Threat Detection Marketplace 4.4.3 Is Released

On February 25, 2021, we released version 4.4.3 of Threat Detection Marketplace to provide our customers with an even more streamlined and smooth experience while using our content-as-a-service (CaaS) platform. The latest release introduces translation enhancements, implements new Intercom service, pushes the Dashboard page redesign as well as fixes minor bugs and inconsistencies.
Translation Enhancements
With this latest release, our SOC Prime Team introduced a number of major cross-platform translation improvements. First of all, we’ve added the ability to download various content items available for the Corelight security solution in the appropriate file formats, including json, ndjson, or as other acceptable extensions. Before this improvement, all detections translated to the Corelight language format were downloaded as files with the single yml extension, which caused translation issues. Apart from Corelight, we’ve made improvements to translation logic and field mapping for the SentinelOne security solution.
Additionally, our team thoroughly reviewed all translations of Sigma rules to various language formats and added support for Chronicle Security and FireEye Helix to Uncoder.io, SOC Prime’s online translator for SIEM saved searches, filters, queries, API requests, and correlation. Furthermore, we’ve improved Sigma rule translations to the X-Pack Watcher format and other language formats when the Sigma rule includes the product: zeek logsource and condition: aggregation / timeframe, which caused a translation error.
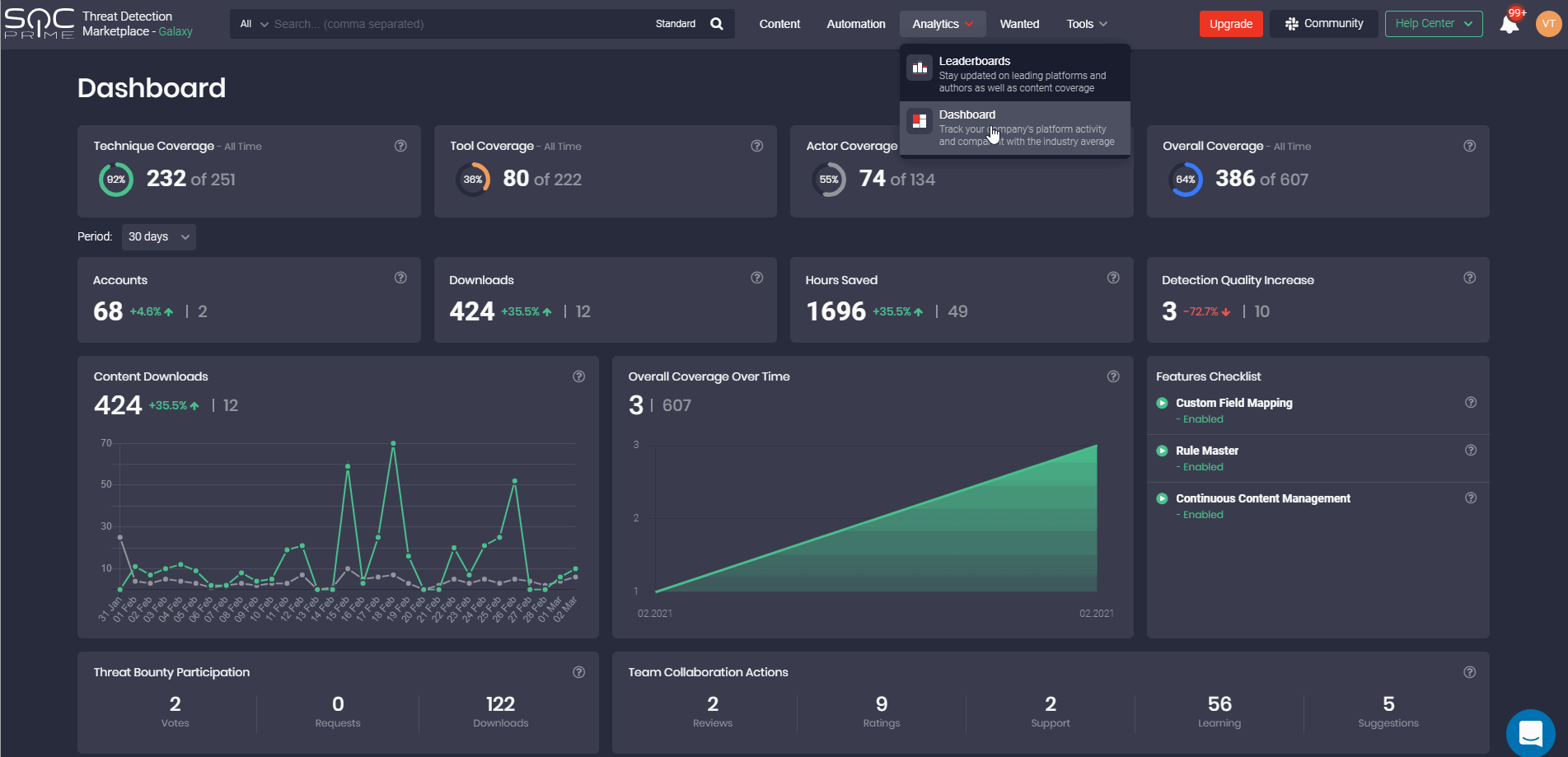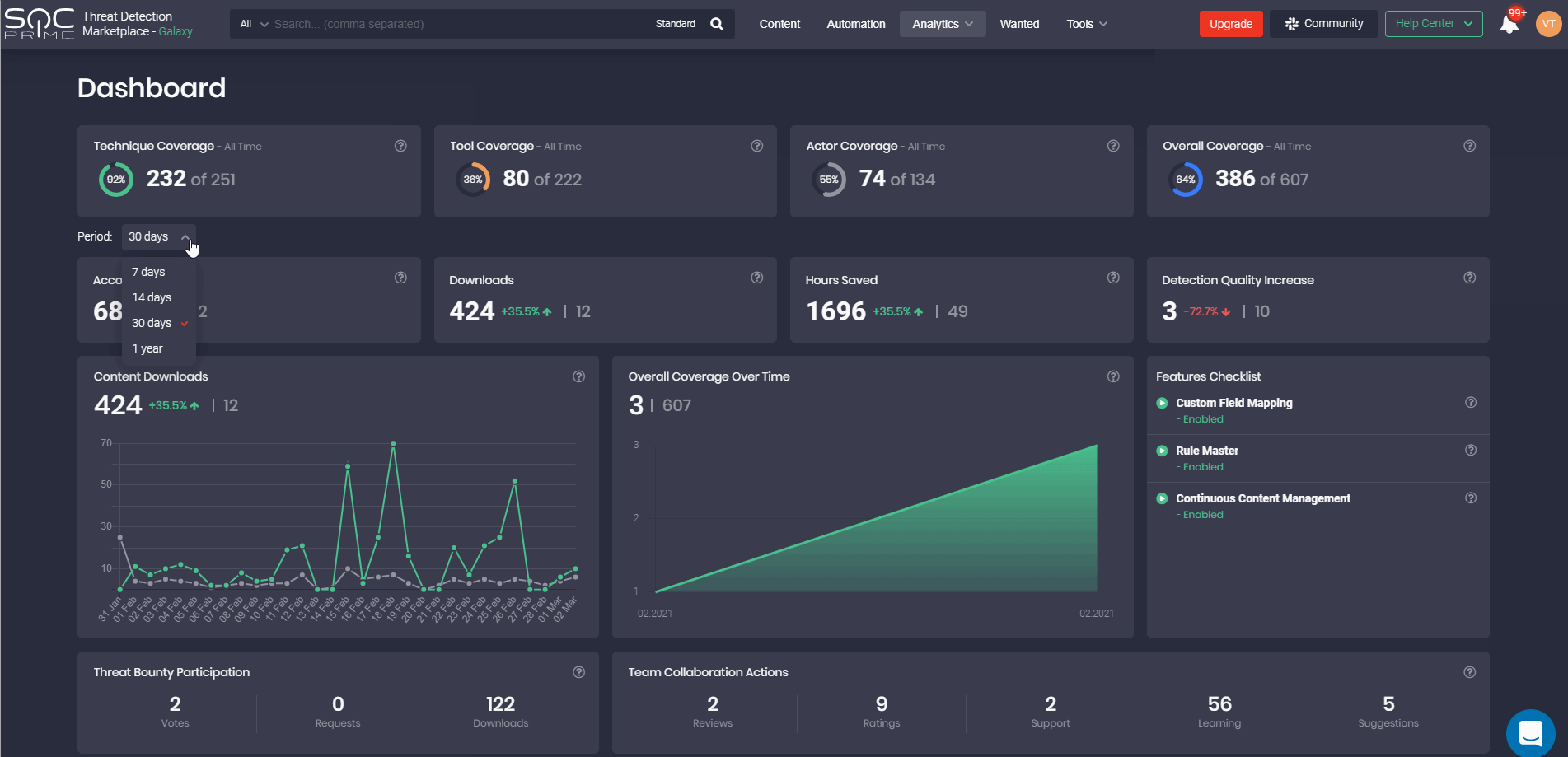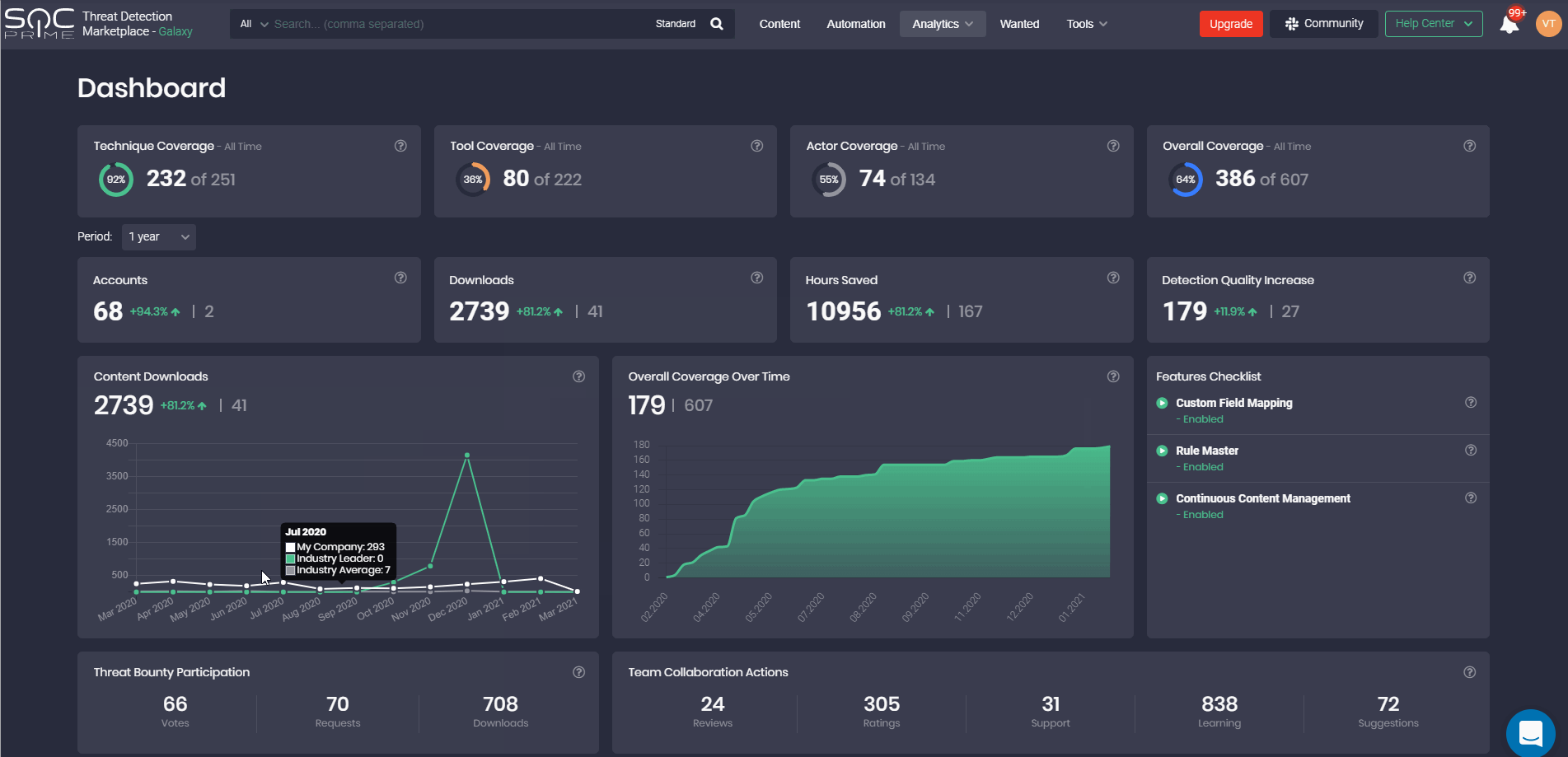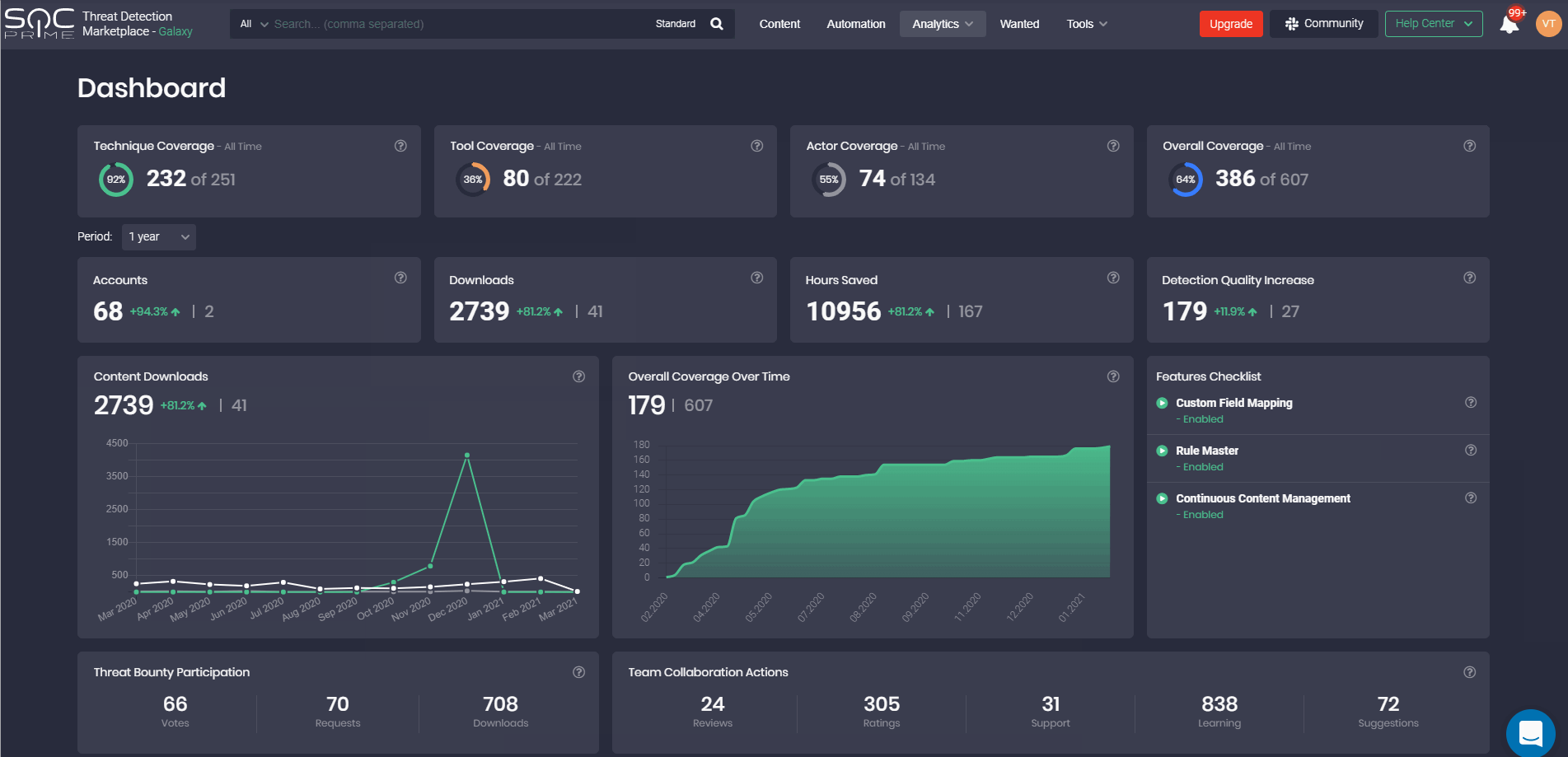
Dashboard
The latest Threat Detection Marketplace update brings in the Dashboard page redesign to make it consistent with the new look and feel we’re gradually applying to the entire platform functionality.
These platform experience improvements are as follows:
- Localization improvements to the page sections with the company’s platform activity analytics
- New Content Deployments section that reflects the amount of content deployed to the SIEM instance using the Continuous Content Management (CCM) module
- Separate charts displaying the MITE ATT&CK® coverage, including:
- Techniques
- Tactics
- Tools
- Actors
- Improved animation for charts
- Improvements to the drill-down tables displaying the details of each section statistics
Intercom Integration
With this release, we’ve completed the integration of Threat Detection Marketplace with the Intercom service, which streamlines communication between the SOC Prime representatives and our users. From now on, when chatting via Intercom, the Threat Detection Marketplace users do not have to introduce themselves each time they need to reach out to us. What’s more, our SOC Prime Team representatives can directly contact the users even if they haven’t used the Intercom chat before, which adds a personal touch to mutual communication and helps solve any issues regarding the platform experience much easier and faster.
To be in sync with these changes, we’re also updating our Privacy Policy including the details of the Intercom service integration and how it affects the collection of users’ contact and social information. Threat Detection Marketplace users will be notified of all the related updates.
Join Community Button
To boost the power of the community, we’ve added the Join Community button to the main navigation panel that leads to the dedicated Slack space where security enthusiasts who have signed up for our Detection as Code platform can have live discussions on the most topical cybersecurity issues and learn what’s new in Threat Detection Marketplace.
Note: This button along with the Content Sales button won’t be available for the Limited Access subscription. To join our Community Slack space, security performers are welcome to change their email address to the corporate one and upgrade to the Community subscription for free.
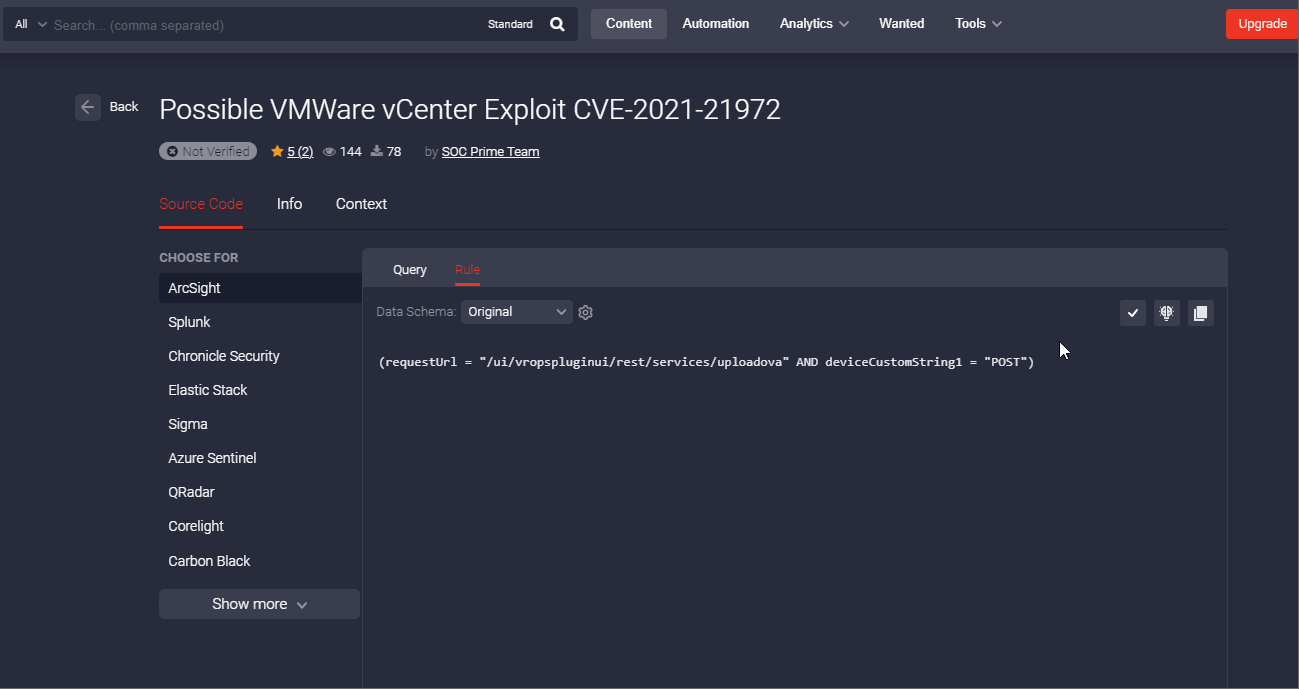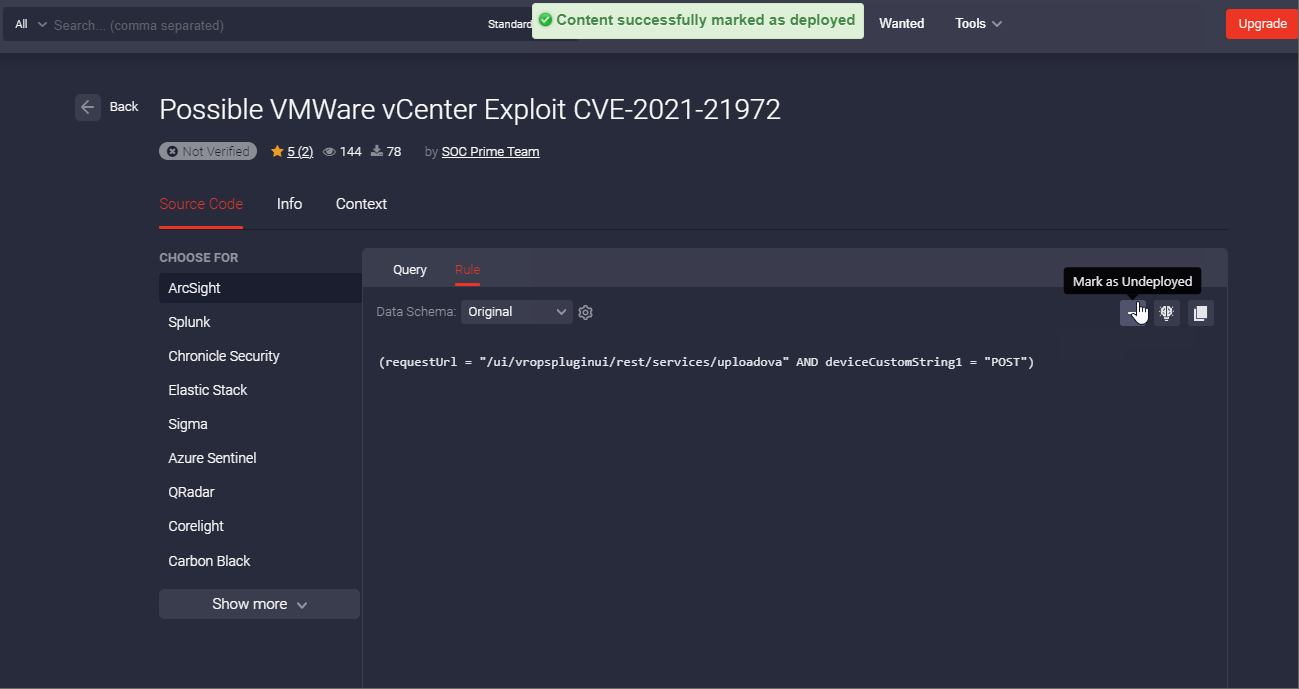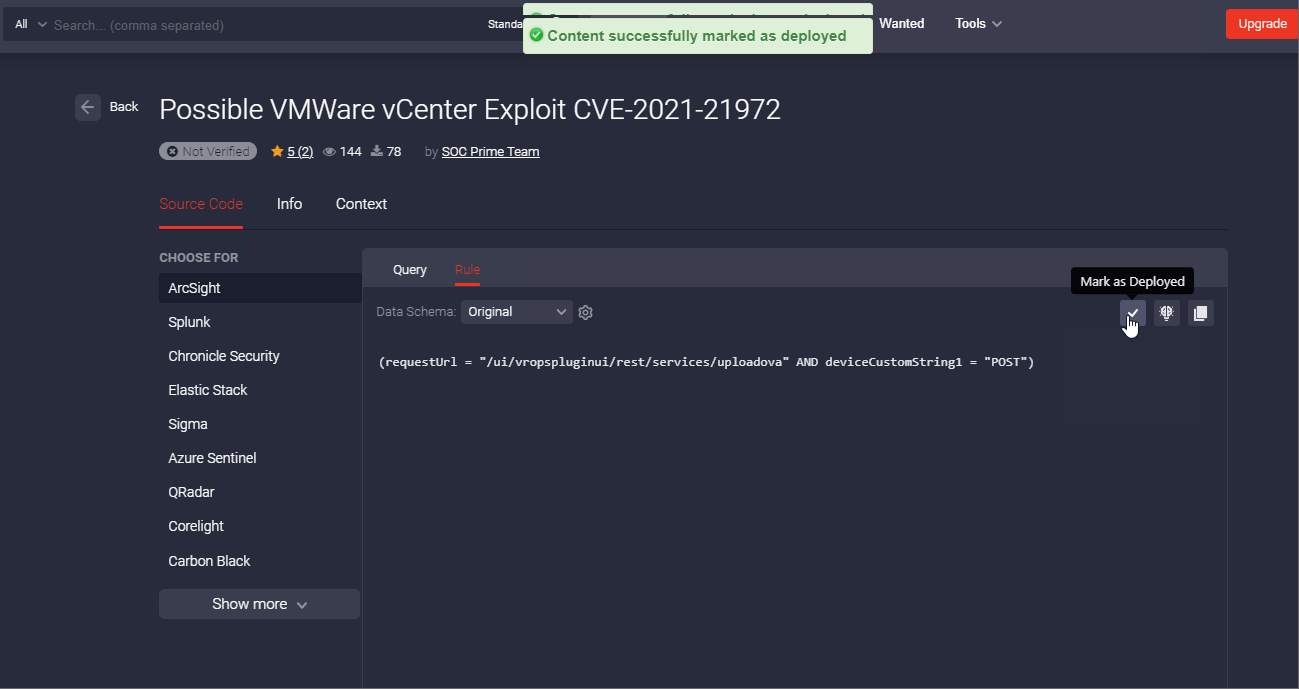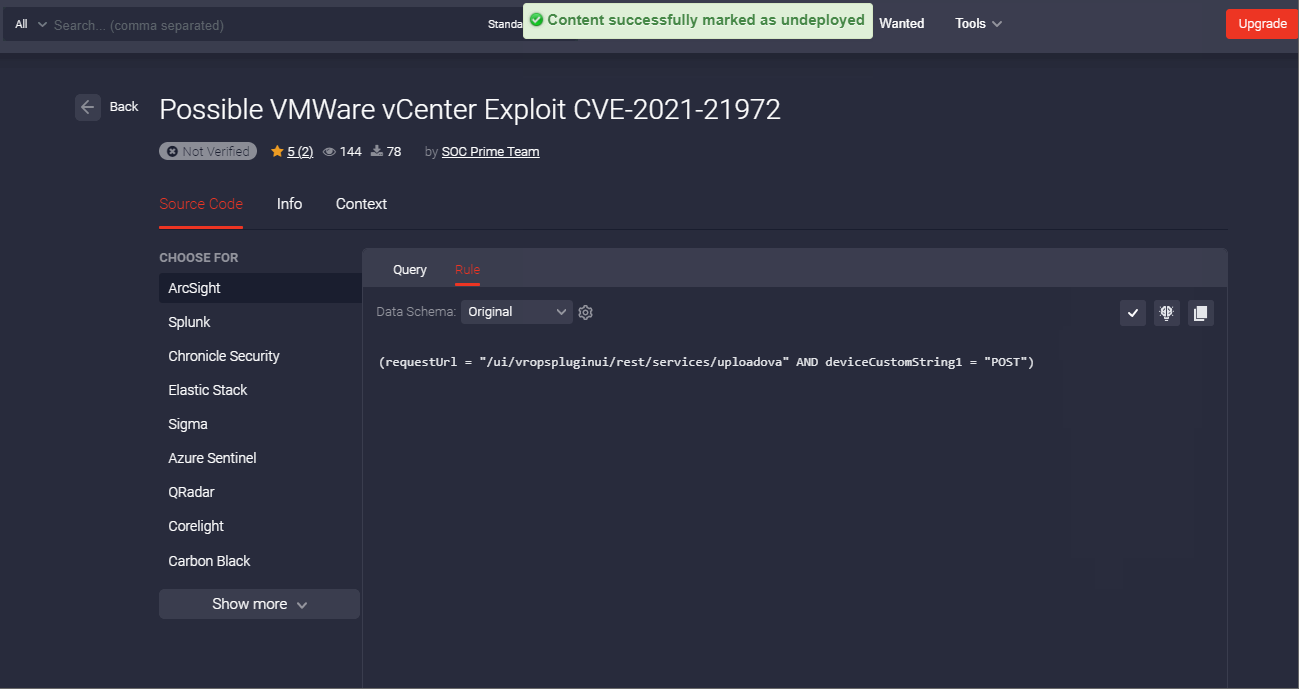
Marking Rule as Deployed
With each Threat Detection Marketplace release, we’re striving to improve the threat hunting experience for our security practitioners. We’ve recently enriched our action panel on the Rule page with one more button that allows marking the related content item as deployed when added to the user’s SIEM, EDR, or NTDR instance. After successful deployment of this content item to the security tool in use, the content will be automatically marked as deployed displaying the corresponding checkmark icon and tooltip.
Once marked this way, the corresponding rule will be also identified on the Content item page by the Deployed icon. The user can still update this status manually if the content item was deployed a long time ago and might be outdated. By clicking the checkmark icon, it will change to a minus icon and the icon tooltip will display “Mark as Undeployed” accordingly.
Subscription Updates
With this release, we’ve made updates to the Limited Access subscription. Now users with this Freemium subscription plan will see pop-ups prompting them to upgrade to the Community subscription by changing their personal email address to the corporate one. These pop-ups will appear when they try to access the following functionality:
- API
- Custom Field Mapping
- Continuous Content Management
In addition, we’ve removed the Try button for users with the Limited Access subscription when they attempt to access the above-mentioned functionality. The Limited Access subscribers will also see the corresponding pop-ups when trying to access Rule Packs, Configs, Premium Apps, and Playbooks.
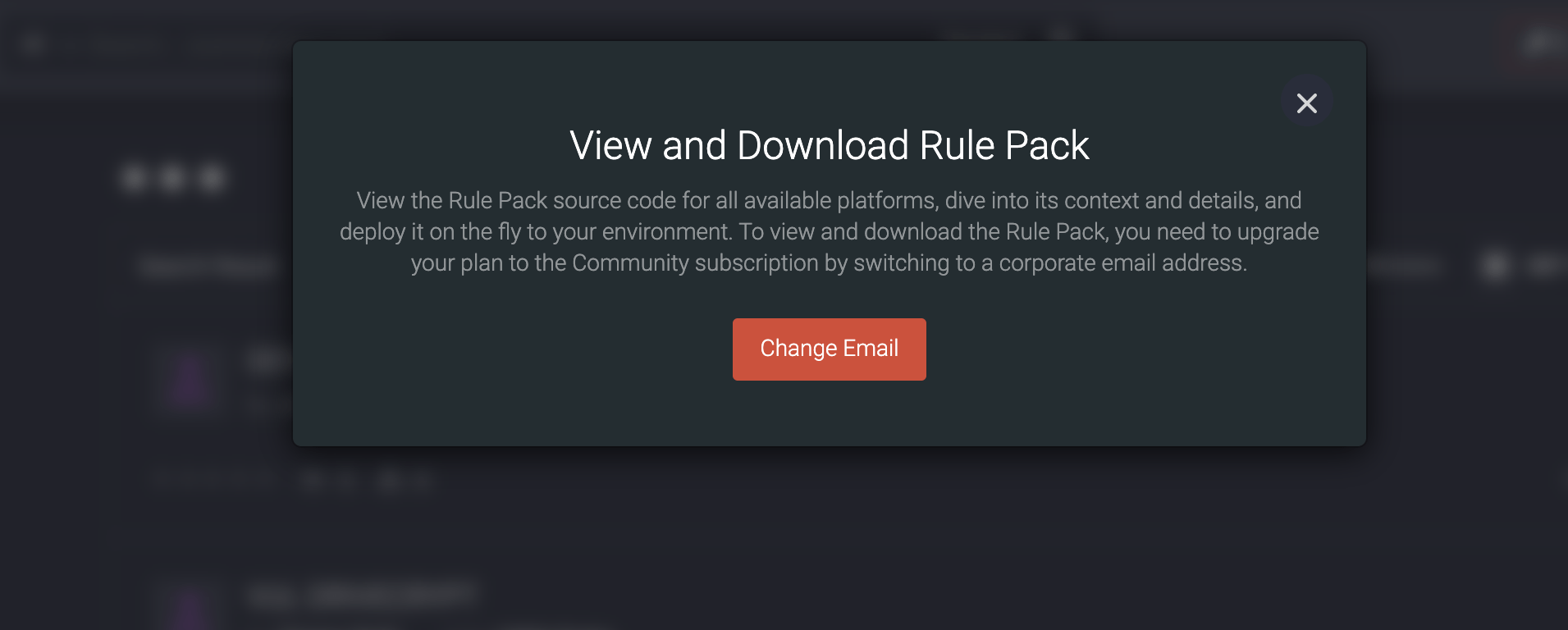
Also, we’ve made crucial improvements to the Community Access subscription privileges that have significantly affected the CCM module and content available only for paid subscribers. The CCM module is still available as part of Free Trial or as a separate license, however, starting from this release, CCM doesn’t offer full access to all Exclusive content to prevent breach of subscription privileges. To gain full access to all Exclusive content on our platform, you can upgrade to the Premium subscription with unlimited CCM module privileges.
Key Bug Fixes & Improvements
With the Threat Detection Marketplace update as of February 25, 2021, the SOC Prime Team introduced a number of improvements to smooth the experience with our Detection as Code platform.
The list of bug fixes are as follows:
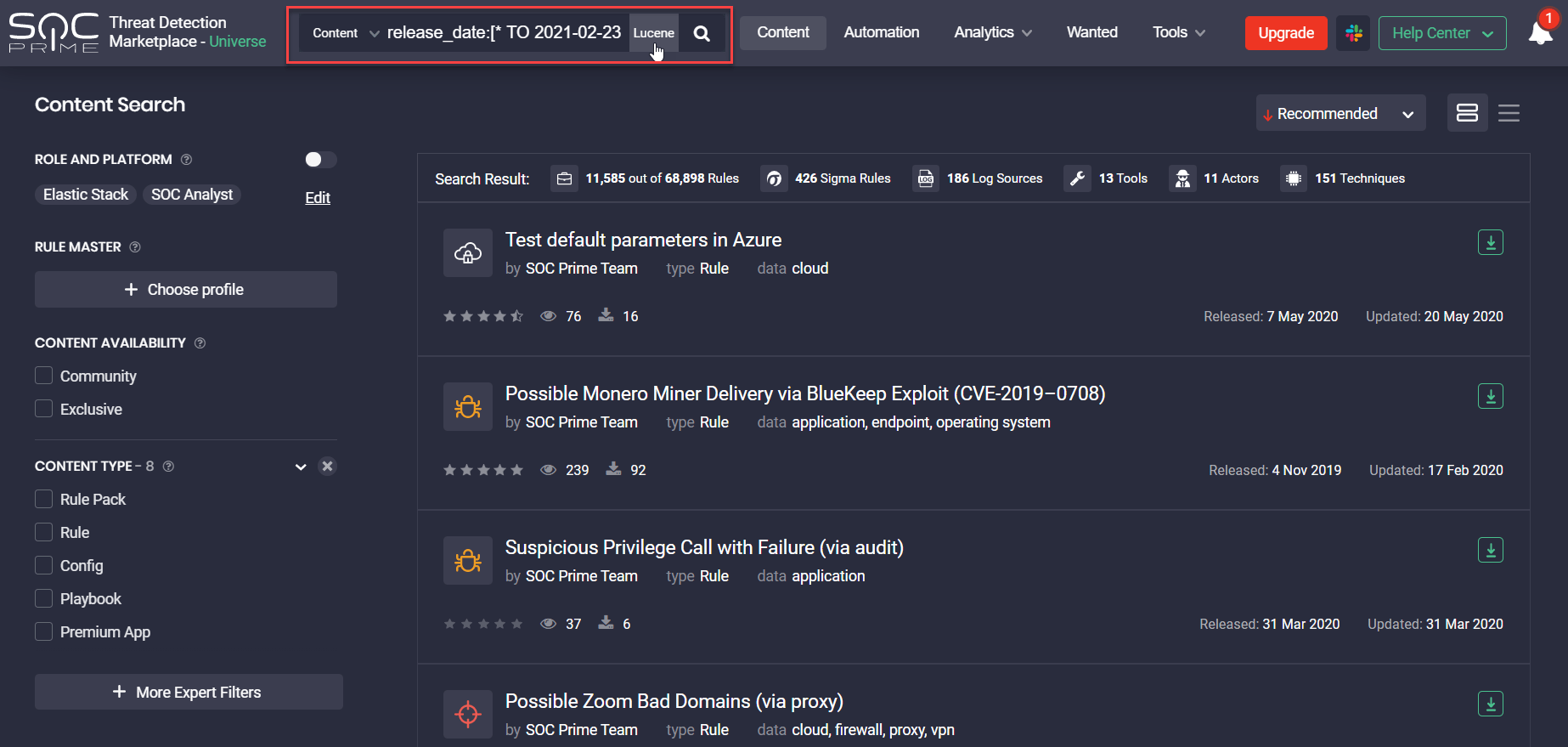
- Fixed the issue with proper content filtering by the Year date range on Leaderboards > Top Platforms chart.
- Fixed the issue with drilling down to the list of content items developed by the specific author(s) from Leaderboards > Top Authors chart filtered by All Time. The issue involved causing an error due to the search using the related Lucene query:
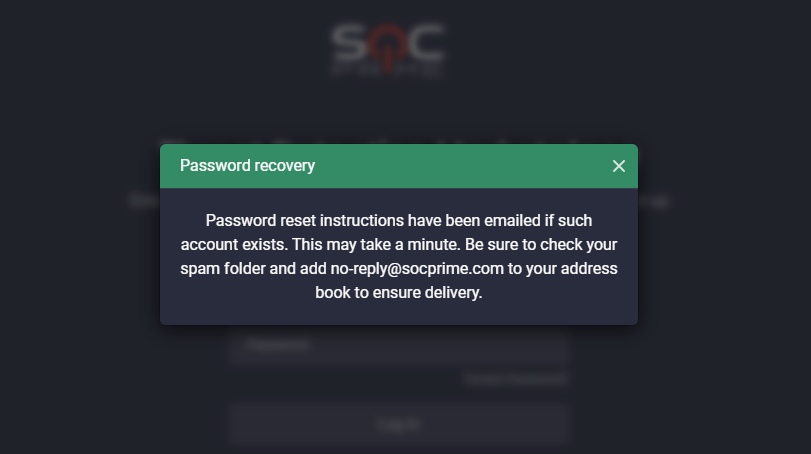
3. For security purposes, replaced the password recovery pop-up notification with the more specified message adding a condition that the action is relevant if the user account exists:
4. Updated the email text that allows unlocking Exclusive content developed by the SOC Prime Team only rather than all detections whose authors include the Threat Bounty Program members.
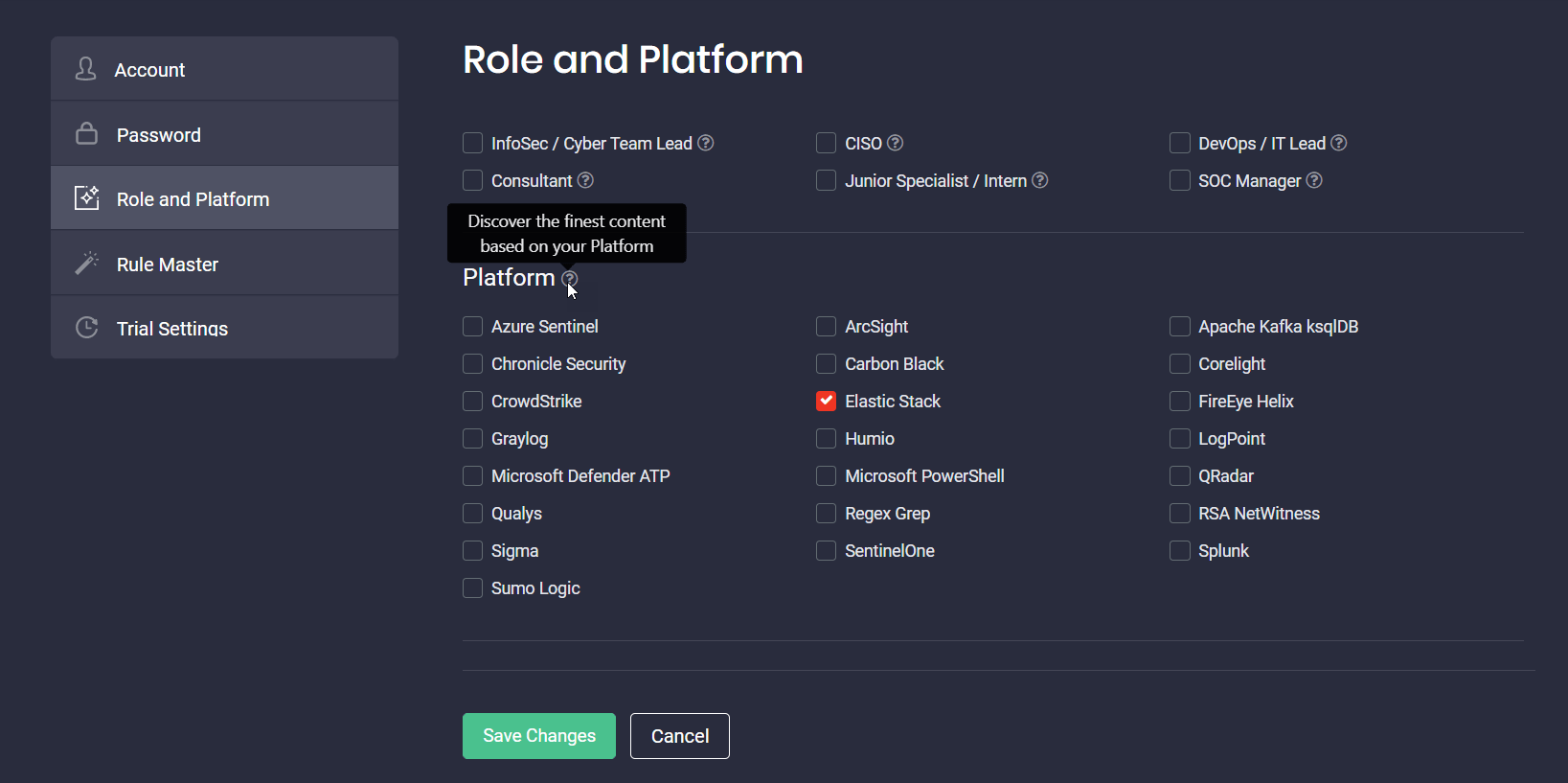
5. Made localization improvements to the Platform section for a more intuitive platform experience:
-
- Updated the tooltip text
- Improved an error message that appears when the platform hasn’t been selected
6. Fixed issues with the search suggester on the MITRE ATT&CK page that couldn’t find the appropriate Technique data by clicking the following matching fields:
- mitigation
- detection
- description
7. Fixed the issue with the user’s opting out of receiving notifications related to content releases and updates, which automatically disabled crucial system notifications sent via email, like:
- Email address update
- Password update
- OTP code receipt
- Information on the Free Trial activation of a certain feature, etc
Sign up to Threat Detection Marketplace to reduce the meantime of cyber-attack detection with the 96,000+ SOC content library that aggregates rules, parsers, search queries, Sigma and YARA-L rules easily convertible to various formats. Want to enrich the content base and create your own detection content? Join our Threat Bounty Program for a safer future!


