The China-backed hacking collective tracked as UNC6384 has been observed behind cyber-espionage attacks against diplomats in Southeast Asia and various global organizations in pursuit of Beijing’s strategic objectives. The campaign hijacks web traffic to deliver a signed downloader, leading to the deployment of a PlugX backdoor variant through sophisticated social engineering and evasion techniques.
Detect UNC6384 Attacks
CrowdStrike’s 2025 Global Threat Report highlights the intensifying pace of China-linked cyber operations, noting a 150% surge in state-sponsored activity and up to a 300% rise in targeted attacks against financial services, media, manufacturing, and industrial sectors. The latest UNC6384 campaign resonates with this trend, illustrating the expanding offensive capabilities and the increasing sophistication of Chinese hacking groups.
Register for SOC Prime Platform to tap into an extensive marketplace of 600,000+ detection rules and queries that can be used across industry-leading security analytics solutions, AI-native threat intelligence, automated threat hunting, and advanced detection engineering capabilities. SOC Prime Platform curates a relevant detection stack to help global organizations safeguard against stealthy attacks linked to the China-backed UNC6384 hacking group. Click the Explore Detections button to reach behavioral Sigma rules mapped to the MITRE ATT&CK® framework, along with IOCs and AI-generated rules, compatible with multiple SIEM, EDR, and Data Lake platforms in use.
For more content on TTPs associated with China-linked Mustang Panda, which shares similarities with UNC6384 tactics and tools, defenders can browse the Threat Detection Marketplace under the “Mustang Panda” tag or use the “APT” tag to access broader coverage of nation-state threats.
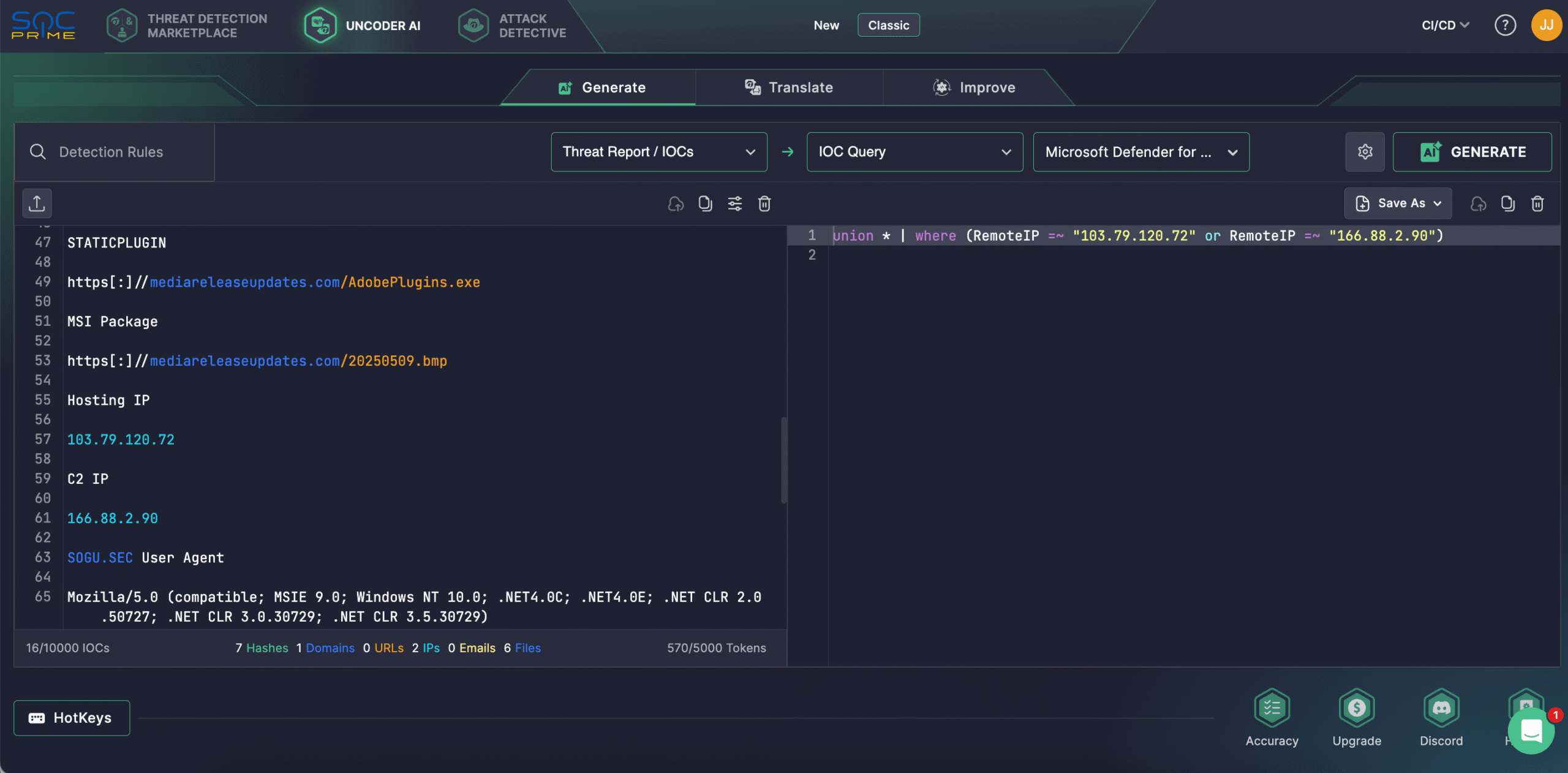
Security engineers can leverage Uncoder AI to accelerate IOC matching by instantly converting threat intel from the corresponding Google Threat Intelligence Group report into custom hunting queries. Alternatively, rely on Uncoder AI to craft detection algorithms from raw threat reports, predict ATT&CK tags, optimize query code with AI, translate it across multiple language formats, and visualize the Attack Flow covering the latest UNC638 activity.
UNC6384 Attack Analysis
In early spring 2025, Google Threat Intelligence Group (GTIG) unveiled sophisticated attacks attributed to the China-linked actor UNC6384, with a primary focus on diplomats in Southeast Asia and other organizations worldwide. UNC6384 exhibits TTPs overlapping with Mustang Panda (aka BASIN, Bronze President, Camaro Dragon, Earth Preta, Red Lich, Temp.Hex, TA416, or RedDelta). The operation leveraged captive portal redirects to hijack traffic and delivered STATICPLUGIN, enabling in-memory deployment of a PlugX (aka Korplug) iteration known as the SOGU.SEC backdoor.
Active since at least 2008, the PlugX malware has been extensively leveraged by Chinese threat groups, including the Mustang Panda group. For instance, in 2022, Mustang Panda launched a campaign against state bodies in Europe, the Middle East, and South America, leveraging PlugX. UNC6384 and Mustang Panda have both been observed targeting the public sector in Southeast Asia, delivering SOGU.SEC via DLL side-loaded launchers and using common C2 infrastructure.
In this campaign, the attack flow begins when the victim’s browser performs a captive portal hijack to spread malware disguised as an Adobe plugin update, exploiting Chrome’s hard-coded captive portal check (www.gstatic[.]com/generate_204). Then, threat actors conduct Adversary-in-the-Middle (AitM) redirections to an adversary-controlled website, leading victims to spoofed update pages secured with valid TLS certificates. From there, the first-stage malware STATICPLUGIN was delivered, which then retrieved an MSI package from the same site. The MSI enabled DLL side-loading of CANONSTAGER, finally leading to the in-memory deployment of the SOGU.SEC backdoor. Over two dozen such signed samples have been observed since 2023, underscoring UNC6384’s growing sophistication.
As potential UNC6384 attack mitigation measures, the vendor advises applying the latest updates and targeted defenses against this malicious activity and other China-backed threats. Recommended steps include enabling Enhanced Safe Browsing in Chrome, keeping all devices fully patched, and activating 2-Step Verification on accounts.
With Chinese hacking groups largely adopting stealthy tactics to evade detection, organizations are urged to strengthen proactive defenses to identify threats at the earliest attack stages and protect their overall cybersecurity posture. By relying on SOC Prime’s complete product suite backed by top cybersecurity expertise and AI, fusing automation, AI-native threat intel, and built on zero-trust security milestones, global organizations can outscale cyber threats of any sophistication.




