About a week ago we got this info from one of our partners “We are seeing phishing emails flying in our environment (Internal to Internal)” along with sharing an email sample with us. Today we’re going to analyze the recent phishing attacks targeted at Fortune 500 and Global 2000 companies dubbed “Stealthphish” aimed at compromising business emails (BEC) and tricking financial specialists on transferring money to wrong accounts. This incident is performed by the same actor as described in IBM X-force IRIS report from Feb 21: https://securityintelligence.com/ibm-x-force-iris-uncovers-active-business-email-compromise-campaign-targeting-fortune-500-companies/ Without further ado, let’s dive into technical details on the infrastructure and attack mechanisms, mine some IOCs and attempt an attribution.
Let us begin with the email header fragment:
X-MS-Exchange-Organization-AuthMechanism: 04
X-Originating-IP: [154.118.XXX.YYY]
Dynamic allocation for LTE customers
CityLagos
NameNigeria
The ASN is the same as IPs from report above. Two URLs the email was redirecting to:
hXXps://arcadiansilverspring[.]com/wp-admin/images/files/encrypted_access_area/signdocu/
hXXp://libertym[.]us/wp-content/themes/twentysixteen/files/encrypted_access_area/signdocu/
Associated IP addresses:
184[.]173[.]132[.]214
50[.]2[.]225[.]147
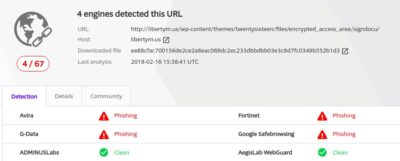
libertym[dot]us appears to be a recently hacked domain:
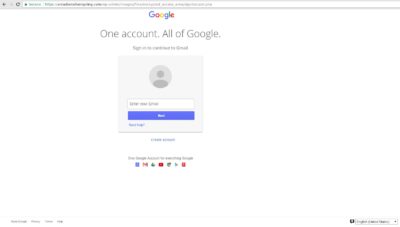
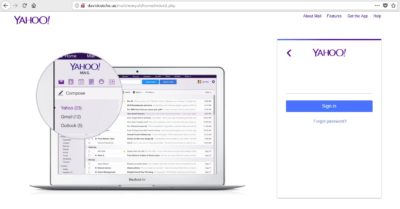
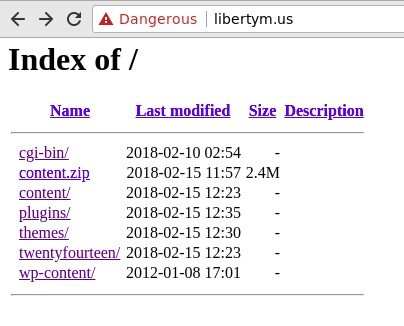 It is hosting a phishing Office365 login page for Credential Harvesting. In this case there is at least an SSL certificate warning at the top of the page that may stop a vigilant user.
It is hosting a phishing Office365 login page for Credential Harvesting. In this case there is at least an SSL certificate warning at the top of the page that may stop a vigilant user.
The libertym[.]us domain was listed as malicious on February 16th so was relatively easy to detect.
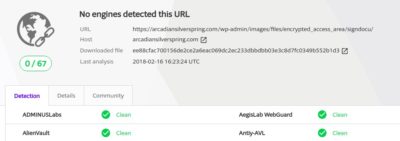
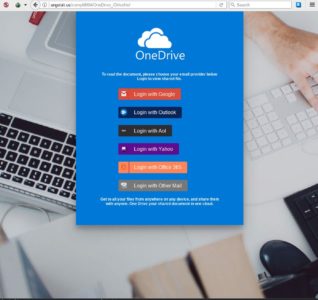
A more dangerous domain hXXps://arcadiansilverspring[dot]com was also recently hacked and has a proper SSL implemented. This serves us as a good example that a green HTTPS alone != trust or security. In this example phishing pages for Google Apps and DocuSign are similar to ones we’ve seen earlier so this is another link to Stealthphish. Screenshots of the phishing URLs:
Domain remained unlisted for some time even as attack was progressing.
As of today situation is somewhat better: https://www.virustotal.com/#/url/cc38768a899bd34a208a5cb15f84a9b139d1703b1c7477774e9eb73740e5af5c/detection
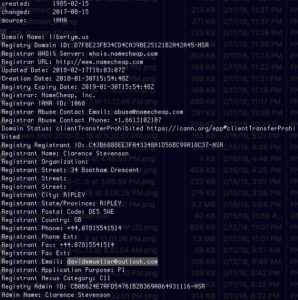
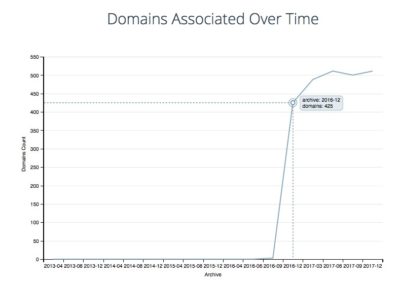
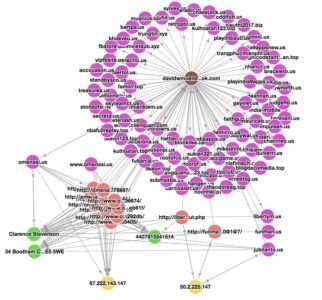
Initially we did a Whois on the first malicious domain which pointed us to davidwmueller[at]outlook[.]com aka Clarence Stevenson:
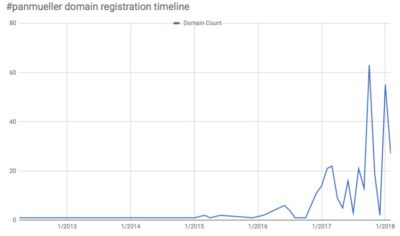
A reverse whois on the davidwmueller’s email using some of the freely available tools finds 500+ domains that were registered since December 2016.
Discovered domains look like typosquatting attempts or even legit websites rather than DGA:
• mobile-india.us
• hextracoin.us
• nikemail.us
• tipclub.us
• travelworld123.com
• treasurea.us
• app-android.us
• jumail.us
Many of the domains were kept inactive and some of them already expired by the attack’s time so we decided to manually review the OSINT and filtered out the noise:
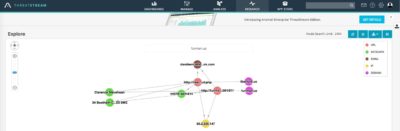
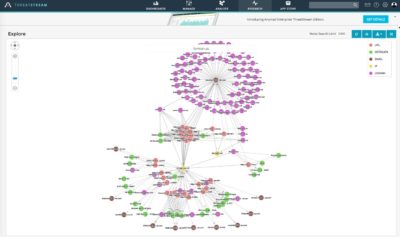
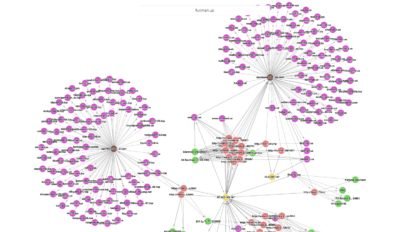
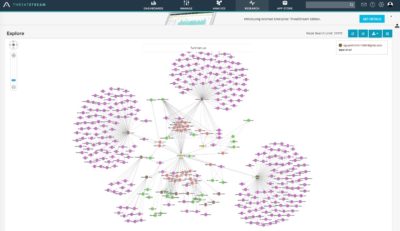
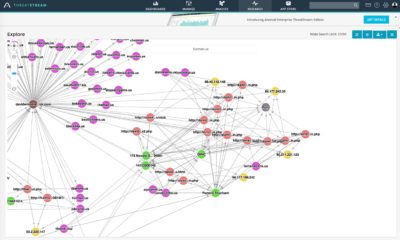
Things got more interesting once looked up our findings in Anomali ThreatStream:
Adding some Whois information to the davidwmueller[at]outlook[.]com along with Clarence Stevenson lookup in ThreatStream data:
Now let’s take a look what is behind those URLs and domains (do not try this at home!):
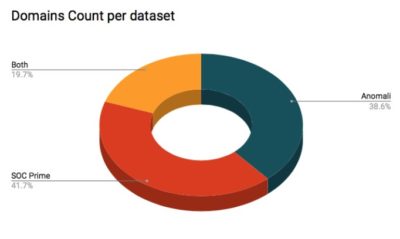
Stealthphish is clearly going after O365, OneDrive, Google Apps and Yahoo Mail as well. As a next step we verified the 500+ domains further by leveraging OSINT and some of our proprietary threat intel feed, then matched our dataset with ThreatStream. As a result we confirmed total of 528 domains related to the attack with 204 listed in ThreatStream, 220 in SOC Prime and 104 in both feeds:
Time to look up the IP’s in ThreatStream and see if there are any more links:
We’ve got ourselves new names (stolen or pseudo identities) and 10 more Gmail addresses to use in our Whois and threat intel research. We also don’t see much context on OSINT IPs found meaning they are still not used in active attack (not an IOC yet). At this point we tried to check out the basic security measures of the PanMueller’s outlook account (PAN stands for Phishing Attack Nigeria and also translates as “Mr.” from Ukrainian so was used by our researchers as internal name).
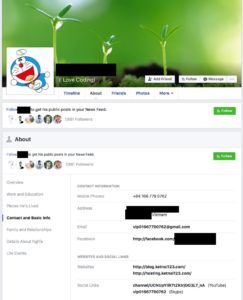
We got 10 Gmail accounts to go through, let us start with the one that looks similar to the backup email: vip01667790762[at]gmail[.]com
As we continue enriching all emails on our graph we also notice nguyenthilinh110591[at]gmail.com with many linked domains:
We start seeing domains protected by WhoisGuard and private registrations. But it seems that our PanMueller was not so concerned about hiding his identity when mass registering domains. Let us try to find out who is behind the vip01667790762[at]gmail.com and davidwmueller[at]outlook[.]com account by simply googling around:
Looks like our PanMueller is not an evil mastermind who planned a world domination attack for 2,5 years but a person who is not very concerned about his personal cyber security. He sells VPN services, quick hosting and domain registrations, overall this is not exactly a criminal activity. Even further, he publicly lists his mobile number at facebook page along with using it in his domain registration Gmail address. Either he got hacked or was determined enough to really plan this all along and getting 7,681 followers/friends in the process. PanMueller’s behavior is also very different from the latest developments in this campaign. The “arcadiansilverspring” domain simply does not fit! PanMueller used cheaply registered domains under fictional names and information is kept open. Meanwhile StealthPhish clearly demonstrated capabilities of hacking legitimate websites that use WordPress (recent bug in version 4.9.3 with auto-update disabled may ring the bell) and their domains are hidden behind the WhoisGuard services. While we have uncovered the majority of the attacker infrastructure there is still a pool of domains that remains in the shadow. And those are the hacked domains with legit SSL certificates that pose a much higher threat. Discovering these domains is a proper task for any threat hunters, SOC and SIEM analysts out there, so we’ll get ready to assist with the right threat detection content.
Going back to the graph we’ve tried to search on each meta-data piece that ThreatStream could find and found a particularly interesting result related to “Pamela Touchard”:
Pamela has lead us to the infamous Pony. Perhaps PanMueller was just a proxy and sold his stuff to the wrong guys? Some brief information from Anomali Threat bulletin on Pony:
“Pony is a password stealer and a loader. A loader is a program that downloads additional malware in order to further compromise the system. Pony is widely available as source code and via multiple hack forums. Pony is often hosted on bulletproof hosting with infrastructure in Russia and Ukraine. Pony is closely associated with Chanitor/Hancitor and Neverquest/Vawtrak. Pony has affected millions of victims worldwide.”
There are some 4000+ indicators of compromise associated with Pony usage by CyberCrime with 250+ fresh URL’s in 2018 alone. To further dive into this matter I recommend following https://ui.threatstream.com/tip/7073 and https://ui.threatstream.com/search?status=active&value__re=.*pony.*
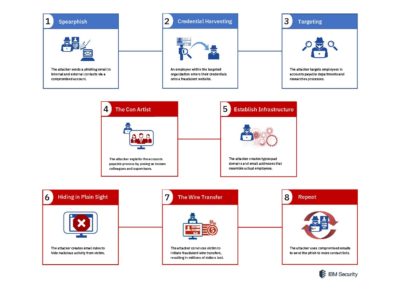
We can conclude that Stealthphish is the global scale phishing campaign organized by Cyber Crime with significant resources. The actor is operating out of stealth and is hiding in plain sight by using Compromised Business Email accounts (aka #BEC), leveraging email filters to mask activity from hacked victims and carefully impersonating the hacked individuals working at financial and accounting positions of the Fortune 500 and Global 2000 enterprise.
Original image source: IBM Security
The goals of the Stealthphish campaign is to leverage social engineering to trick personnel responsible for financial operations to wire transfer money to the cyber criminals masking this as legitimate operation. We may not have seen the endgame of this actor yet. The compromise or misuse of PanMueller domains (and accounts?) has given Stealthphish an unprecedented amount of domains for the Credential Harvesting. These domains are not listed or even marked as clean on most OSINT, commercial threat intelligence. They are not registered recently, excluded from malware listings such as VirusTotal and even dedicated anti-phishing resources like OpenPhish and PhishTank. There is also no malware involved at initial attack stage and Stealthphish got itself a huge “pre-IOC” infrastructure. Additionally if we take a thorough look at the domains we see that this is far from a typical DGA (domain generated algorithms) case in order to avoid modern machine learning based detections. And as we know once credentials are obtained Stealthphish leverages corporate email accounts to blend the phishing actions with legitimate business communications (Living off the land 2.0: cloud email services). With all of this combined we see a carefully executed attack that will avoid most of today’s phishing defenses.
It is highly recommended to blacklist any connections to IOCs supplied below and adding them to watch lists in detection technologies that you have. Additionally, close integration of any threat intelligence related to Pony be it URL’s or hashes is of high importance.
Meanwhile we are contributing all our findings to Anomali ThreatStream as well as finalizing content for our own Threat Detection Marketplace.
ASNs involved in attack, recommended for blacklisting if applicable:
AS37340 https://ipinfo.io/AS37340
AS36873 https://ipinfo.io/AS36873
TLP:WHITE Indicators of Compromise (IOCs):
IP:
184[.]173[.]132[.]214
50[.]2[.]225[.]147
67[.]222[.]143[.]147
50[.]2[.]225[.]167
Domain:
aamape[dot]com
angelalt[dot]us
app-android[dot]us
davidcutche[dot]us
getartifa[dot]top
hextracoin[dot]us
jumail[dot]us
libertym[dot]us
likeviet[dot]top
mobile-india[dot]us
nhacsan[dot]pro
nikemail[dot]us
omenaxi[dot]us
passethus[dot]com
ribbinkx[dot]xyz
tintuc36h[dot]com
tipclub[dot]us
travelworld123[dot]com
treasurea[dot]us
URL:
hXXps://arcadiansilverspring[dot]com/wp-admin/images/files/encrypted_access_area/signdocu/
hXXp://libertym[dot]us/wp-content/themes/twentysixteen/files/encrypted_access_area/signdocu/
All other IOCs are not for public disclosure yet and involve 528+ domains (324+ discovered by SOC Prime), 120+ IPs along with compromised emails. We are in process of distributing them along with detection content via https://my.socprime.com/en/tdm/ and https://ui.threatstream.com/
Links to SIEM threat detection content:
ArcSight QRadar and Splunk https://tdm.socprime.com/login/
A special thanks goes to one of our partners for sharing the initial 77 suspected domains and email sample which helped to speed up the investigation – thank you man, you rock!
This report is brought to you by the Vader Division
/Stay safe