Boost Your Google Chronicle Platform with SOC Prime Detection Rules

At SOC Prime, we actively broaden the support of open source projects and constantly enrich our SIEM and XDR stack with cloud-based solutions. Starting from 2020, we evolve the partnership with Chronicle, Google Cloud’s security analytics platform, and expand our Detection as Code content base with new YARA-L 2.0 detection rules perfectly tailored to defend against modern threats. Read more about SOC Prime’s partnership with Chronicle in the recent blog article from Google.
Threat Detection Marketplace enables full Continuous Integration (CI) / Continuous Delivery (CD) workflow for cyber defense operations by providing seamless deployment and customization of cutting-edge cross-tool SOC content like Queries, Rules, Functions, and Incident Response Playbooks mapped to the MITRE ATT&CK® framework. Infuse your Chronicle instance with enriched, constantly curated content from Threat Detection Marketplace to hunt out threats at Google speed!
Chronicle Integration with Threat Detection Marketplace
As of April 2021, you can reach 500+ Community YARA-L rules written by the SOC Prime Team already available in Threat Detection Marketplace. Also, Chronicle customers can access these free detections at Chronicle GitHub repository powered by the Chronicle Detect rules engine.
SOC content written in the generic YARA-L threat detection language enables security teams to smooth out the development of new rules and their deployment to the Chronicle platform.
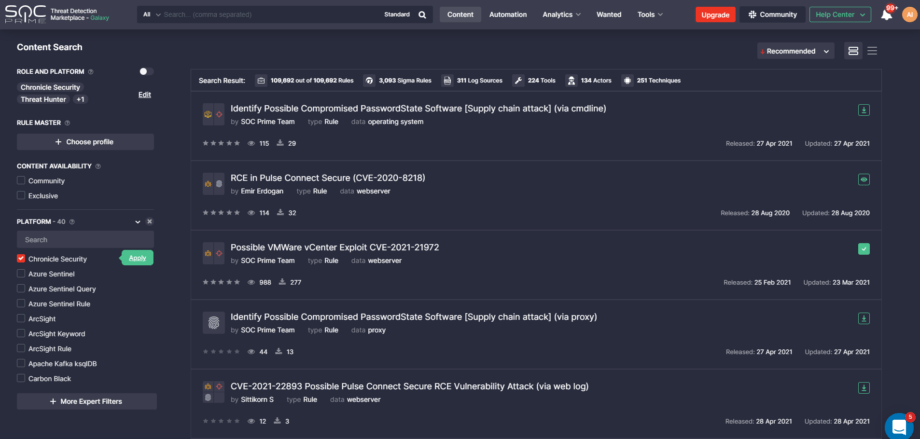
YARA-L based rules in Threat Detection Marketplace fit into the following use case categories:
- Proactive Exploit Detection — rules related to CVEs and exploits and tagged accordingly. Examples include CVE detection, such as Citrix Netscaler attack (CVE-2019-19781), F5 BIG IP security hole (CVE-2020-5902), SIGRED (CVE-2020-1350) exploitation attempts, and other suspicious activity putting users at the risk of compromise.
- Active Directory Security — rules related to the Azure Active Directory (AD), including detections for potential abuse of Active Directory Replication Service (ADRS) from a non-machine account and rules for RDP logons from non-private IP ranges.
- Cloud Security — rules related to IaaS, SaaS, or PaaS data sources, such as web skimming attacks and suspicious command-line activities.
- Threat Hunting — rules for threat hunting and tagged with “APT,” including those detecting Powershell attacks from antivirus logs, potentially malicious Sysmon activity, suspicious DNS queries known from Cobalt Strike beacons, and more.
- Compliance — rules that cover compliance-related security controls, including those related to administrative account privilege violations.
- IOC Sigma — rules that belong to IOCs (Indicators of Compromise), like content for detecting a highly relevant antivirus alert that reports a password dumper or a detection rule for identifying the SUNBURST C2 channel applied in the related compromise.
- Mixed/Other — other rules that do not fall into any specific category, like content addressing malicious executions based on command-line arguments used for msbuild.exe binary.
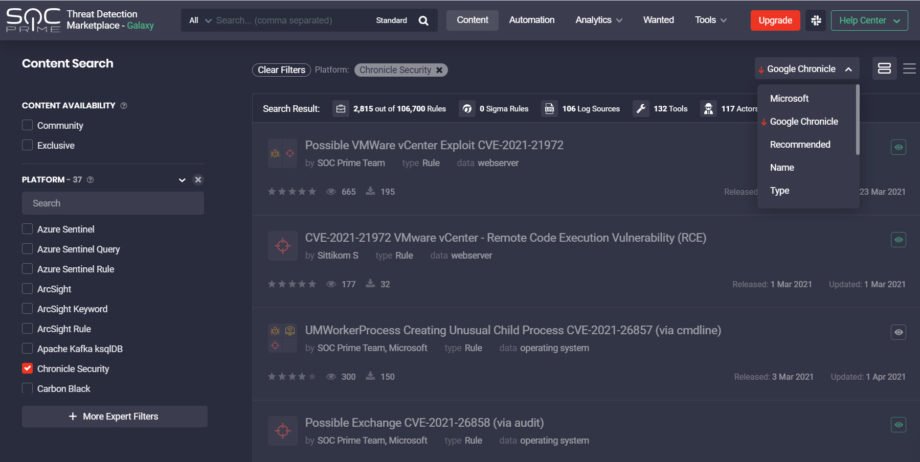
Chronicle customers leveraging Threat Detection Marketplace can streamline their content search using the Google Chronicle sorting option tailored directly to meet their security needs. The enhanced content boosting functionality enables viewing the most relevant content on top of the list.
Open Source Support and Contributor Recognition
Being part of the open source community means giving credit to all content authors. Starting from July 2020, we release all open source detections with a link to the Detection Rule License (DRL) or another appropriate license to recognize each community content contributor. All YARA-L detections available in Threat Detection Marketplace contain the author field within the source code that explicitly points to the content contributor.
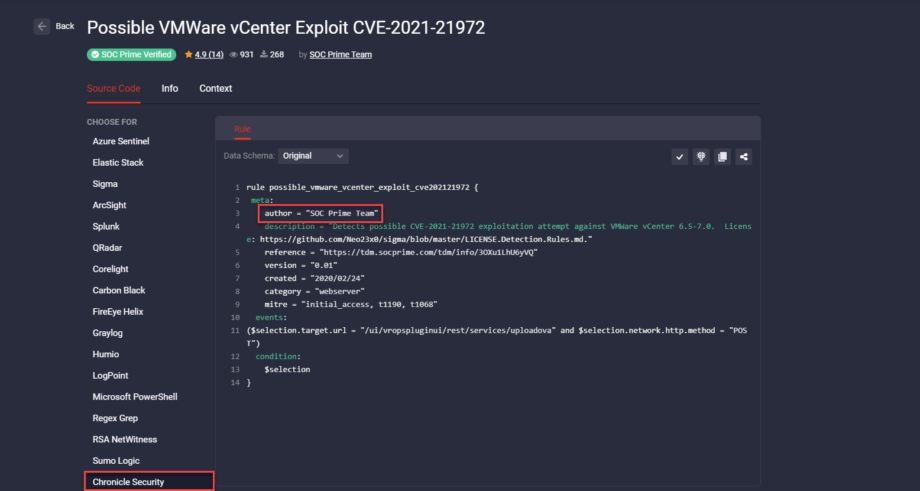
SOC Prime Team contributes to the Google Chronicle repo on GitHub by constantly enriching it with the collection of curated detections written in the generic YARA-L 2.0 format. The entire collection of SOC Prime’s YARA-L rules are accessible in the soc_prime_rules folder of the Chronicle GitHub repository. Security practitioners can deploy these YARA-L detections to their Chronicle instance via the Detection UI or the Chronicle Detection API.
Helping Security Operation Teams to break the limits of being dependent on a single solution for threat detection, SOC Prime has developed Uncoder.IO, a free online translator tool that converts Sigma rules into other language formats on the fly. Uncoder.IO currently supports translations from Sigma to YARA-L enabling seamless transition of existing rules from legacy solutions to Chronicle.
To learn more about Chronicle’s SOC Prime rules, check out the Chronicle GitHub repository or reach YARA-L content directly from Threat Detection Marketplace. SOC Prime’s Content-as-a-Service (CaaS) platform offers 100K+ detection algorithms and threat hunting queries for 20+ market-leading SIEM, EDR, and NTDR tools. Eager to develop your own rules and contribute to the world’s cyber defense? Join our Threat Bounty Program!


