The UAC-0099 hacking collective, which has been launching targeted cyber-espionage attacks against Ukraine since the second half of 2022, resurfaces in the cyber threat arena. The CERT-UA team has observed a spike in the group’s malicious activity throughout November-December 2024 against Ukrainian government entities using the phishing attack vector and spreading LONEPAGE malware.
Detect UAC-0099 Attacks Covered in the CERT-UA#12463 Alert
The increasing volumes of cyber-espionage campaigns against government agencies in Ukraine and its allies stand out as a significant aspect of the current cyber threat landscape. The latest CERT-UA#12463 alert observes a set of new intelligence-gathering operations targeting the Ukrainian public sector organizations and underscores the need for elevating defenses to minimize the risks of infections via CVE-2023-38831 exploitation and LONEPAGE malware distribution.
Click Explore Detections to reach the curated list of SOC content for UAC-0099 attack detection covered in the corresponding CERT-UA alert, which focuses on the group’s adversary operations spanning November and December 2024. All detections are mapped to the MITRE ATT&CK® framework and offer relevant cyber threat context to enhance threat research, including CTI and other key metadata. Security teams can also leverage the automated translation capabilities and convert detection code into over 30 SIEM, EDR, and Data Lake formats to meet their specific security requirements.
Security engineers can also explore TTPs that are linked to the actor’s cyber-espionage attacks by reaching the comprehensive detection stack via the corresponding “UAC-0099” tag based on the group identifier.
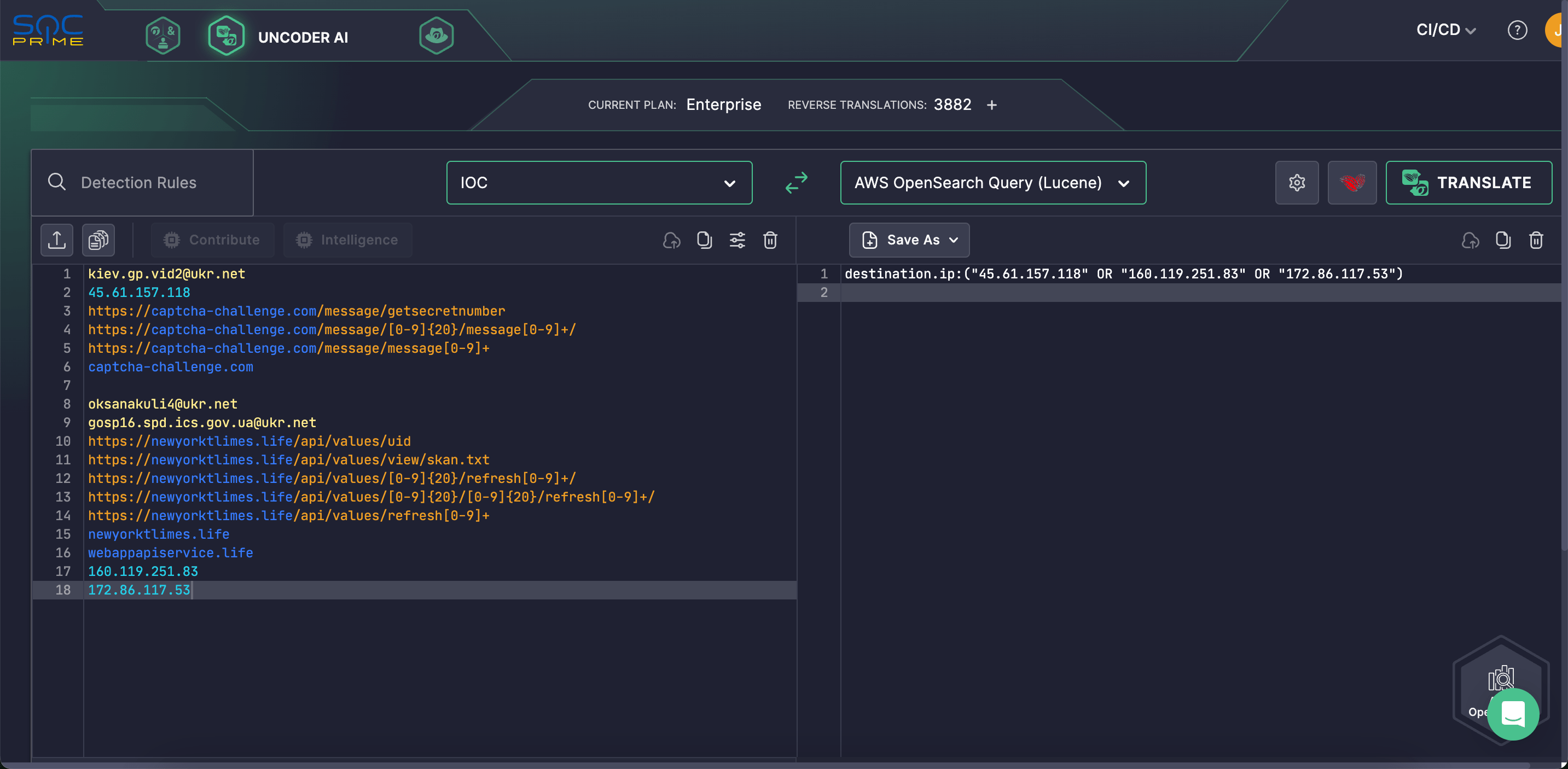
In addition, teams can accelerate IOC packaging and retrospective hunting of the group’s TTPs. Leverage Uncoder AI to instantly convert IOCs from the latest CERT-UA research into curated hunting queries compatible with multiple language formats.
UAC-0099 Attack Analysis
On December 14, 2024, CERT-UA issued a new heads-up tracked as CERT-UA#12463 notifying security teams of a surge in cyber-espionage activity by UAC-0099 actors. Between November and December 2024, adversaries launched a series of cyber-attacks targeting state bodies, including forestry departments, forensic institutions, factories, and other public sector agencies in Ukraine.
The attackers applied their common behavioral patterns via phishing emails containing attachments in the form of double archives with LNK or HTA files. Some of these archives also included an exploit for the known WinRAR vulnerability CVE-2023-38831. Upon successful compromise, the LONEPAGE malware is executed on the affected machines, enabling command execution. This malware executes malicious PowerShell commands to infect the system and transmit stolen data to the server through an HTTP POST request.
In June 2023, the UAC-0099 group was also observed behind a long-term campaign against Ukrainian media and government agencies aimed at intelligence gathering. In those cyber-espionage operations, attackers similarly leveraged phishing emails with malicious attachments and, in some cases, exploited the same critical vulnerability in the WinRAR software to deliver LONEPAGE malware.
Despite similarities in the offensive toolkit leveraged by adversaries, researchers observed changes in the group’s TTPs in the latest campaign. Notably, LONEPAGE was previously implemented as a VBS file stored in one of the system directories. In December 2024, the described functionality was executed using two files—a 3DES-encrypted file and a .NET application designed to decrypt this file and execute the resulting PowerShell code in memory.
Adversaries continue to remain under the radar and ensure infrastructure resilience by abusing Cloudflare services. The expanding scope of UAC-0099’s cyber-espionage campaigns, coupled with its shifting methods, tools, and targets, highlights the critical need for enhanced cyber vigilance to counter the group’s adaptability effectively. By leveraging SOC Prime Platform for collective cyber defense, organizations can proactively thwart attacks of any scale to strengthen their cybersecurity posture without surrendering data.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK helps security teams gain detailed insights into UAC-0099 TTPs used in a cyber-espionage campaign against Ukraine and covered in the most recent CERT-UA report. Refer to the table below to view the comprehensive set of Sigma rules addressing relevant ATT&CK tactics, techniques, and sub-techniques.
Tactics | Techniques | Sigma Rule |
Initial Access | Phishing: Spearphishing Attachment | |
Execution | Scheduled Task/Job (T1053) | |
Exploitation for Client Execution (T1203) | ||
User Execution: Malicious Link (T1204.001) | ||
User Execution: Malicious File (T1204.002) | ||
Command and Scripting Interpreter: PowerShell (T1059.001) | ||
Command and Scripting Interpreter: Windows Command Shell | ||
Defense Evasion | Obfuscated Files or Information (T1027) | |
Obfuscated Files or Information: Command Obfuscation (T1027.010) | ||
System Binary Proxy Execution (T1218) | ||
Hide Artifacts (T1564) | ||
Hide Artifacts: Hidden Window (T1564.003) | ||
Command and Control | Ingress Tool Transfer (T1105) | |
Exfiltration | Automated Exfiltration (T1020) | |




