Hard on the heels of the phishing campaign against Ukraine spreading Remcos RAT, another offensive operation relying on a similar adversary toolkit comes to the scene. At the end of December 2023, Trendmicro researchers reported CERT-UA about suspicious military-related files sent through a series of new phishing attacks against Ukraine. The uncovered malicious activity aimed at the Armed Forces of Ukraine impersonates the recruitment process of the Third Separate Assault Brigade and the Israel Defense Forces. The offensive actions attributed to the UAC-0184 group rely on the use of Reverse SSH tunneling and are aimed at infecting the targeted infrastructure with Remcos RAT.
UAC-0184 Attack Analysis
On December 22, 2023, Trendmicro informed CERT-UA about the newly discovered adversary activity against Ukraine involving military-related phishing lures. Based on the received details, on January 6, 2024, CERT-UA released a new CERT-UA#8386 heads-up covering a phishing operation masquerading as the recruitment process related to the Third Separate Assault Brigade and the Israel Defense Forces.
No later than November 2023, adversaries applied Signal to distribute malicious archives containing LNK files. Executing the latter initiates an infection chain that results in distributing Remcos RAT. As a result of an attack using Reverse SSH tunneling, adversaries can gain unauthorized remote access to the impacted instances.
The above-referenced shortcut files contain an obfuscated command for loading and executing an HTA file via mshta.exe, which contains obfuscated code. In turn, VBScript code executes a PowerShell command intended for decrypting, decompressing, and launching a harmful PowerShell script. The latter ensures the loading and execution of malware samples, as well as a lure file in PDF or DOCX format. Notably, the names and content of these phishing lures are military-related.
Despite the use of publicly available tools by attackers, the uncovered offensive activity can be considered a separate cluster of cyber threats and is linked to the UAC-0184 hacking group.
Detect UAC-0184 Attacks Covered in the CERT-UA#8386 Alert
A growing volume of malicious campaigns targeting Ukraine and frequently relying on publicly available hacking tools gives the green light to multiple collectives to use the Ukrainian cyber threat arena as a battleground for further attacks of more increased sophistication. To help defenders effectively detect attacks linked to the UAC-0184 group and covered in the new CERT-UA#8386 alert, SOC Prime Platform curates a batch of relevant behavior-based Sigma rules.
Press Explore Detections to explore the entire collection of algorithms for UAC-0184 attack detection. Explore MITRE ATT&CK® and CTI references, or reach more actionable metadata right at your fingertips.
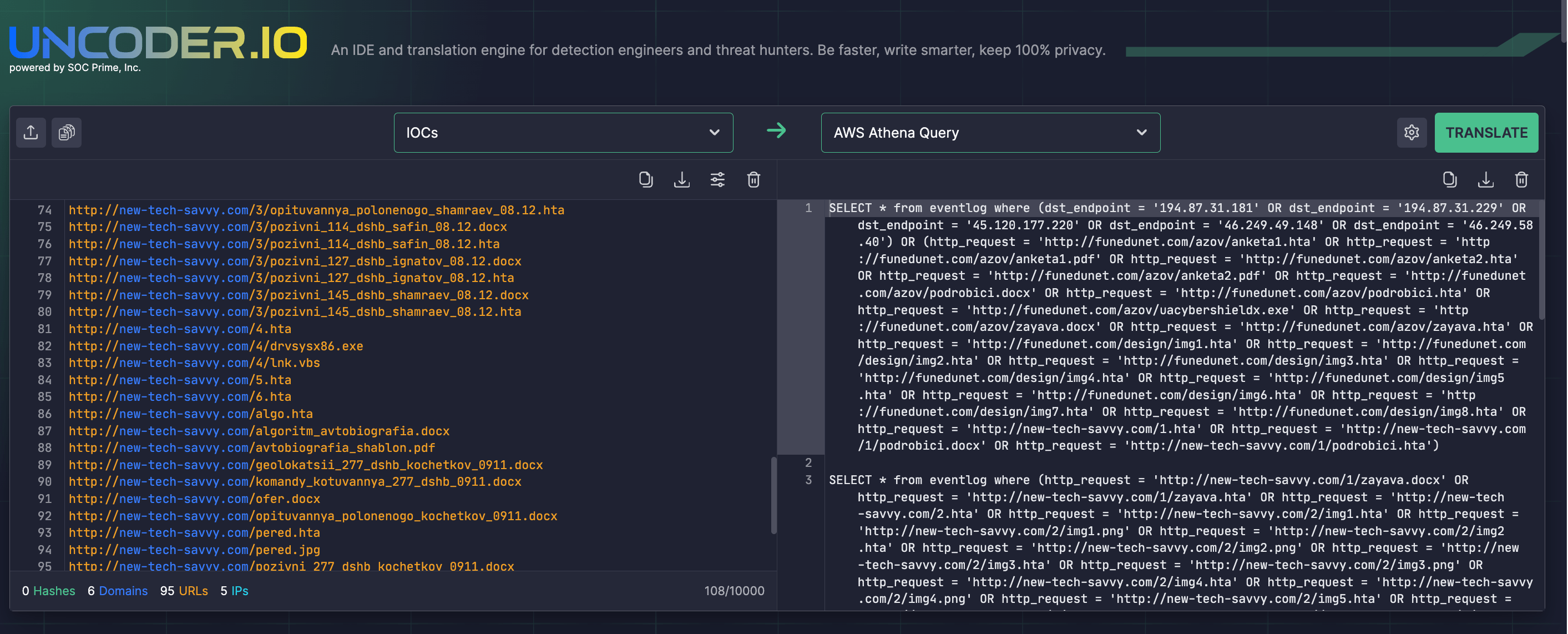
Search for IOCs associated with the UAC-0184 attacks and listed in the CERT-UA#8386 alert via the open-source Uncoder IO tool that enables instantly generating threat intel into custom IOC queries ready to run in your SIEM or EDR environment.
MITRE ATT&CK Context
Using MITRE ATT&CK provides detailed insight into the context of the most recent offensive campaign associated with UAC-0184. Refer to the table below to view the comprehensive set of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques. Tactics Techniques Sigma Rule Execution Command and Scripting Interpreter: PowerShell (T1059.001) Command and Scripting Interpreter: Windows Command Shell (T1059.003) Command and Scripting Interpreter: Visual Basic (T1059.005) Persistence Boot or Logon Autostart Execution (T1547) System Binary Proxy Execution (T1218) Hide Artifacts: Hidden Windows (T1564.003) Discovery Software Discovery: Security Software Discovery (T1518.001)




