Intro
This is a practical guide based on Zoom and CheckPoint recommendations crafted with common sense and Zoom usage specific in our Company, aka work from home (WFH) activity as every company in the world now and sales / pre sales activities as a vendor.
Due to the specific nature of our business, in addition to hardening, we do what we are doing the best, we have developed threat detection analytical content for SIEMs based on Zoom reports available over API, proxy logs and workstation logs.
Tiered Approach
All configurable zoom settings can be controlled at 3 levels. Hierarchical inheritance in place:
- Account level (“default” or “locked” state)
- Group level (“default” or “locked” state)
- User level (“default” state)
Default settings – recommended but could be changed by a user. If a setting is changed at the account level, that becomes the default setting for all groups and users in the account unless the setting had been previously changed by a group or user.
Locked settings – obligatory and couldn’t be changed by a user. Each setting can be locked at either the account level or the group level. Locking a setting at the account level means that the setting cannot be changed by any user. Locking the setting at the group level means that members of the group cannot change the setting.
Tech Tips
- For each group that requires different settings, navigate to Group Settings > group_name > Settings.
- To Lock settings at account or group level – click the Lock icon to the right of the option name.
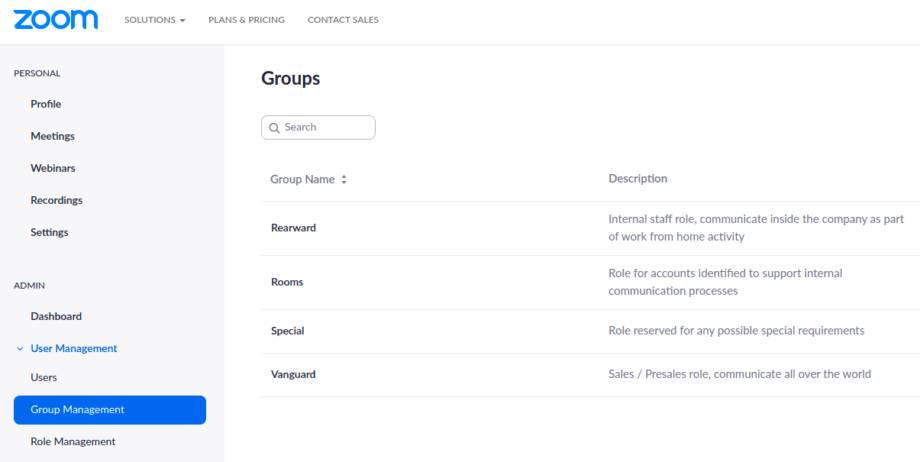
First of all, user groups should be identified based on way of working, internal communication specific and company business specific. As for now we have identified following (yes, this not a constant, we are growing, we are changing):
- “Vanguard” – Sales / Presales role, communicate all over the world, maximum recommended options, minimum restrictions to be more flexible and reach out to all possible clients and customers. All associated risks covered by proper awareness activity and training on how to mitigate crashers activity by Zoom meeting controls.
- “Rearward” – Internal staff role, communicate inside the company as part of work from home activity, one to one, one to many, instant meetings, scheduled stand-ups etc. Communication with the external world is limited. Maximum restrictions and less extensive awareness activity.
- “Rooms” – a role for accounts identified to support internal communication processes, like continuously open rooms etc. Specific restrictions.
- “Special” – role reserved for any possible special requirements. Minimum restrictions. should not be used in a continuous way.
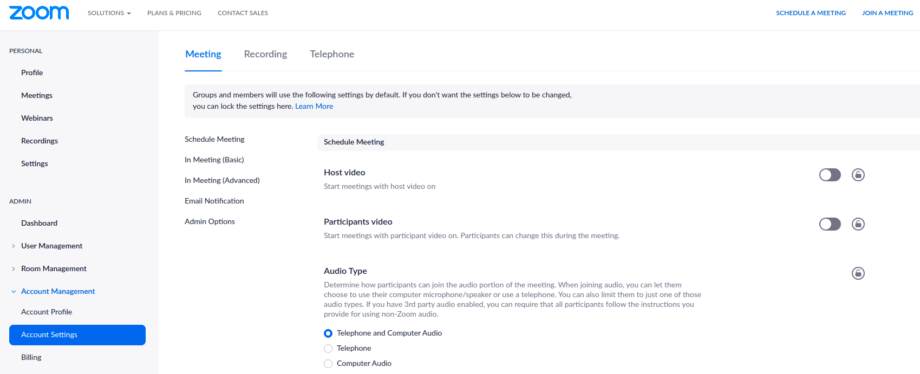
Account-level settings
In details:
- Join before host – disabled default
- Use Personal Meeting ID (PMI) when scheduling a meeting – disabled
- Use Personal Meeting ID (PMI) when starting an instant meeting – disabled
- Only authenticated users can join meetings – enabled default
- Require a password when scheduling new meetings – enabled locked
- Identify guest participants in the meeting/webinar – enabled locked
- Require a password for instant meetings – enabled locked
- Require a password for Personal Meeting ID (PMI) – enabled locked
- Require a password for Room Meeting ID (for Zoom Rooms only) – enabled locked
- Embed password in meeting link for one-click join – enabled default
- Chat – enabled default
- File transfer – disabled locked
- Allow host to put attendee on hold – enabled locked
- Screen sharing – enabled default
- Who can share? – All Participants
- Who can start sharing when someone else is sharing? – Host Only
- Annotation – enabled default
- Whiteboard – enabled default
- Remote control – enabled default
- Allow removed participants to rejoin – disabled locked
- Remote support – disabled default
- Closed captioning – disabled default
- Save Captions – disabled default
- Far end camera control – disabled locked
- Blur snapshot on iOS task switcher – enabled locked
- Local recording – enabled locked
- Hosts can give participants the permission to record locally – off
- Automatic recording – disabled locked
- IP Address Access Control – enabled locked
- Only authenticated users can view cloud recordings – enabled locked
- Recording disclaimer – enabled locked
Group level settings
“Vanguard” group level settings
- Join before host – disabled locked
- Use Personal Meeting ID (PMI) when scheduling a meeting – disabled locked
- Private chat – disabled default
- Can be enabled if required for technical communication of host, co-host, etc.
- Co-host – enabled default
- Show a “Join from your browser” link – enabled default
- Waiting room – enabled locked
“Rearward” group level settings
- Join before host – disabled locked
- Use Personal Meeting ID (PMI) when scheduling a meeting – disabled locked
- Only authenticated users can join meetings – enabled locked
- Private chat – disabled locked
- Remote control – disabled locked
- Waiting room – enabled locked
- Remote support – disabled locked
“Rooms” group level settings
- Join before host – enabled default
- Waiting room – disabled default
Account Security Settings
We have made a decision to use Google for authentication, where we already have password enforcements, 2FA and additional controls in place.
 |
Sign-in methods
Security
User need to input Host Key to claim host role with the length of: 10 |
General and common sense recommendations
- When you share your meeting link on social media or other public forums, that makes your event … extremely public. ANYONE with the link can join your meeting.
- Avoid using your Personal Meeting ID (PMI) to host public events. PMI is basically one continuous meeting and you don’t want randos crashing your personal virtual space after the party’s over. Generate a random meeting ID for meetings where possible.
- According to the research (5), Zoom meeting hosts don’t even have to send out a public link for users to participate in their meetings. Always require a password to join.
- If really required, share random meeting IDs via social networks but send a password by a direct message.
- Never try to open URL links or pictures sent over the Chat.
- Setup proper authentication at account level, Google, Local Passwords with proper controls in place, SAML, 2FA, use authentication relevant to your corporate security policy.
- Familiarize yourself with Zoom’s settings and features so you understand how to protect your virtual space when you need to. How to mute, how to turn off video for participants, to put attendees on hold, etc.
- Configure logs collection from your Zoom account to your SIEM and establish alerting / monitoring mechanisms.
- Logs collection from your proxy server and EDR is mandatory for today’s threat landscape. Just cover zoom specific attacks via these logs.
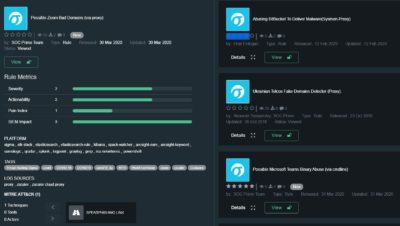
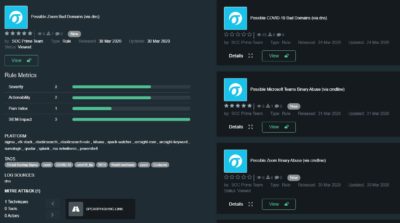
Content to detect Zoom related attacks
Possible Zoom Bad Domains (via proxy) – https://tdm.socprime.com/tdm/info/MrDuoDkETUIP/
Possible Zoom Bad Domains (via dns) – https://tdm.socprime.com/tdm/info/TWstmhIEa1oA/
Possible Zoom Binary Abuse (via cmdline) – https://tdm.socprime.com/tdm/info/BMUtqKem63oL/
Possible NTLM Credential Leak via Unwanted External UNC Path (via cmdline) – https://tdm.socprime.com/tdm/info/i71EA49sF8jW/
References
———————————-
- https://blog.zoom.us/wordpress/2020/03/20/keep-the-party-crashers-from-crashing-your-zoom-event/
- https://threatpost.com/as-zoom-booms-incidents-of-zoombombing-become-a-growing-nuisance/154187/
- https://support.zoom.us/hc/en-us/articles/115005269866-Using-Tiered-Settings
- https://blog.checkpoint.com/2020/03/26/whos-zooming-who-guidelines-on-how-to-use-zoom-safely/
- https://support.zoom.us/hc/en-us/articles/360034291052-Predicting-Zoom-Meeting-IDs
- https://support.zoom.us/hc/en-us/articles/360034675592-Advanced-security-settings
- https://support.zoom.us/hc/en-us/articles/360038247071-Setting-up-and-using-two-factor-authentication
- https://support.zoom.us/hc/en-us/articles/360032748331-Using-Operation-Logs
- https://www.bleepingcomputer.com/news/security/zoom-client-leaks-windows-login-credentials-to-attackers/
- https://library.myguide.org/myguide-library/categories/zoom/zoom-web/zoom-web-guides