Today, under the Threat Hunting Content column, we are heightening your interest in AsyncRAT Detection (Sysmon Behavior) community rule by Emir Erdogan. The rule enables the detection of AsyncRat by using sysmon logs.
According to the author of the project on GitHub, AsyncRat is a Remote Access Tool designed to remotely monitor and control other computers through a secure encrypted connection that was created for educational purposes only. The project page even has a Legal Disclaimer prohibiting the use of this tool for malicious purposes, but when did it stop the attackers?
The AsyncRAT’s code is available on the GitHub page publicly and it can serve as a very threatening tool in the hands of the experienced threat actors. It is not much different from most Remote Access Trojans, but its code is publicly available, and even an unskilled cybercriminal can use it in attacks, and more experienced attackers can create their own malware based on open source code.
Adversaries can use AsyncRat to steal credentials and other sensitive data, record video and audio, collect information from messaging services, Web browsers, and FTP clients. Furthermore, the tool is capable of downloading and uploading files on the infected system, so it can deploy additional malware for the advanced attack.
The threat hunting content that detects this “Remote Access Tool” is available on Threat Detection Marketplace: https://tdm.socprime.com/tdm/info/XQ4PKpZA4PYK/igppdHIBAq_xcQY4-2PH/?p=1
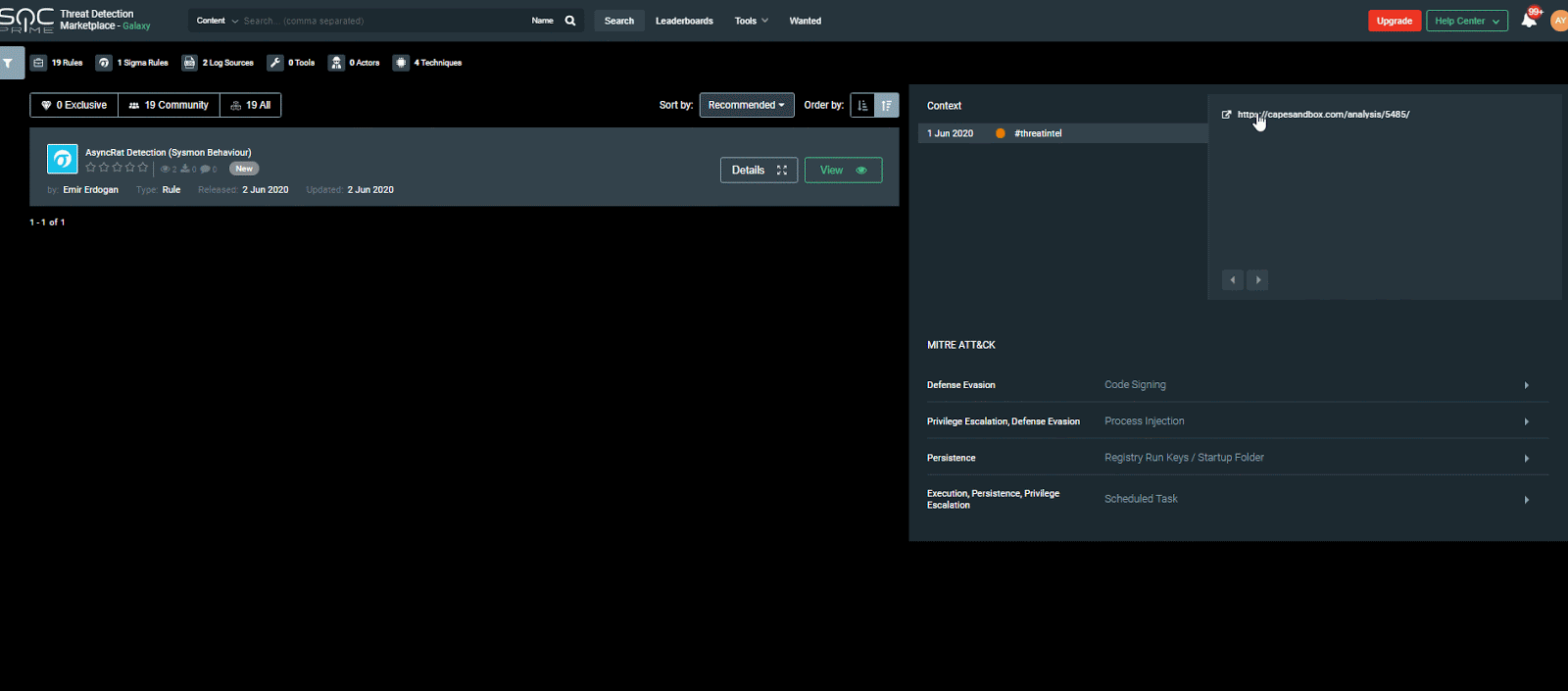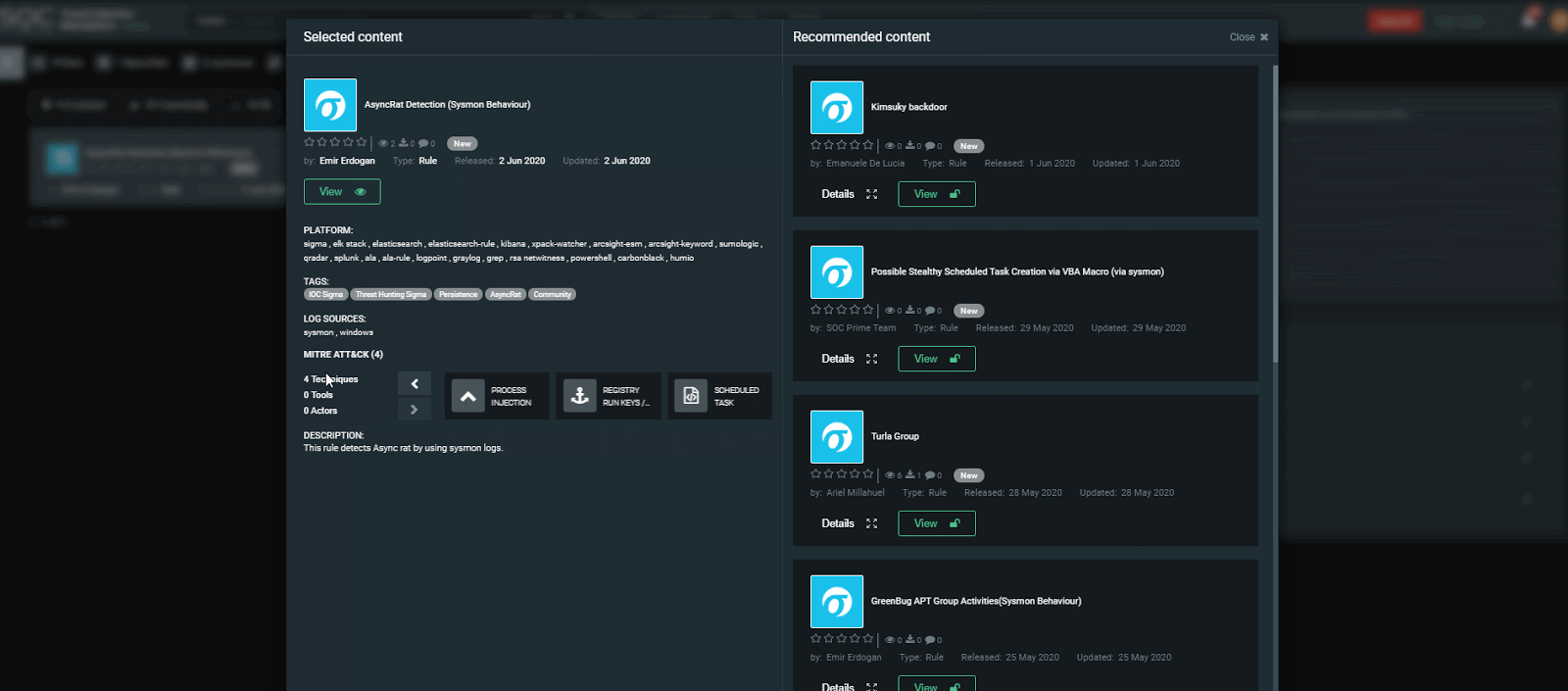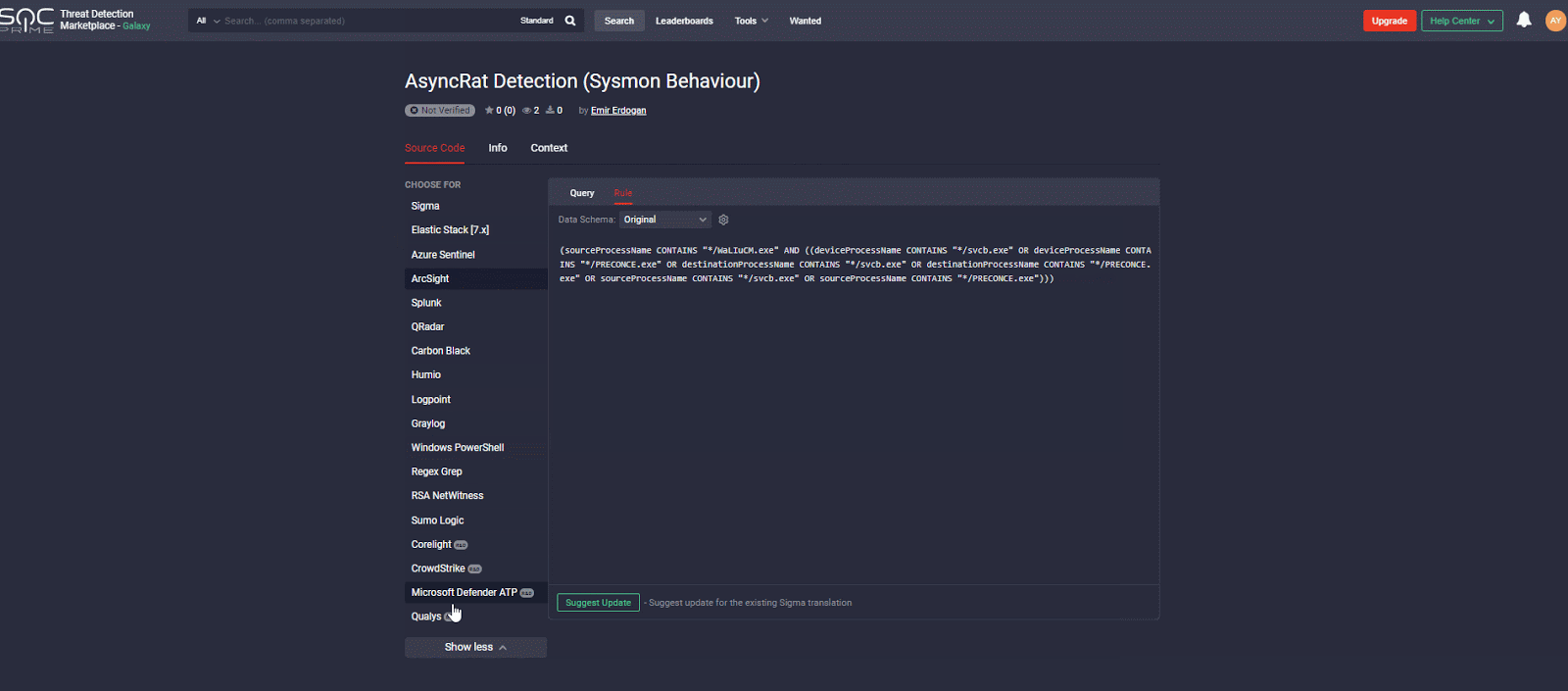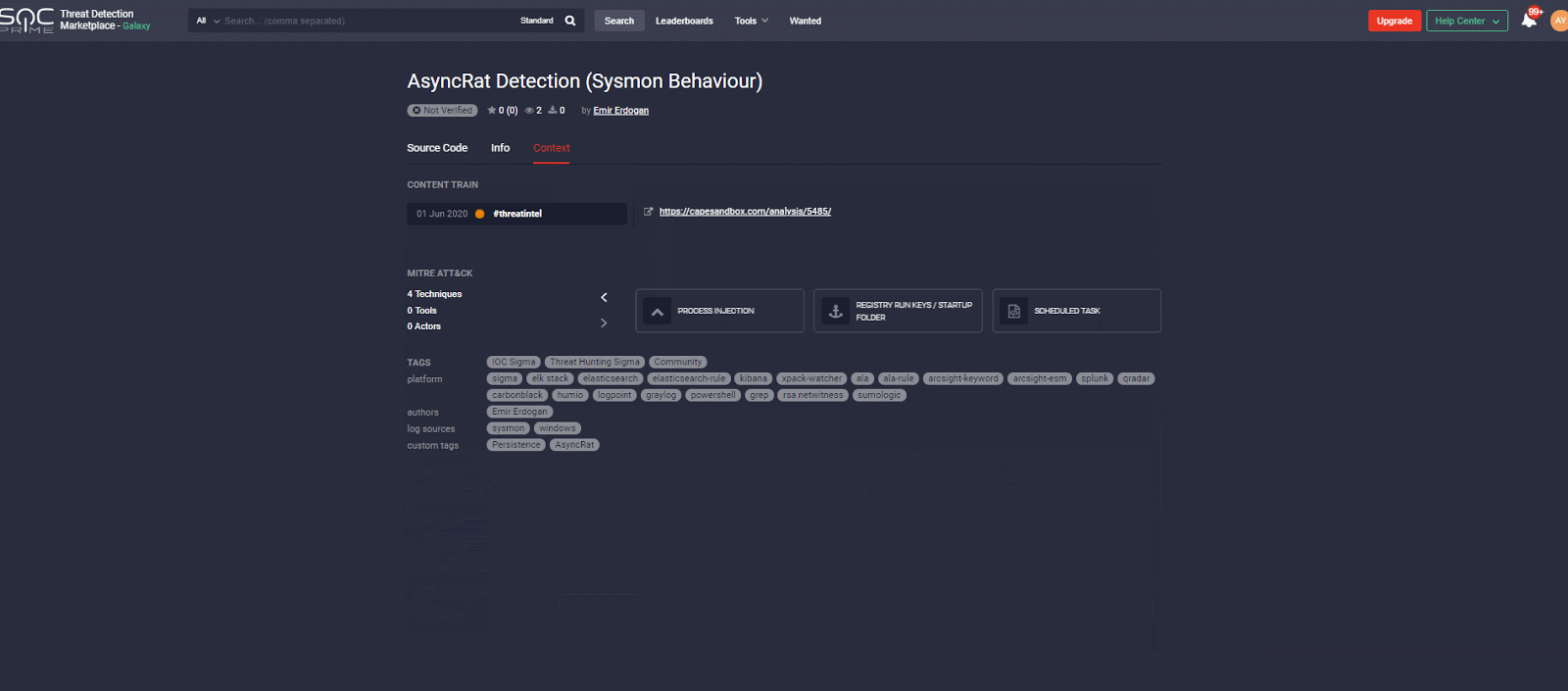
The rule has translations for the following platforms:
SIEM: Azure Sentinel, ArcSight, QRadar, Splunk, Graylog, Sumo Logic, ELK Stack, RSA NetWitness, Logpoint, Humio,
EDR: Carbon Black, Elastic Endpoint
MITRE ATT&CK:
Tactics: Defense Evasion, Privilege Escalation, Persistence, Execution
Techniques: Code Signing (T1116), Process Injection (T1055), Registry Run Keys / Startup Folder (T1060), Scheduled Task (T1053)