Continuous Content Management Updates
Continuous Content Management (CCM) is the Threat Detection Marketplace module that significantly reduces the burden on SecOps Teams by streaming compatible detections directly into the SIEM of the customer’s choice. To provide our users with the best ever experience and broader defense capabilities in their constant battle against emerging threats, on February 25, 2021, we released the new version of Threat Detection Marketplace that covers major improvements to our CCM module.
Azure Sentinel and Humio Enhancements
For performance optimization and better maintenance, with this release, we’ve moved Microsoft Azure Sentinel to the new back-end architecture. Now you can smoothly stream Azure Sentinel Queries and Rules straightforward to your SIEM, and the support for Workbooks and Configs is coming soon. It is worth noting that support for Humio Alerts was initially implemented based on this architecture, being available for users from December 24, 2020.
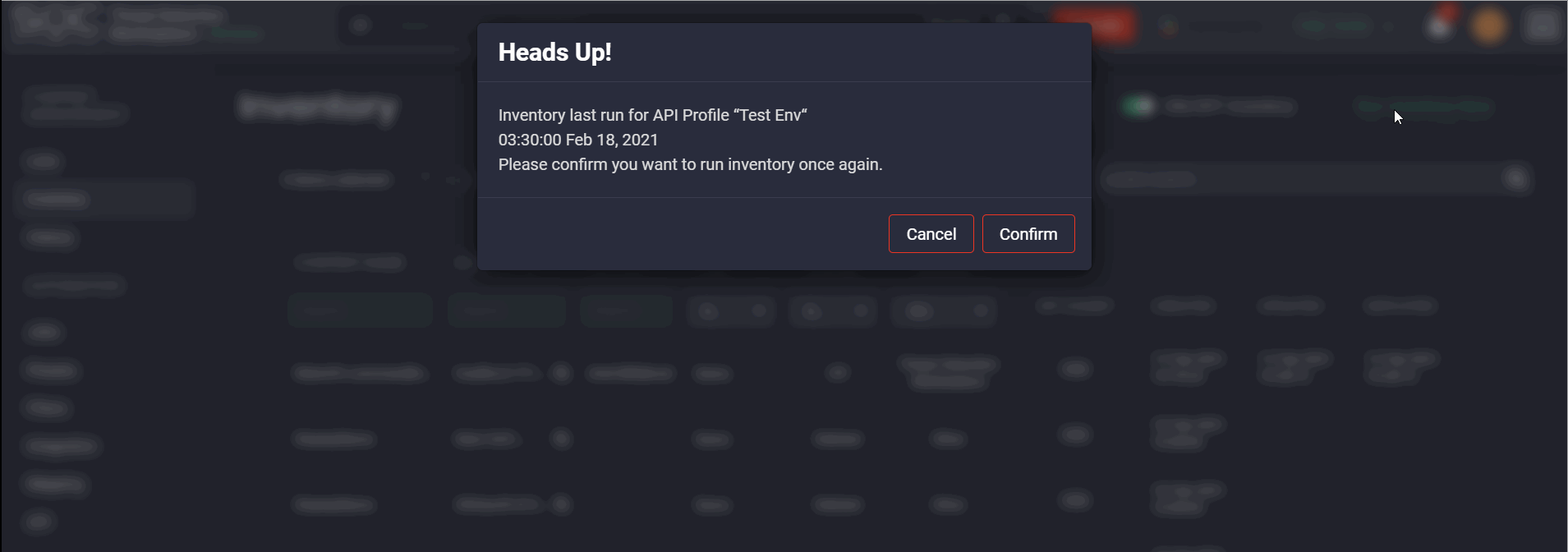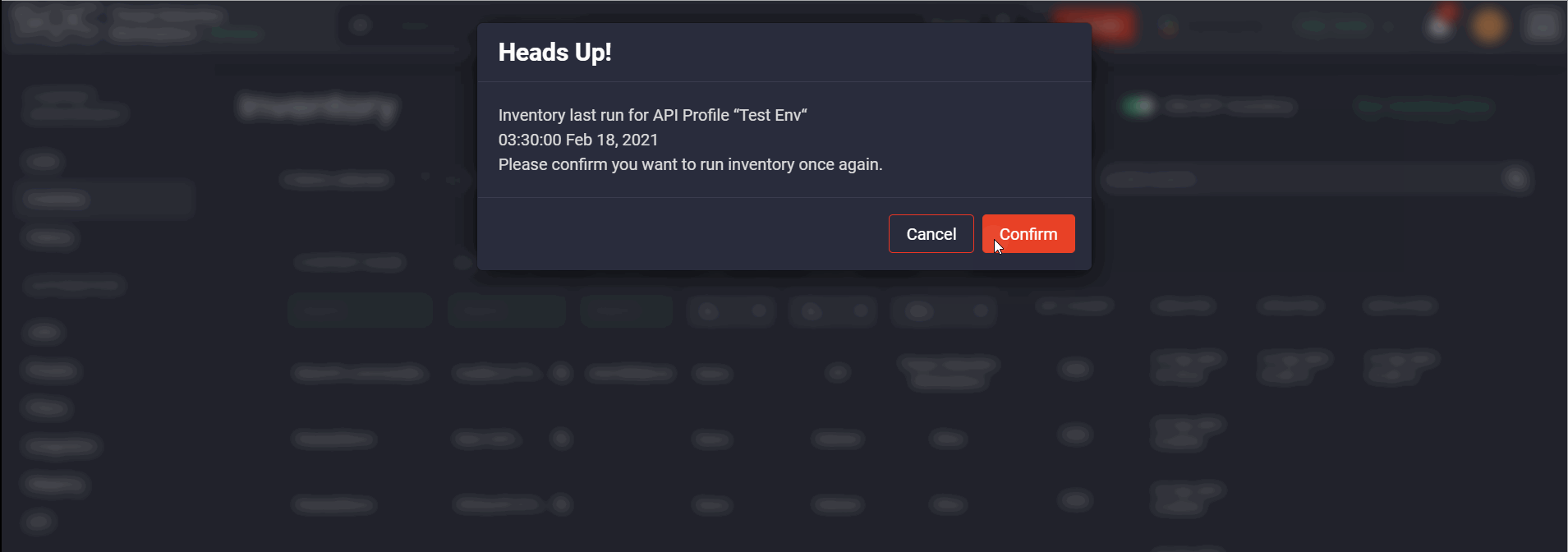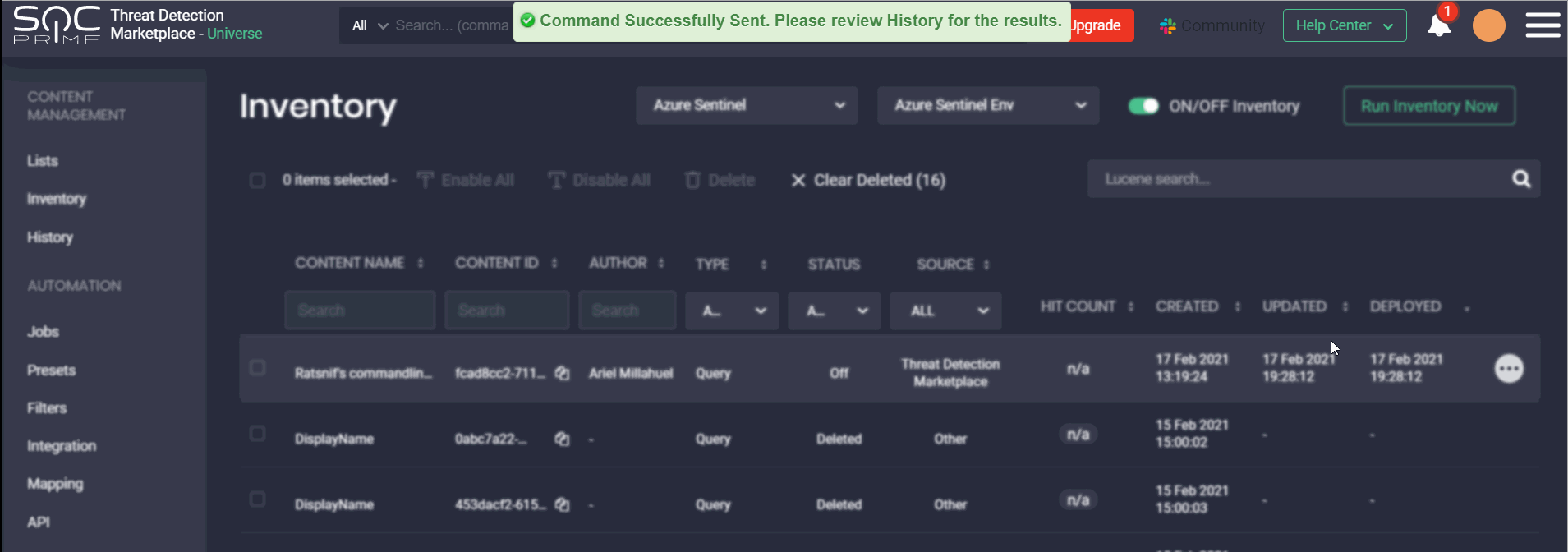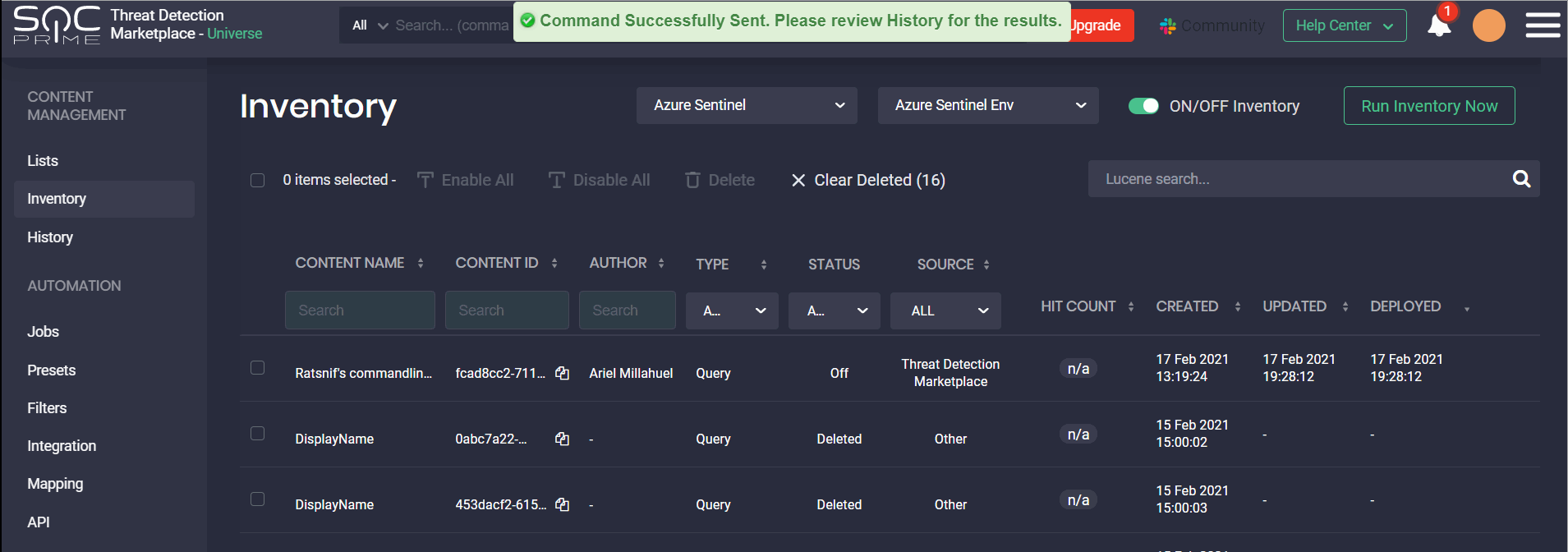
Starting from February 2021, we have provided the CCM users with the ability to run their content inventory script manually for certain enabled API profiles related to the Azure Sentinel and Humio SIEMs. To manually run the script, click the Run Inventory Script button in the upper right-hand corner of the Inventory page. The button is active once the Inventory toggle switch next to the selected API profile for the Azure Sentinel or Humio platform is ON.
Note: You can click the button and Run Inventory Script only after 10 minutes have passed since the last inventory script launch. Otherwise, the button won’t be active. This is done to prevent this script and SIEM data from overload.
After clicking the Run Inventory Script button, you can see the following details:
- The name of the related API Profile to be launched
- The date and time of the last script launch
To complete the manual inventory script launch, click the Confirm button.
Additionally, with this release, our customers can choose the way they want to delete the selected content items:
- From both their Azure Sentinel SIEM and the Inventory page
- From the Inventory page only
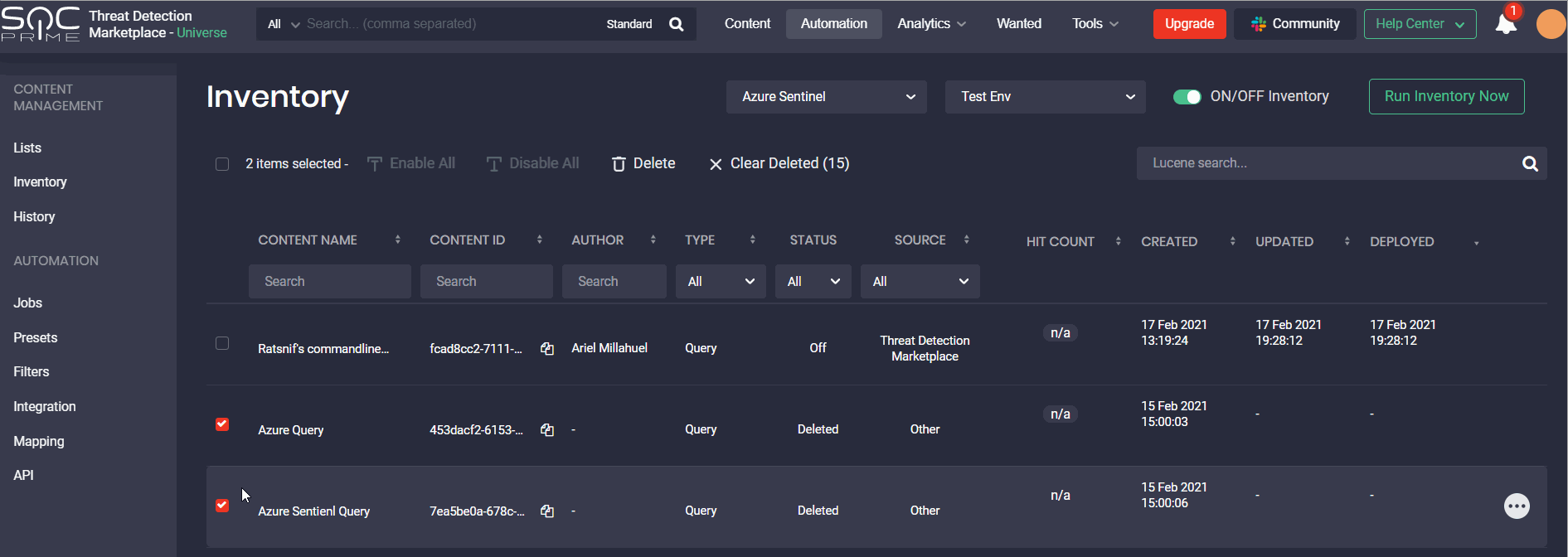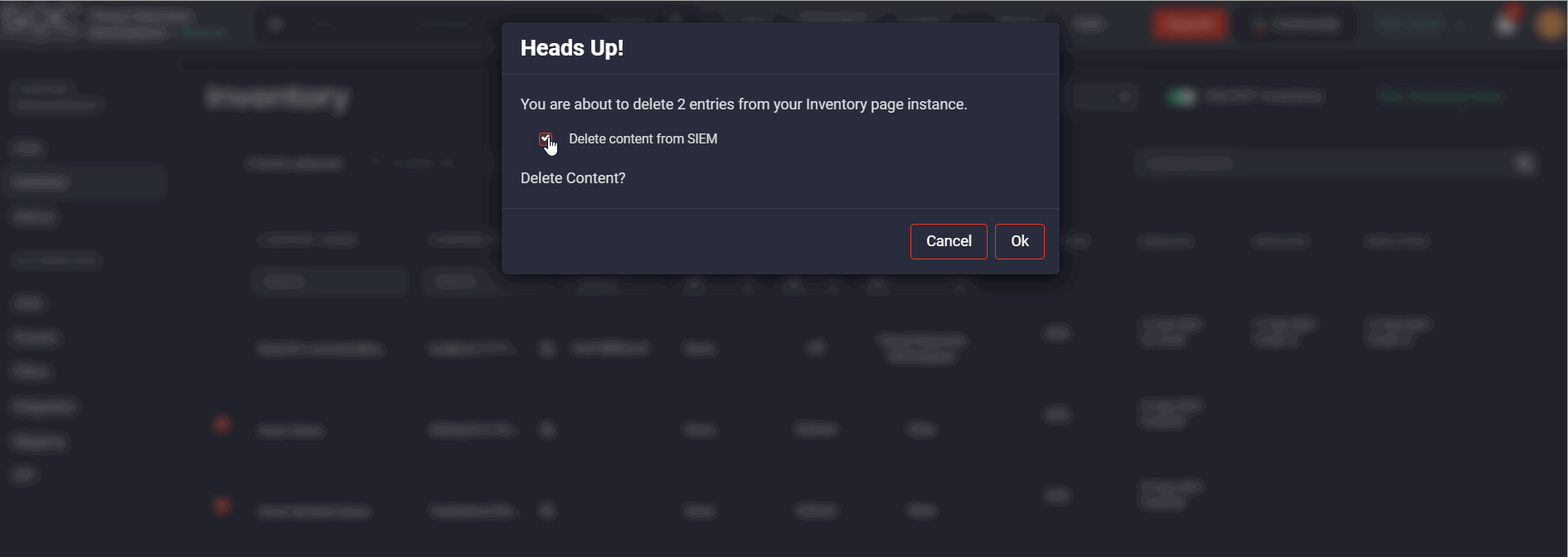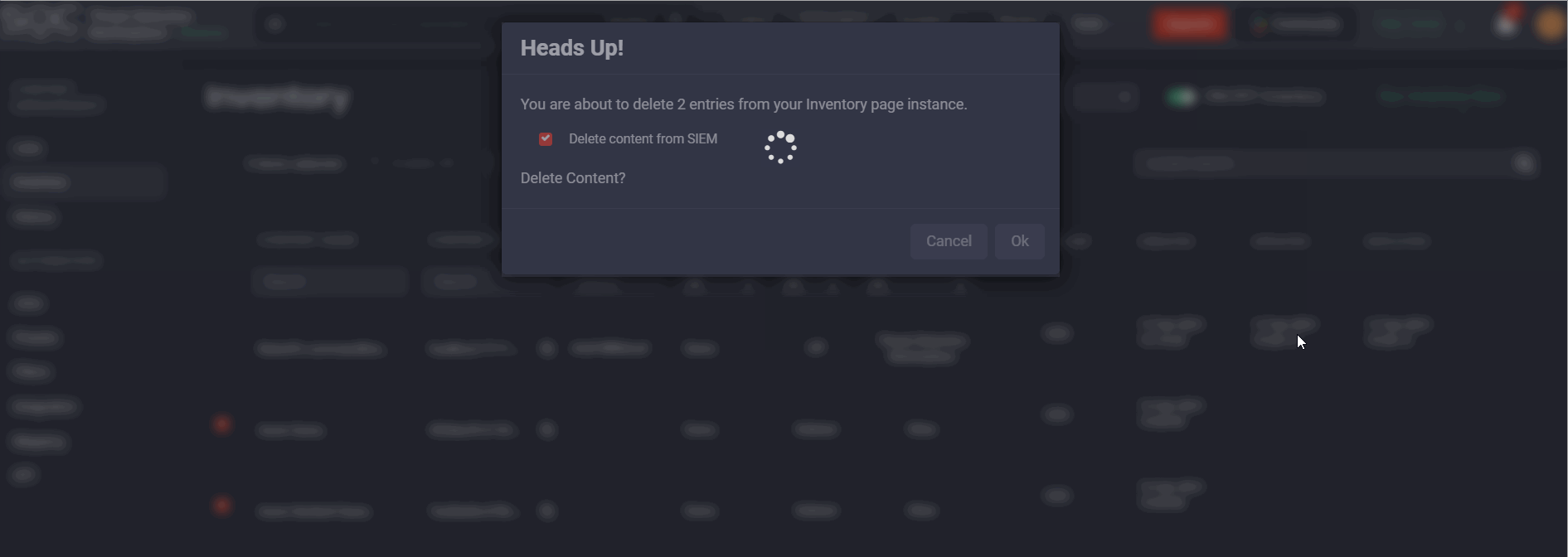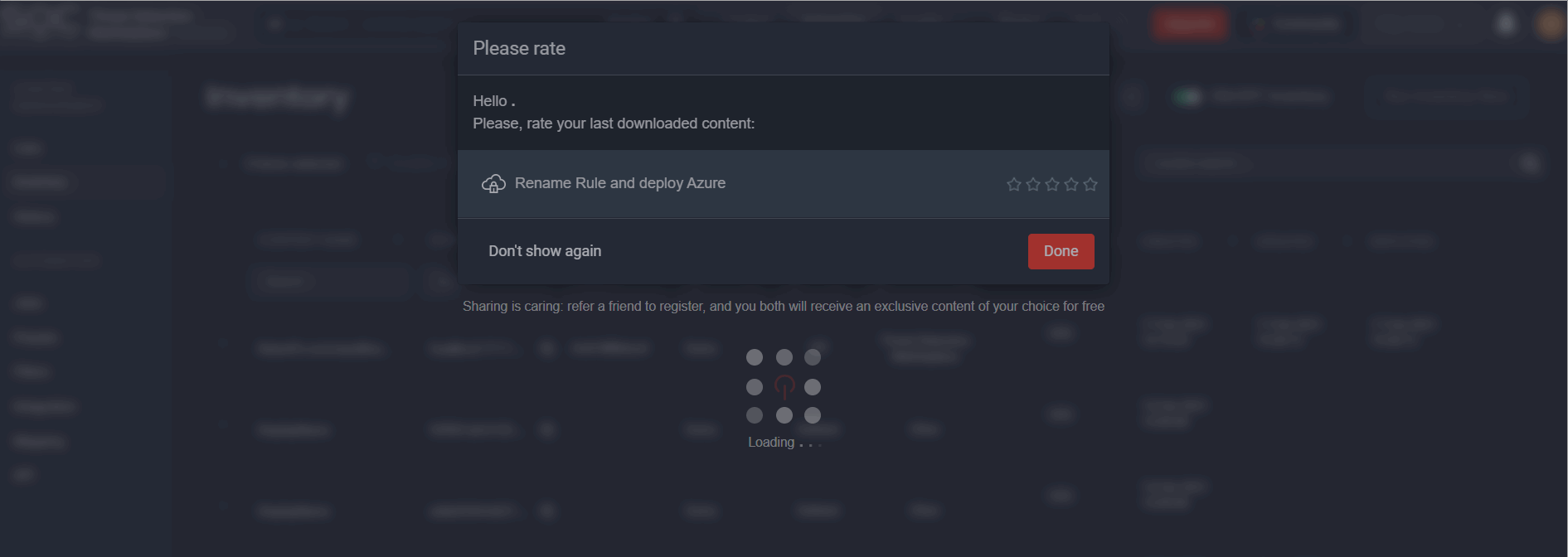
After clicking the Delete button on the Inventory page, the Threat Detection Marketplace users will see a pop-up prompting them to specify their action. To delete content on both the Inventory page and the Azure Sentinel instance, select the corresponding checkbox. If the user hasn’t marked the Delete content from SIEM checkbox, the selected content will reappear on the CCM Inventory page after the next inventory script launch.
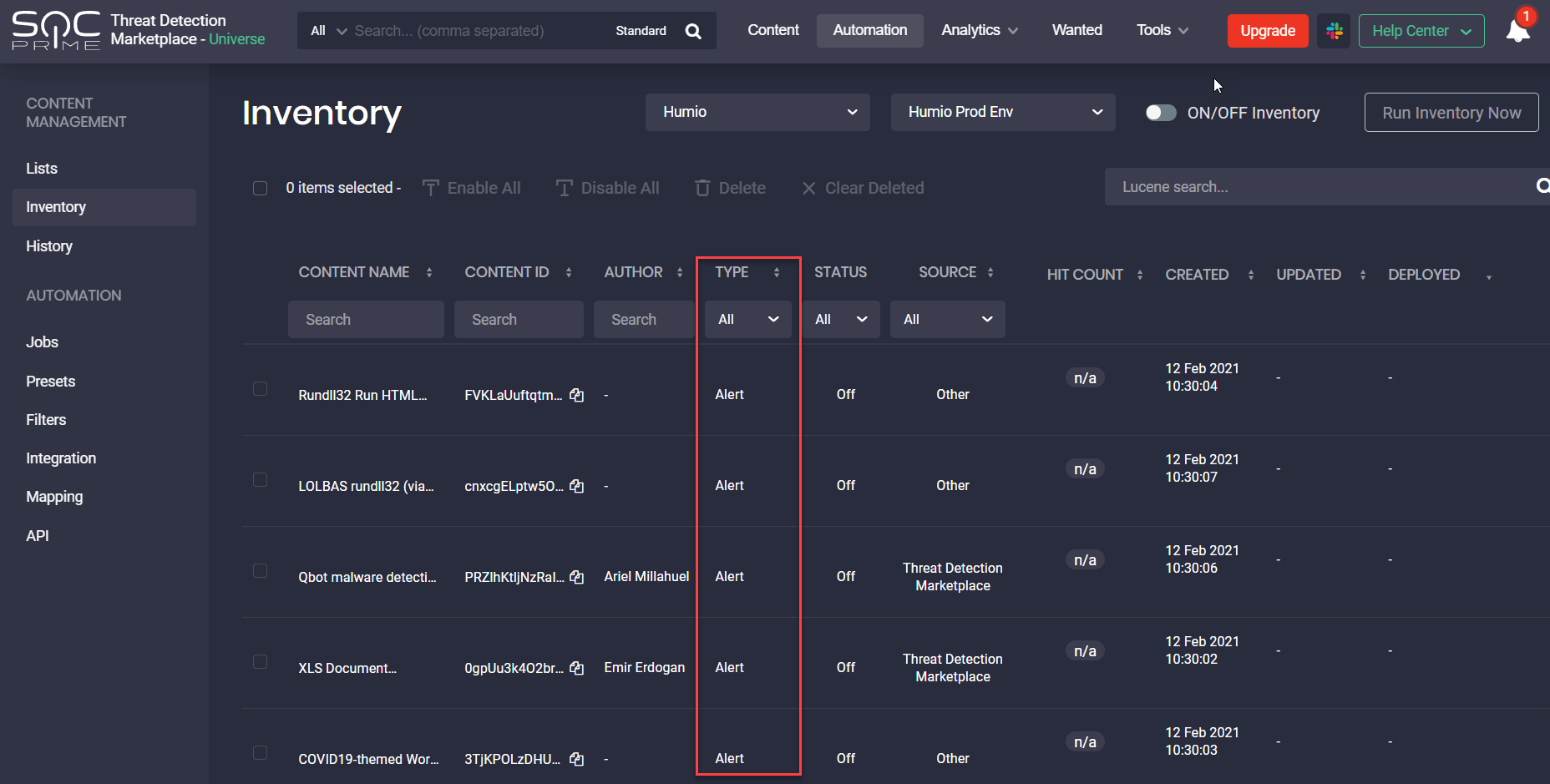
We’ve also introduced a set of Inventory page improvements related to the Humio SIEM. The supported content type for Humio now appears under the Type column. We’ve replaced the Rule content type with the much more intuitive Humio content type name currently supported by CCM — “Alert.”
Additionally, the predefined list of options has been added to the Throttle Time field on the Presets page. Before this release, the field accepted any values that caused issues. From now on, our Humio users can select only one of the options from the list that will be accepted by the system.
New Intuitive Platform Experience and Better Performance
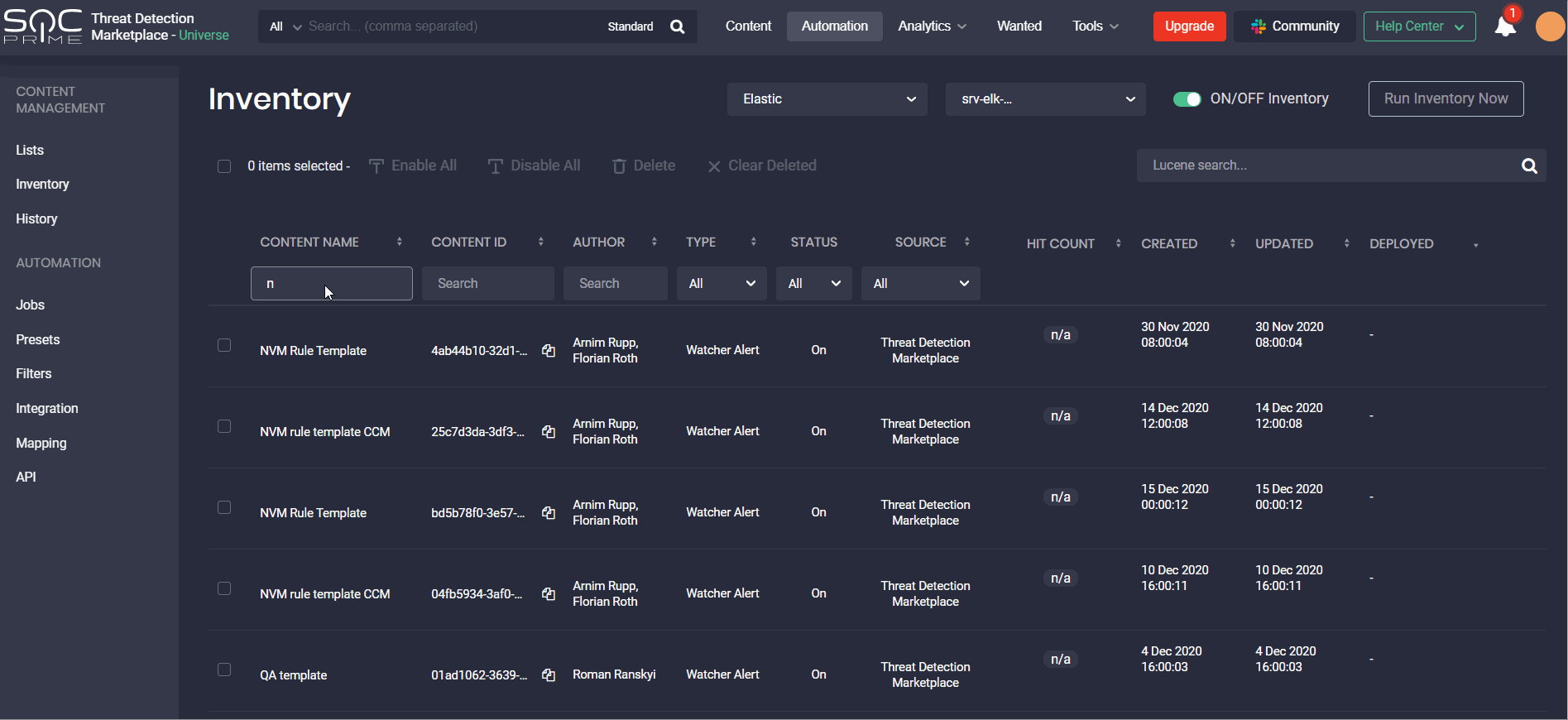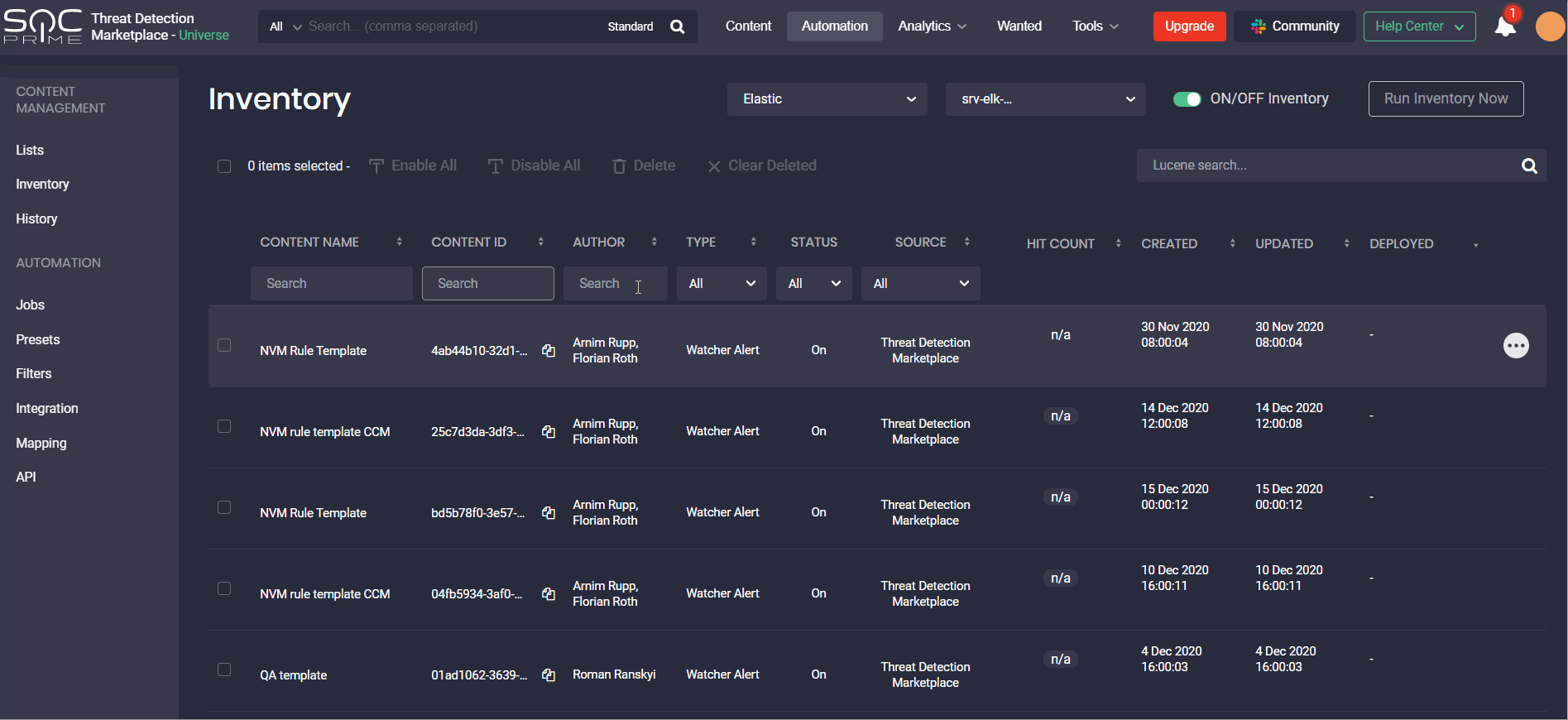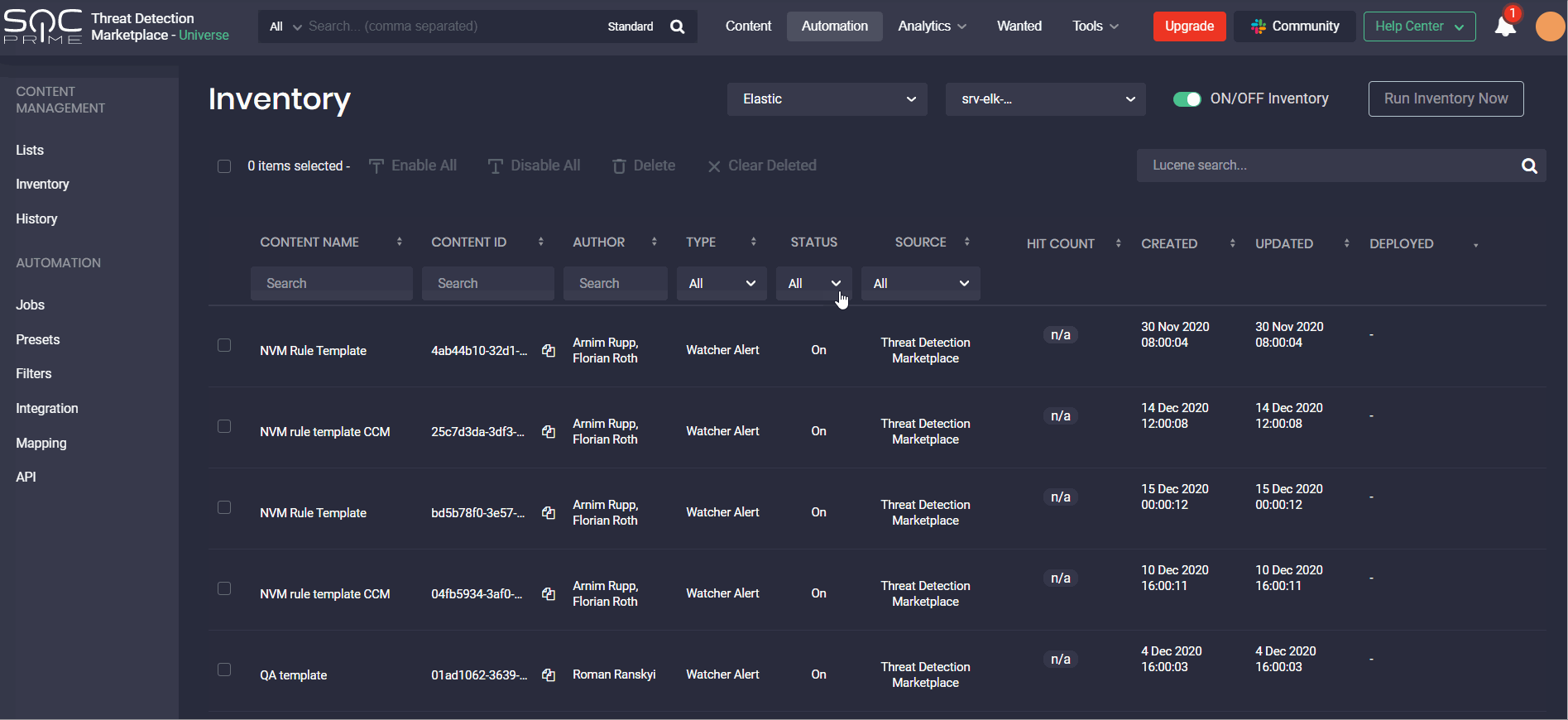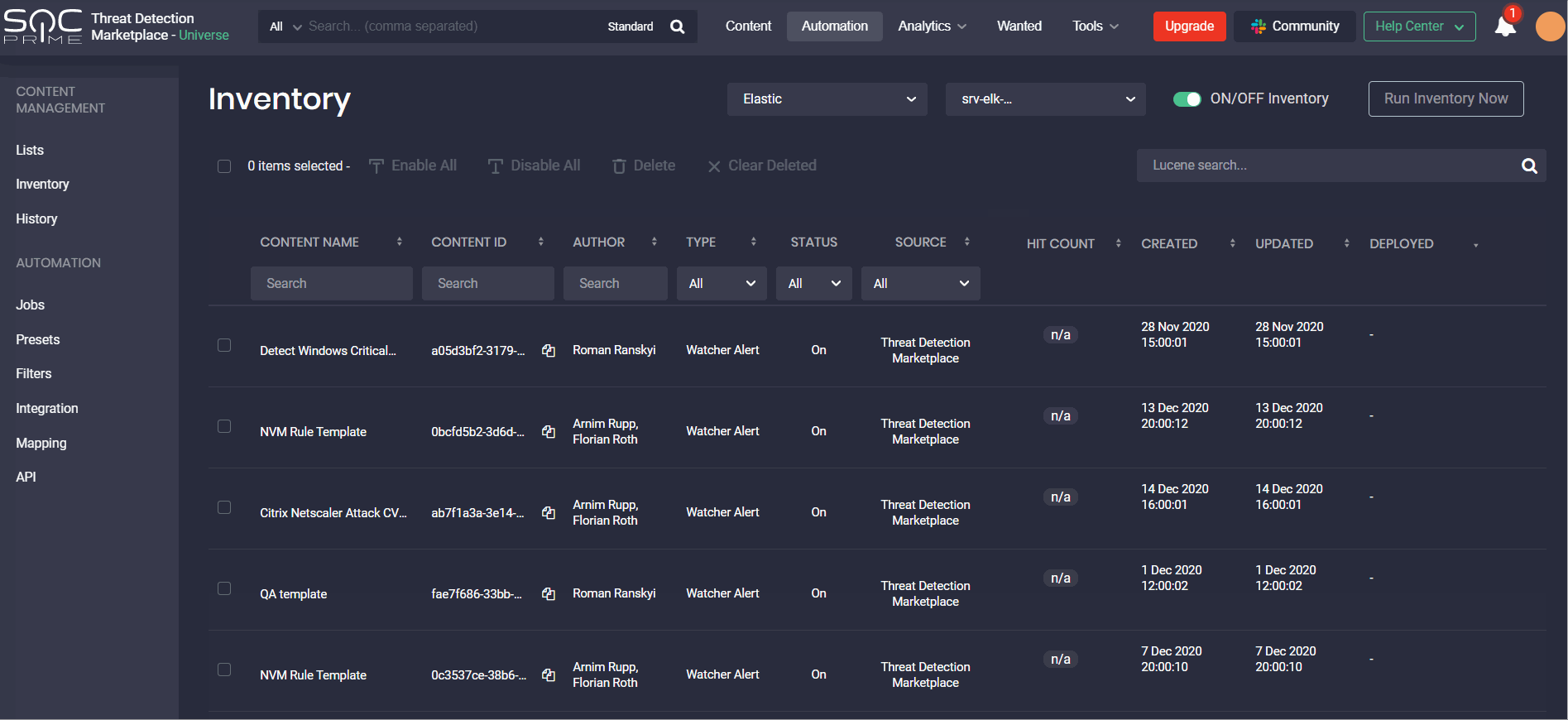
For a more streamlined content search on the Inventory page, we’ve added filters that can be used along with the Lucene search queries based on user preferences, which is similar to the standard and advanced search options on the Content page. These newly added easy-to-use content search filters on the Inventory page allow displaying the search results based on content filtering in a matter of clicks by:
- Content Name
- Content ID
- Author
- Type:
- Querry and Rule for Azure Sentinel (currently supported by the new architecture)
- Alert for Humio
- Rule Alert, Saved Search, and Watcher Alert for Elastic Cloud
- Status
- On — enabled on the SIEM end
- Off — disabled on the SIEM end
- Deleted — deleted from the SIEM instance but available on the Inventory page in CCM
- Source — Threat Detection Marketplace content or other content sources available
Also, with this latest update, the process of creating content lists becomes even more intuitive. To select the list type, users only need to specify tags (optionally for dynamic lists), with no requirements for selecting a platform and its related content type when adding a new list.
Furthermore, our customers are now able to drill down to the content item page with its source code right from the content list in a matter of a click.
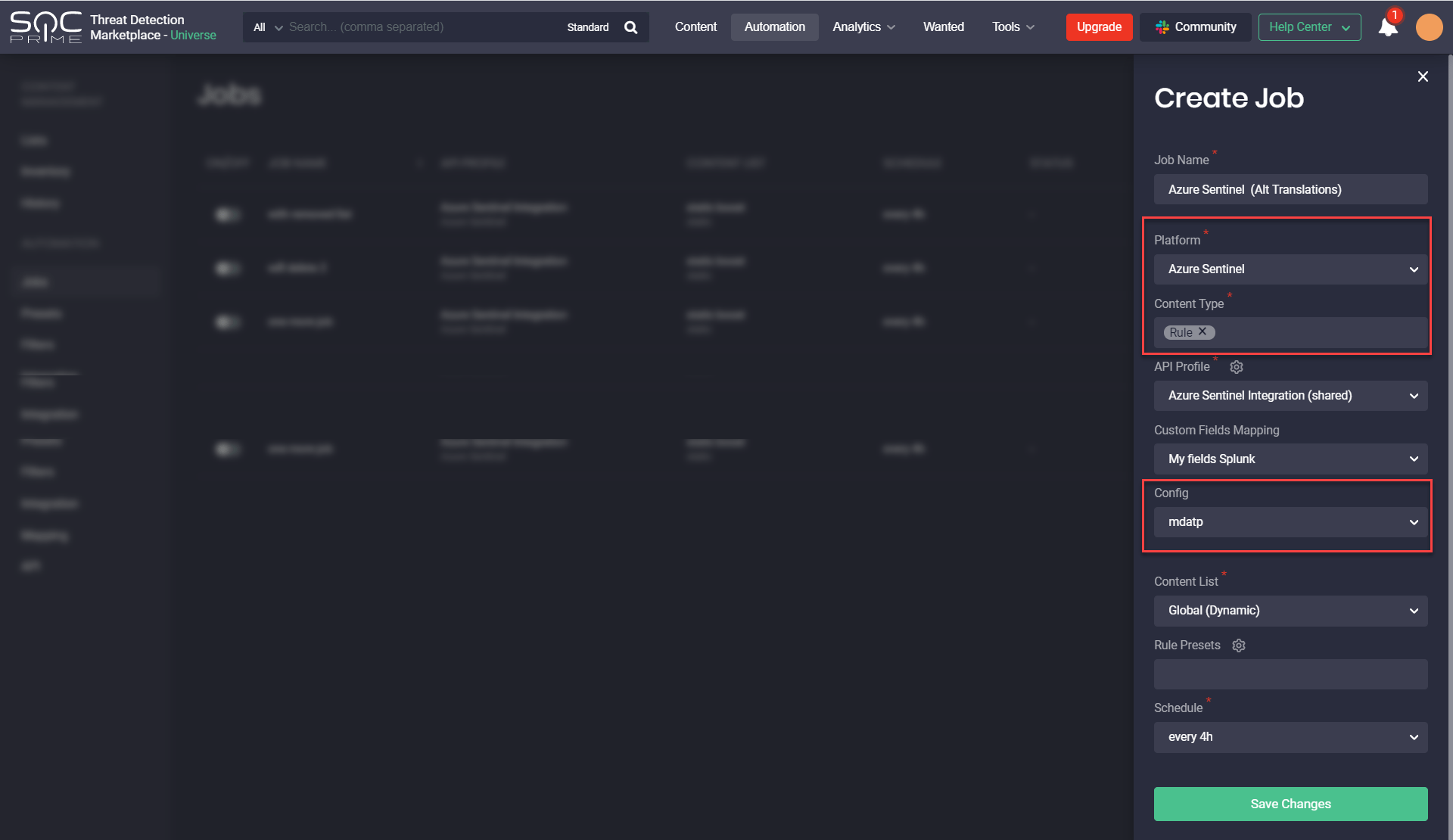
Another major improvement to our CCM module enables linking content lists to specific platforms (Azure Sentinel, Humio, or Elastic) and their related content types when creating jobs. Specifically, security performers can create three separate jobs where each of them performs a certain function and is related to the specific platform instead of creating duplicate lists based on the same content items.
Additionally, while creating Jobs our customers now can deploy alternative translations for certain content types. Just select alternative translations that are available in the Config drop-down list depending on the platform and its content type when creating a new job. For instance, when selecting the Azure Sentinel Rule, you can choose the mdatp alternative translation format and then deploy this content when running the corresponding job.
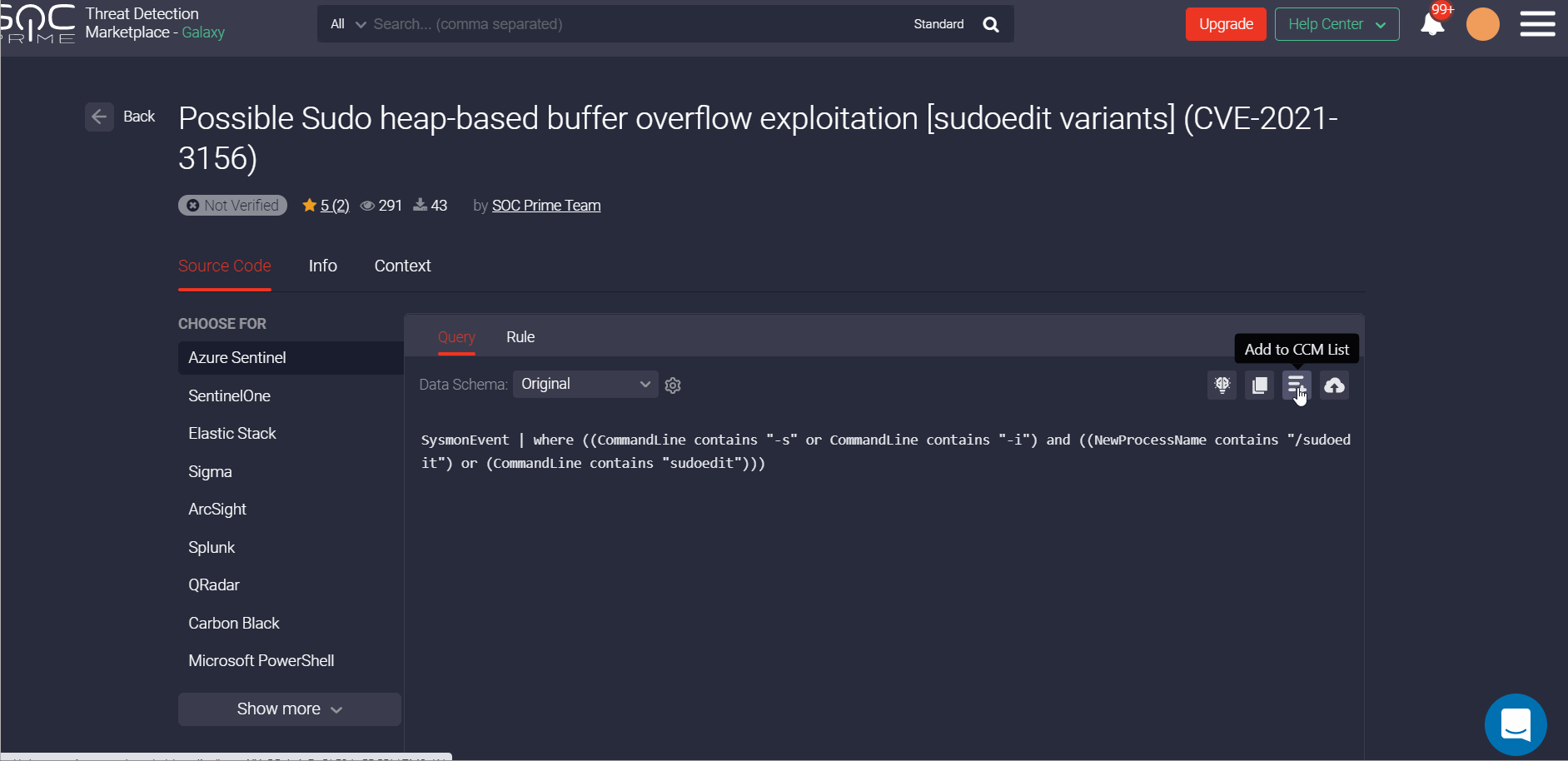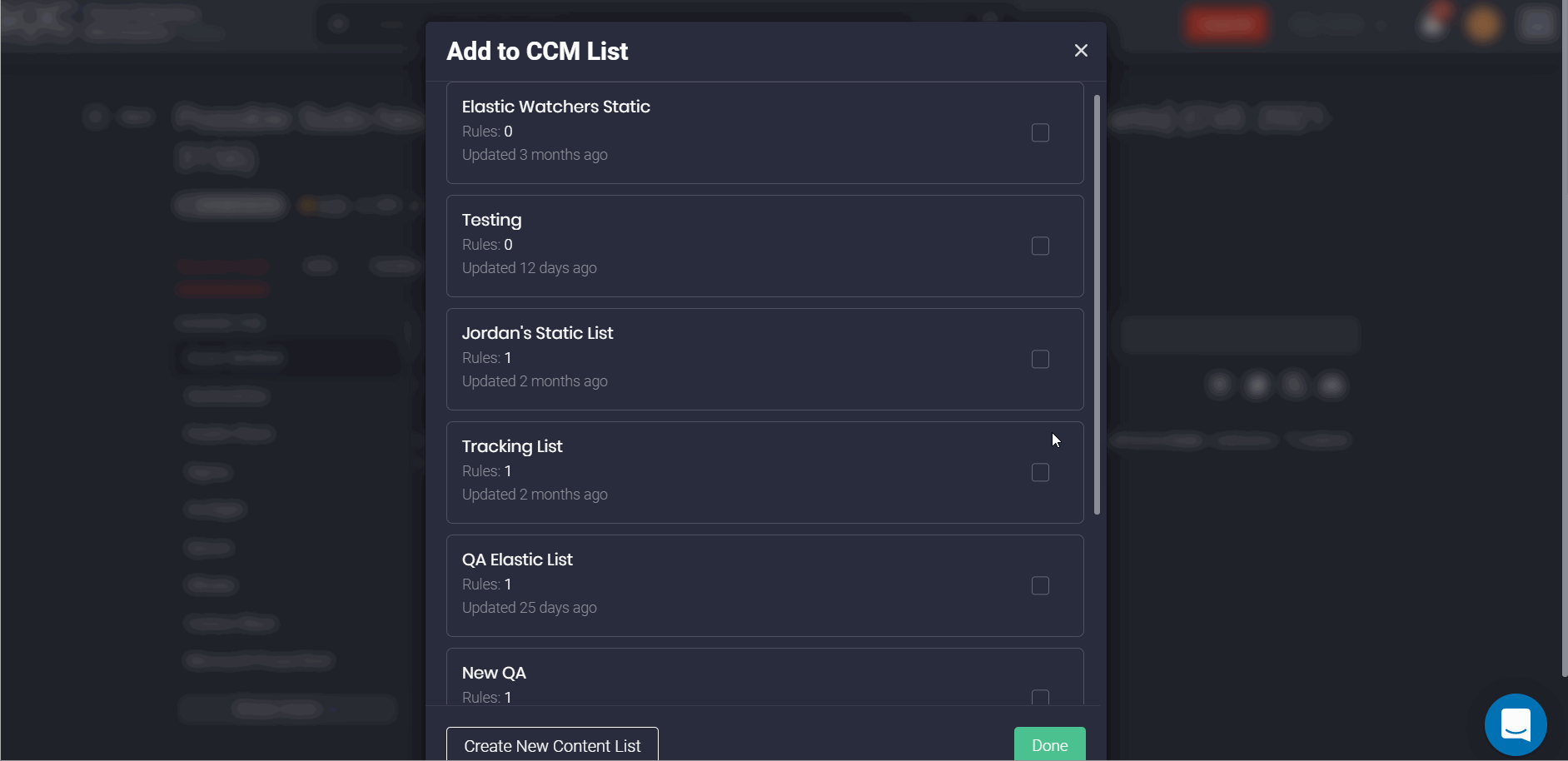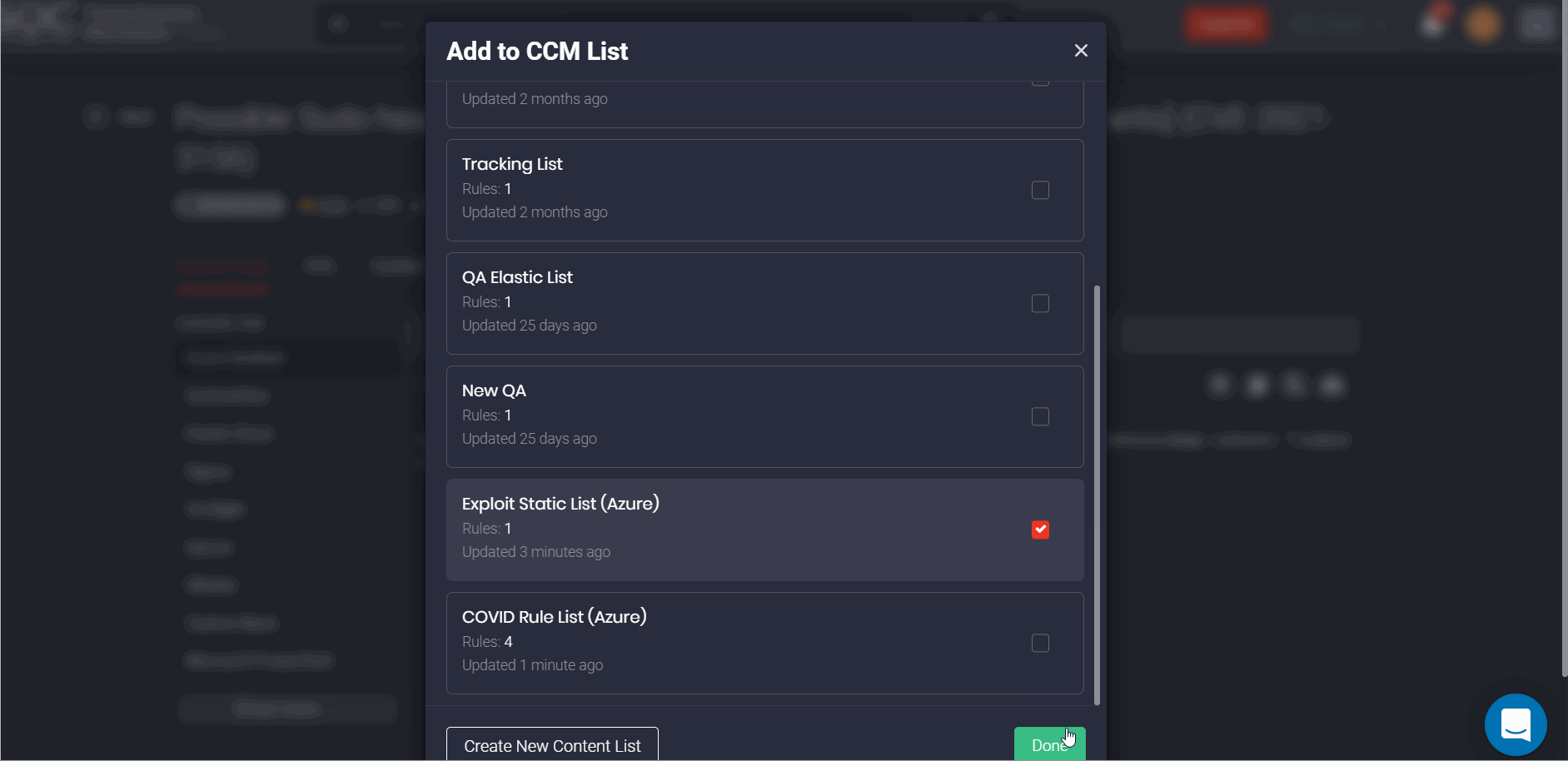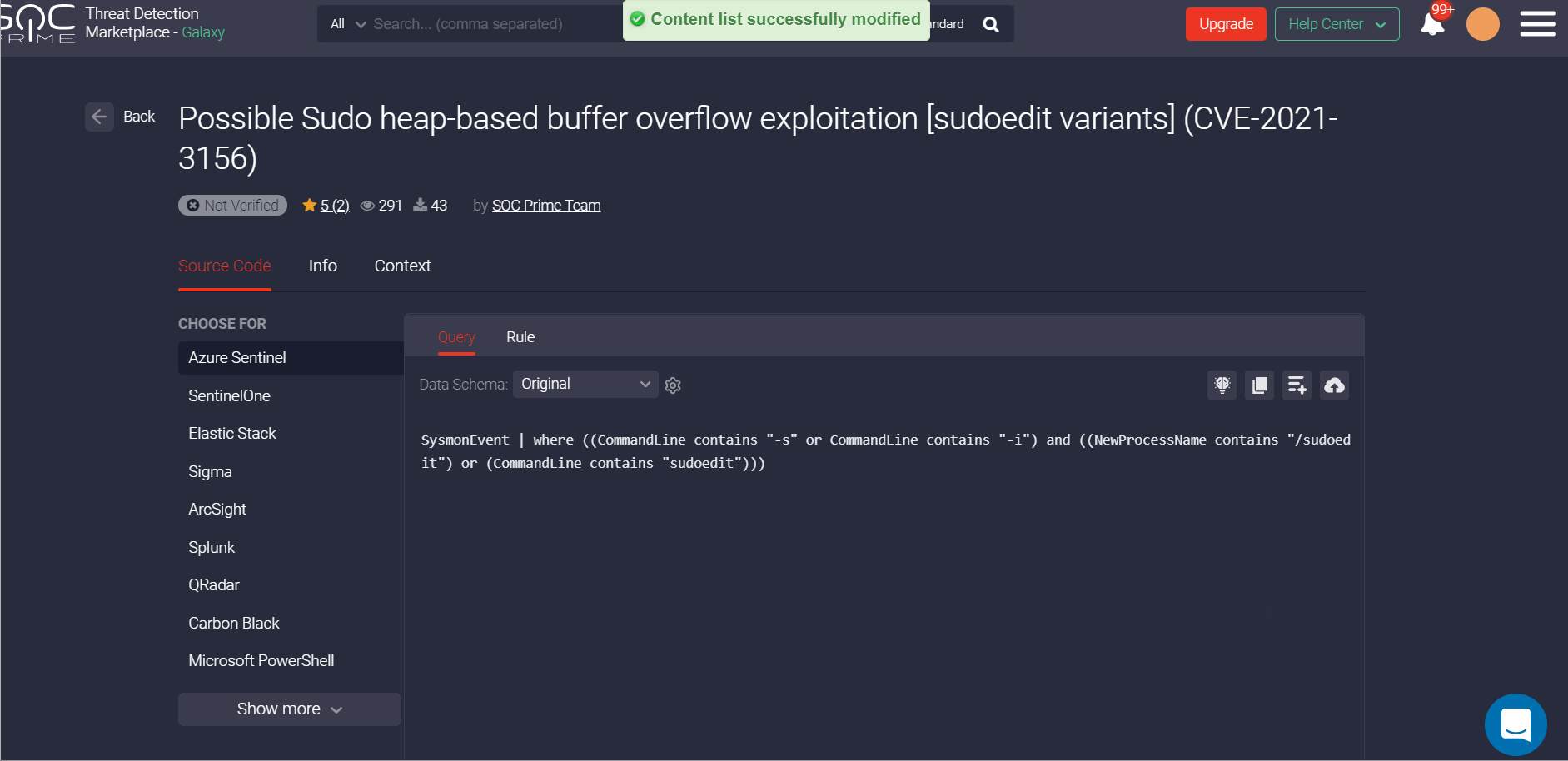
These changes also make it easier to add some specific content to the list from the content item page. By clicking the Add to CCM List button on the action panel, security performers will see the entire collection of lists that are not limited to only one platform. Before this latest update, only lists related to the specific platform and the selected content type were available for linking on the content item page.
Presets & Filters
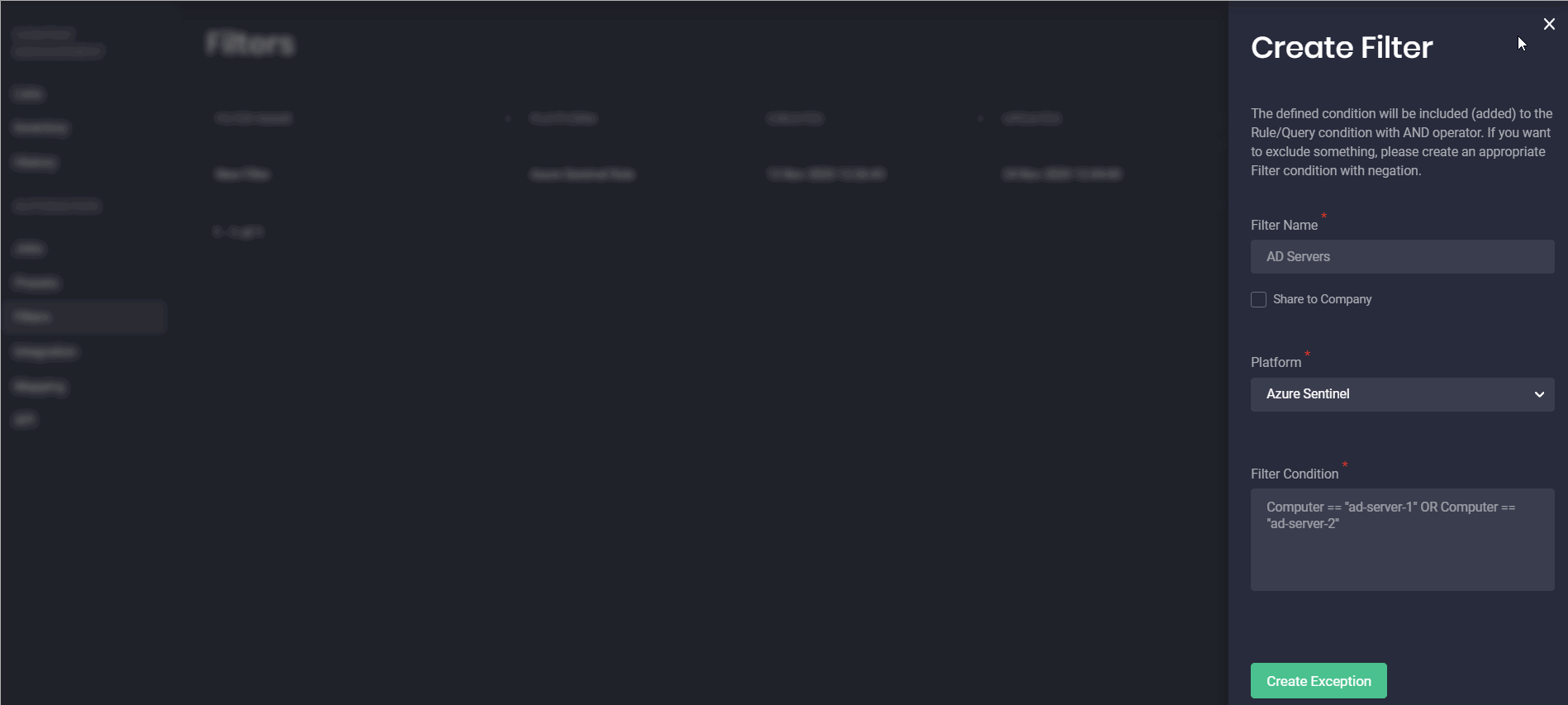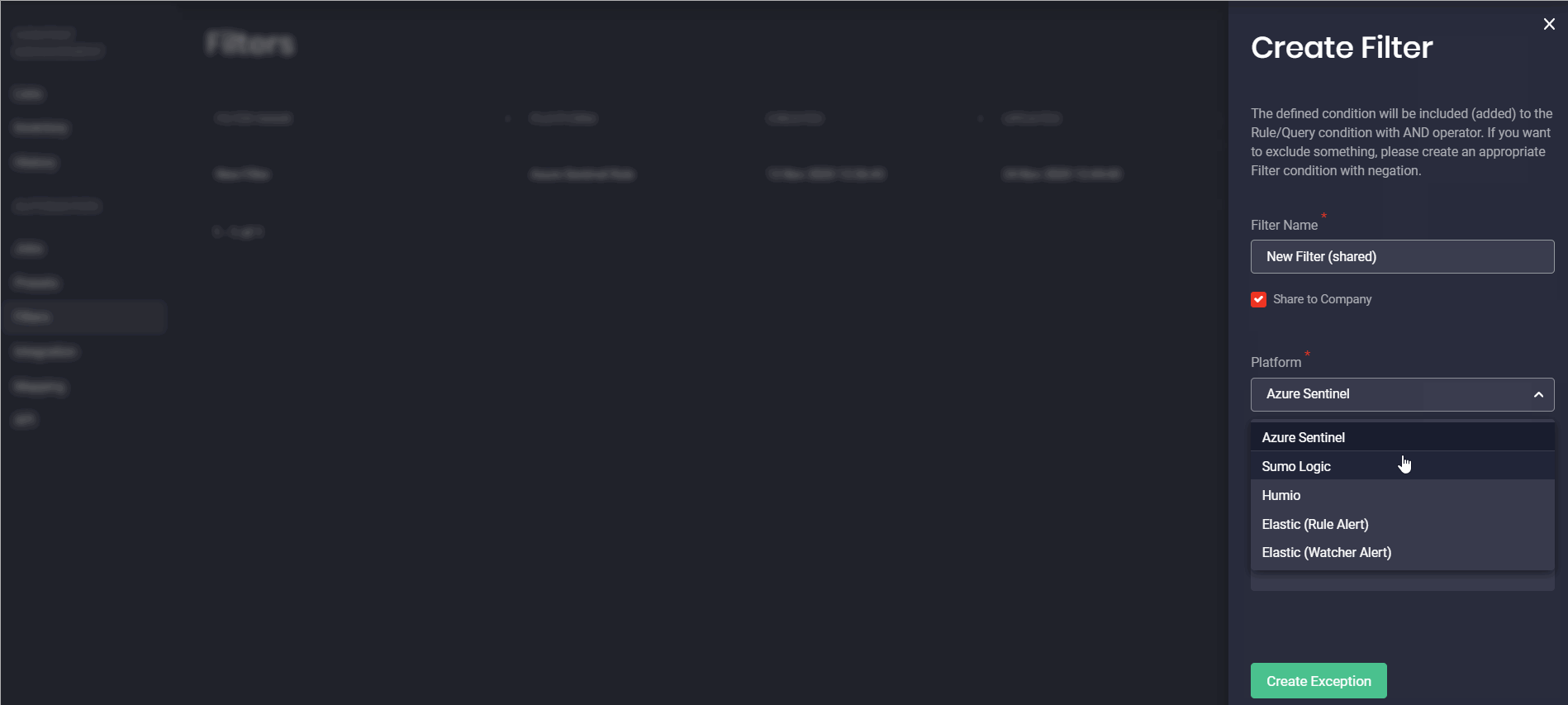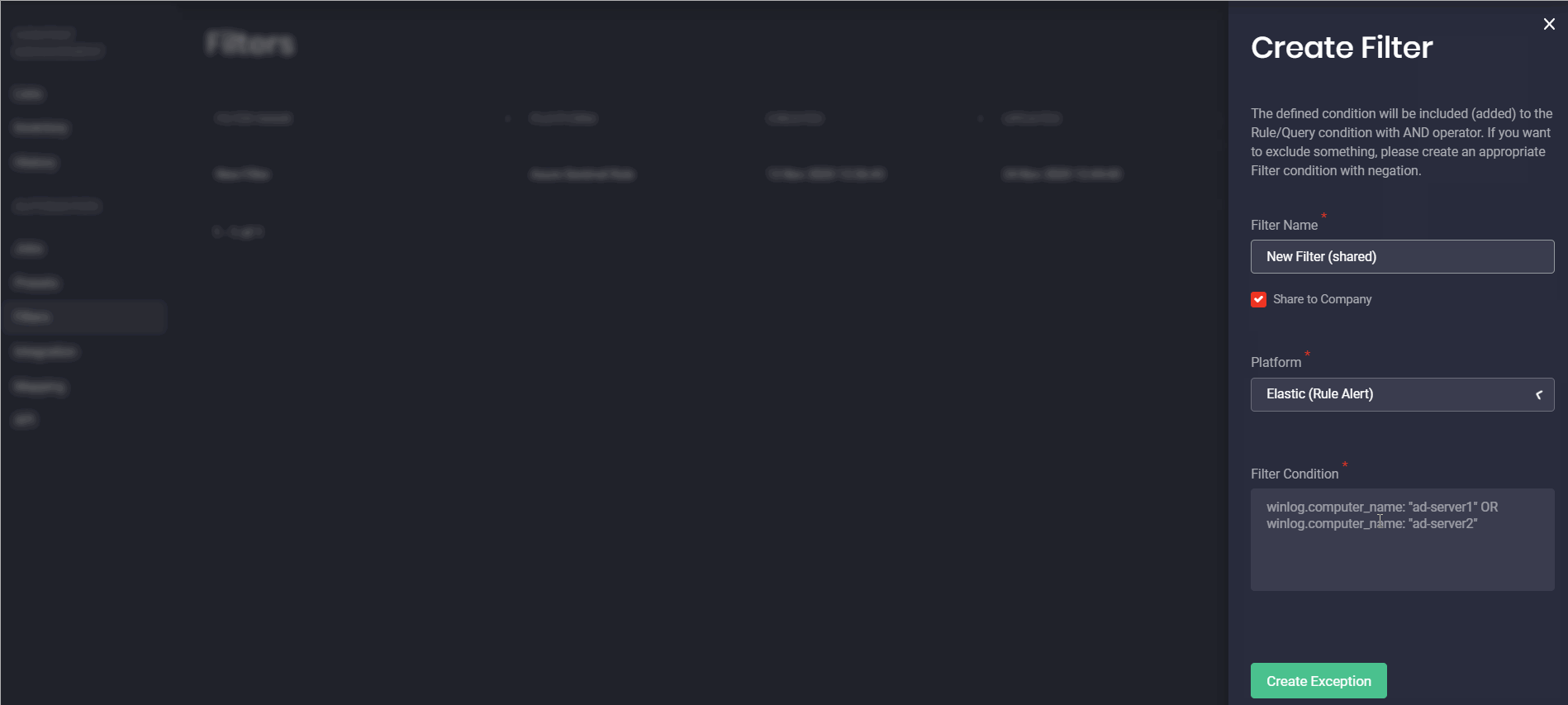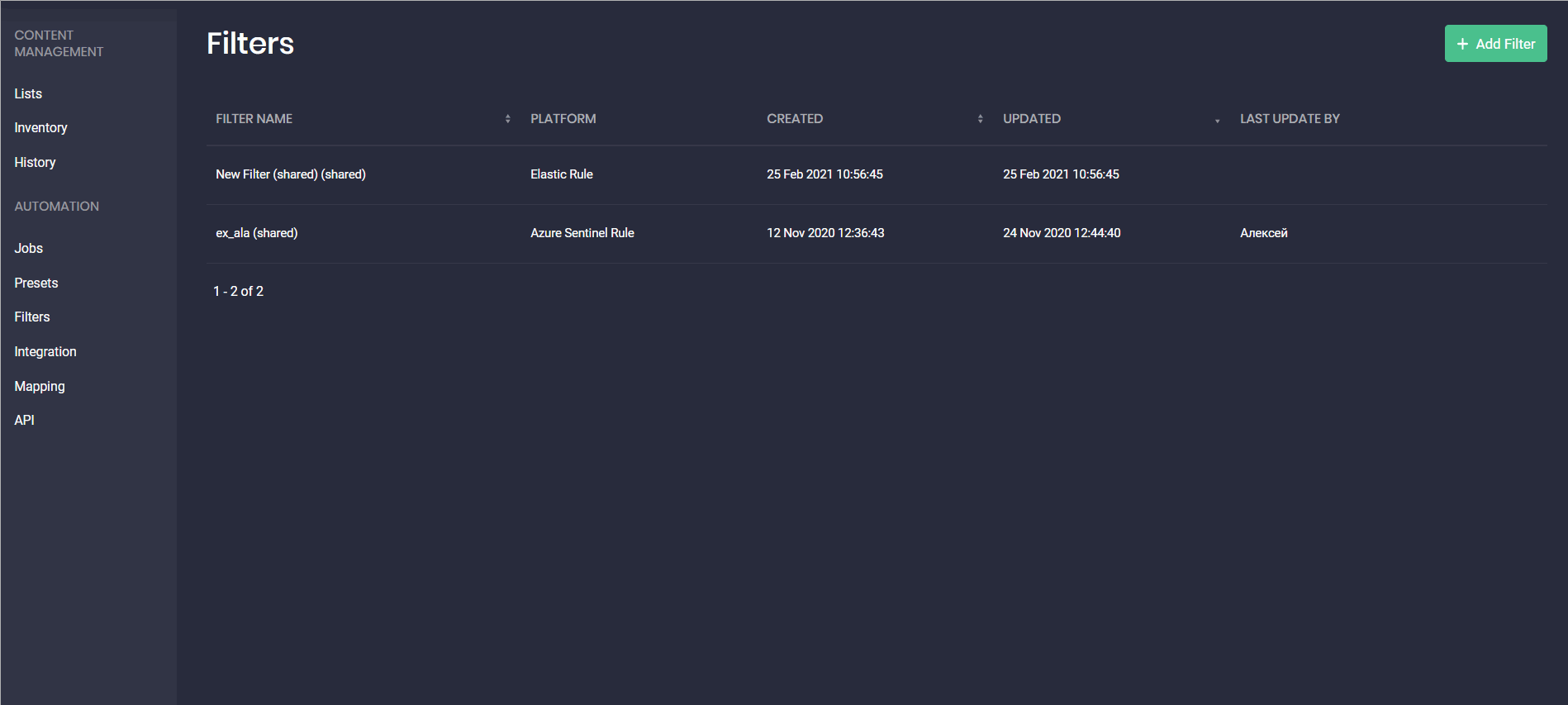
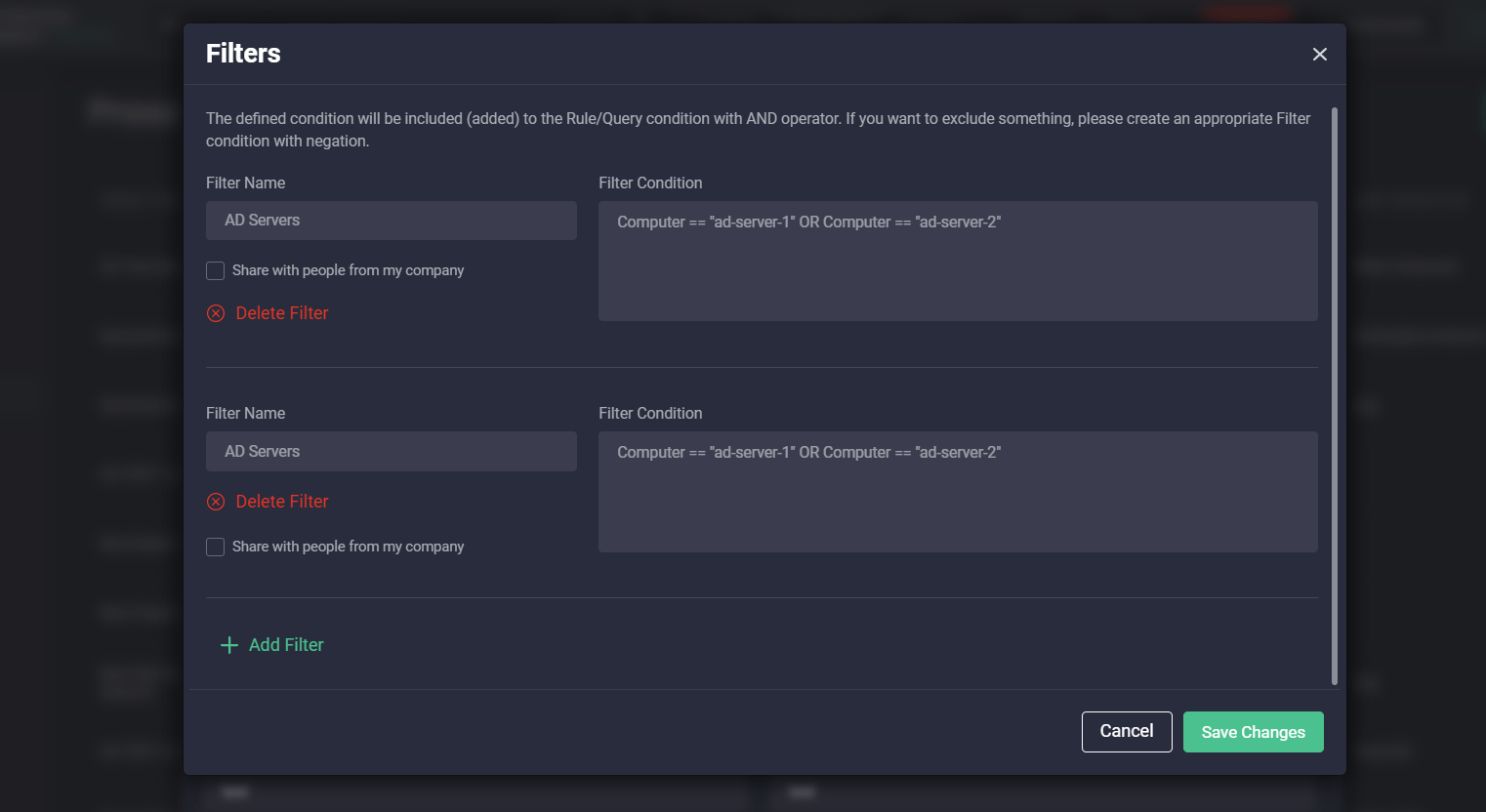
With this release, we’ve introduced the separate Filters page that can be accessed from the Automation menu item on the main navigation panel. For a more intuitive platform experience, “Exceptions” have been renamed to Filters.
Earlier security performers could set up Exceptions for various platforms only from the Presets pop-up by selecting the Exceptions (now called Filters) button in the upper right-hand corner or fill in the Filters field from the selected platform tab. But now, on the newly added Filters page, our customers can create filters for specific platforms and their available content types from scratch. Configuring filters for each platform and the related content type is getting even more streamlined with a unique placeholder. This placeholder is updated on the fly showing the pattern to be used for avoiding errors in the filter configuration for the specific language format.
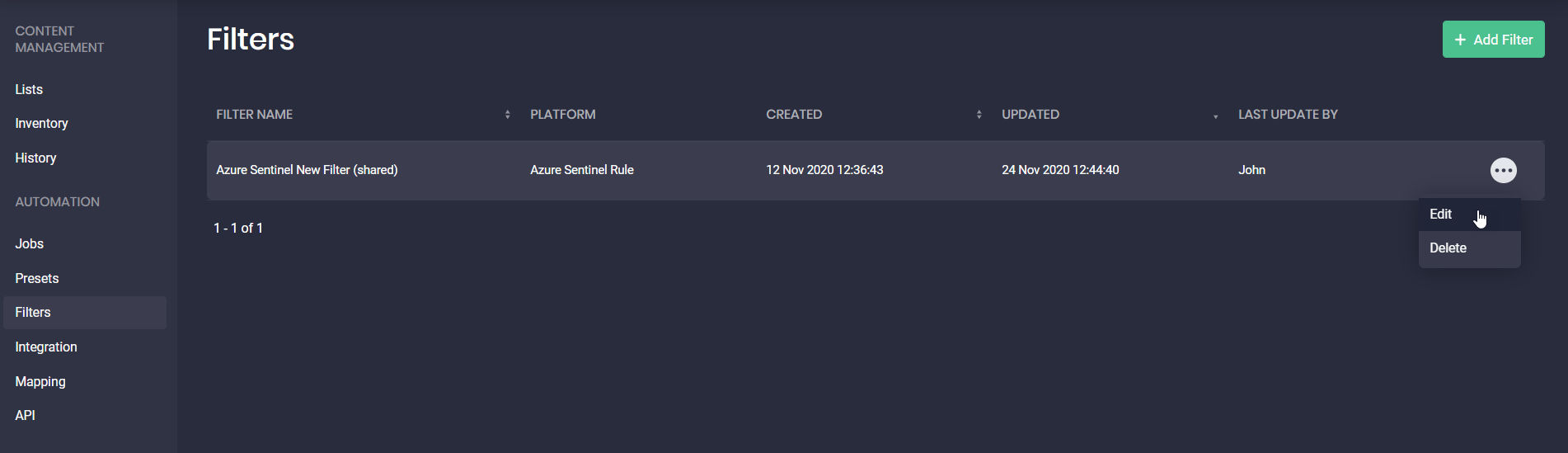
Configured filters can also be shared across the entire company by selecting the corresponding checkbox. Once saved, the Threat Detection Marketplace users can also make changes to the created filters on the fly by clicking the Edit button.
These pre-configured settings for the SIEM in use on the Filters page will then be automatically pre-populated when selecting the Presets pop-up for the corresponding platform this filter is linked to.
In addition, we’ve updated the logic for the Filters functionality on the back-end, which now works based on the AND operator by default.
Sign up for Threat Detection Marketplace, a world-leading Detection as Code platform that provides detection, enrichment, integration, and automation algorithms to support security performers while translating big data, logs, and cloud telemetry into cybersecurity signals. Want to craft your own Sigma rules and support the global threat hunting community? Join our Threat Bounty Program!