SOC Prime’s Innovation for Collaborative Cyber Defense

Technical Highlights of the New SOC Prime Platform
On September 14th, SOC Prime launches the platform for collaborative cyber defense, threat hunting, and threat discovery. The platform helps to detect threats easier, faster, and simpler by leveraging the de facto industry standard for Detection as Code languages (Sigma and Yara-L), the cutting-edge dynamically prioritized MITRE ATT&CK® v9 framework, global crowdsourcing Threat Bounty program, automated integration with major SIEM, EDR & XDR technologies, and most importantly, feedback and vetting by the rapidly growing cybersecurity community of 19,000+ people from 155 countries.
SOC Prime’s Collaborative Cyber Defense platform is built on the foundations of Threat Detection Marketplace and powered by new intelligence-driven capabilities to take your cybersecurity experience to the next level. Now, you can instantly hunt for the latest threats within 20+ supported SIEM & XDR technologies and boost the awareness of all the latest attacks in the context of exploited vulnerabilities and MITRE ATT&CK matrix. Streamline your security operations, while getting anonymized feedback from the global cybersecurity community and automatically generating metrics and trends on your team’s performance.
SOC Prime Platform: What’s New
The SOC Prime platform introduces a set of new capabilities, or Elements, such as Uncoder CTI (for Cyber Threat Intelligence), Quick Hunt, real-time Log Source Coverage and MITRE ATT&CK Coverage dashboards, as well as content enhancements and more opportunities for sharing feedback across the community.
Navigation
The home screen of the platform serves as a navigation page for all of its elements, grouped by core tasks.
Discover
Discover threats challenging your organization with the world’s largest SOC content and security intelligence repository, Threat Detection Marketplace. It enables the delivery of detections of critical threats within 48 hours after their discovery, which checks with the “small window” before exploitation in the wild.
The collection of 130,000+ qualified, cross-vendor, and cross-tool detections is aligned with the MITRE ATT&CK framework. Notably, the content library is powered up with the crowdsourcing initiative of a global community of 300+ threat hunters and security researchers who contribute new and improve the existing detection content every day, ensuring extensive threat coverage and continuous detection quality increase.
Threat Detection Marketplace integrates with 20+ SIEM & XDR platforms to ensure on-the-fly content translations and full customization from the generic languages, like Sigma and YARA-L, to the SIEM-native format.
Three different types of content visualization allow searching for detections much faster and easier while aligning the search with your primary needs and preferences. Additionally, security performers can track the content growth, cross-tool translation maturity, and improved threat coverage as per the MITRE ATT&CK matrix with the dedicated Leaderboards for crisp visualization of the key platform stats.
Hunt
Driving beyond the content itself, we have built a set of new tools for threat hunters that can be used on a daily basis to maximize the efficiency of TTP-based tactical hunts and enable collaboration with Cyber Threat Intelligence teams.
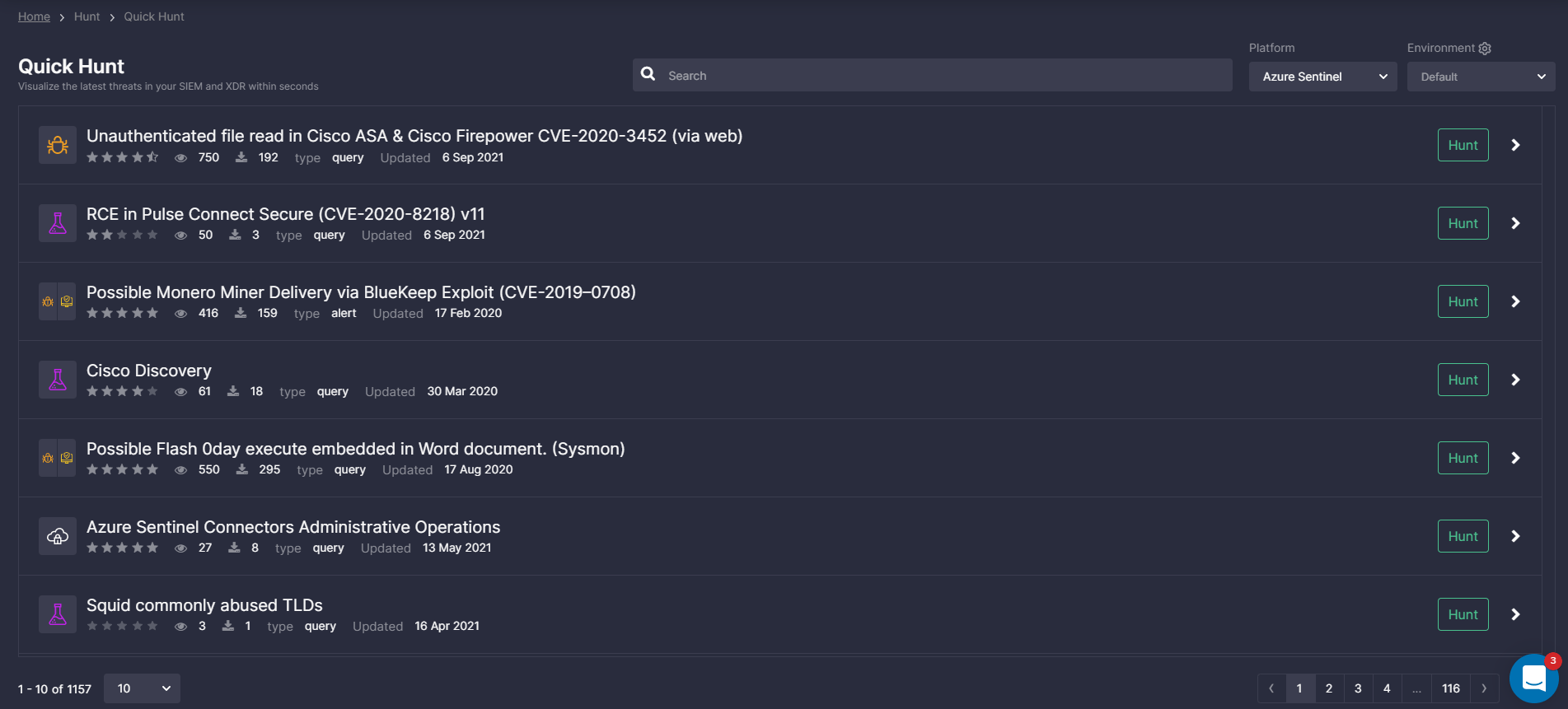
Quick Hunt
Quick Hunt can help anyone do better in Threat Hunting while streamlining threat investigation and improving operational efficiency. It provides a fast, easy, and community-driven means to learn about the latest threats, understand their context, prioritize, and start searching for them right away in their SIEM & XDR with a single click.
As many companies do not have the dedicated Threat Hunting and Cyber Threat Intelligence teams, the capability to hunt for the latest exploits, new ATT&CK techniques and tools, as well as major APT campaigns has long been scarcely available. Now, security teams can save time and money on their regular hunting procedures and go straight to the validation of hunting hypotheses, finding compromised users and assets, revealing suspicious activity, and known bad behavior. These queries are adapted to your data schema on the fly and come from the world’s largest pool of 130K+ TTP-based behavior detection algorithms updated daily and vetted by the global community of 19,000+ people. Quick Hunt supports Google Chronicle, Microsoft Azure Sentinel, Splunk, Humio, CrowdStrike, and Elastic (commercial stack, cloud, and open-source) as destinations for hunting.
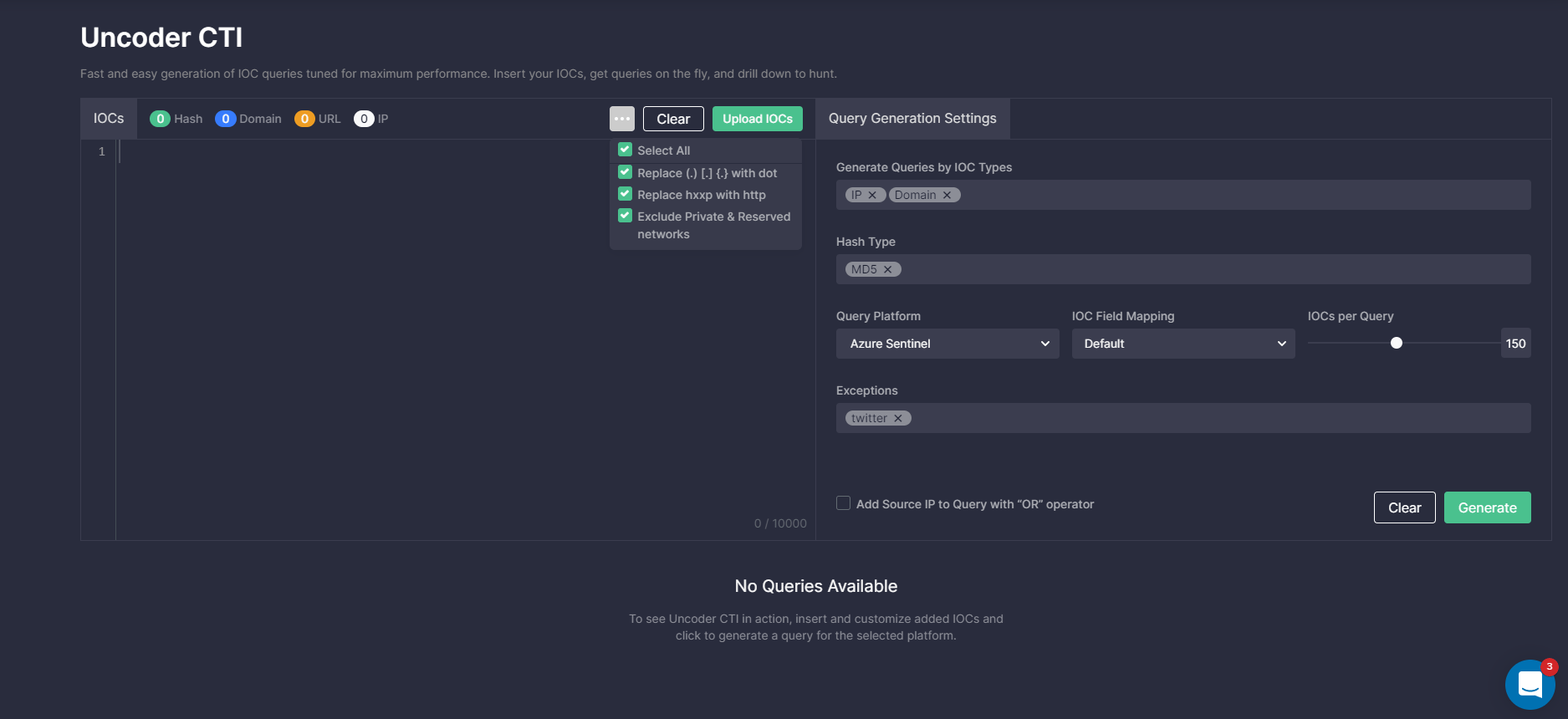
Uncoder CTI
Uncoder CTI is built for threat intelligence specialists and threat hunters to make IOC matching more streamlined and accurate. Grab IOCs and shape them to generate custom, performance-optimized IOC queries ready to run in your SIEM and XDR in just 2 clicks. Uncoder CTI can also remap the default parameters to your specific data schema on the fly to overcome any data normalization limitations or parsing challenges. Moreover, you can automatically add exceptions to decrease the number of false positives, such as 8.8.8.8 IP, private subnets, or other typical CTI report errors that create noise and reduce search performance.
Manage
Having curated detection content and solutions to improve threat hunting operations at hand, organizations require more advanced tools to manage these processes. Elements under the Manage section help to track the metrics on log sources and MITRE ATT&CK, making them dynamic, live, and easy to prioritize.
Log Source Coverage dashboard shows the detection content stats for a certain log source that is taking X amount of data costs. While today such metrics are usually tracked in the spreadsheets, the reality is much more complex. As a result, keeping the information up to date blocks a large amount of time for security teams. With elements under the Manage section, you can easily monitor the Log Sources coverage with relevant content, based on the manual download history and automated API deployments from the SOC Prime platform.
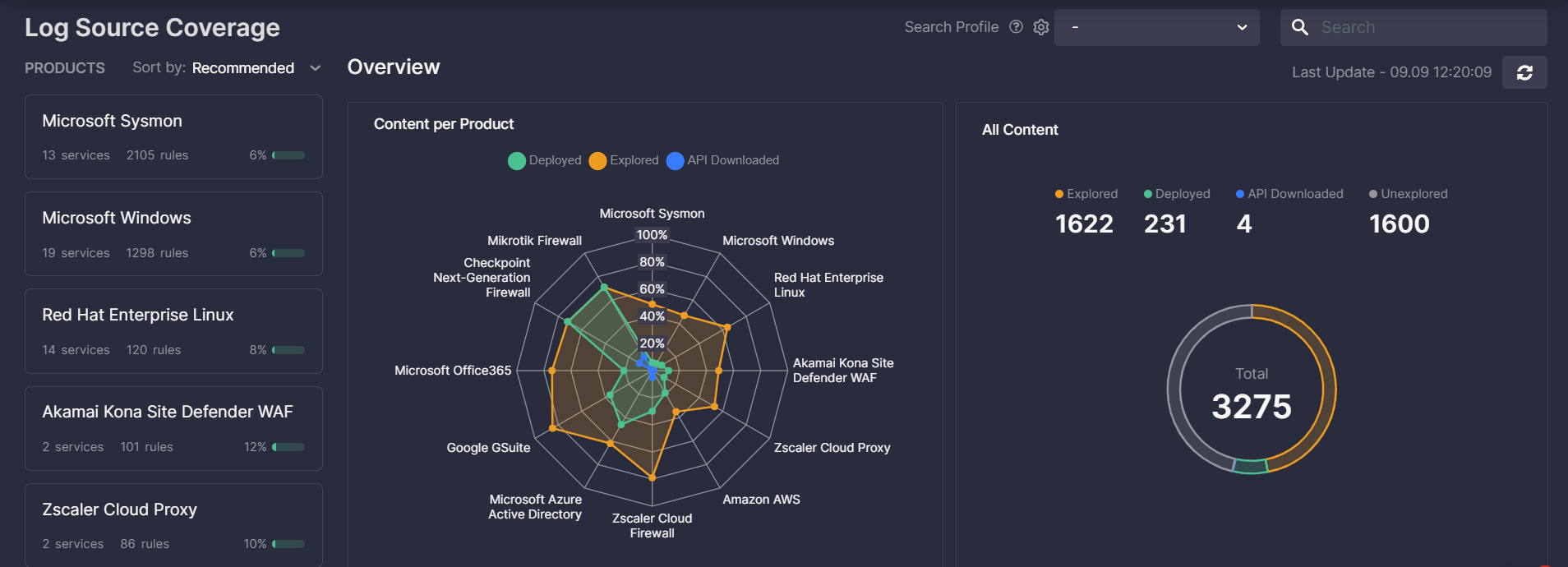
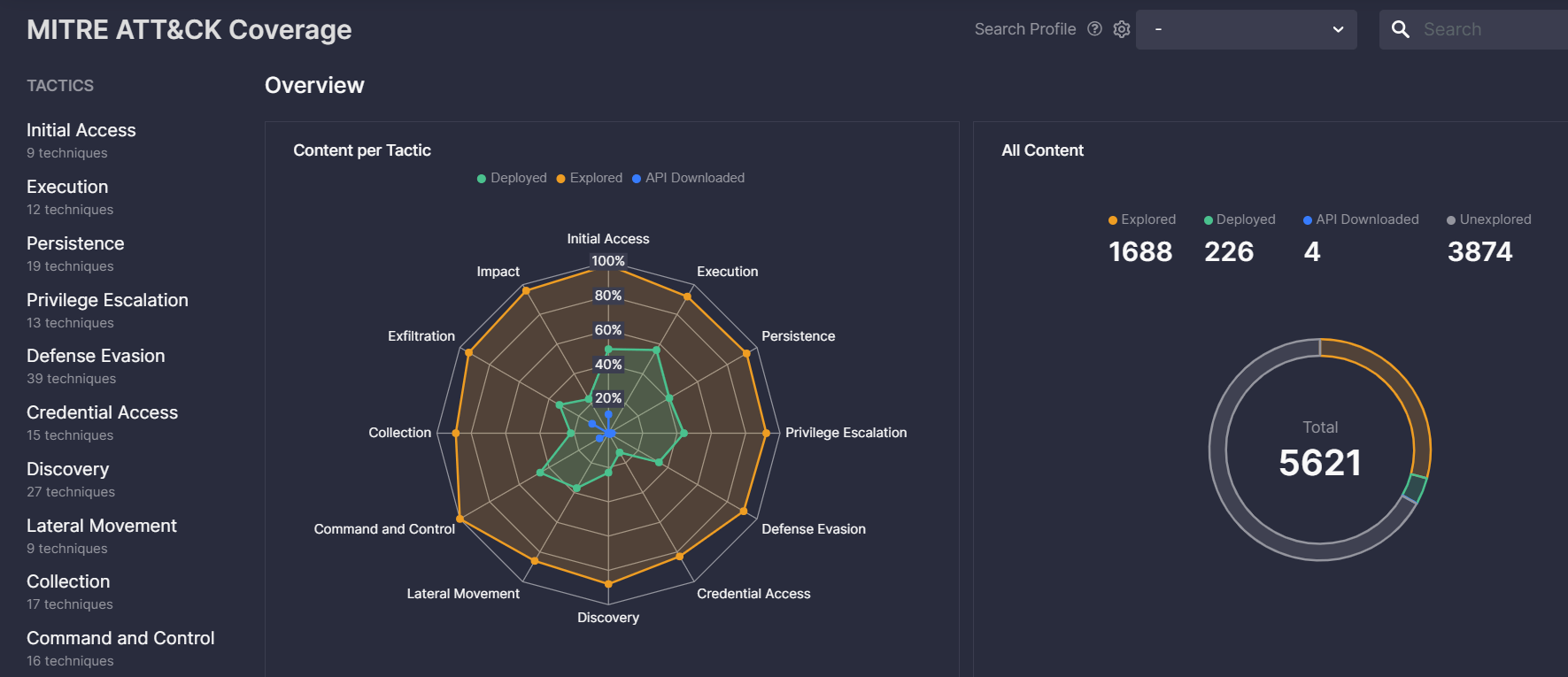
MITRE ATT&CK Coverage dashboard displays the dynamics on threat coverage using the v9 framework. It has the same logic as the Log Source Coverage dashboard, yet aligned to tactics, techniques, and all the way to sub-techniques and tools. Using ATT&CK as a benchmark is not a static task, new threats and vulnerabilities appear every day, and so does the new detection content. Now, it is possible to capture and explore your own trend of making progress on the industry benchmark in a dynamic fashion.
Integrate
Under the Integrate category, we’ve placed all major configurations to easily connect and manage the security tools in use from a single place. Configure environments for 20+ platforms, build your Search Profiles, and adjust Custom Field Mapping to your SIEM & XDR stack to be all set for a streamlined platform experience.
We’ve also revised localizations to make them more intuitive and consistent across the entire platform. What’s more, Search Profiles (formerly known as “Rule Master”) and Custom Field Mapping are now free and accessible to all community users.
Automate
Adapt your cyber defense to the latest threats in real-time with Continuous Content Management. Leveraging this functionality, security performers can tune detection logic to their needs, configure exceptions, add filters, and stream customized content directly to the SIEM & XDR instance.
Learn and Collaborate
Also, the SOC Prime platform serves multiple options for security practitioners to stay abreast of the latest trends in cybersecurity and network with peers worldwide:
- Join our Slack Community to participate in live discussions with security enthusiasts and share ideas for a safer future.
- Become a member of our Threat Bounty Program for individual cyber defenders to contribute to the world’s cybersecurity and receive recurrent rewards for sharing your own detections via the SOC Prime’s world-first SOC content repository.
- Get direct access to free cybersecurity knowledge via Cyber Library to improve your technology skills, watch deep-dive educational videos, and catch up with how-to guides on threat hunting online.


