Threat Detection Marketplace 4.9.0 Is Released

On May 19, 2021, we released Threat Detection Marketplace version 4.9.0 to enhance the existing capabilities of our Content-as-a-Service platform and provide our customers with the most streamlined platform experience. The latest upgrade includes major content quality improvements, introduces a simplified flow for updating from the Limited Access to Community subscription, provides access to a detailed how-to guide on Microsoft Azure Sentinels rules creation, and advances Warden functionality by mastering the Scan Result pop-up.
Content Quality Enhancements: Carbon Black
At SOC Prime, we’re striving to improve the content quality when translating behavior-based detections to various SIEM, EDR, and NTDR language formats. With this latest release, we’ve improved content translations to the Carbon Black language format. Before the update, rule translations encountered an issue with round brackets () that were wrongly applied to all values on the platform back end. After making improvements, Carbon Black translations are processed in the expected format.
Change Email: Simplified Flow for Upgrading from Limited Access to Community
The latest Threat Detection Marketplace version introduces a more intuitive process of changing a personal email to a corporate one from the Your Account section in the user profile. Security performers can now seamlessly switch from the Limited Access to the Community subscription via a corporate email address. The simplified change email flow now consists of the following three steps:
1. Confirm Email — here security performers are prompted to confirm their current email address by entering a 6-digit OTP code sent to this email.
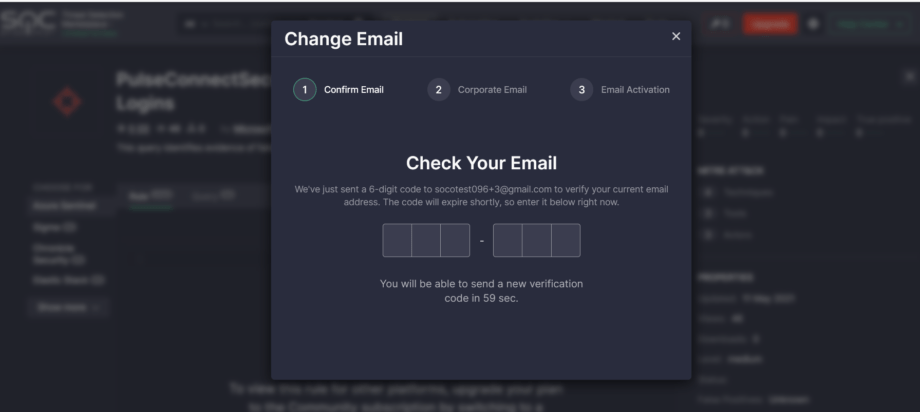
2. Corporate Email — this step requires entering a new corporate email address and confirming it with the OTP code sent to this new email.
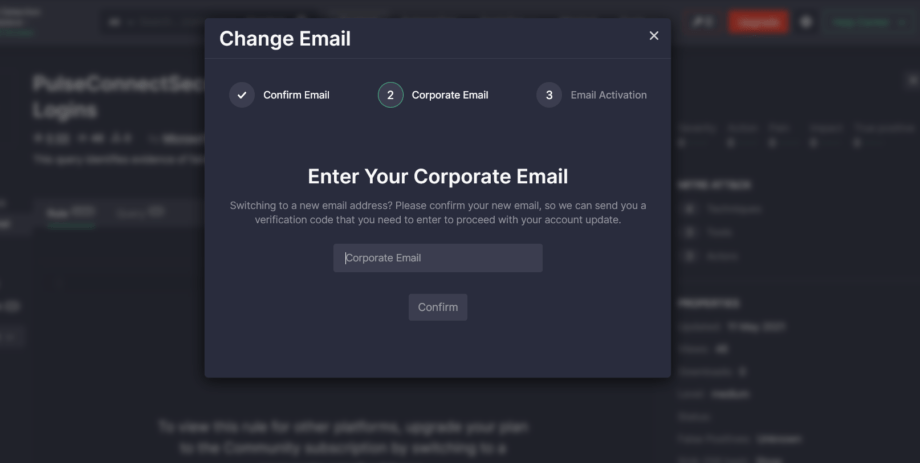
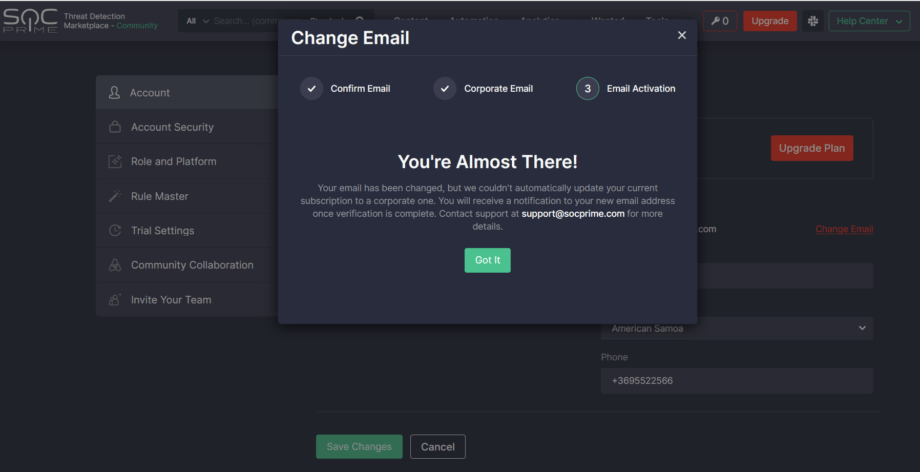
3. Email Activation — the final step where users are notified of the successful email change and the automatic subscription upgrade if everything goes smoothly.
In certain cases, the Email Activation step may take some time when users with the Limited Access subscription want to upgrade to Community by switching to the corporate email address. If they cannot be automatically upgraded to the Community subscription, verification on our side is required. For more details, Threat Detection Marketplace users can reach out to our Support Team.
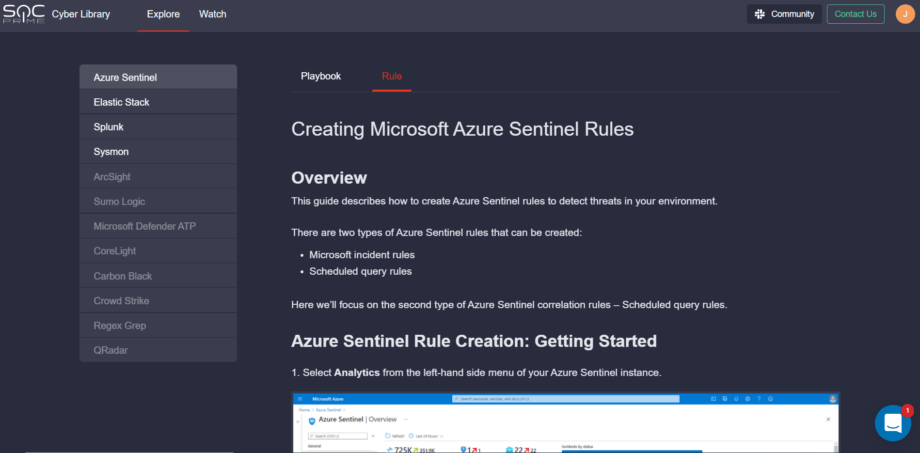
Cyber Library: How-to Guide for Microsoft Azure Sentinel Customers
To deliver the most personalized experience to our Microsoft Azure Sentinel customers, we’ve enriched our Cyber Library with the new insightful how-to guide on creating Azure Sentinel rules from scratch right in the customer’s SIEM instance. Follow this link and select the Rule tab to reach the guide and hone your cybersecurity skills.
Warden Improvements: Scan Result Pop-Up
With each new Threat Detection Marketplace release, we’re striving to add even more enhancements to the Warden functionality to make sure all detections written by our content contributors are unique and there are no rule duplicates.
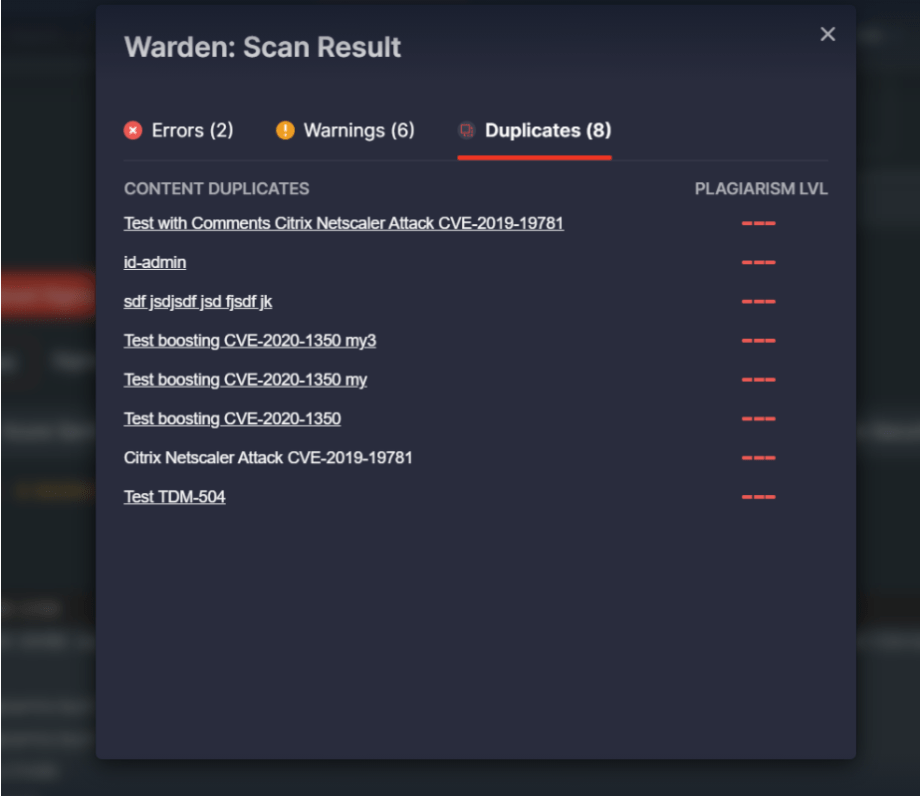
We’ve added the ability to display the Scan Result pop-up in the Developer Portal to be in sync with the Warden functionality in Threat Detection Marketplace. After adding a certain Sigma rule to the console, the Scan Rule button becomes active and allows viewing the detected results on the corresponding pop-up. The Scan Result pop-up has the same look and feel as in Threat Detection Marketplace and displays scan results categorized as Warnings, Errors, and Duplicates accordingly.
Also, we’ve made user experience improvements to the Scan Result pop enabling it to properly display a list of 10+ messages detected by Warden. Now security performers can see all the detected issues under the corresponding tabs to make the entire look and feel more compact and easy-to-read:
- Errors
- Warnings
- Duplicates
Key Bug Fixes & Improvements
To master the existing functionality of Threat Detection Marketplace and make your platform experience smother, version 4.9.0 fixes a set of bugs. With the latest upgrade, we’ve enhanced the following:
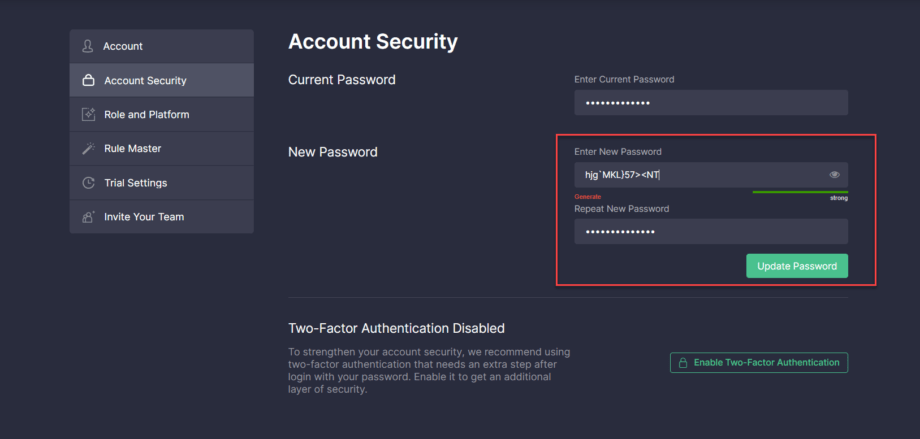
1. Fixed the issue when the system couldn’t accept a new password that contained < or > symbols. After the update, a new password can be seamlessly generated in the Account Security section of the user profile without causing any similar issues.
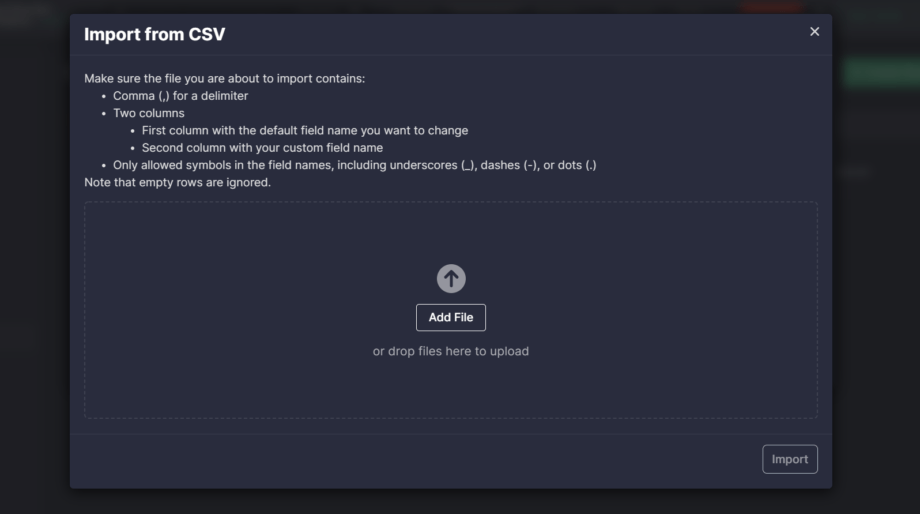
2. Fixed a couple of Custom Field Mapping issues:
- Related to importing a CSV file with the same fields. After the update, the system checks the file for duplicate fields and imports only one of these fields to avoid data redundancy.
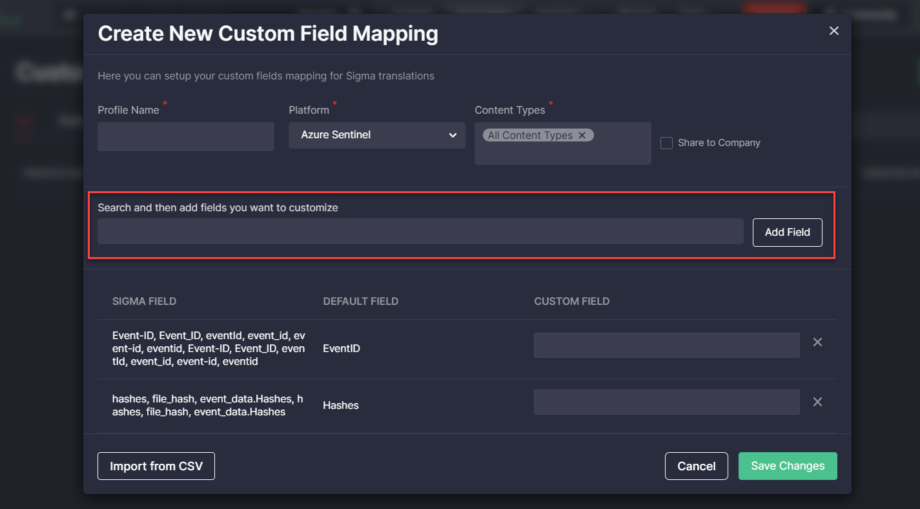
- With keeping displaying an error message after adding mapping fields the user wants to customize. After this update, an error message doesn’t show up when at least one mapping field has been added.
3. Fixed the Cyber Library issue with displaying speaker thumbnail images on the selected webinar page.
4. Fixed the font issue on Leaderboards > Top Authors bar chart for a consistent look and feel across the entire page.
Subscribe to Threat Detection Marketplace for free to explore the cutting-edge Detection as Code platform aggregating 100K+ queries, parsers, SOC-ready dashboards, YARA and Snort rules, Machine Learning models, and Incident Response Playbooks tailored to 23 market-leading SIEM, EDR, and NTDR technologies. Our content is continuously enriched with additional threat context, verified, checked for impact, false positives, and other operational considerations through a series of quality assurance audits. Eager to participate in threat hunting activities and craft your own detection content? Join our Threat Bounty Program!


