SOC Prime is thrilled to announce that Uncoder CTI, introduced with the release of the SOC Prime platform for collaborative cyber defense, is now available for public use at https://cti.uncoder.io/. From now, threat intelligence analysts and threat hunters regardless of their experience in the field can try on-the-spot IOC-based hunting for threats using Uncoder CTI. The public Uncoder CTI version for generating instant IOC queries customized to the team’s security needs is now 100% free of charge and doesn’t require registration.
In this blog, you can find guidelines on how to get started with Uncoder CTI to make your threat hunting experience easier, faster, and simpler.
Uncoder CTI was designed by the SOC Prime Team to supercharge threat hunting with cyber threat intelligence and streamline IOC matching for maximum performance in the applied SIEM or XDR. Like Uncoder.IO, this SOC Prime’s innovation enables cross-tool support and can be applied across multiple security solutions. With Unocoder CTI, threat intelligence analysts and threat hunters can generate custom queries for 15+ SIEM & XDR technologies, including Microsoft Azure Sentinel, Chronicle Security, Elastic Stack, and Splunk.
We Care About Your Privacy
SOC Prime attaches great importance to the privacy of user data, which is also reflected in the Uncoder CTI privacy notice visible to anyone who first opens the tool. SOC Prime does not store IOC data uploaded to Uncoder CTI, and no data is shared with third parties. Access to IOC data is only available for security performers running each particular Uncoder CTI session.
Uploading IOCs
Insert a file containing IOCs directly into the left hand-side window or import it by clicking the Upload IOCs button. Please select the files in the acceptable format (CSV, JSON, or TXT).
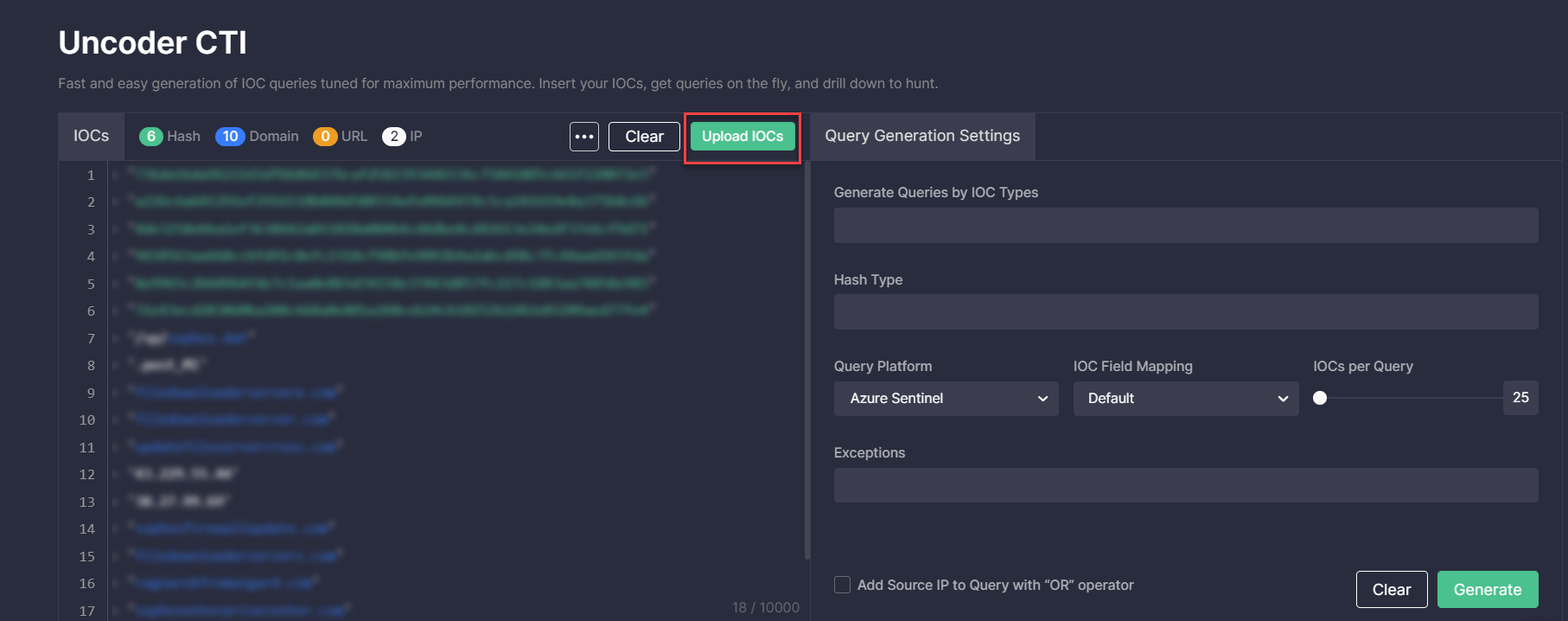
Uncoder CTI already includes default settings that prevent syntax errors and parsing issues through automatic replacement of certain symbols and keywords. Teams can customize these settings by clicking the More button and selecting an option to replace certain character combinations in the content to be parsed:
- Select all — all listed replacement options are applied
- Replace (.) [.] {.} with dot
- Replace hxxp with http
- Exclude private and reserved networks (like 0.0.0.0/8, 10.0.0.0/8, etc.)
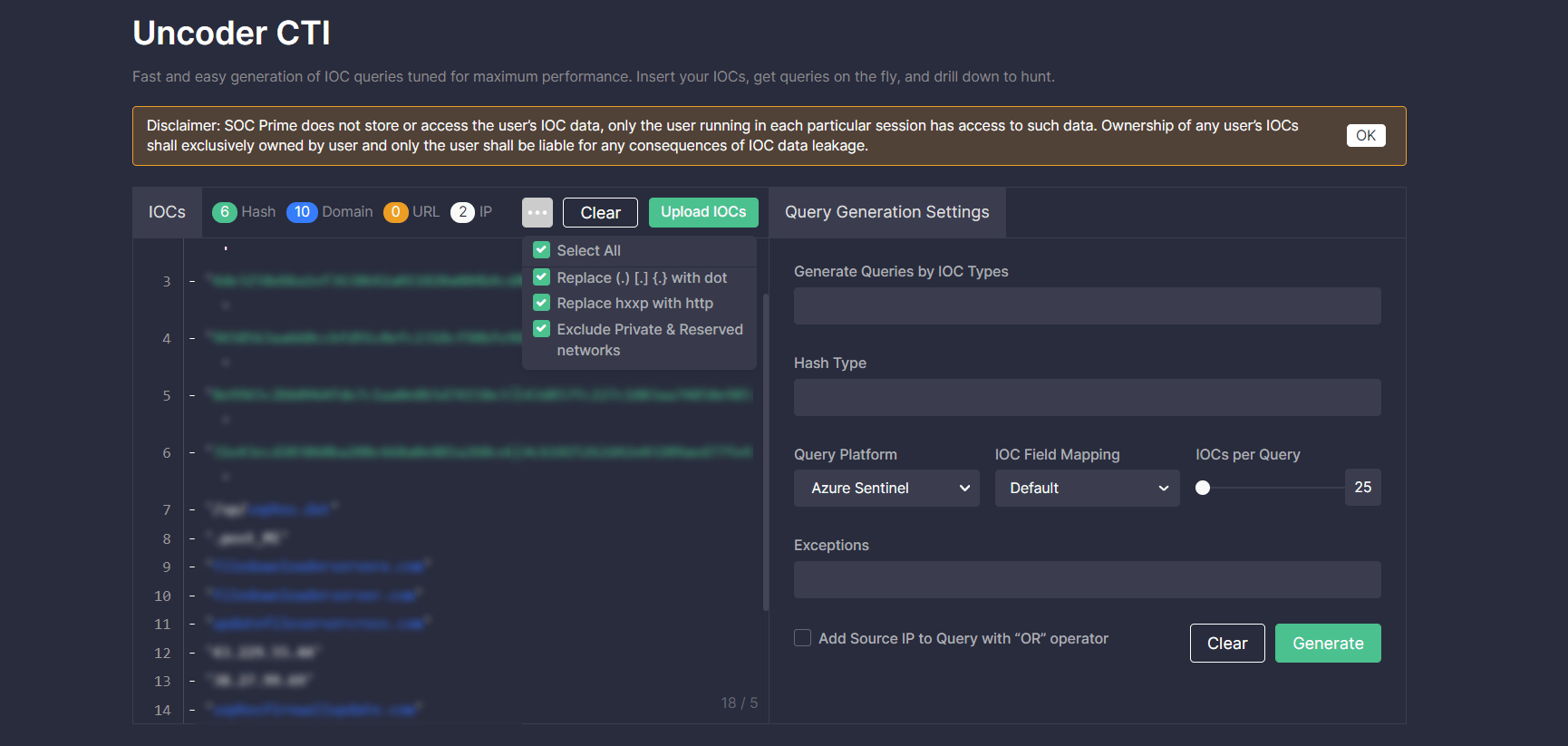
Query Generation Settings
To customize the added IOC query to your security needs in the Query Generation Settings, take these steps:
- Select IOC types that will be used in your query (IP, Hash, Domain, or URL).
- Select the hash type if needed (MD5, SHA-1, SHA-256, SHA-512).
- Select the SIEM or XDR in which you want to run the query.
- Optionally, you can create the custom IOC field mapping to adjust the default parameters of the technology in use to your specific data schema.
- Use a slider to set the number of IOCs per query.
- Optionally, you can add exceptions to exclude certain IOCs from your queries and decrease the number of false positives. For instance, you can enter here 8.8.8.8 IP, private subnets, or other typical CTI report errors.
- Additionally, you can include the source IP in your query with the “OR” operator by selecting the corresponding checkbox.
- Click the Generate button.
|
Note: To configure a new IOC field mapping profile, you need to register for the SOC Prime platform or log in using your existing account. |
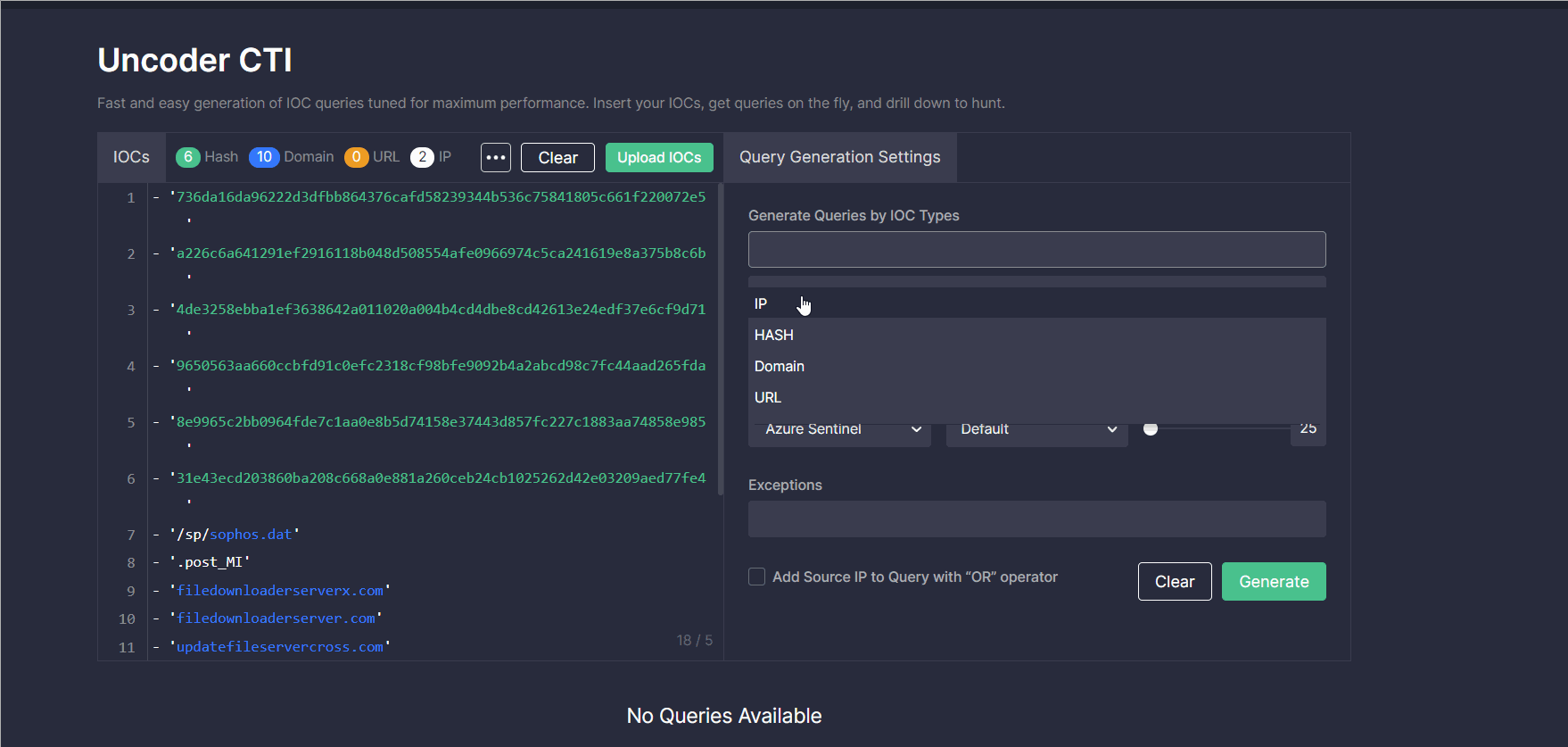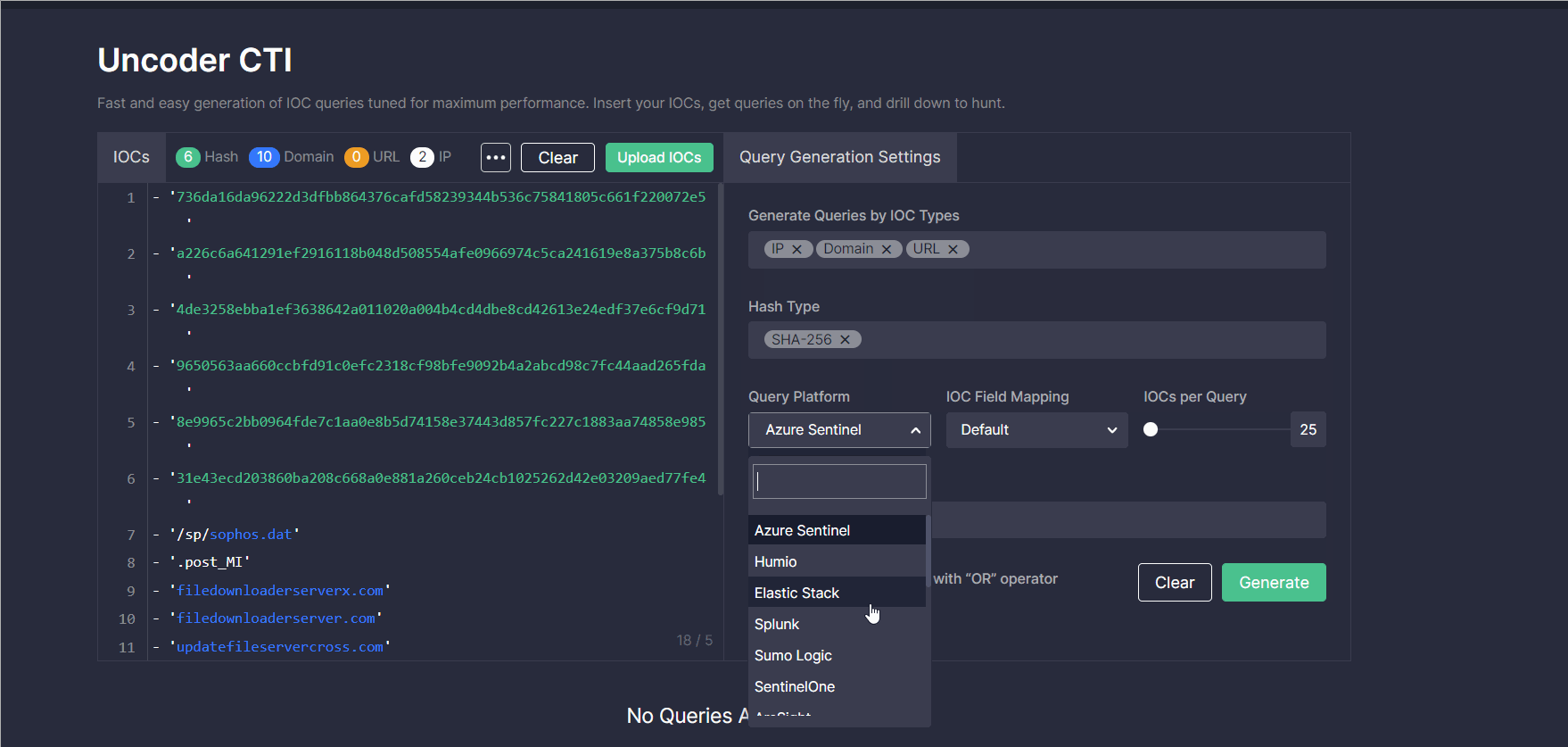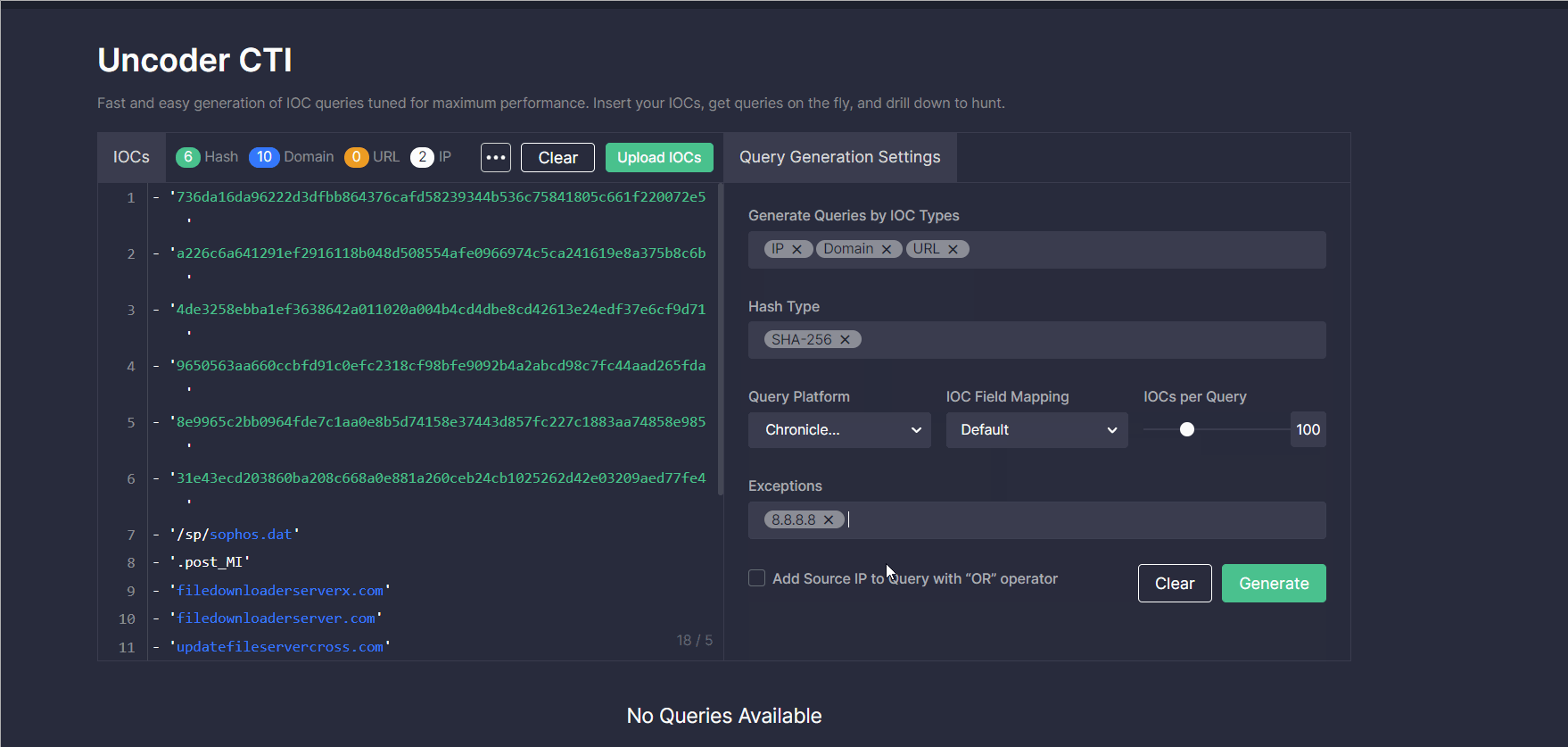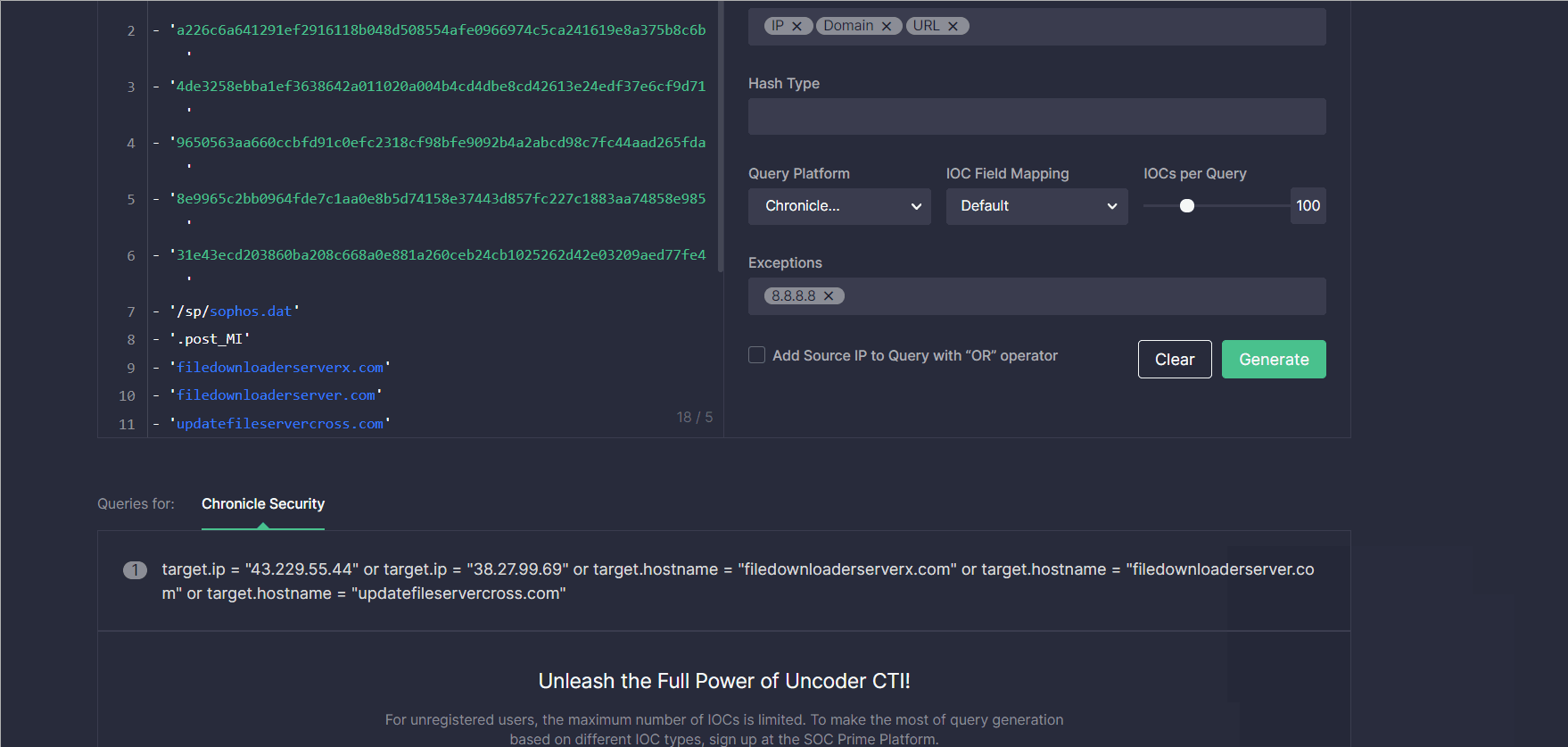
Drilling Down to Hunt in Your SIEM or XDR
The generated custom IOC query will be displayed below. Threat intelligence analysts and threat hunters can run a query in the selected environment by copying and then pasting it directly to the SIEM or XDR instance.
Alternatively, Uncoder CTI allows automatically sending queries to the security solution in use.
|
Note: To leverage this capability, security performers need to sign up or log in to the SOC Prime platform and configure the corresponding API environment using the Platform Environments settings. |
Choose how to grab the generated hunting query with one of the action buttons that appear when hovering over the query code.
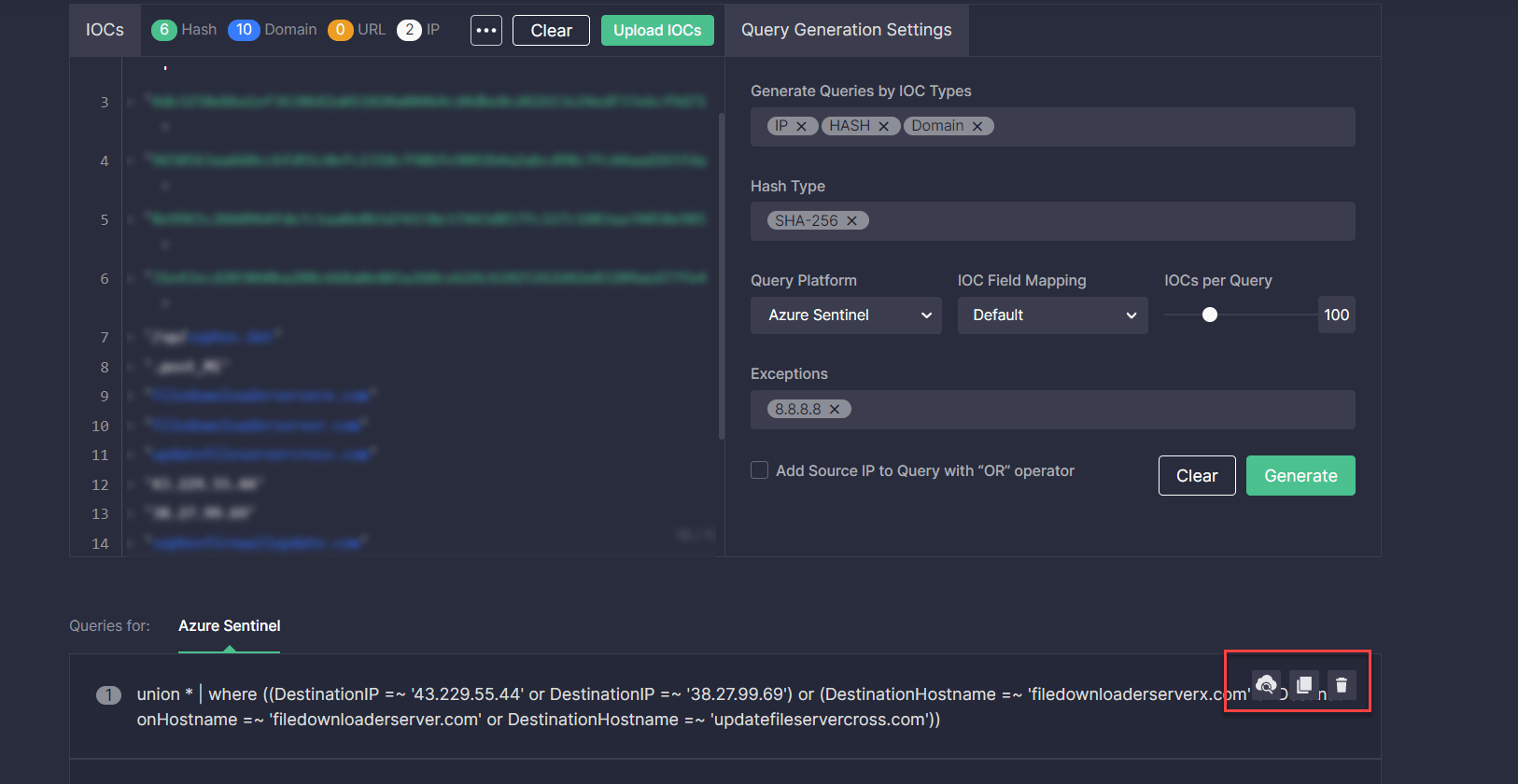 That’s it, you’re all set for hunting in the selected Query Platform.
That’s it, you’re all set for hunting in the selected Query Platform.
The public version at https://cti.uncoder.io/ is the simplest and fastest way to get started with Uncoder CTI and run queries that do not require advanced fine-tuning. For a more insightful threat hunting experience leveraging extended Uncoder CTI capabilities, like custom IOC mapping and automated search in your SIEM or XDR, join the SOC Prime platform and gain access to 130,000+ detections for threat discovery and threat hunting. Check out the overview of Uncoder CTI to learn more about the tool intelligence-driven hunting capabilities.