Detecting insider access to sensitive data—like password documents—is a challenge for even mature SOC teams, especially when the activity is wrapped in benign processes like Notepad or triggered via Windows Explorer. While SentinelOne provides robust telemetry, interpreting detection rules often requires navigating multi-condition logic.
That’s where Uncoder AI’s AI-generated Decision Tree transforms the workflow. Instead of reading through a dense SentinelOne event query, security analysts now get a step-by-step logic tree, making intent and scope immediately understandable.
The Detection Logic: Password File Discovery via Notepad
This rule is crafted to catch situations where a user opens password-related files (e.g., password.txt, password.xls) through Notepad, and the action is launched by explorer.exe—a telltale sign of interactive file browsing.
The detection flags potential:
- Insider reconnaissance
- Manual data exfiltration attempts
- Non-compliant access to protected credentials
How the AI-generated Decision Tree Helped
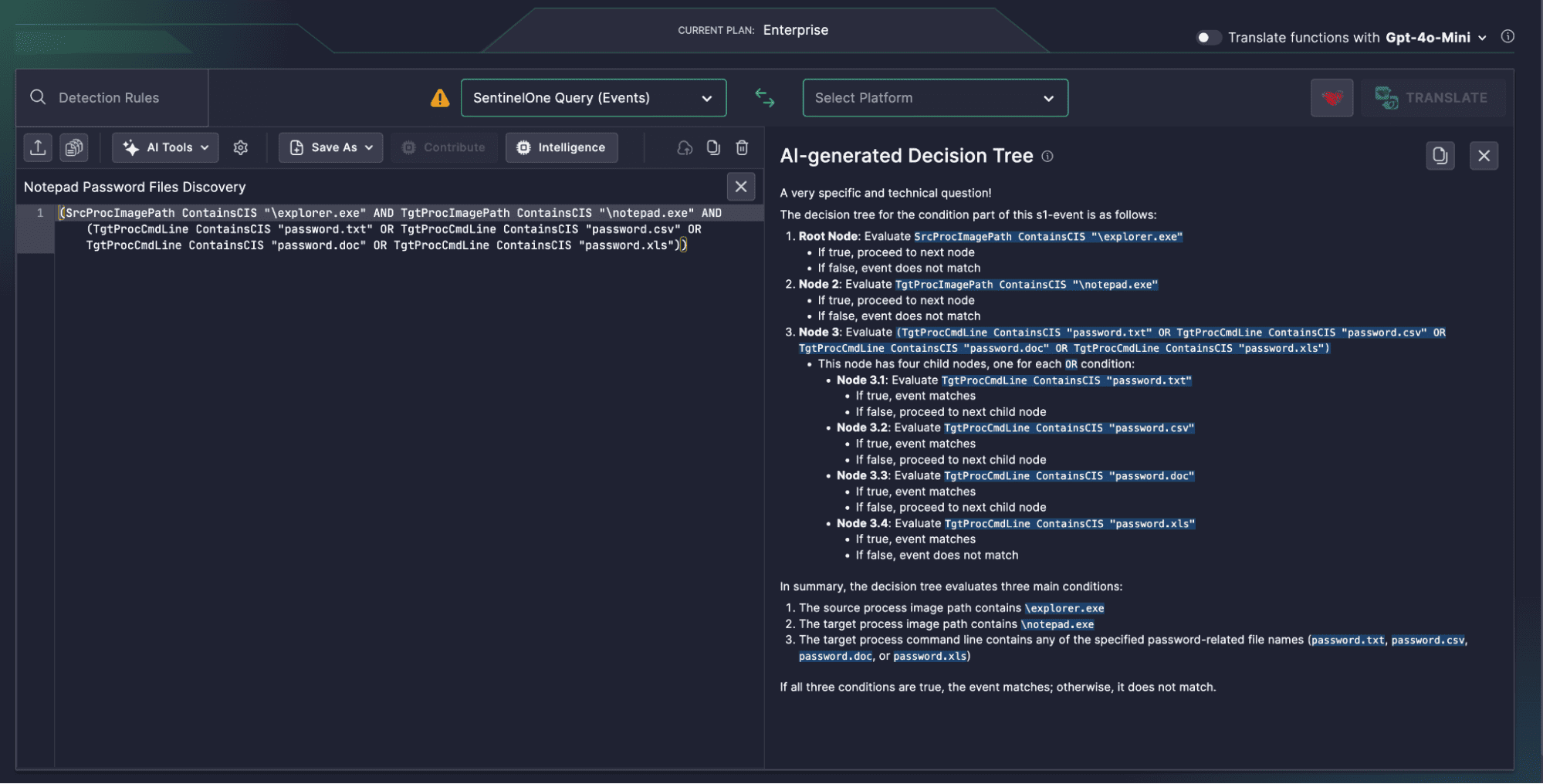
Uncoder AI’s Decision Tree broke down the query into three sequential checks:
- Explorer.exe as the parent process
- Notepad.exe as the executable accessing the file
- Password-related keywords in the filename:
.txt,.csv,.doc,.xls
Each condition is clearly structured as a node, visualizing the flow like a decision tree:
- If Node 1 matches, proceed to Node 2
- If Node 2 matches, evaluate password indicators
- Only if all three match does the rule trigger
This approach provides unmatched clarity—especially when sharing detections across teams or building playbooks for insider threat programs.
Operational Benefits
- Triage Time Reduced: Analysts no longer need to parse through nested logic manually
- Audit-Friendly Structure: Easy to document and explain in internal reviews or compliance checks
- Improved Accuracy: Better understanding means fewer misfires or overlooked risk signals
When dealing with sensitive data access—especially potential password exfiltration—understanding the “how” and “why” of detection logic is just as important as the alert itself.
From Rule to Readability: Uncoder AI in Action
The AI-generated Decision Tree in Uncoder AI doesn’t just translate query language. It teaches the logic, guides response prioritization, and makes complex detection rules instantly usable across SOC roles.




