What Is Threat-Informed Defense?

Table of contents:
Organizations have to constantly struggle with an avalanche of threats while relying on a straightforward and proactive method to dynamically assess the performance of their security programs. Introducing a threat-informed defense strategy empowers organizations to focus on known threats and dynamically test defenses by equipping teams with better data and insights into their security program performance.
This article covers the concept of threat-informed defense as a game-changing cybersecurity strategy backed by peer-driven collective expertise. Learn how to seamlessly implement this innovative approach into your security program to maximize its efficiency powered by SOC Prime’s industry-first solutions for active threat-informed defense.
How Threat-Informed Defense Changes the Game
Threat-informed defense (TID) is an innovative community-based approach to cybersecurity that provides insights into the strategies and tools employed by adversaries to proactively detect and mitigate cyber attacks based on real-time data and analysis. Before the concept of TID gained prominence, cyber defenders struggled with the following hurdles:
- Reactive Security Measures. Cybersecurity practices were often more reactive and focused on historical data along with traditional security measures designed to defend against known threats and vulnerabilities, rather than keeping up with rapidly evolving attacks.
- Signature-Based Detection Systems. The traditional approach to cybersecurity was primarily based on signature-based detection systems, which relied on known patterns or signatures of offensive operations or malware, failing to detect and prevent new or unknown threats.
- Securing the Perimeter Strategy. Securing the perimeter was designed to protect an organization’s infrastructure by establishing a strong boundary between the internal network and the external environment. However, this approach failed to provide comprehensive visibility across all assets and could lead to cyber defense blind spots.
- Autonomous Incident Response. Traditional security measures focused on individual components rather than considering the broader context of the organization’s ecosystem. There was often a lack of standardized mechanisms and platforms for sharing CTI among peers.
The rise of APTs, zero-day exploits, and other sophisticated attack techniques highlighted the need for a more proactive and intelligence-driven defense strategy. A shift toward a threat-informed defense strategy arose from the need to address the evolving nature of the dynamic attack surface while preparing teams for the most relevant threats and gaining in-depth visibility into the effectiveness of the organization’s security measures.
How Does Threat-Informed Defense Impact the Cybersecurity Strategy?
Progressive organizations can gain from the following key advantages by enabling active threat-informed defense as a future-proof cybersecurity strategy:
- Continuous CTI Sharing. TID integrates threat intelligence into security operations and decision-making processes, empowering organizations to effectively identify and prioritize the most critical threats and allocate resources accordingly.
- Proactive Threat Detection. Combining CTI and MITRE ATT&CK® enables organizations to evolve from a reactive to a proactive approach, ensuring adaptive defenses to counter emerging threats.
- Data-Driven Alignment of Threat and Risk Management. TID empowers organizations to minimize cyber defense blind spots by aligning their security controls and practices with known threats, thus eliminating data breach risks.
- Continuous Improvement with Collective Cyber Defense. TID fosters an environment that promotes ongoing enhancement backed by the combined expertise of Blue, Red, and Purple Teams to test and constantly improve their defenses in a collaborative manner to drive up effectiveness. Through engagement in Green Team, organizations shape the future direction of threat-informed defense for the AI era by advancing it on a global scale.
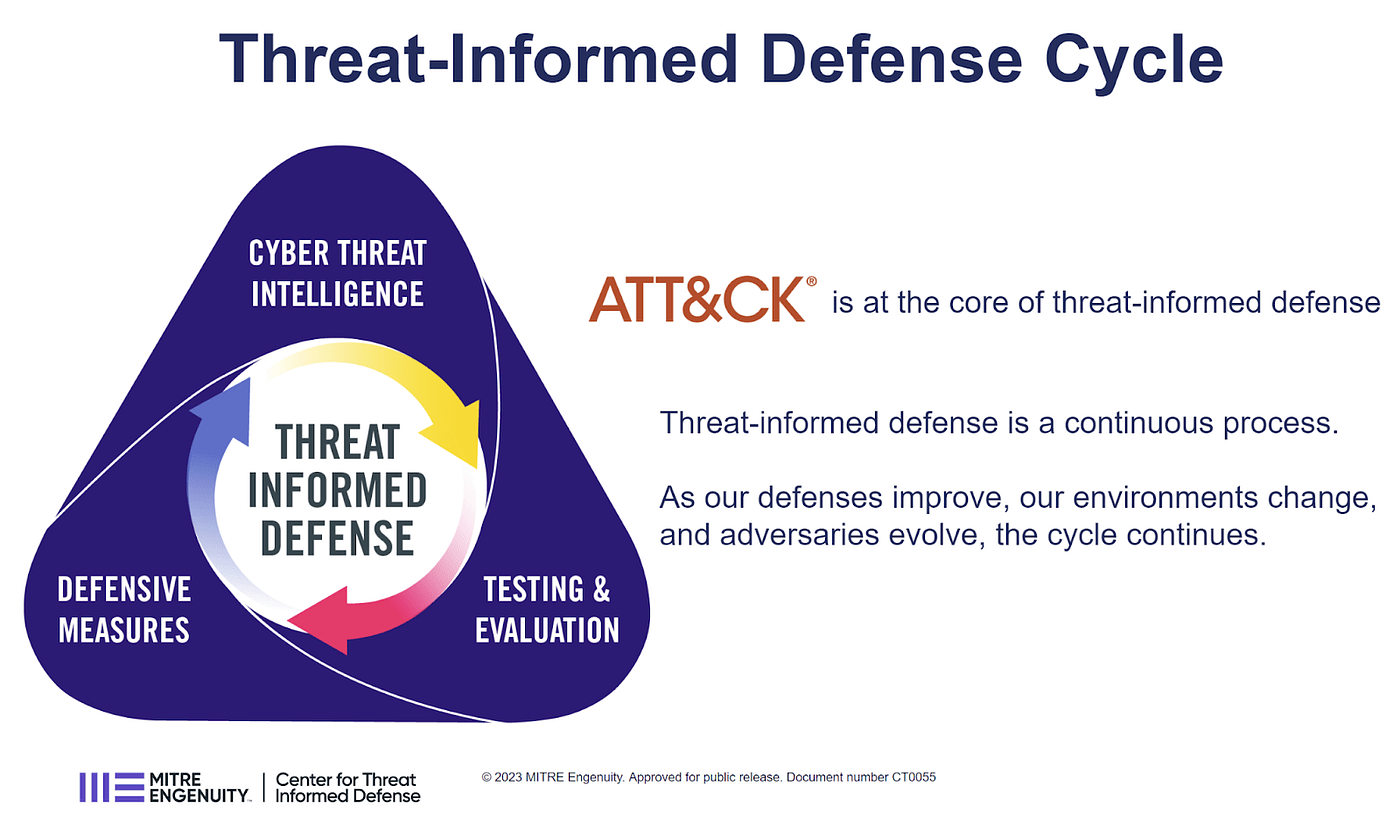
Figure 1: TID cycle
SOC Prime equips security teams with innovative tools to enable active threat-informed defense backed by collective industry expertise that relies on MITRE ATT&CK, Sigma, and fosters Green Team evolution. As one of the active TID pillars, the concept of Green Team creates the environment for seamless knowledge sharing where peers coordinate their efforts to defend against emerging threats striving to make defense cost-efficient, fast, and far less stressful.
How to Implement a Threat-Informed Defense Strategy with SOC Prime
According to the AttackIQ Guide, TID is an essential ingredient in an efficient cybersecurity strategy and key to prioritizing and optimizing security decisions. This approach goes beyond acquiring knowledge; it also drives actionable changes. To identify the appropriate steps to take promptly and with efficient resource allocation, the next important phase is optimizing security measures. Fusing threat intel with MITRE ATT&CK enables organizations to smoothly transition to a proactive cybersecurity approach.
SOC Prime is dedicated to evolving collective cyber defense as a driving force to outsmart and outpace the coordinated efforts of offensive forces. By relying on the industry-first platform for collective cyber defense, security teams are equipped with next-gen solutions that foster continuous threat intel exchange and minimize risks while maximizing SOC investments.
Threat Detection Marketplace helps teams adapt an active threat-informed defense strategy into their regular security practices by accessing the world’s largest feed of curated detection algorithms mapped to ATT&CK and enriched with tailored intelligence. With the Threat Detection Marketplace, organizations can preempt emerging cyber attacks, thus implementing a proactive cybersecurity approach.
Attack Detective acts as an industry-first SaaS for active threat-informed defense, enabling organizations to automatically validate detection stack in less than 300 seconds, gain real-time attack surface visibility, investigate existing risks matching custom threat hunting scenarios, and prioritize detection procedures to find breaches before adversaries have a chance to attack.
Uncoder AI serves as a single IDE for active threat-informed defense. The solution delivers sub-second performance on any detection engineering task and enables on-the-fly cross-platform query translation for 44 SIEM, EDR, XDR, and Data Lake native languages or open-source language formats like Sigma. Uncoder AI fosters collective cyber defense globally, enabling detection code writing, exchange, and enhancement in a trusted environment while protecting the intellectual property of threat researchers.
Join Discord to connect to your peers, keep up with the freshest news and trends in the industry, and learn more about how to successfully instill and mature an active threat-informed mindset in your security program.