Since russia’s full-fledged invasion of Ukraine, the aggressor’s offensive forces have launched thousands of targeted cyber attacks against Ukraine. One of the most persistent threats belongs to the infamous cyber-espionage gang tracked as UAC-0010 (Armageddon). This article provides an overview of the group’s adversary activity against Ukraine largely exploiting the phishing attack vector as of July 2023 based on the corresponding CERT-UA research.
UAC-0010 (Armageddon APT) Attack Description
With the ever-increasing volumes of cyber attacks targeting Ukrainian officials and aimed to cripple the organizations’ critical IT infrastructure, defenders are implementing effective means to prevent, identify, and timely remediate related threats. According to the CERT-UA investigations, Armageddon aka Gamaredon also identified as UAC-0010 remains one of the most persistent threats on the Ukrainian cyber front line with cyber-espionage activity against the security and defense forces of Ukraine being the key adversary objective. Ex-officials of the Crimean main Department of the Security Service of Ukraine, who broke the military oath and started serving russian Federal Security Service in 2014, are believed to be behind the group’s offensive campaigns.
Based on the investigated incidents, the number of infected devices within the information and communication systems of the Ukrainian public sector organizations may amount to several thousands of items. UAC-0010 mainly applies email distribution or Telegram, WhatsApp, and Signal messengers as the initial attack vector by leveraging already compromised accounts. One of the most frequent means of initial compromise is sending an archive that contains a malicious HTM or HTA file to the targeted users. Opening the file lures leads to generating an archive that contains a shortcut file, which triggers an infection chain.
For malware distribution, Armageddon APT exploits vulnerable removable data storage devices, legitimate files, including LNK ones, and modified Microsoft Office Word templates, which enables hackers to infect any documents generated on the targeted systems by adding the corresponding macros.
At further attack stages, adversaries are capable of stealing files and user-sensitive data via GammaLoad or GammaSteel malware. As a result of infection, the vulnerable device can contain over 100 compromised files. Moreover, in case after the OS registry cleanup or file and scheduled tasks removal one of the infected files remains on the affected system, the computer is highly likely to fall prey to the recurring infection. As of July 2023, UAC-0010 applies PowerShell commands to perform data exfiltration and remote code execution and Anydesk utility for real-time remote access.
Adversaries are continuously enriching their offensive capabilities aimed at detection evasion and bypassing security protection. For instance, they apply a specific PowerShell scenario to bypass two-factor authentication. To avoid using the DNS sub-system, they apply third-party Telegram services for identifying the IP addresses of the management servers and tend to change the IP addresses of the intermediate control nodes several times a day.
As potential mitigation measures, CERT-UA researchers recommend imposing restrictions on launching certain utilities on the organization’s system, like mshta.exe, wscript.exe, cscript.exe, and powershell.exe. Devices that apply Starlink to establish an Internet connection might be more exposed to threats attributed to the UAC-0010 malicious activity.
Detecting UAC-0010 aka Armageddon russian APT Ongoing Campaigns Against Ukraine
The growing number of offensive operations launched by the UAC-0010 russia-linked hacking group requires immediate attention of defenders looking for ways to help Ukraine and its allies effectively thwart the aggressor’s attacks. SOC Prime Platform for collective cyber defense curates a comprehensive list of Sigma rules for proactive UAC-0010 attack detection filtered by the relevant tag “UAC-0010”.
To drill down to the above-referenced verified alerts and hunting queries, press the Explore Detections button and choose Sigma rules matching your current security needs and covering your organization-specific log sources. All detection algorithms are aligned with the MITRE ATT&CK framework v12 addressing the appropriate TTPs and can be used across dozens of SIEM, EDR, and XDR technologies used in your organization.
Defenders can also run instant hunts leveraging indicators of compromise related to the UAC-0010 threats and listed in the corresponding CERT-UA report and SOC Prime’s Uncoder AI that enables teams to create custom IOC queries in a matter of clicks and automatically work with them in the selected SIEM or EDR environment.
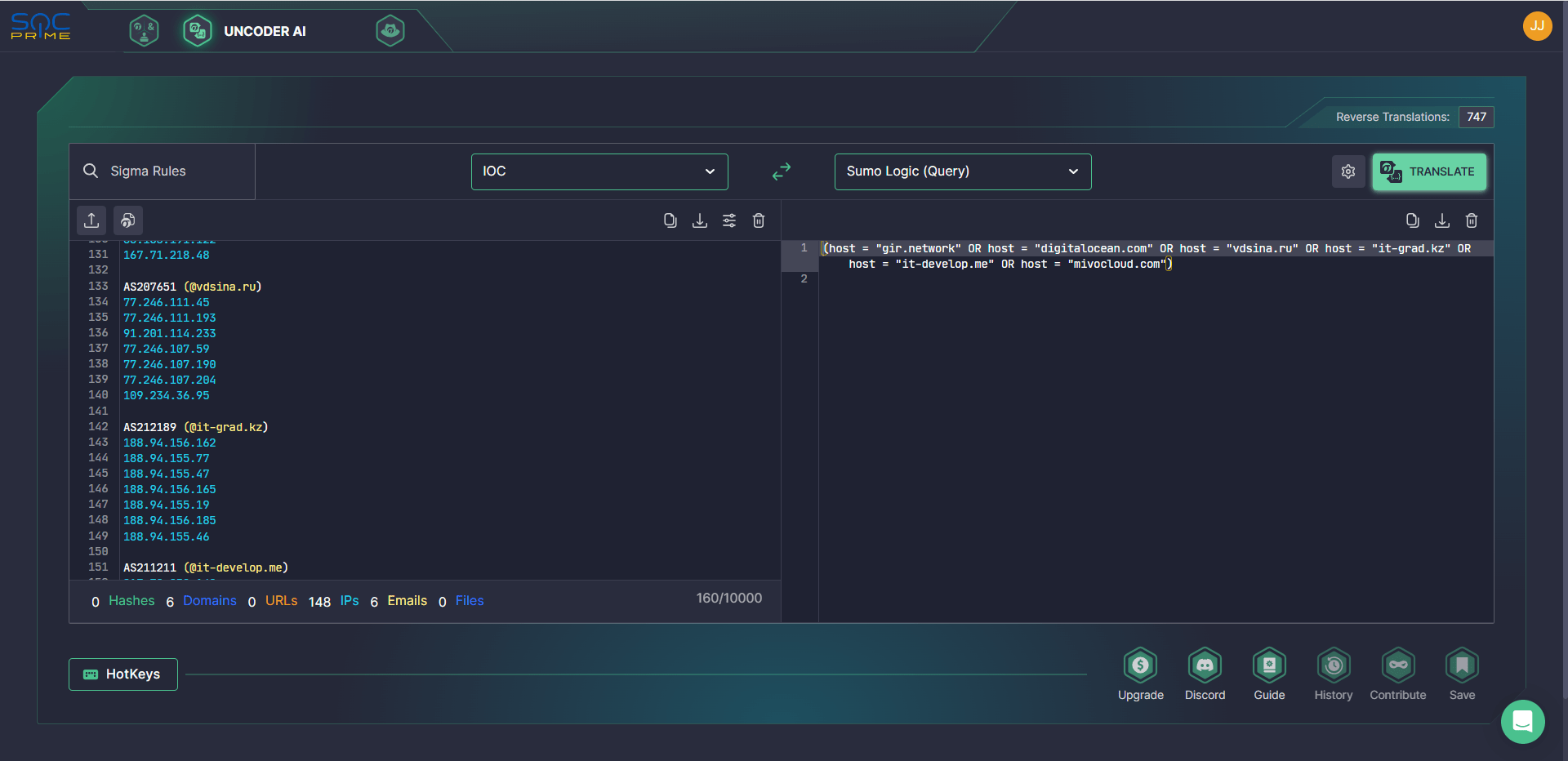
Register for SOC Prime Platform to choose the tools tailored to your current cyber defense journey. Explore the world’s largest collection of Sigma rules for existing and emerging threats with Threat Detection Marketplace, delve into the cyber threat context behind the selected content, adjust detections to your custom data schema and translate them on the fly to the language format of your choice with Uncoder AI, or validate your entire detection stack in seconds to seamlessly identify blind spots in your detection coverage and run threat scans based on your content priorities.




