Efficiency and collaboration are essential in cybersecurity. As part of the SOC Prime Platform, Uncoder AI is a a professional IDE & co-pilot for detection engiennering to streamline content creation and threat detection rule contribution. For those participating in the Threat Bounty Program, this tool makes it easier to contribute detection rules, collaborate with experts, and track the success of their contributions.
In this article, we’ll provide a step-by-step guide for contributors of threat detection rules on how to use Uncoder AI, from logging into the SOC Prime Platform to submitting your detection rules for review.
Step 1: Log into the SOC Prime Platform
To begin contributing detection rules, head over to the SOC Prime Platform and log into your account. Ensure that you use the same email address that you registered with for the Threat Bounty Program. If you’ve forgotten your password or haven’t set one up, don’t worry. Click on Get OTP, enter your email address, and hit Proceed. A six-digit one-time password (OTP) will be sent to your inbox. Use this OTP to log in and access your account.
Step 2: Set Up Your Custom Repository
Once you’ve logged into the Platform, the next step is to check if you have a custom repository where your rules and content can be saved. To do this, navigate to the Threat Detection Marketplace and select the Repositories section from the top menu. If you don’t have access to this, click on your account icon and look for the corresponding option in the menu.
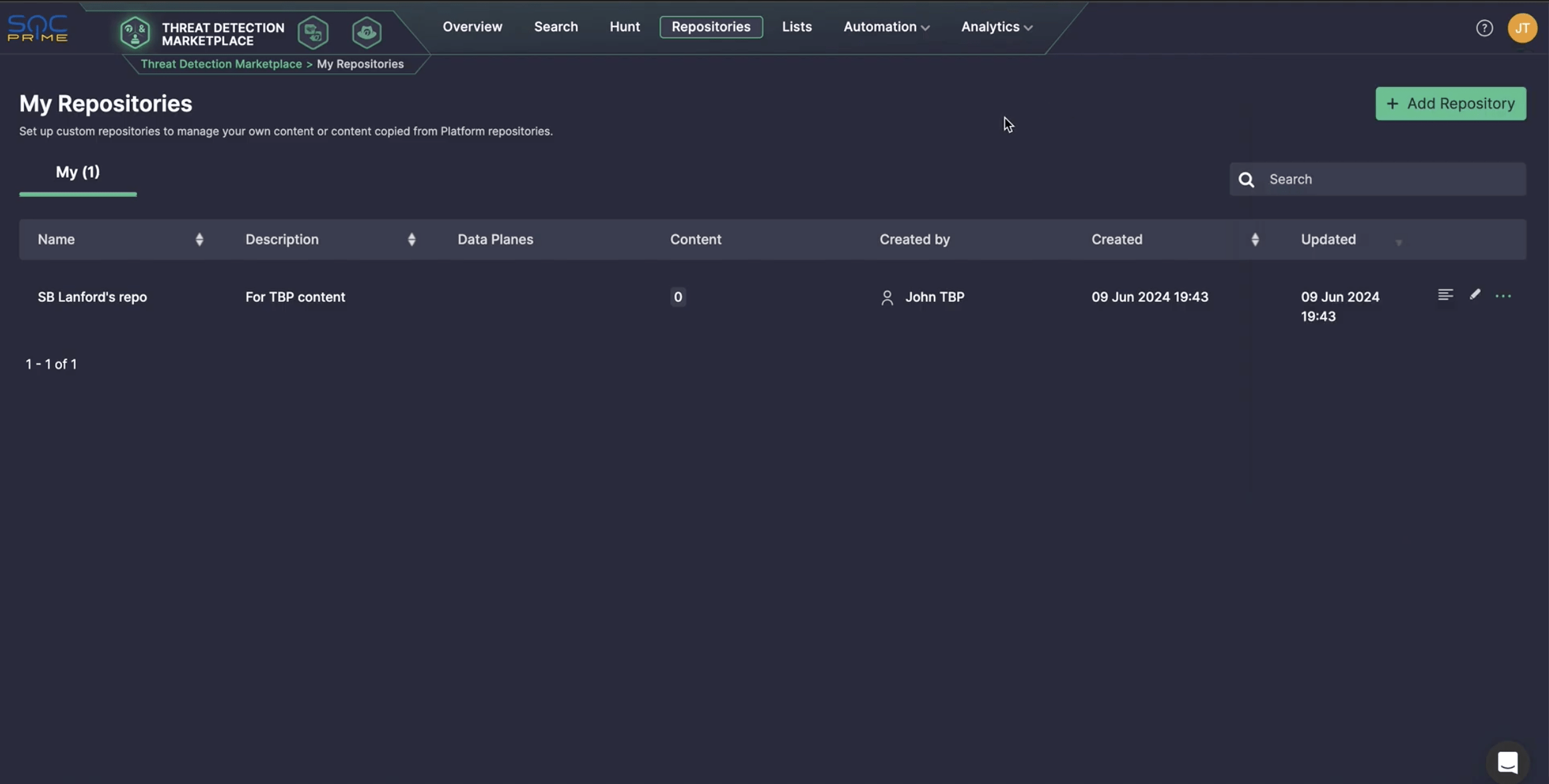
If you already have a repository, you’re good to go. If not, create one by clicking Add Repository. Give your repository a meaningful name and add an optional description. This is where you’ll store the detection rules you create.
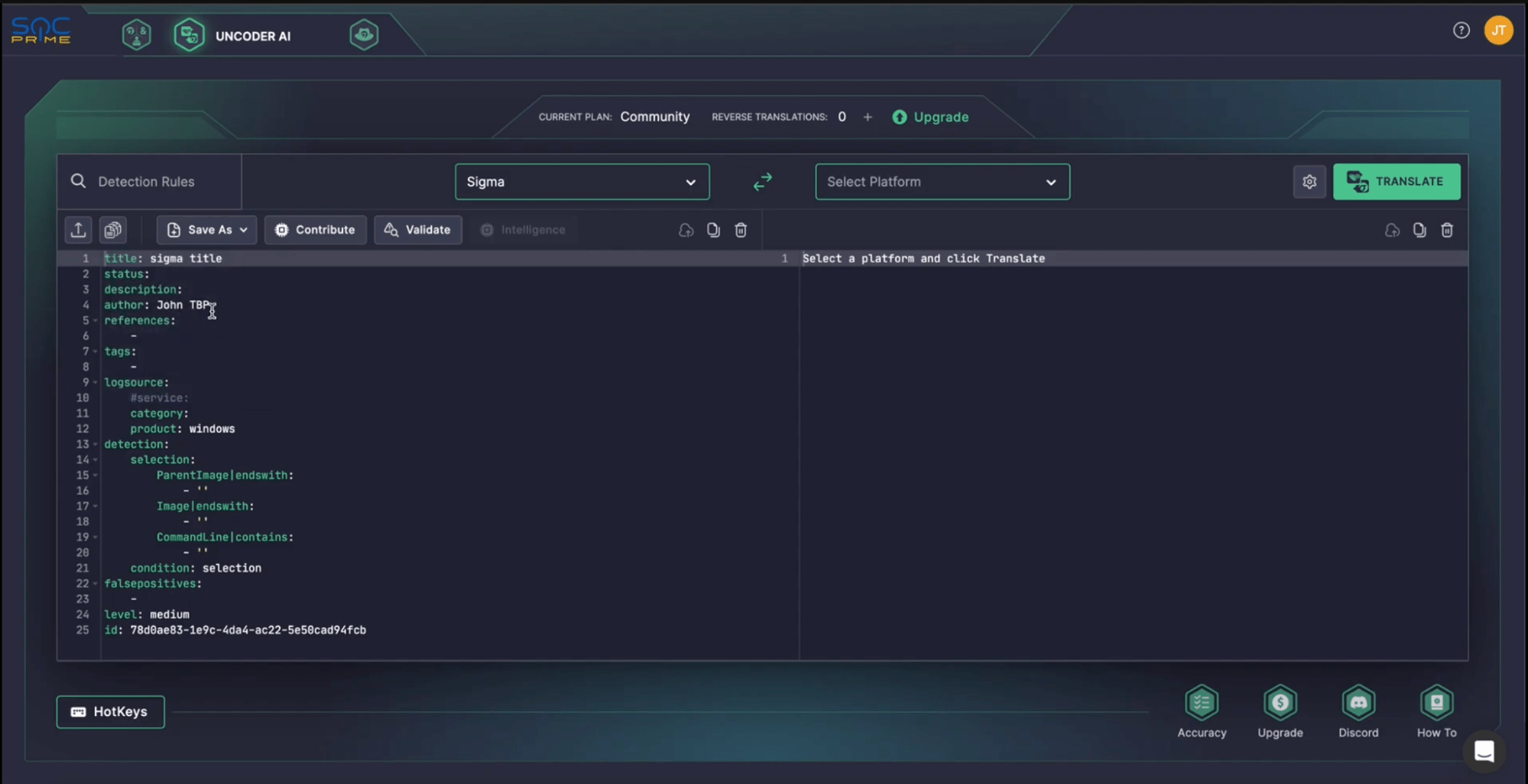
Step 3: Start Writing Rules with Uncoder AI
Now that your repository is set up, it’s time to use Uncoder AI to create detection rules. Navigate to the Uncoder AI section within the Platform by choosing the corresponding tab in the top menu. When contributing content to the Threat Bounty Program, select a template. There are two templates available:
- Roota for Threat Bounty
- Sigma for Threat Bounty
Pick the one that best fits your needs. The Author and ID fields will be pre-filled to save time and make the process more efficient.
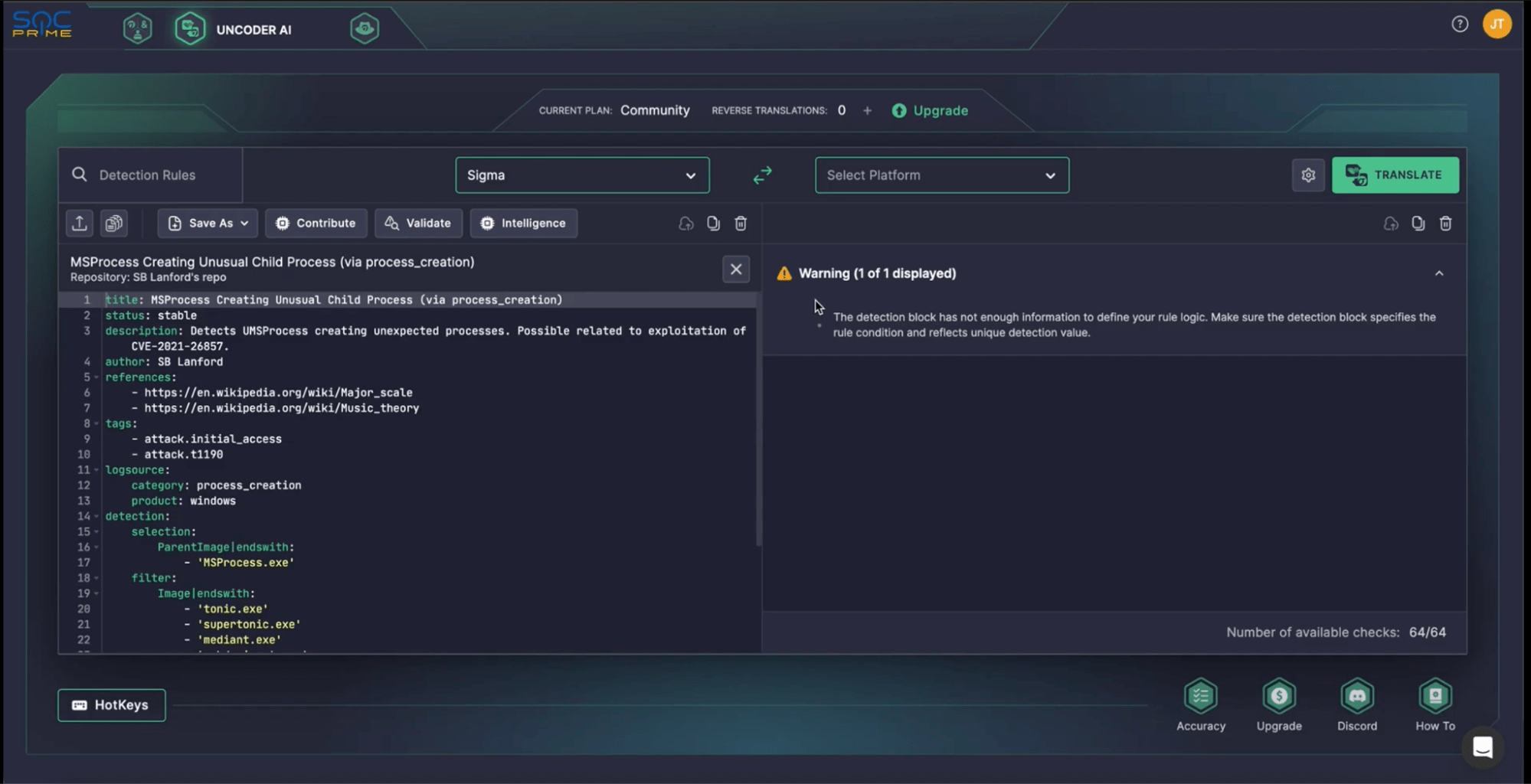
Step 4: Save and Validate Your Rule
After writing your rule, save it to your custom repository. To do this, click Save As New Rule, ensure no changes are needed, and hit Save.
Next, validate your rule using Warden, the validation tool within the Platform. It’s crucial that the rule passes validation, as errors will prevent your rule from being accepted. Address any issues identified by Warden to ensure the rule is ready for submission.
Step 5: Submit Your Rule for Review
Once your rule is saved and validated, you can submit it for review. Click Contribute, and you’ll see the Threat Bounty Contribution section. Here, you can track the history of the rule, including when it was saved and submitted for review.
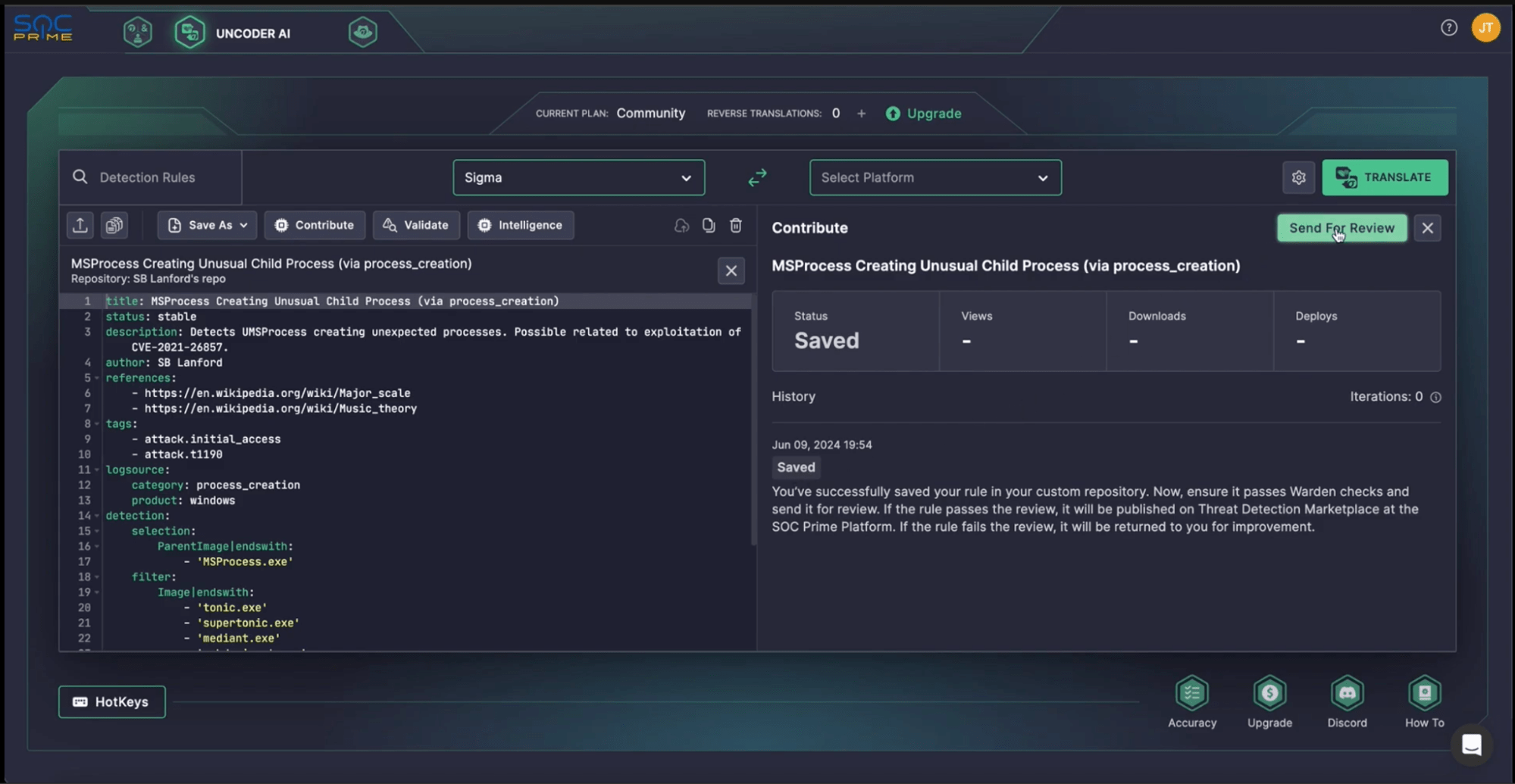
After submitting, the rule is now in the review stage, awaiting feedback from the SOC Prime team. You’ll be notified by email once the review is complete. If the rule meets the required quality standards, it will be published on the Threat Detection Marketplace.
Step 6: Review Results and Iteration
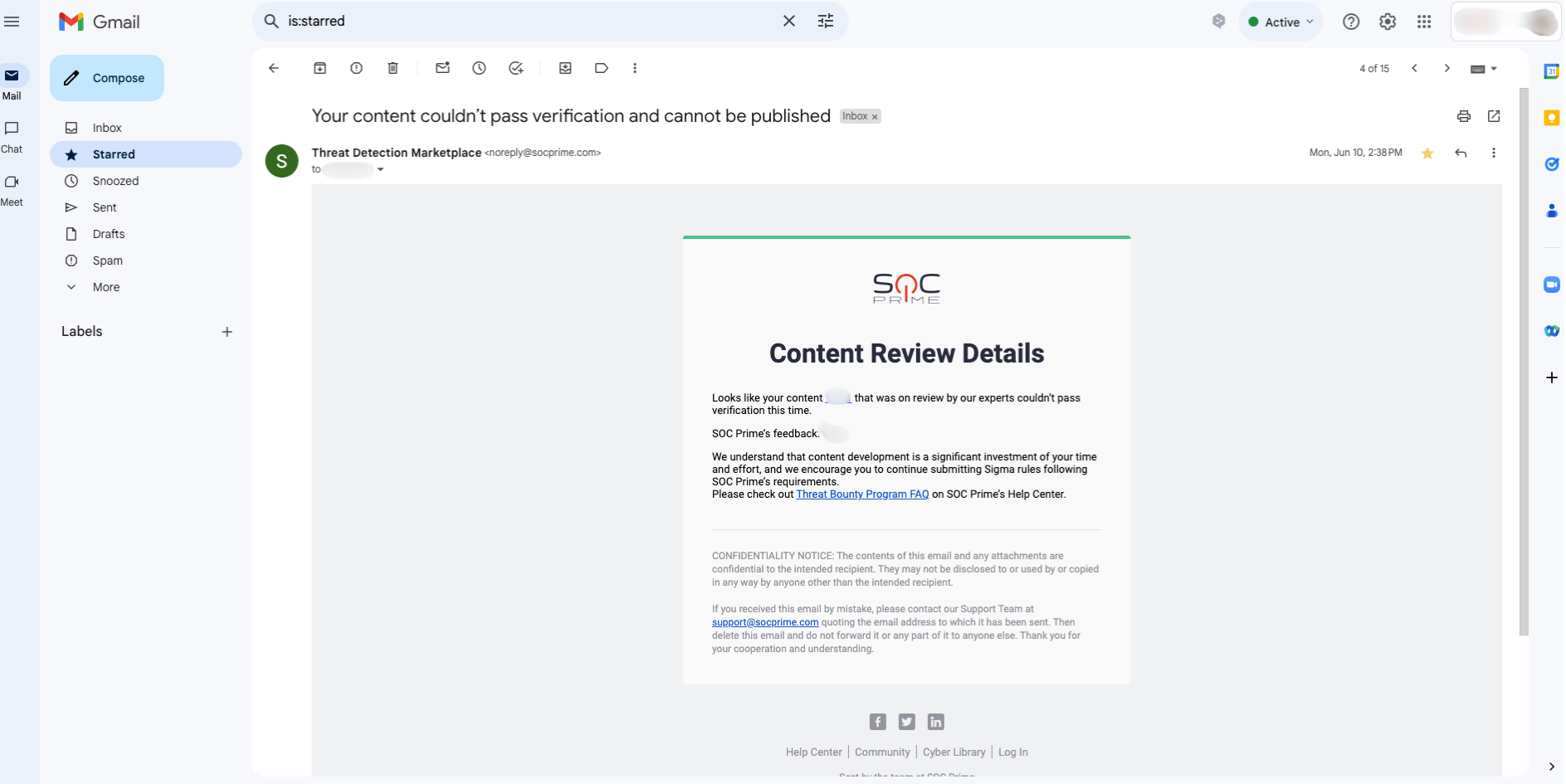
If the rule doesn’t pass the review, it will be returned with suggestions for improvement. You can see the exact reason for the Returned status and make the necessary adjustments. Once the corrections are made, resubmit the rule for another review.
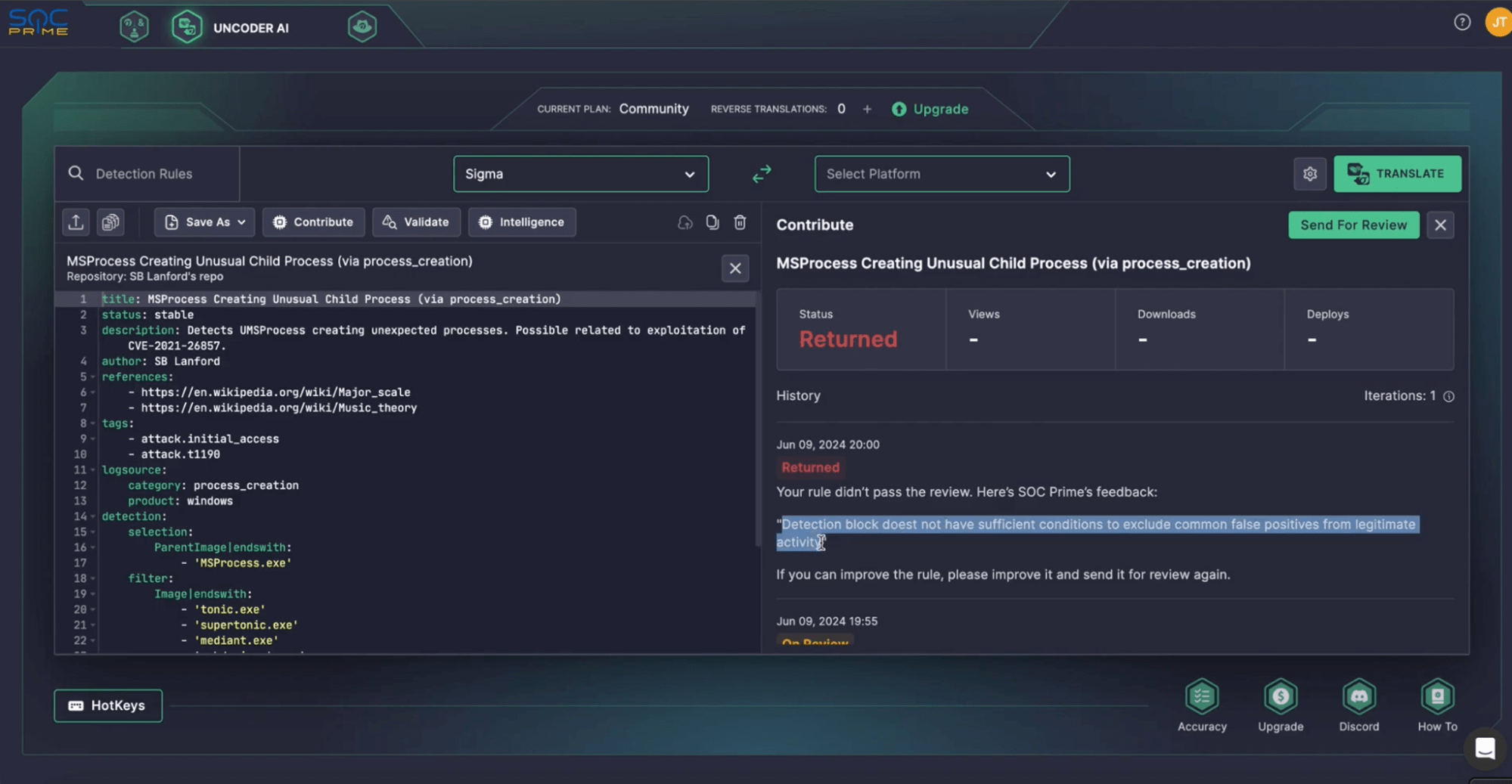
The iteration process continues until the rule meets the necessary standards. After each iteration, you will be notified via email.
Step 7: Rule Publication and Tracking Performance
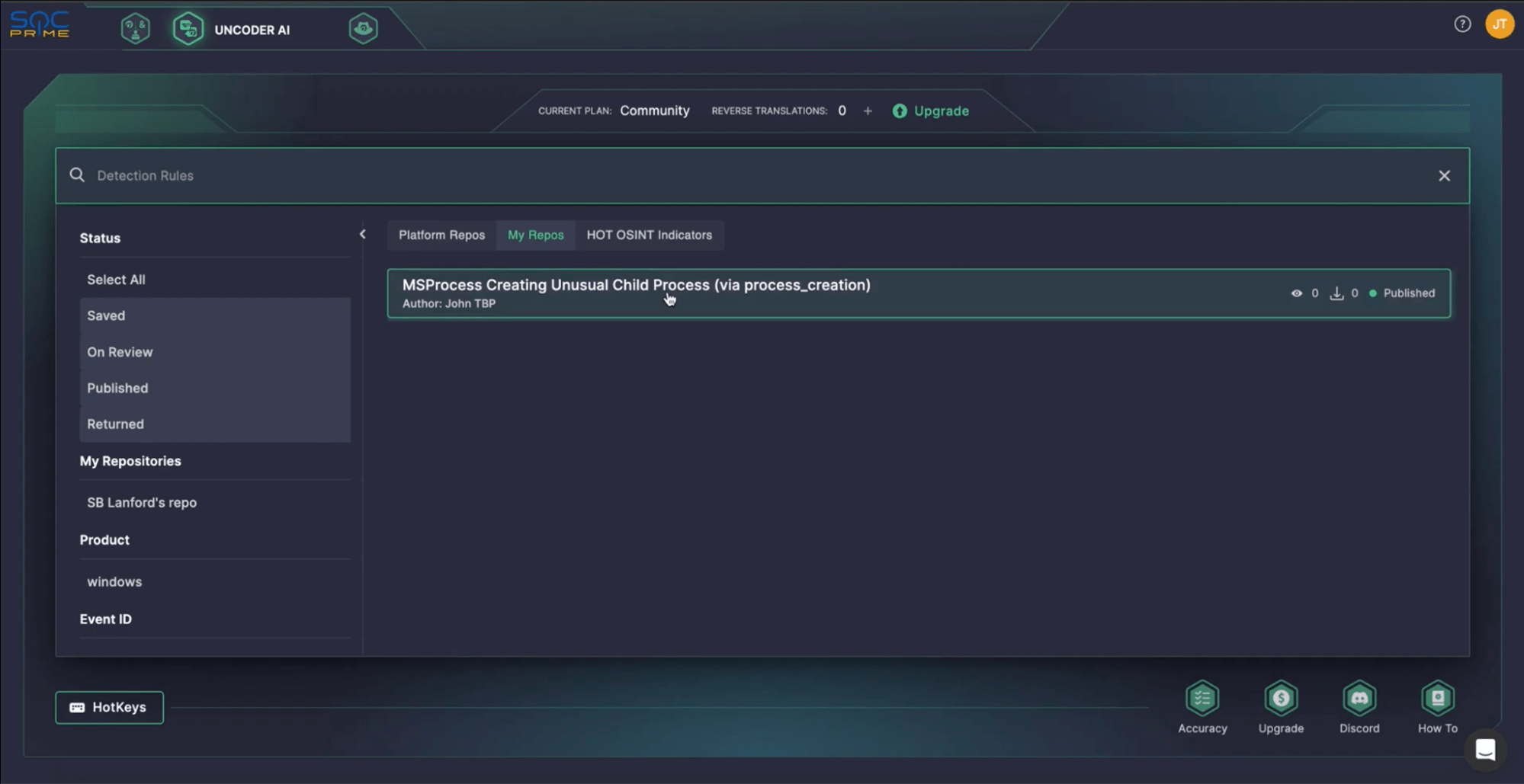
Once the rule is approved and published, it will be available on the Threat Detection Marketplace. You can monitor its performance and track how often it’s downloaded and deployed. The Platform also provides statistics on the rule’s usage.
All of this information is available in the Detection Rules Search section of Uncoder AI, under My Repositories. Simply click on a rule to see its status, history, and contribution details.
Conclusion
Uncoder AI is a powerful tool that simplifies the creation and contribution of detection rules within SOC Prime’s Threat Bounty Program. By following this guide, you’ll be able to navigate the process from setting up your repository to publishing and tracking the success of your rules.
The ability to collaborate with industry experts and track the real-world usage of your contributions makes Uncoder AI an essential tool for cybersecurity professionals. So, get started today and contribute to a safer digital world.




