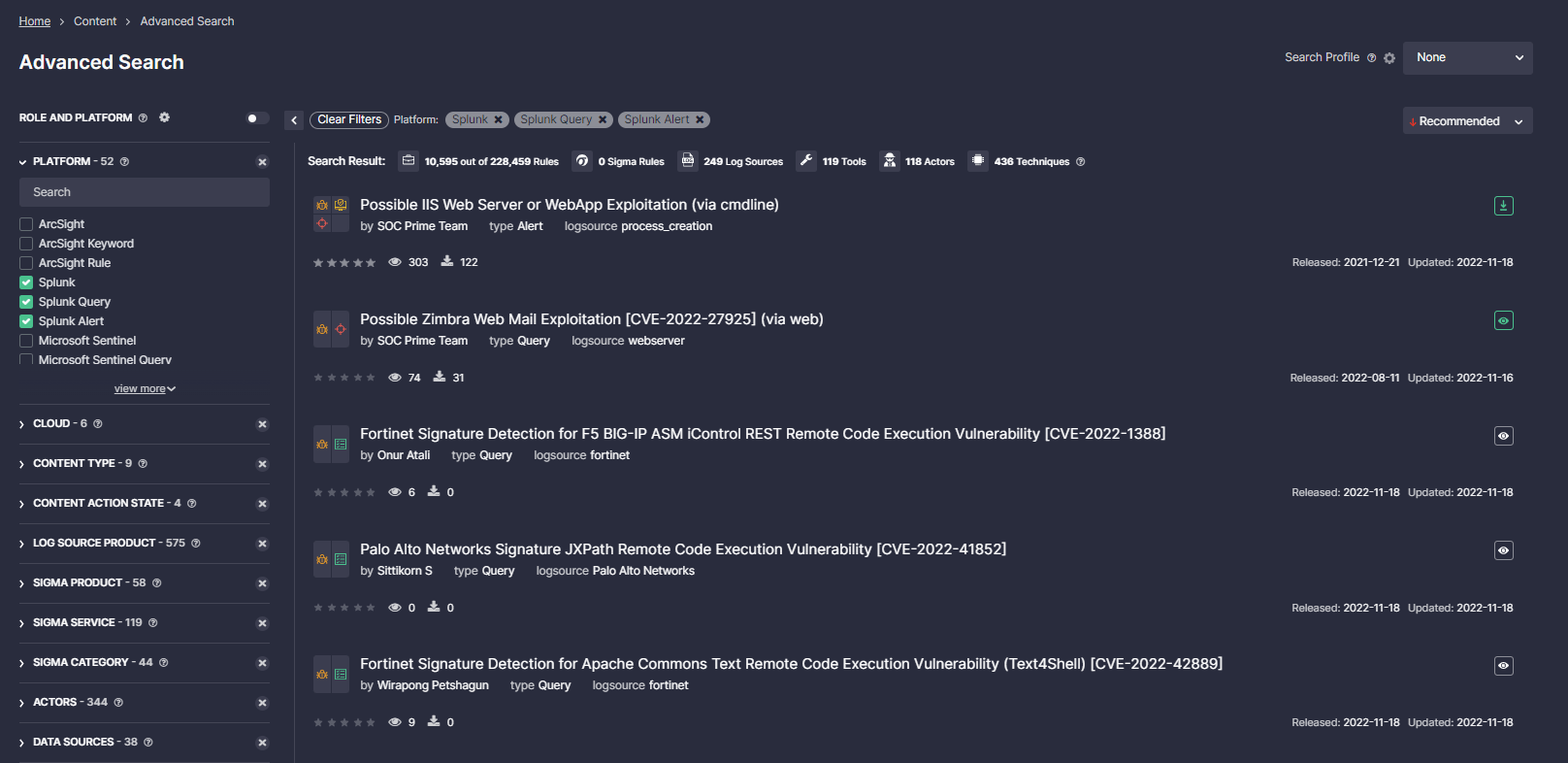
The SOC Prime CCM App for Splunk allows streaming the most critical detection content to both on-premises and cloud-based Splunk environments.
Powered by the SOC Prime’s Detection as Code platform, the world’s largest Threat Detection Marketplace provides access to 10,000+ Splunk Alerts and Queries. Leveraging the Continuous Content Management (CCM) module and the SOC Prime CCM App for Splunk, security professionals can automatically stream the most relevant SOC content into Splunk. Detections can be automatically deployed based on a preferred recurring schedule saving time on manual configurations.
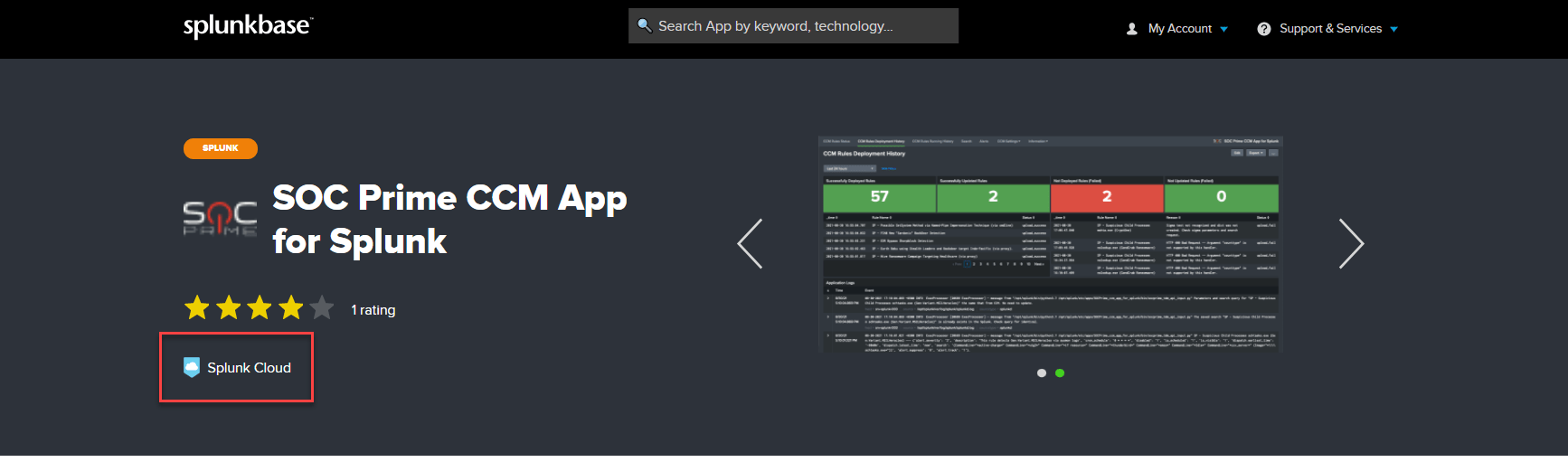
We are thrilled to announce that the SOC Prime CCM App for Splunk has been recently vetted for Splunk Cloud Platform, providing continuous content streaming capabilities to Splunk Cloud customers. Community users of the SOC Prime’s Detection as Code platform can also use the app to pull the latest detection content to Splunk.
In this blog article, we’re going to cover how to install, configure, and work with the SOC Prime CCM App.
Note: To automatically deploy rules from a selected Content List, security practitioners need to have an enabled access to the SOC Prime Threat Detection Marketplace API. For guidelines on how to enable API access, please refer to the latest version of the guide to the Threat Detection Marketplace API Integration Tool here.
Installing the SOC Prime CCM App on Splunk Cloud Platform
The SOC Prime CCM app can be deployed directly from the Splunk Web Console.
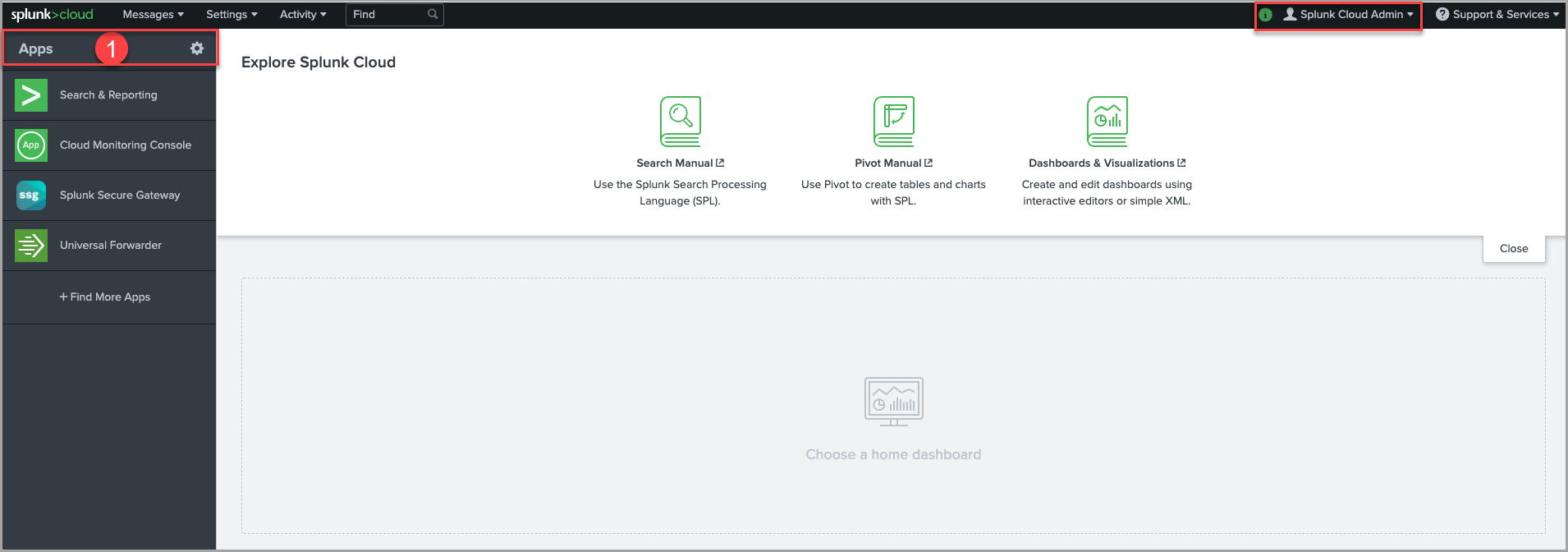
1. In the Splunk Web Console, click the Apps gear icon. Note that only users with the sc_admin role can install the app on Splunk Cloud Platform.
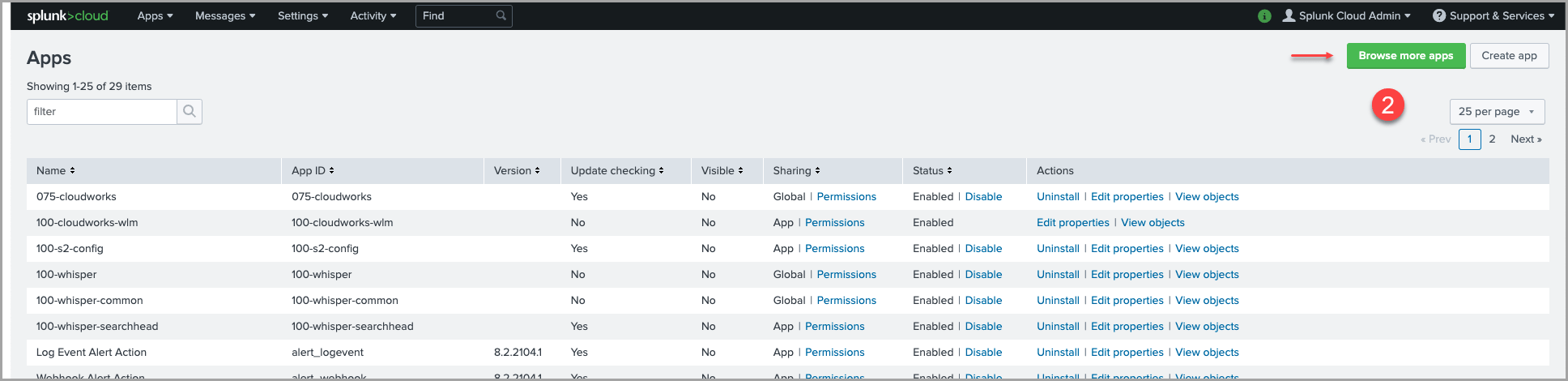
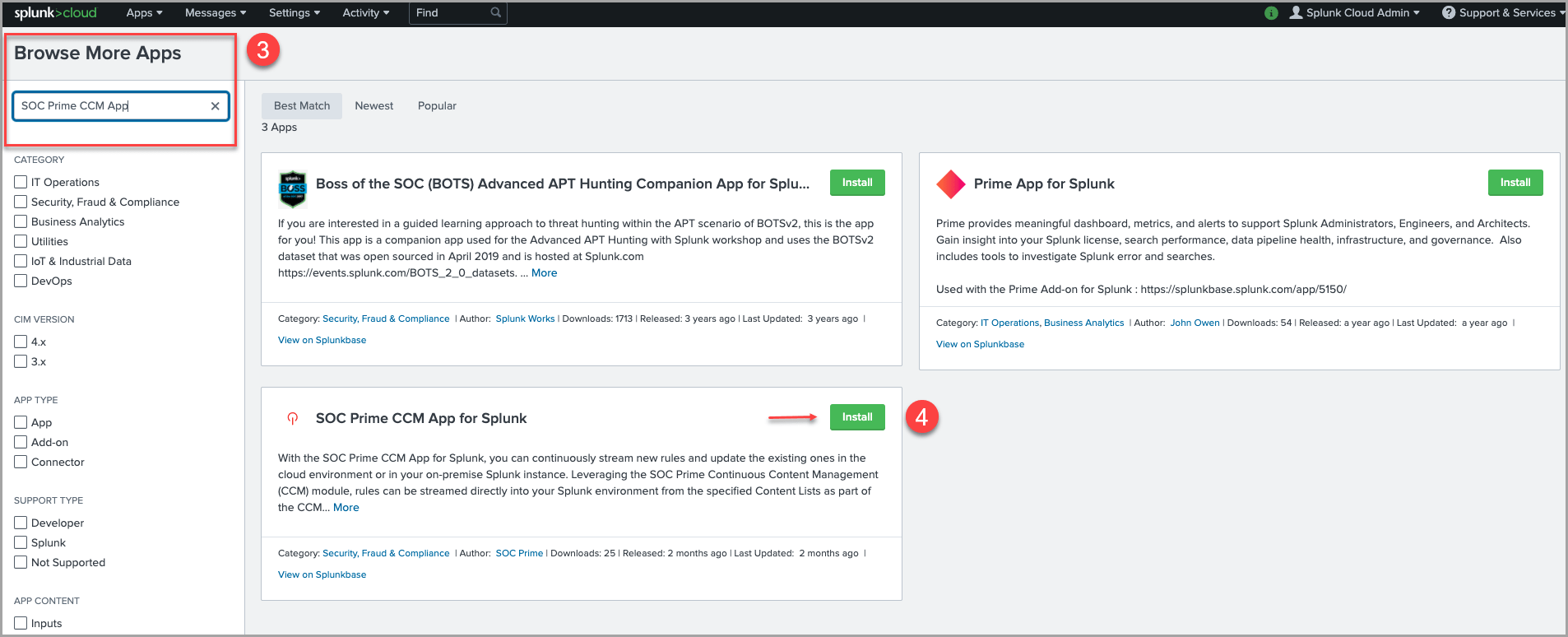
2. Click the Browse more apps button in the top right-hand corner of the page.
3. In the Search field, enter the “SOC Prime CCM App for Splunk”.
4. Find the SOC Prime CCM App for Splunk from the list of search results and click Install.
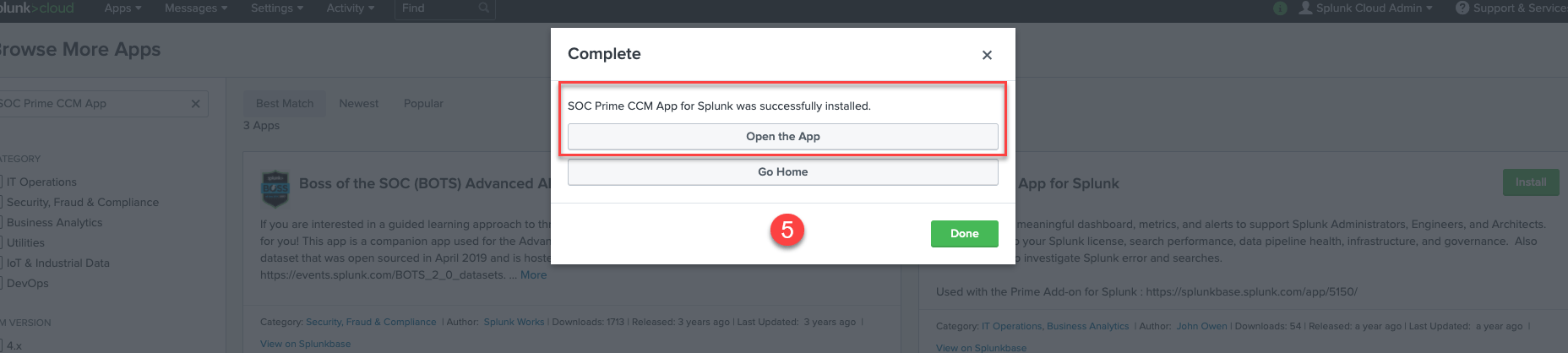
5. If installation is complete, security engineers will be notified by the corresponding success notification. Click Open the App to get started with the app.
After successful installation, the app should appear as “SOC Prime CCM App for Splunk” in Splunk’s Apps menu.
Configuring the App in the Splunk Environment
After installation, configure the rule import with the Data Inputs menu:
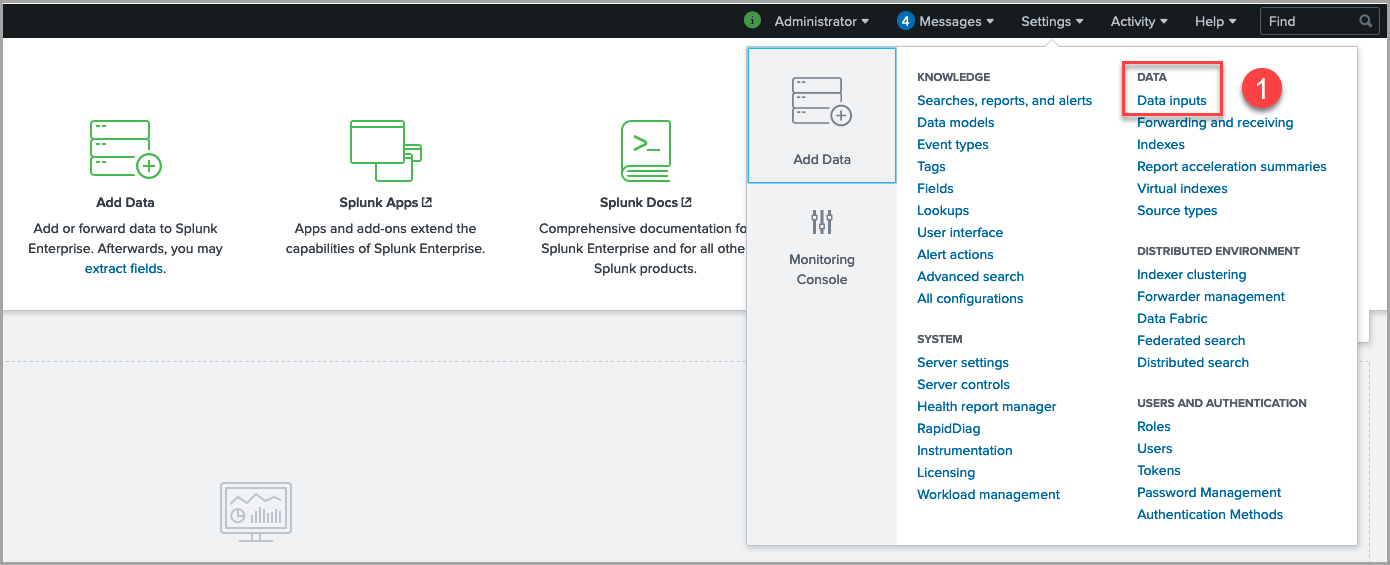
1. Select Settings > Data Inputs.
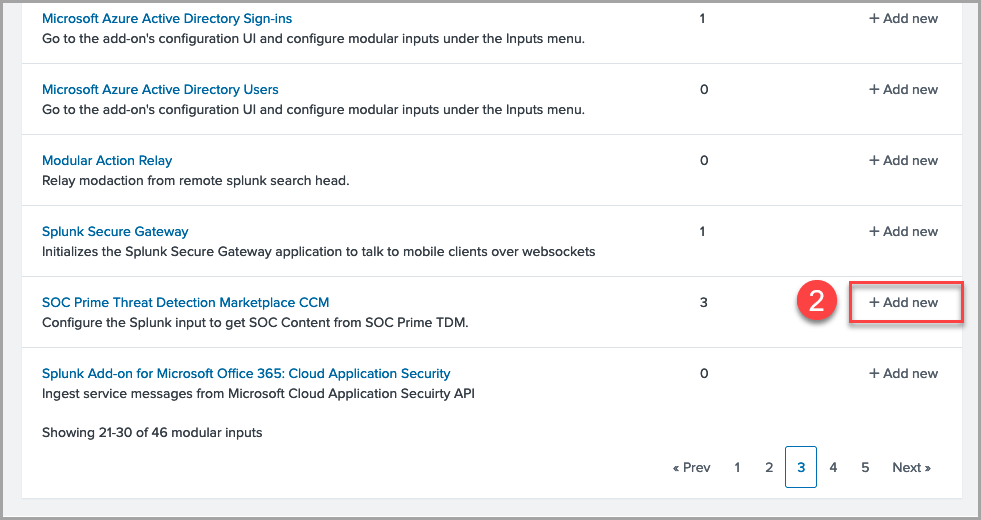
2. In the list of inputs, find “SOC Prime Threat Detection Marketplace CCM” and click the Add new button.
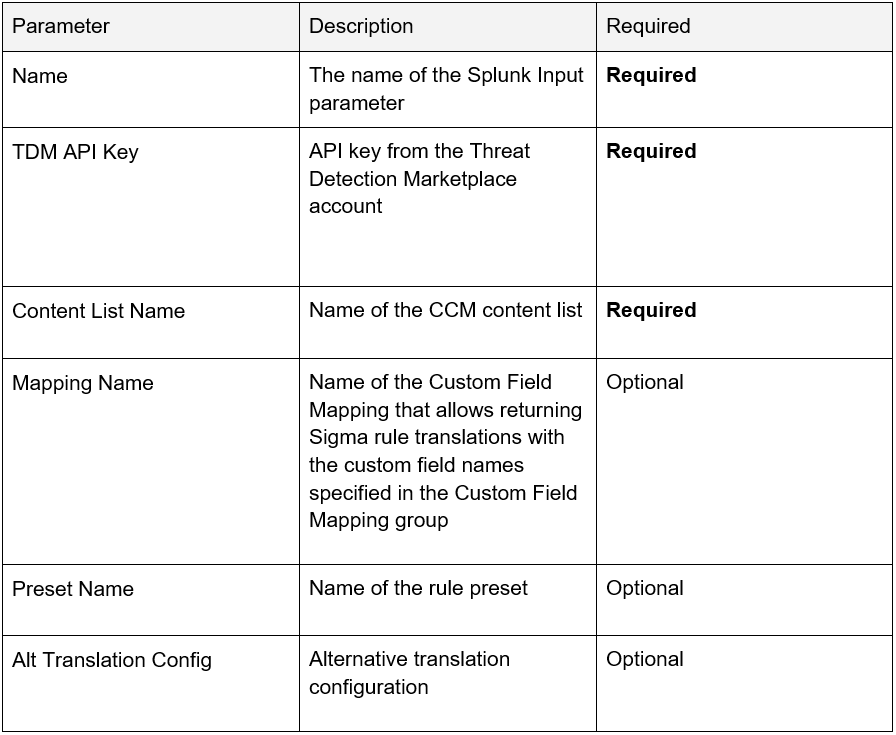
3. Fill in all the required and optional parameters:
|
Note: Selecting More settings allows changing the schedule of rule synchronization with the CCM module. By default, the synchronization is run once per day. The Cron format can be used for configuring the Interval settings. |
Working with the SOC Prime CCM App for Splunk
After successful installation and configuration, wait for the first synchronization of alerts.
The dashboards visualize information on deploying, updating, and running rules in the SOC Prime CCM App for Splunk:
1. Select SOC Prime CCM App for Splunk in the main Apps menu of the Splunk Web Console:
2. Explore the dashboards (screenshots are provided for reference only):
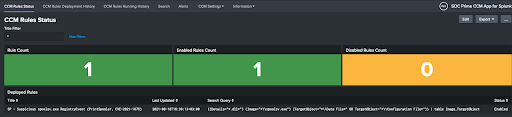
- CCM Rule Status:
-
- Status of all deployed rules (Enabled/Disabled)
- Rule count and stats on the last update
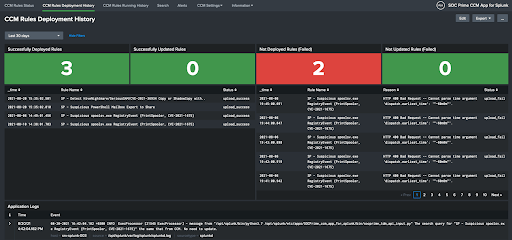
- CCM Rule Deployment History — statistics and logs of the deployment process:
- Deployment of new alerts
- Alert updates
- Failed deployments and their causes
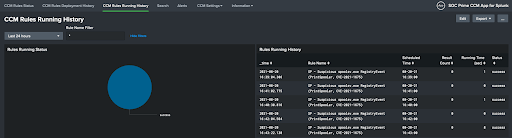
- CCM Rules Running History — information on running statuses of deployed alerts:
- When the last run occurred
- Number of results
- Result status
All alerts will be installed in the SOC Prime CCM App for Splunk. To view all the installed alerts and settings, select the Alerts tab. To view the settings of a certain alert and make changes to them, click the corresponding item, and the fired events for this alert will be also displayed on this page. The app allows configuring actions for all available alerts. That’s it, you’re all set for continuous content streaming using the SOC Prime CCM App for Splunk.
Explore the world’s largest and most advanced platform for collective cyber defense to boost your threat detection and hunting capabilities and defend against attacks before they strike. Tired of handling the data schema complexity challenges? Сheck out this blog post to see how the CCM module can help you address these challenges while streamlining daily SOC operations. SOC Prime also welcomes cybersecurity enthusiasts to join the Threat Bounty Program and share their expertise with industry peers, monetize contributions, and master Detection Engineering skills.