The method of a secure cryptographic key exchange was introduced by Whitfield Diffie and Martin Hellman in 1976. Cool thing about the public and private key pair is that the decryption key cannot be deciphered in any way from an encryption key.
This feature is exactly what’s exploited by ransomware actors who encrypt data and demand high payments in exchange for a decryption key or keys (when they encrypt directories and/or files separately) so that the victim can access their data again.
However, people that are well-versed in digital forensics know that special tools can help to painlessly decrypt or recover even completely destroyed data. Backups work, too. That’s why adversaries needed another leverage to use on high-profile targets. And they found it – multi-extortion. Research shows that 2021 saw an 85% increase in extortion since 2020, with 2,566 victims being exposed to leak sites and threatened of follow-on attacks.
That’s why it’s important to be able to detect the earliest signs of ransomware presence. All the patterns that occur prior to the ransom note must be identified before they do any harm.
According to SOC Prime’s annual Detection as Code Innovation Report, ransomware continued to be a pressing challenge throughout 2021-2022, with the increasing sophistication of intrusions and escalating volumes of high-profile ransomware attacks.
Definition of Ransomware Detection
Ransomware detection is a set of techniques, processes, and solutions that are used to identify adversary behavior associated with ransomware. It is mostly used on a professional level as part of required cybersecurity policies in security operations centers (SOC) that work for enterprises.
You might think, why detect ransomware? If it has already infected a system, it shows a ransom note, and there’s no way back. Yes, but there are lots of activities that are performed in the background before a ransom note shows up. This might be network discovery, escalation of privileges, data exfiltration, and encryption. SOC Analysts want to recognize all these behaviors as early as possible before they reach a point of no return. Provided that ransomware is also designed to evade detection, it’s not an easy task to do.
Examples of Ransomware Detection
Some signs of suspicious activity allow security researchers to suggest a possible presence of ransomware. Enterprise attacks are usually precisely targeted, so attackers need a certain degree of mastery to infiltrate a highly protected entity, get to the valuable data, and initiate impact. While actors are taking their time to strategize the next move, it’s a great opportunity to detect them.
Typically, the following digital systems can be checked for early signs of ransomware:
- Network
-
-
- Anomalous volumes of traffic – might be signs of data exfiltration.
- Logon from a suspicious location – might be a compromised account or a C2 server connection.
- Downloads – check for zero-click downloads, especially through wireless connections.
-
- Endpoints
-
-
- Scheduled tasks – need to be checked for injections.
- Files – might be malicious or an infected legit one.
- Code Signing System – check for compromised certificates.
- Communication – check for phishing, insider job, man-in-the-middle attacks.
-
- Cloud
-
-
- API – most of the things in the cloud are enabled by APIs, so it’s the weakest point. Control plane might be exploited for execution.
- Vulnerabilities – might be exploited at various stages of attacks. Even the patched ones might resurface with a new adversary procedure that finds a way around the previous patches.
- Command-line tools – often abused to look for directories storing credentials. Try to detect suspicious network discovery, lateral movement, and privilege escalation.
-
- DevOps Environments
-
-
- Development tools – some attackers will aim at compromising development and CI/CD environments, toolchains, and open-source libraries, which is especially challenging to detect.
- Secrets – the nature of the coding practice implies that developers have multiple privileges. Their credentials, session tokens, etc., are a ripe target for cyber-attacks.
- Native vulnerabilities – programming languages and cryptography algorithms naturally have lots of vulnerabilities. Their behavior is extremely hard to predict at the coding phase, while even a single exploit can easily go viral through thousands of dependencies.
-
Cybersecurity architecture might also include solutions like Host Intrusion Prevention Systems (HIPS) can block suspicious modifications, i.e., encryption. Web Application Firewalls (WAF), Intrusion Prevention systems (IPS), and Intrusion Detection Systems (IDS) also might be useful. Even the smallest organization processes immense amounts of data daily, so there must be some automated layer that acts as a safety net for general volumes of traffic. Keep in mind that many of those devices (except for stateful inspection firewalls) do not consider the context.
How Does Ransomware Detection Work?
As you know, modern ransomware is much more than just a data encryptor with a screen locker. So, the practice of detecting ransomware might not just be about ransomware. Instead, Security Analysts want to understand the overall health of their networks to spot the slightest signs of maliciousness. In other words, this might not sound too encouraging, but the ransomware kill chain might include packs of all kinds of malware. There’s a tendency to shift left and weaponize vulnerabilities at different stages of a software supply chain, as shown by Microsoft Research:
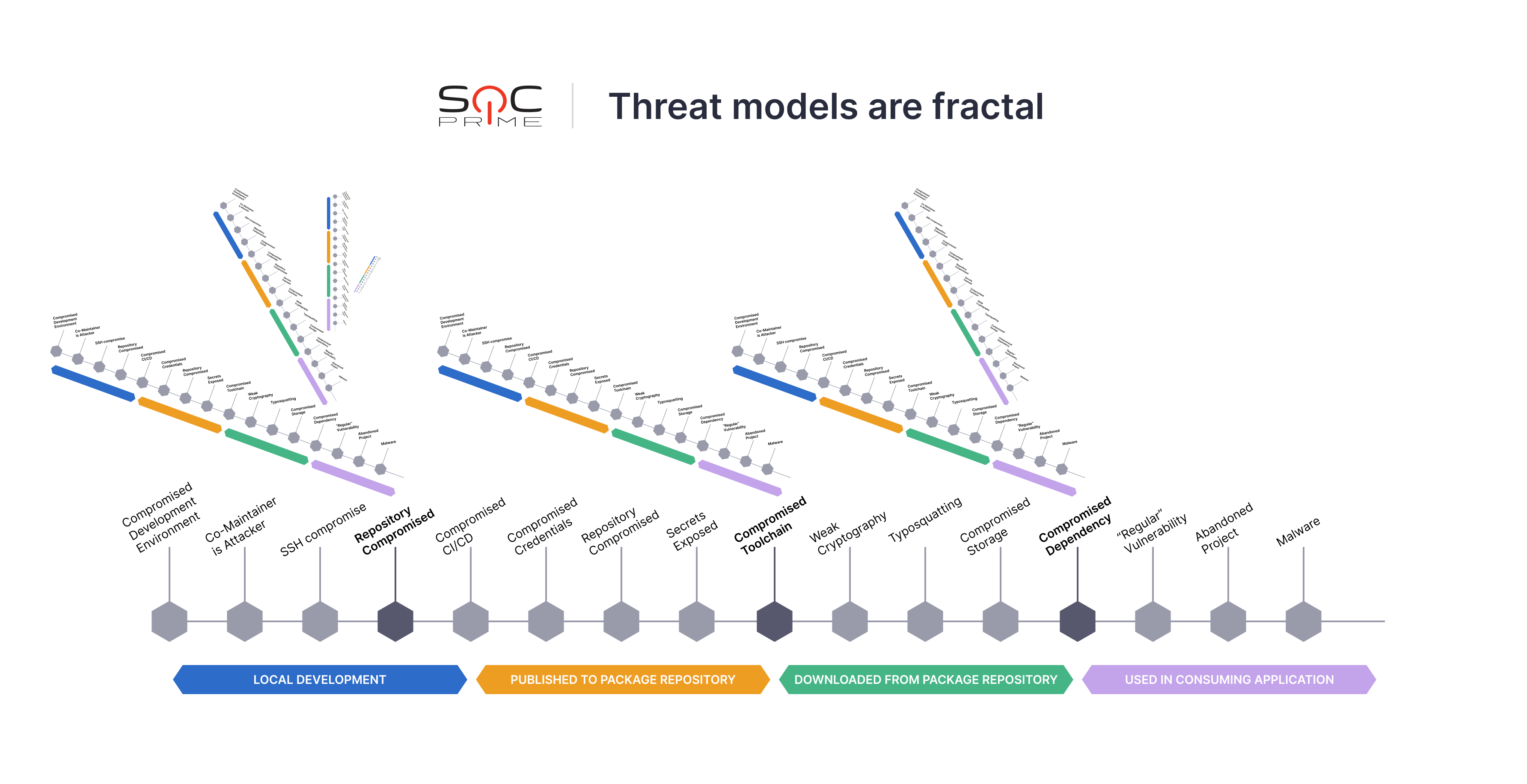
By the way, if the organization is on the top players list (like a transcontinental bank) or deals with critical infrastructure (like oil supply, communications, etc.), they should pay special attention to pre-attack patterns. The success of reconnaissance means everything to APT attackers; however, strictly technical security controls won’t cover it. Here, organizations need to circle back to risk policies and information that they decide to collect or observe. Information that they share is also critical, so a PR strategy must be risk-assessed, too. In fact, an official FBI warning says that ransomware actors tend to track mergers and acquisitions and craft their attacks precisely at that time. How do they know about such major financial events? From the news.
When it comes to technical security controls, focus on what you can track. For example:
- Real-time network analysis. Here you want to look at what happens East-South and North-West, but also at containers, VMs, what users do, what processes are running, and where they are coming from. Services like Cisco Stealthwatch can analyze even encrypted traffic (and it’s vendor-agnostic).
- Data at rest. This might be a blind spot that adversaries gladly use. Look for suspicious action on backup storage like scanning, power outages, and syncing with the cloud. A malware might sit quietly until the ransomware hits, and then they’ll block data recovery. It might be smart to sanitize the data that is no longer in use and run regular security checks on what’s retained.
- Logs. SIEM aggregates all the data from log sources if configured right. Then, detection rules are applied to search for malicious behavior. If you ingest threat intelligence, AI can take care of some cases. Here’s a list of data sources that can provide logs.
- Files. Suspicious files are quarantined and sent to Malware Analysis. Sometimes, malicious samples are specifically downloaded or caught in a honeypot by Security Analysts that want to deconstruct it and see how it works. Handle with care!
Now, we’ll look at some of the ransomware detection techniques. You’ve probably heard about signature-based, behavior-based, and deception detection, so let’s take a different approach.
Ransomware Detection Techniques
In ransomware detection, the Confidentiality, Integrity, and Availability triad (CIA) should always be in mind. It’s the core and purpose of every security policy. As simple as it sounds, ransomware detection can be boiled down to three major terms:
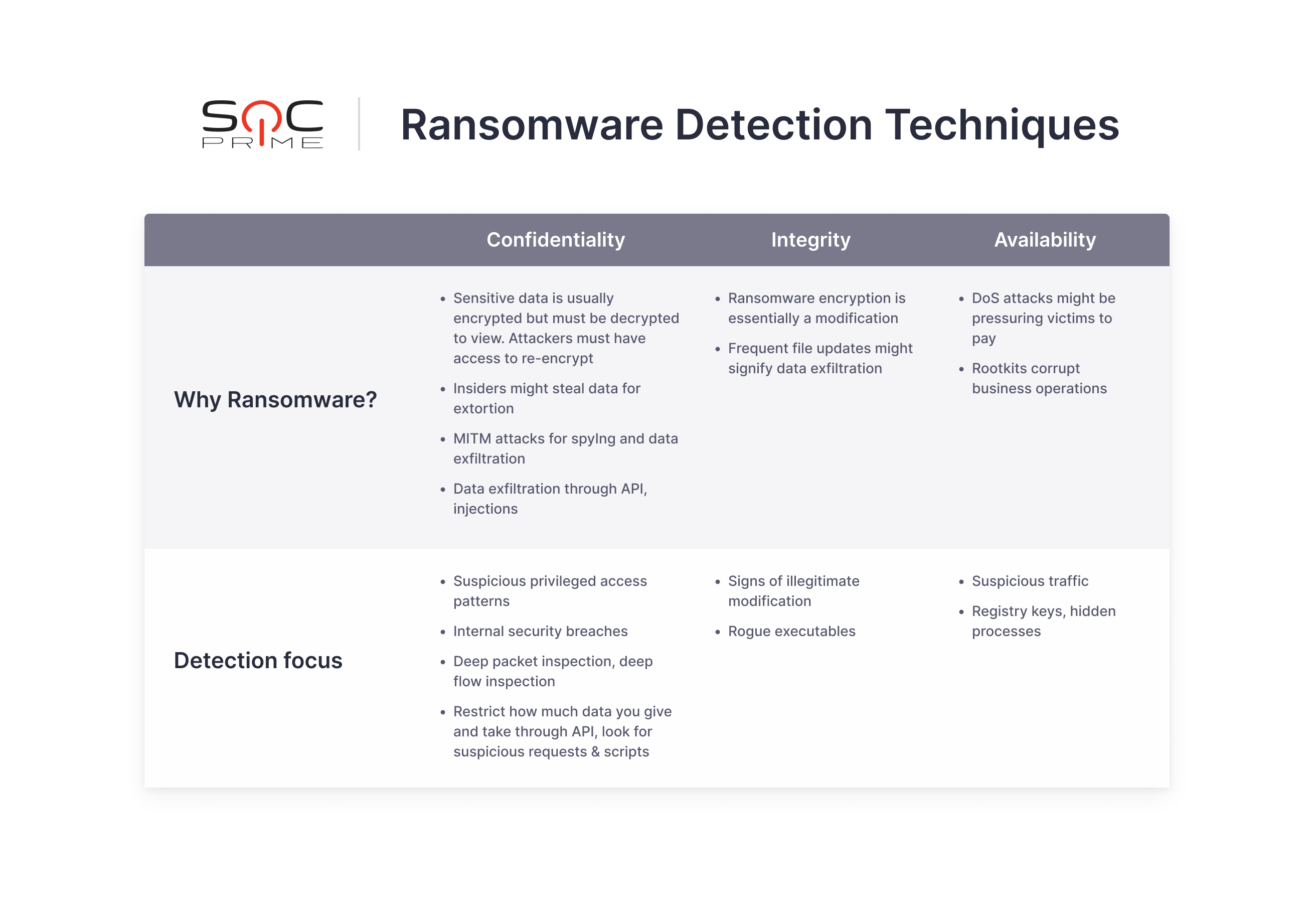
Of course, this is not an exhaustive list. You can make your own table, sticking to key concepts like the ones above, and jot down useful ideas that you come across. Organizing your thoughts along the way is extremely important because, with the vast amounts of information to process each day, some valuable thoughts might be lost. Also, here’s a structured report on ransomware TTPs mapped to MITRE ATT&CK®. It might help to focus on ransomware trends to prioritize detection.
Some of the ransomware detection techniques might be the following.
Preventive Measures
Obviously, detecting ransomware shouldn’t be conducted without due diligence and due care. Because if the sensitive and proprietary data is not duly protected, there is no point in waiting to see what happens and detecting everything that might come your way.
The process of protecting data usually starts with the classification of the business-critical information that’s either in use or at rest. The labels of sensitivity are attached to different kinds of informational sources. Once it’s done, the SOC team can start configuring cybersecurity baselines. A data custodian might be assigned to maintain the asset’s security.
Preventive security controls are implemented across different levels:
- Network
Traffic filtering, load balancing. Automatic blocking of malicious scripts and downloads
- Zero-Trust Architecture
Access management – need-to-know basis, separation of duties
- Software Level
Trusted Computing Base (TCB), Software composition analysis, security tests in CI/CD pipeline (Static application security testing (SAST), Container image–scanning tools, Dynamic application security testing (DAST), Runtime application self-protection (RASP), Web application firewalls (WAFs))
- Physical Level
Trusted Platform Module (TPM), backups
Threat Hunting
Some events might look like absolutely legitimate ones on the surface, however, be malicious in nature. Preventive controls might not catch them. Passive detection either. When such a sophisticated attack kicks in, it’s time to do some Threat Hunting. Note that it’s not necessary to have an incident per se. Instead, Threat Hunting premise is that something is wrong, but we don’t see it.
Threat Hunting can be based on three major approaches:
- Hypothesis-driven
- Intelligence-driven
- Custom
If you want to know more, jump to our guide on Threat Hunting and Threat Hunting Hypotheses examples. Also, consider learning about audit trails.
Overall, the context that surrounds an event plays a huge part in custom threat investigation. For example, the Windows built-in command AT (at.exe) might potentially be used by an attacker, but it also might’ve been used by an administrator. That’s why it’s essential to check the local context, like which commands were scheduled. A Threat Hunter might also ask questions like:
- What happened before?
- What happened after?
- What else happened on the network?
- What happened in other networks (Threat Intelligence)
Situational awareness and professional experience of a Security Engineer might be vital in reducing the time of identifying and triaging critical threats. However, it’s also necessary to challenge your assumptions instead of trying to gather only the pieces of evidence that would favor your hypothesis. With intelligence-driven Threat Hunting, it might be easier to know how to detect ransomware because you’re looking for specific occurrences that match with what you’ve seen in a threat intel feed.
Layered Defense
Logical reasoning behind the layered defense is simple. Implement security on all the layers of digital infrastructure to be able to intercept an attack at any of them, plus be able to identify ransomware in several different ways. It’s like insurance – if one layer didn’t catch malware, another one might be able to do it.
The success of detective controls largely depends on being able to provide a constant stream of relevant detection algorithms aimed at identifying different ways of vulnerabilities’ exploitation. To make the detection process faster and the code reusable across different tools and solutions, a vendor-agnostic Sigma format might be used. Explore SOC Prime’s Cyber Threats Search Engine to find a rich pool of Sigma rules for ransomware detection, enriched with relevant intelligence and MITRE ATT&CK mapping for streamlined cyber threat investigation.
Review and Improve
Finally, no security policy is good enough to last forever. Regular assessment, analysis, and review are necessary to maintain the utmost efficiency of ransomware detection activities.
Security professionals often ask: how do we make sure that detection rules actually work?
One of the interesting ways to do it was introduced by the Director of Detection and Response at Google, Tim Nguyen. He says that “Good is a matter of manual review and scrutiny.” At Google, they have weekly reviews of cases, comparing metrics like time-to-triage and the actual response to a threat. That’s a fresh approach, as opposed to tracking Mean Time to Detect (MTTD).
Most Dangerous Ransomware in 2022
GuidePoint Research and Intelligence Team reveals that Lockbit 2.0 has been the most consistent ransomware actor that attacked 208 victims in Q2, 2022. Other active groups mentioned in the report are Conti, Alphv, and Blackbasta. The most targeted country, according to researchers, has been the US. In June 2022, a new version of Lockbit 3.0 was released, but the activity of ransomware operators since then is not covered in the report.
Digital Shadows saw an increase in Q2 ransomware activity compared to Q1, 2022. They also discuss the infamous Conti shutdown after a massive data leak and a fake Lockbit attack on Mandiant after the latter disclosed some info. Despite the fall of the giants and the termination of many data-leak websites, an increased number of newcomers has shown rapid growth. Black Basta is also mentioned as one of the most active. After the latest REvil raids and arrests, researchers have also seen some activity, but not a highly successful one.
TechTarget created a ransomware attacks database – check it out for a quick look at the latest attacks. Also, Google’s Threat Analysis Group (TAG) recently published important updates on post-Conti activity based on CERT-UA findings and their own research from April to August 2022.
Latest Ransomware Detections
Following the timeline and context of every threat might be overwhelming. Security Engineers can use SOC Prime’s Cyber Threats Search Engine to track the detections of the latest threats. Instant access to Sigma rules, as well as vendor-specific query formats, helps to reduce time-to-triage while staying in control of TTP coverage. Every detection is mapped to MITRE ATT&CK and comes with all the relevant CTI context.
Check out the hottest ransomware detection rules here:
And if you feel like you would like to contribute and monetize your cyber experience, discover our Threat Bounty Program – a crowdsourcing initiative where Security Engineers from around the world collaborate, enriching our continuous flow of Detection-as-Code content.




