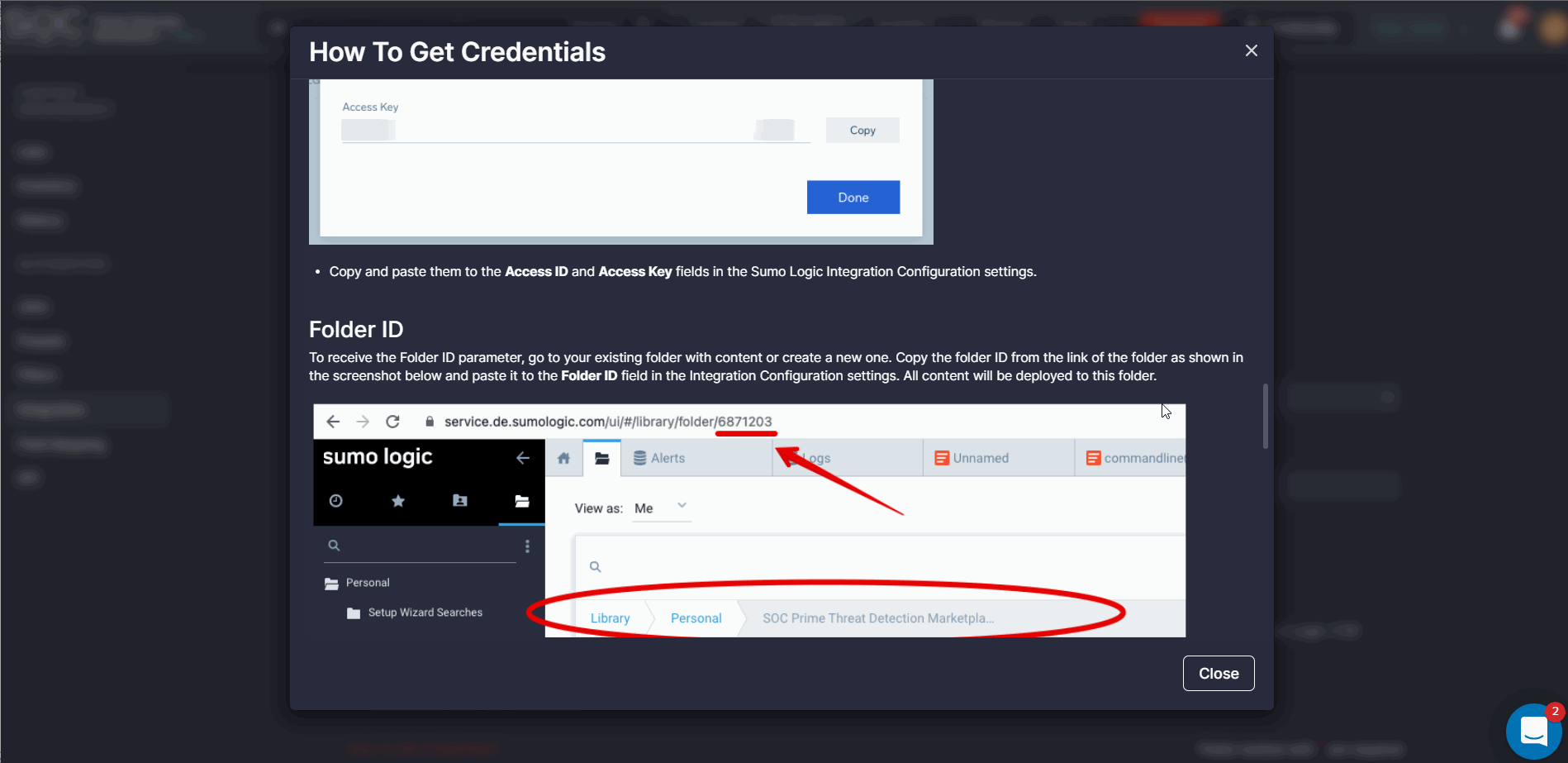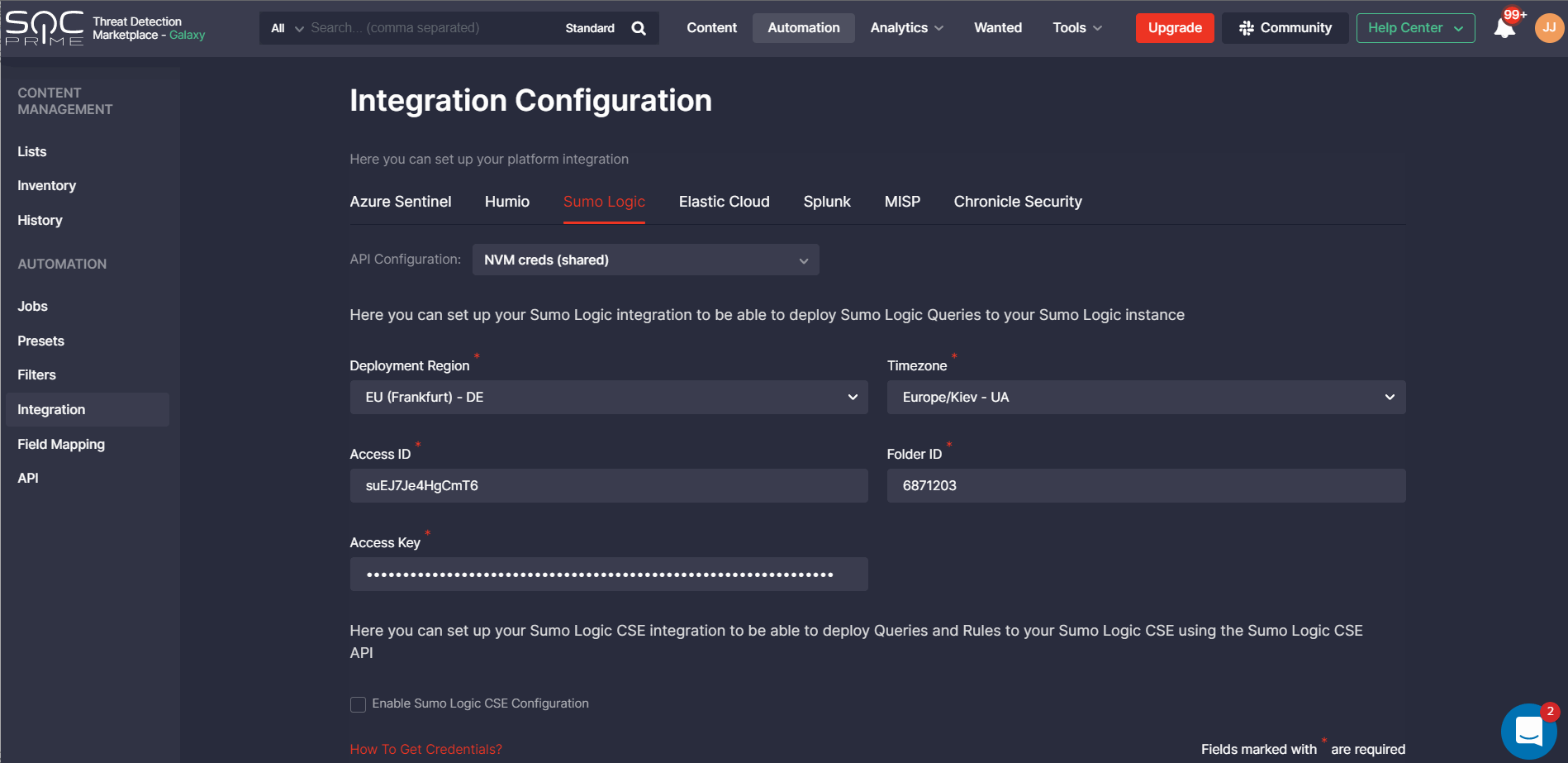
How to Get Credentials for Humio and Sumo Logic
To help security performers set up integrations with ease, we’ve recently added two how-to guides for Humio and Sumo Logic available by clicking the How To Get Credentials link on the Integration Configuration page. These guides are formatted similarly to the same how-to guide for Azure Sentinel and include detailed descriptions and screenshots for a more intuitive experience.
Threat Detection Marketplace API Integration Tool v. 2.3.1
With this release, we’ve enriched the TDM API Integration Tool with the ability to download detection content right from the Continuous Content Management lists using the corresponding /content-list endpoint. The following parameters should be included in the API request:
- content_list_name
- siem_type
- mapping_name
- preset_name
- alt_translate_config
All these parameters are described in the TDM API Integration Tool guide based on its latest version 2.3.1:
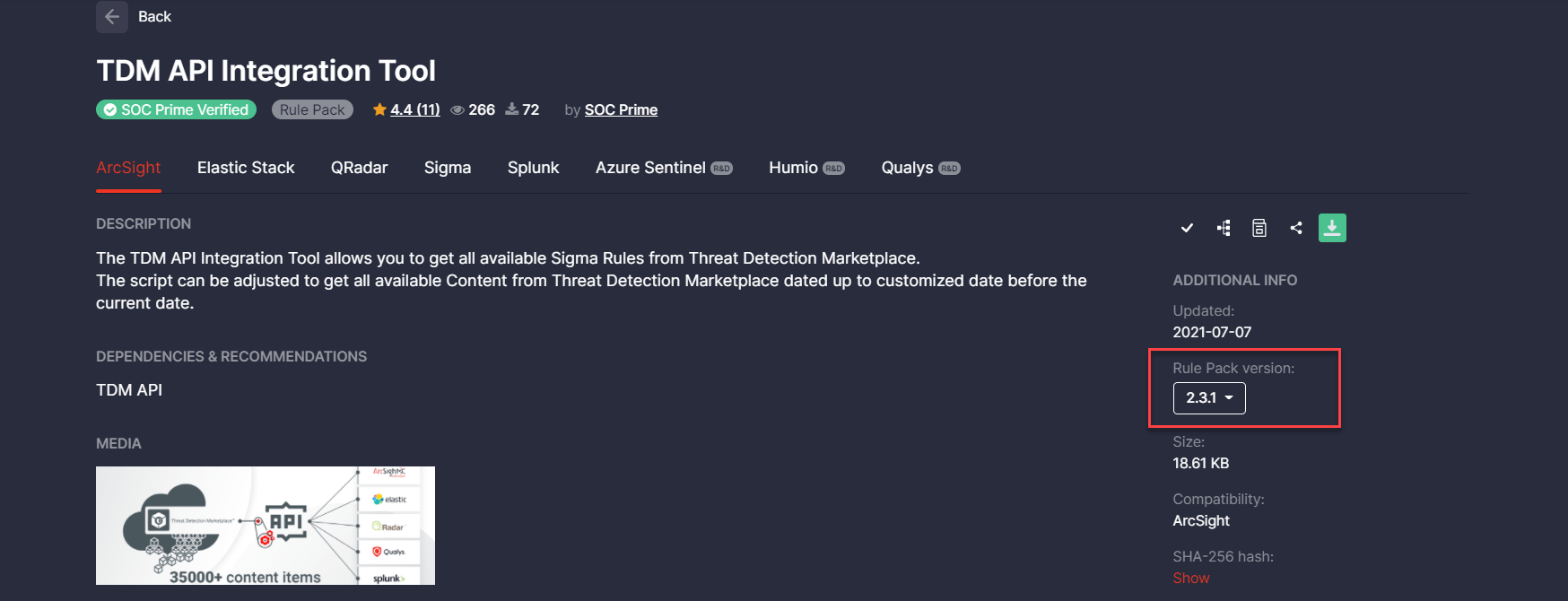
In addition, we’ve updated regular expressions for custom field mapping to make sure API obtains content items with the specified custom field mapping settings.
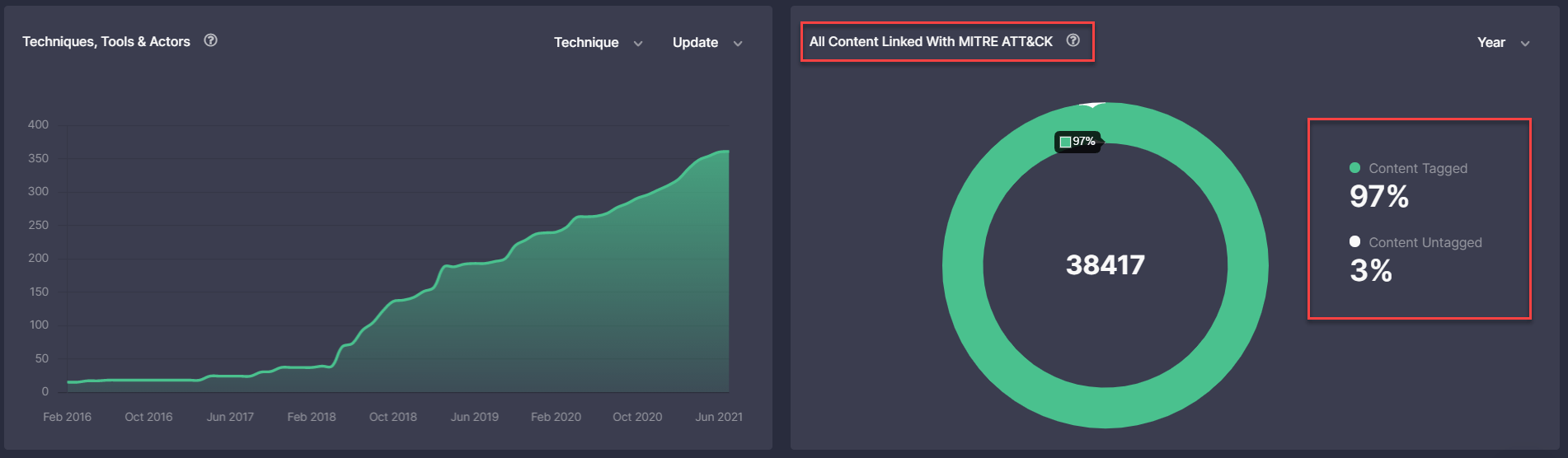
Leaderboards Page: All Content Linked With MITRE ATT&CK
With this Threat Detection Marketplace update, we’ve updated the All Content Linked With MITRE ATT&CK pie chart on the Leaderboards page that now displays the data in percent. The percentage value is more appropriate and intuitive for displaying the ATT&CK coverage.
Key Bug Fixes & Improvements
With this release, we’ve made the following bug fixes and improvements to Threat Detection Marketplace:
- Key user experience improvements:
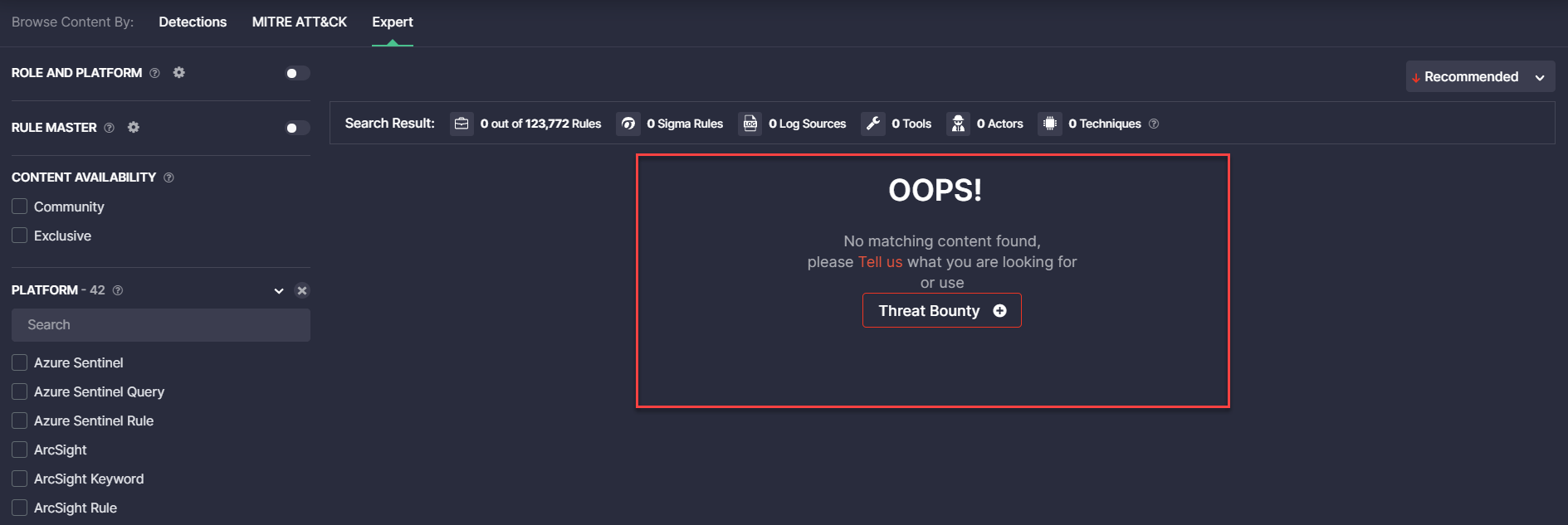
- Fixed the issue with the wrong layout of the No matching content found message, which occurred when moving to the next page. After making improvements, the message is properly positioned in the middle of the page.
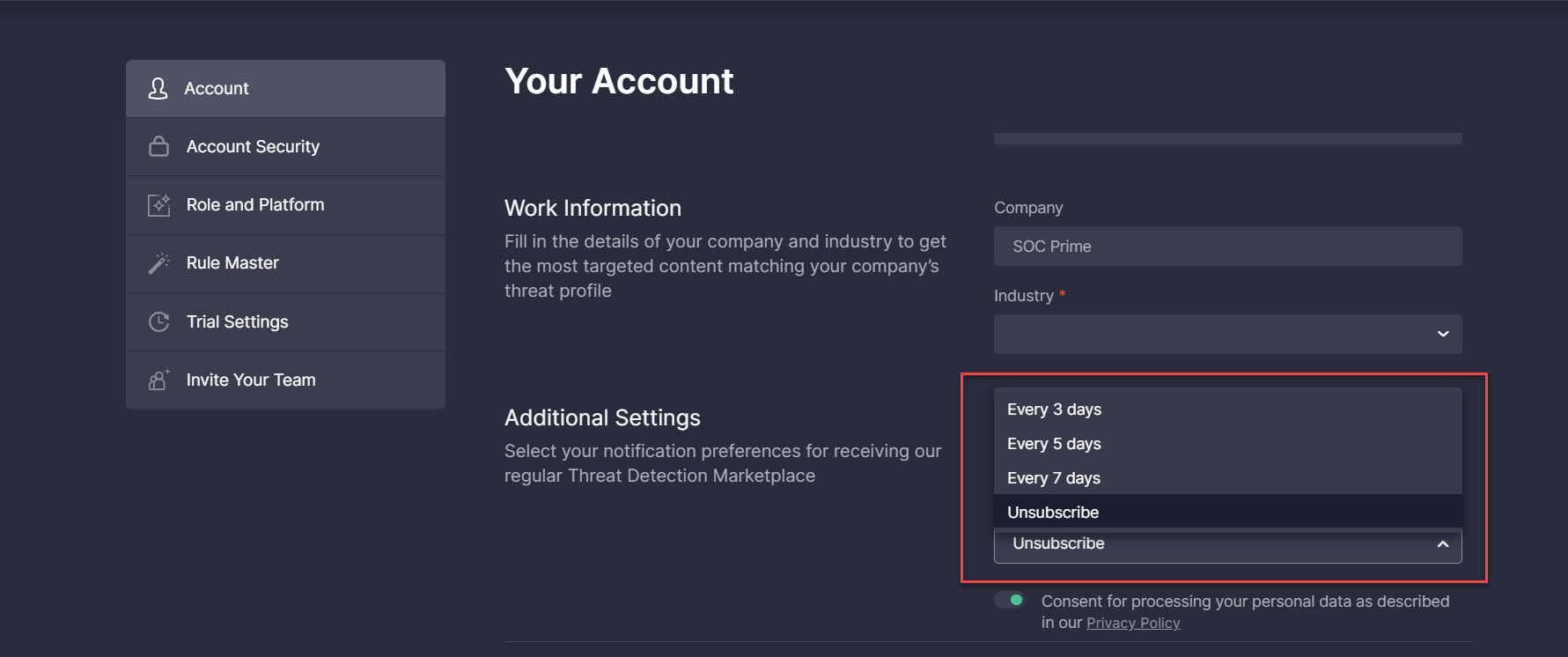
- Fixed the issue with the Notification interval drop-down list that improperly displayed available options when opening it upwards.
- Fixed the issue with the Close rule (X) button that returned users to the Content page and reset all previously entered filters and search criteria. After making improvements, security performers can now filter content, drill down to a certain rule and then click the X button and seamlessly return to the Content page, which will display the saved content search results.
- Fixed the issue with the display of the content number for Limited Access users in the Expert view mode.
- Renamed the Query tab to IOC Query for Qualys for a more intuitive threat detection experience.
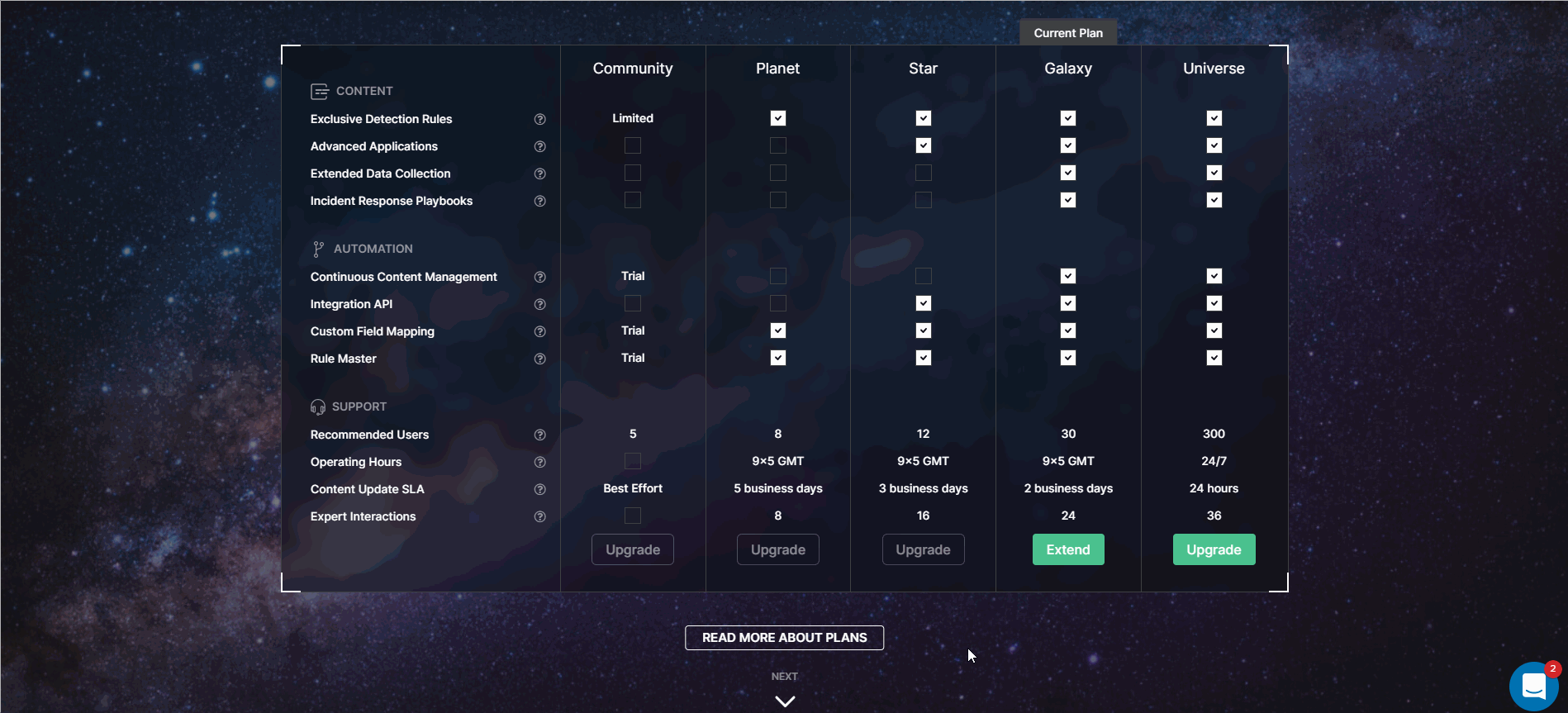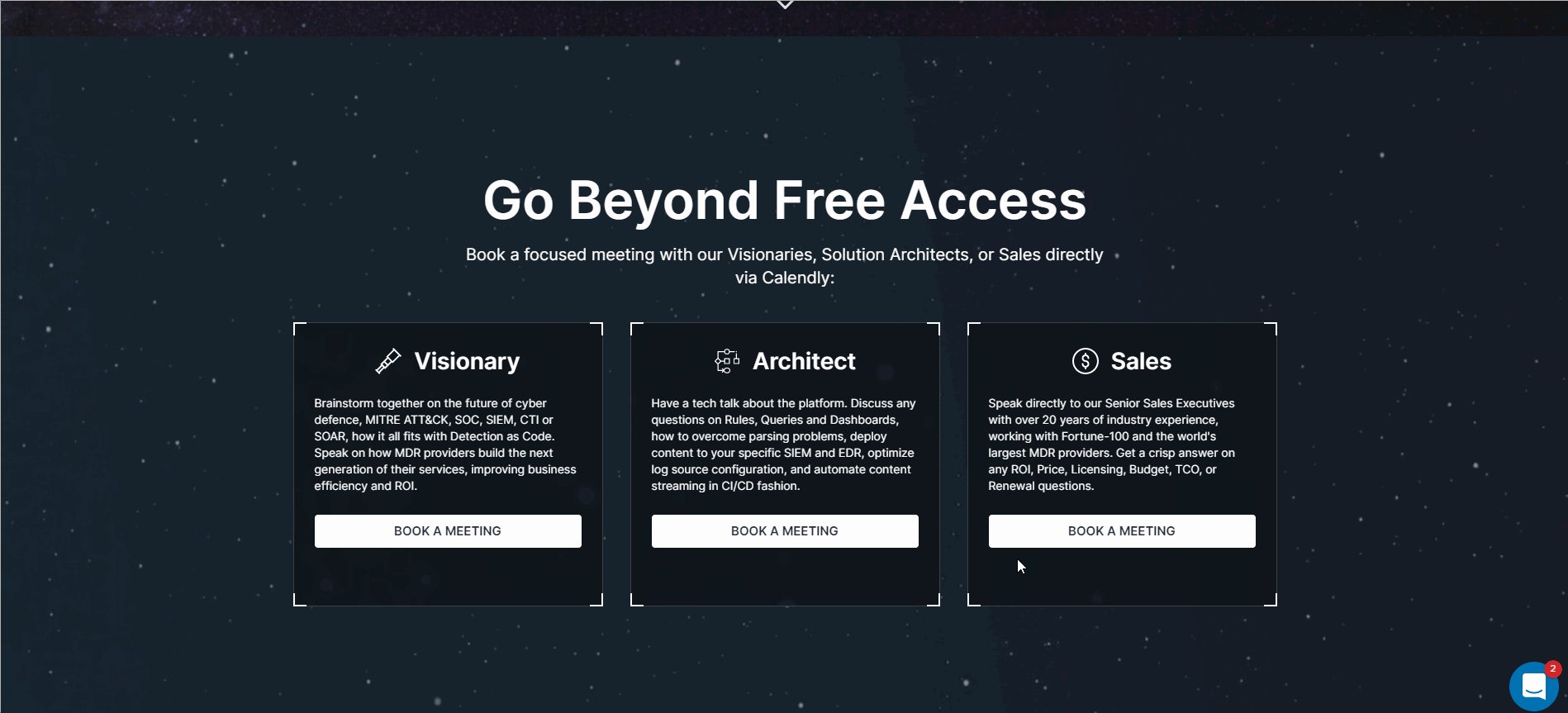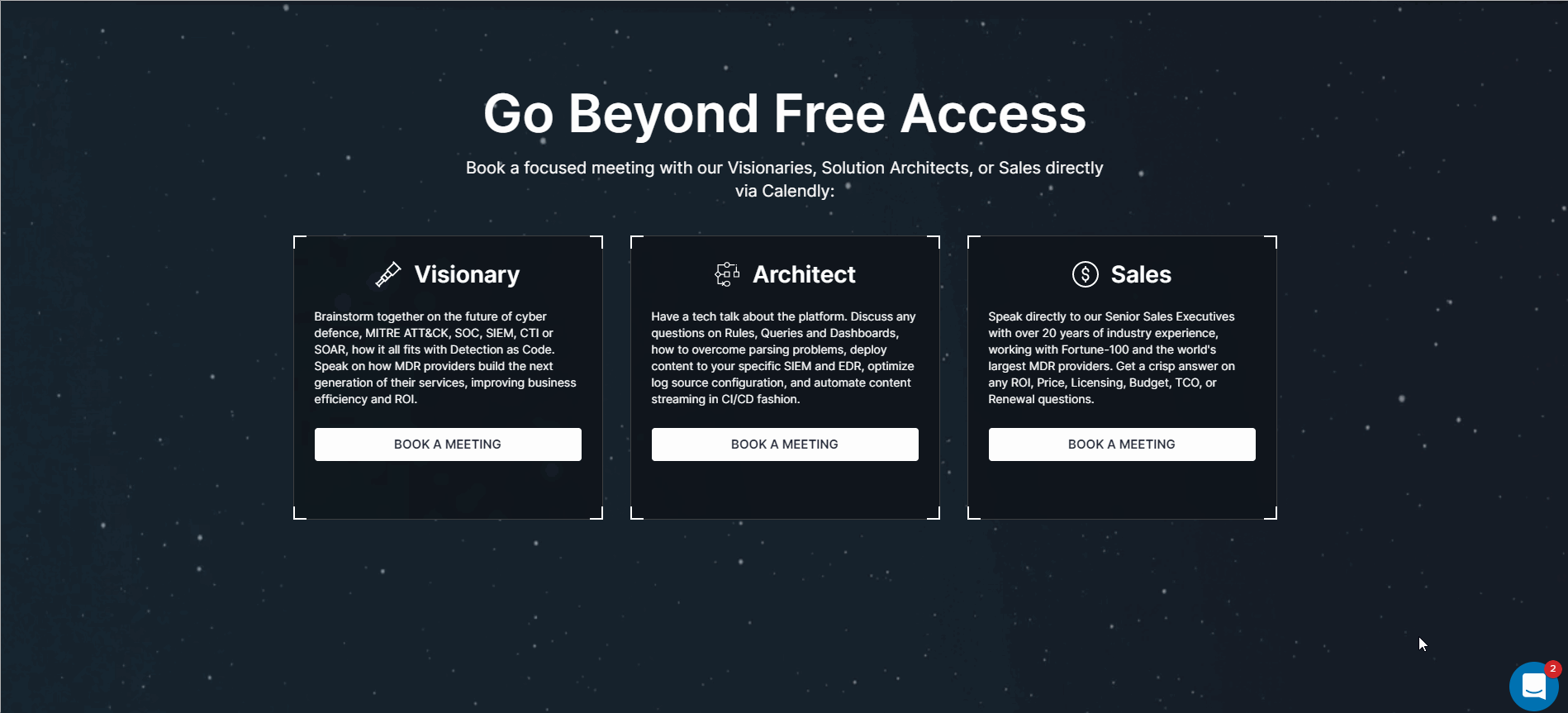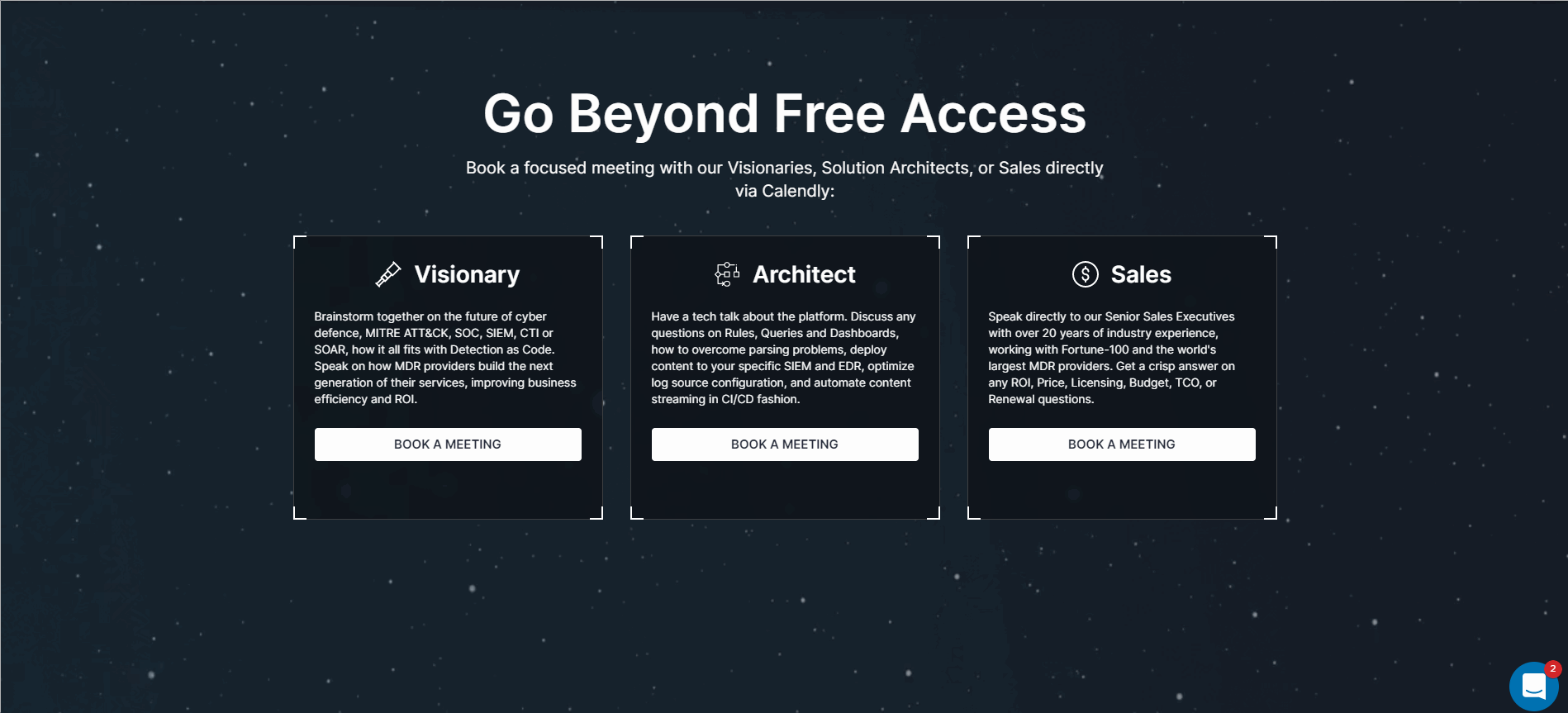
2. On the Upgrade page:
- Updated the time zone for Operating Hours to GMT, like 9×5 GMT
- Changed the order of the Subscription section and the block for booking a focused meeting via Calendly. The Subscription section now appears at the top since our Threat Detection Marketplace customers are first interested in the subscription plans once they land at this page, and then they can turn to the contact possibilities and book a focused meeting mostly tailored to their needs.
3. On the Content page > Detections view mode:
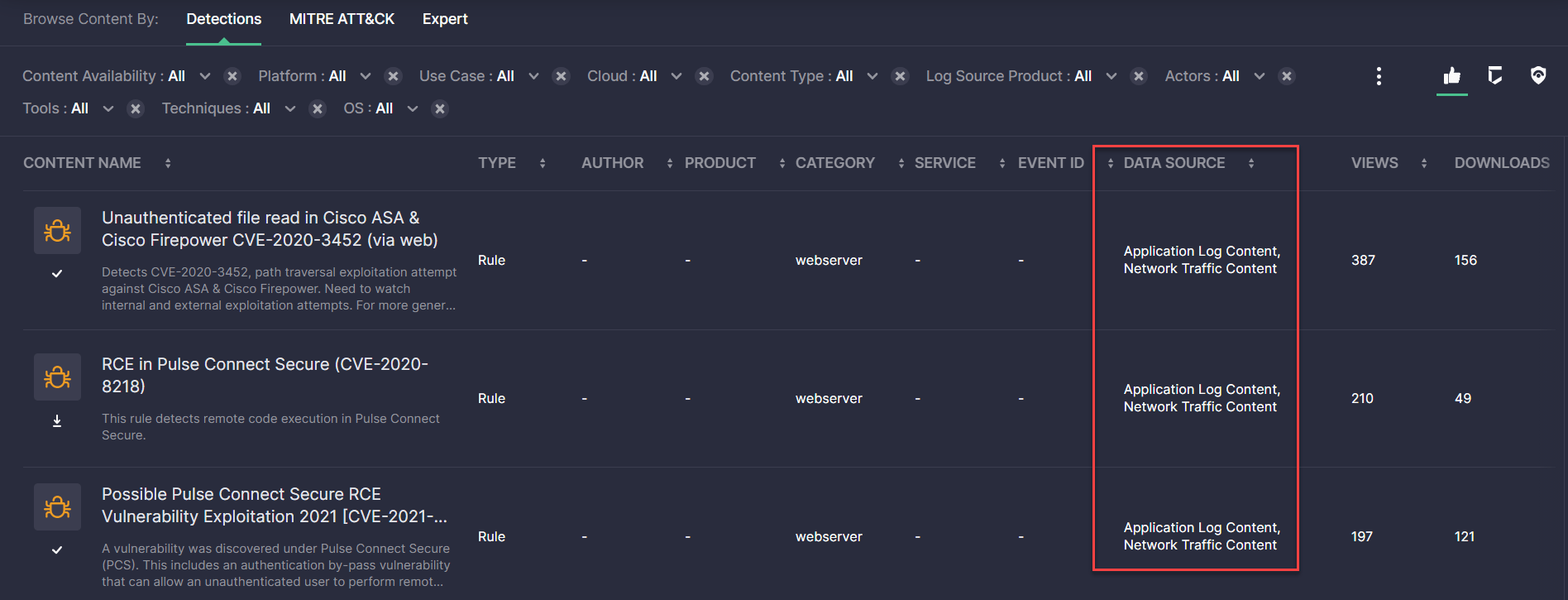
- Fixed the display of the Data Source block that was partly hidden.
- Fixed the issue with resetting applied filters after searching for content. With these improvements, the applied filters are saved after the content search similarly to the Expert view mode behavior.
- Fixed the scrolling issue when the table with content failed to scroll to the top automatically when moving to the next page.
Join Threat Detection Marketplace, the world’s largest Detection as Code platform that provides access and support for 100,000+ cross-tool SIEM & EDR algorithms matching your industry-specific use cases. And how about contributing to a global community of cyber defenders with your own detection content? Get started with our Threat Bounty Program!


