The research is based on OSINT evidence analysis, local evidence, feedback from attack victims and MITRE ATT&CK methodology used for actor attribution. SOC Prime would like to express gratitude to independent security researchers and specialized security companies who shared the reverse engineering reports and attack analysis on the public sources and their corporate blogs. On our side, we share this TTP attribution threat brief as well as threat detector SIEM content for ArcSight, QRadar and Splunk.
Executive Summary
Bad Rabbit is a global ransomware worm outbreak that happened on October 24 2017 and impacted high number of organizations across different industries mostly in CIS and APAC countries.
Forensics report by Cisco Talos states that the first initial download was observed around 2017-10-24 08:22 UTC. SOC Prime was informed of attack by one of the transportation organizations in Ukraine at 2017-10-24 10:12 UTC. At the time organization was already encrypted so we agree that most conclusive evidence of attack execution is the one reported by Talos: 08:22 UTC.
As of 2017-10-25 08:24 UTC there is no public evidence that attack is of APT nature. However it was executed in parallel with another Ransomware attack: Loky ransomware hit the same using malicious email attachment as delivery vector and leveraging vulnerability in Microsoft Word DDE. While several researchers have pointed out similarities with NotPetya attack we strongly disagree with this statement as TTP attribution clearly shows that threat actor is not the same. Unless other evidence is presented the attack should be considered a Cyber Crime activity and not a state sponsored attack. However, we have seen the same pattern of launching a decoy attack to cover up for APT operation during NotPetya in June 2017.
Since attack has worm capabilities and distributes quickly it is highly advised to deploy proactive threat detection controls in SIEM technologies and deploy temporary vaccination configurations on Windows host systems.
Threat name: Bad Rabbit
Aliases: Discoder / Win32/Diskcoder.D / Trojan-Ransom.Win32.Gen.ftl / DangerousObject.Multi.Generic / PDM:Trojan.Win32.Generic
Threat type: Ransomware
Actor type: Cyber Crime
Threat level: High
Impact by Geo: Russia, Ukraine, Bulgaria, Turkey, Japan, Romania, Germany.
Impact by Industry: Transportation and Retail (mostly in Ukraine), Media sector (mostly in Russia)
Infection vector: Drive by Download malicious javascript on infected websites
Affected IT assets: Windows OS.
Related APT: no conclusive attribution can be provide due to lack of evidence.
Threat Actor Attribution and TTP Analysis
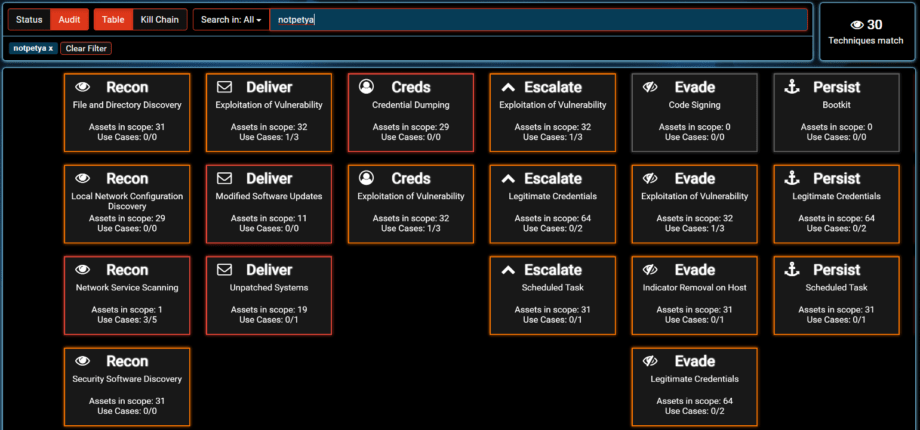
Several research companies have stated the similarity of the Bad Rabbit attack with NotPetya. We think that this is yet another problem of PR and media promotion and many security experts acting independently to catch “the next big threat”. As of 2017-10-25 08:24 UTC there is no public technical evidence of Bad Rabbit attack being an APT or having TTP similar with NotPetya and Sandworm. Furthermore several research firms reported that there is 13% source code overlap of Bad Rabbit and NotPetya ransomware component which is not enough to pinpoint the similarity as NotPetya had major similarities of code with Petya ransomware to act as decoy and distraction. It is clear that Petya and NotPetya ransomware code is available to multiple actors. Let’s take a closer look at NotPetya TTPs by leveraging MITRE ATT&CK methodology and custom threat model from SOC Prime SVA AI:
The actor behind NotPetya used 30 techniques to execute the attack.
TTPs difference between Bad Rabbit and NotPetya:
- Supply-chain attack vector (Modified M.E.Doc software updates)
- EternalBlue vulnerability (Bad Rabbit does not use it)
- Indicator removal on host (by clearing up MS EventLog. Bad Rabbit does not do that)
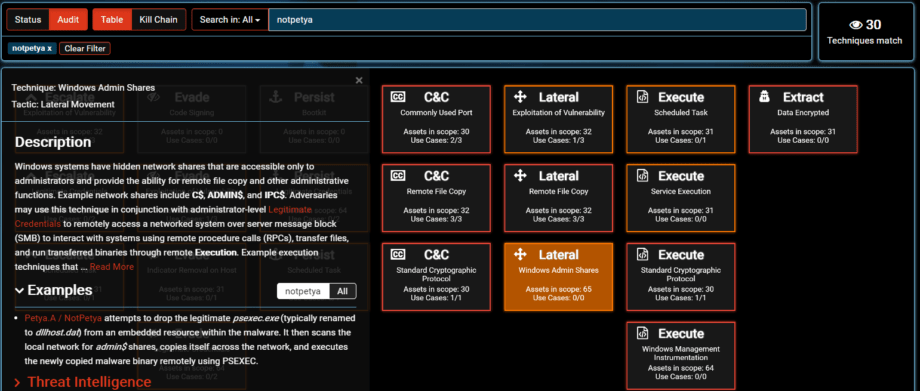
- PsExec is not used by Bad Rabbit for Windows Admin Shares of Lateral Movement
- Hardcoded credentials are used by Bad Rabbit and not used by NotPetya
- Legitimate credentials obtained by NotPetya were managed by C2. This allowed attacker to use specific Active Directory accounts of Lateral Movement such as Microsoft SCCM service account.
Debated similarity:
1. Bootkit is heavily used in NotPetya as “signature” technique of Sandworm actor for data destruction aka “wiper feature” (in BlackEnergy campaigns) and for irreversibly encrypting data at boot time also equivalent to data destruction (in NotPetya campaign). Bad Rabbit does not have a full-blown Bootkit as it only places the ransomware notice to bootloader.
To elaborate more on debate we’ll use a quote from Bleeping computer
As for Bad Rabbit, the ransomware is a so-called disk coder, similar to Petya and NotPetya. Bad Rabbit first encrypts files on the user’s computer and then replaces the MBR (Master Boot Record). Once Bad Rabbit has done its job, it reboots the user’s PC, which gets stuck into the custom MBR ransom note. The ransom note is almost identical to the one used by NotPetya, in the June outbreak.
They key difference here is that NotPetya actually encrypted the data with Bootkit at boot time and modified MFT as additional technique to encrypted them at OS level (original Petya “feature”). Bad Rabbit only replaces the boot screen. Similar screen design is easily spoofed.
TTPs similarity of Bad Rabbit and NotPetya:
- Use of the same Mimikatz version for Credential Dumping
- Use of SMB shares for Lateral Movement
- Use of WMI for Lateral Movement
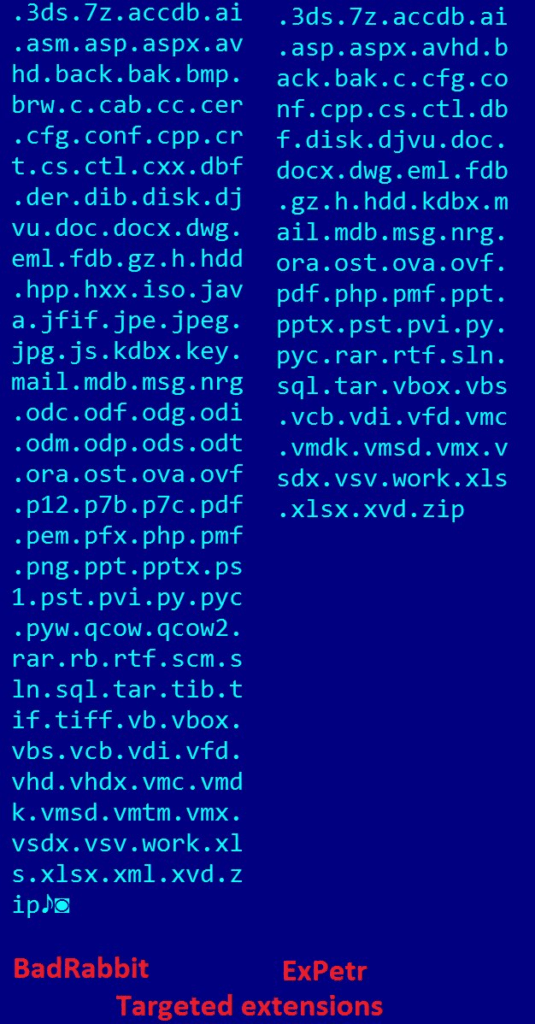
Additionally targeted file extensions are significantly different in Bad Rabbit compared to NotPetya: typical ransomware targets more files (Bad Rabbit) while APT attacks which use ransomware as File Deletion technique go after specific files.
There is also debate on the infection vector as Waterhole attack from hacked website. The piece that does not fit is that the hacked sites are not even a top-100 of popularity in affected countries.
Prevention: host-based vaccines and network protection
Network Protection controls
Block network access to 185.149.120[.]3 on perimeter level devices
Block all infected URLs on security web gateways / proxies.
Host-based Vaccination
The downloaded file named install_flash_player.exe needs to be manually launched by the victim. To operate correctly it needs elevated administrative privileges which it attempts to obtain using the standard UAC prompt. If started it will save the malicious DLL as C:\Windows\infpub.dat and launch it using rundll32.
- Disable WMI service where possible as temporary mitigation measure
- Create the following files C:\Windows\infpub.dat and C:\Windows\cscc.dat and REMOVE ALL PERMISSIONS (inheritance) from these files.
Indicators of Compromise
IP’s
| IP | Source |
| 185.149.120[.]3 | https://www.welivesecurity.com/2017/10/24/bad-rabbit-not-petya-back/http://blog.talosintelligence.com/2017/10/bad-rabbit.html |
| HashOfFile | FileName | Source |
| 0b2f863f4119dc88a22cc97c0a136c88a0127cb026751303b045f7322a8972f6 | cscc.dat | http://blog.talosintelligence.com |
| 16605a4a29a101208457c47ebfde788487be788d | https://www.welivesecurity.com | |
| 1d724f95c61f1055f0d02c2154bbccd3 | infpub.dat | https://securelist.com |
| 2f8c54f9fa8e47596a3beff0031f85360e56840c77f71c6a573ace6f46412035 | http://blog.talosintelligence.com | |
| 301b905eb98d8d6bb559c04bbda26628a942b2c4107c07a02e8f753bdcfe347c | http://blog.talosintelligence.com | |
| 3d05f09fb436c0e4dea85a8c6a12d47502016795df6ea5c8844da1655f1657b4 | dispci.exe | https://www.virustotal.com |
| 413eba3973a15c1a6429d9f170f3e8287f98c21c | https://www.welivesecurity.com | |
| 4f61e154230a64902ae035434690bf2b96b4e018 | page-main.js | https://www.welivesecurity.com |
| 579FD8A0385482FB4C789561A30B09F25671E86422F40EF5CCA2036B28F99648 | infpub.dat | http://blog.talosintelligence.com |
| 630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0da | http://blog.talosintelligence.com | |
| 682ADCB55FE4649F7B22505A54A9DBC454B4090FC2BB84AF7DB5B0908F3B7806 | cscc.dat | https://www.welivesecurity.com |
| 7217fae6f3634cde7d54eba3858e8958eb1e5e85e2c36d968818cdce75a3fae9 | Invoice_file_06565.doc | https://www.hybrid-analysis.com |
| 79116fe99f2b421c52ef64097f0f39b815b20907 | infpub.dat | https://www.welivesecurity.com |
| 80c336a30aa746f5a05a21056e36328b9527c4ace59cd9e2fbb5211e87e5841d | Invoice_file_06565.doc | https://www.hybrid-analysis.com |
| 84ac3d2f1ca70bc83149bec52b00009639e9006f941caed3ca83e4e8e47f64bd | https://www.hybrid-analysis.com | |
| 8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93 | dispci.exe | https://www.hybrid-analysis.com |
| 8fd96bb2ce94146f1b0271d18ba52f176d4ebf8fabd275f1d16d59ed9d91d2da | https://www.hybrid-analysis.com | |
| afeee8b4acff87bc469a6f0364a81ae5d60a2add | dispci.exe | https://www.welivesecurity.com |
| b14d8faf7f0cbcfad051cefe5f39645f | dispci.exe | https://securelist.com |
| de5c8d858e6e41da715dca1c019df0bfb92d32c0 | install_flash_player.exe | https://www.welivesecurity.com |
| fbbdc39af1139aebba4da004475e8839 | install_flash_player.exe | https://securelist.com |
Scheduled Tasks names
| Task name | Source |
| viserion_ | http://blog.talosintelligence.com/2017/10/bad-rabbit.html |
| rhaegal | http://blog.talosintelligence.com/2017/10/bad-rabbit.html |
| drogon | http://blog.talosintelligence.com/2017/10/bad-rabbit.html |
External references
1. https://www.welivesecurity.com/2017/10/24/bad-rabbit-not-petya-back/
2. https://securelist.com/bad-rabbit-ransomware/82851/
3. http://blog.talosintelligence.com/2017/10/bad-rabbit.html
4. https://gist.github.com/roycewilliams/a723aaf8a6ac3ba4f817847610935cfb
5. https://gist.github.com/Belorum/7b57e925a0bcc6ed6a72b6af07006ace
6. https://www.hybrid-analysis.com/sample/8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93?environmentId=100
7. https://www.hybrid-analysis.com/sample/99b695b3d2ce9b0440ce7526fea59f7a4851d83d9a9d9a6cf906417068bc7524?environmentId=100
8. https://twitter.com/craiu/status/922911496497238021
9. https://blog.qualys.com/news/2017/10/24/bad-rabbit-ransomware
10. https://threatprotect.qualys.com/2017/10/24/bad-rabbit-ransomware/?_ga=2.71482960.293546626.1508923179-346340547.1500997518
11. https://analyze.intezer.com/#/analyses/d41e8a98-a106-4b4f-9b7c-fd9e2c80ca7d
12. https://www.bleepingcomputer.com/news/security/bad-rabbit-ransomware-outbreak-hits-eastern-europe/