Threat hunting assisted by BlackEnergy mark

First, let me thank everyone for the feedback and comments on the previous article. It was quite thrilling to see how the theory holds up in practice.
After the article has been published, our colleagues from Talos shared with us the results of the signature application; all samples have been tested by us on VirusTotal and are recorded in the following table:
| # | Hash | Rating |
| 1 | Hash: b13c462151177a1ef112ae938ed6a52f26195d9759017cce1c82840069fb9ba6 Name: Win32/TrojanDropper.Binder.NBH File submission: 21.12.2013 20:30 |
43 / 54 |
| 2 | Hash: 03c4ca20c96633f5e9b53026cb737bd9befa2f8701b057a4abf06d180de3c356 Name: Win32/Adware.Virtumonde File submission: 24.03.2014 3:43 |
51 / 56 |
| 3 | Hash: 3bf213c1e8ec915cf5bca3ab97158337832cb6dd66438e22650d9e7825fc0d33 Name: Gen:Variant.Graftor.161021 File submission:07.03.2016 20:56 |
11 / 53 |
| 4 | Hash: 3e69db57ebbd14115ce2371527d4da503854ef55b9898547a50be2b90140c811 Name: Win32/TrojanDropper.Agent.DGO File submission: 31.10.2011 16:20 |
52 / 56 |
| 5 | Hash: 04b1059085af0a345ffbe3cb110a910e1f92ad586c63f078bb0555e7c2cbcc4f Name: Win32/Dumaru.AF File submission: 08.06.2009 20:37 Interesting sample names: Jiangmin Worm/Sramota.akb |
49 / 56 |
| 6 | Hash: 8b6ba59b291826109e76757a87b52c8499ab250f0bc18de81117ff816b0bc732 Name: Win32/Dumaru.Y File submission: 10.04.2009 19:02 |
46 / 56 |
| 7 | Hash: 9ec01dab187f3578a42b0a2317e1927d311a0d7b958bfb999d6413fd70f786fa Name: a variant of Win32/Kryptik.AXDV File submission: 07.03.2016 15:58 Behavior: 175.41.29.181:80 |
45 / 56 |
| 8 | Hash: 9f3d6ac4bddec3f9b568147ce8430daa75417c0ea6741dcd24664838de81b222 Name: a variant of Win32/Alinaos.B File submission: 07.03.2016 8:40 Interesting sample names: Kaspersky Trojan.Win32.Bublik.drvb |
37 / 54 |
| 9 | Hash: b0d6e3a685e6e004087b1306c60aea544d333bf1c9d6454e22e98ef05097ed64 Name: Win32/AutoRun.Agent.AFJ File submission: 14.05.2012 7:42 Interesting sample names: Baidu-International Trojan.Win32.Zapchast.aews |
51 / 54 |
| 10 | Hash: 7568e3e71607e2b2c76ac4836c4284fe8561388b335442f4a5ecbae78ea48079 Name: Trojan.Win32.Monderb.bifs File submission: 18.06.2011 8:17 |
40 / 56 |
| 11 | Hash: 425336c65bd42720330c09f1ae8128ac9120257032db51bbd7f900f419c5d14a Name: Win32/Dumaru.Z File submission: 10.04.2009 18:56 |
48 / 56 |
| 12 | Hash: 555928dddb20eab93858a2d815ce50a9315444be0c938cc4d7e8cc7ee3df18d3 Name: Win32/TrojanDownloader.Small.OC File submission: 10.12.2007 3:54 |
46 / 55 |
| 13 | Hash: a0acc7a856dfec11d4f89dc42a46661d01006dc2e0fdbb20e82d00aeba3c3160 Name: Win32/TrojanDownloader.FakeAlert.AQI File submission: 04.07.2011 11:45 |
50 / 56 |
| 14 | Hash: b3546dc1244113cd5c14ba99aa2b98f2476fdfbddb36482ed624641b4b83d4ef Name: Win32/Agent.QXQ File submission: 07.03.2016 17:20 |
20 / 55 |
| 15 | Hash: cd86b354334af457c474c13901d905745edebbef5c23a276854cd2fb26795917 Name: Win32:Blackenergy-N Drp File submission: 07.03.2016 20:53 |
3 / 54 |
| 16 | Hash: f85e08a0d957be9eeb1d133e5a6c08a8c648c9310b9060ba7a986bb4e8d246f7 Name: Trojan.Win32.Generic!BT File submission: 07.03.2016 22:29 |
20 / 56 |
| 17 | Hash: ffc0e20dee78732ca31069738217a3aa5e9559a349fdf8f62325c3cec54e9171 Name: Win32/PolyCrypt File submission: 08.03.2016 13:06 |
29 / 57 |
As you can see from the table, we have 7 samples that had first appeared on the VirusTotal in the last couple of days.
The oldest sample is more than 8 years old.
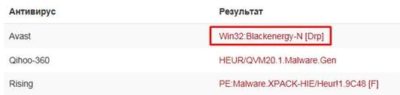
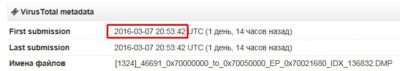
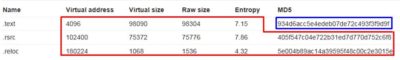
There is one sample that is identified only by three anti-virus solutions – cd86b354334af457c474c13901d905745edebbef5c23a276854cd2fb26795917 – and one of those solutions classifies it as BlackEnergy:
It has appeared just one day ago:
I propose you to join the hunt and fill in this table with your samples. It will be interesting to see the oldest sample and how many different samples we can “catch”. You can write the hashes right here in the comments. I hope the “hunt” for new samples will reveal patterns that are even more interesting.
Updated on March 11th
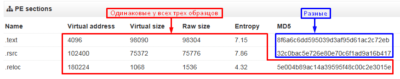
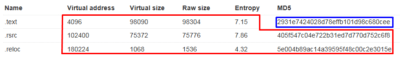
We have received three more samples. Based on the virus name, file size and other parameters it is obvious that we are dealing with mutation of the same source code, though as mentioned in the article the common attribute for these samples are the same hashes (8 bytes). Thus we can observe that this is yet another example how our simple signature has helped to tie the three samples to the same tool that was used to process the code during Weaponization phase before being delivered to the target. So despite the code mutation this could be detected earlier on during initial analysis stage.
| # | Hash | Rating |
| 1 | Hash: 3b69f60d97f9363c0b14edbd33adddc387d78064700c1d13fbdd68f7267e5020 Name: Win32/AutoRun.Agent.AFJ File submission: 06.03.2016 11:22:44 Interesting sample names: Kaspersky Trojan.Win32.Zapchast.aews |
42 / 53 |
| 2 | Hash: 045f1df82f5e3dd04337edc87a5795645a2598b7f8410c59330d02b18404e4ac Name: Win32/AutoRun.Agent.AFJ File submission: 06.03.2016 22:38:02 Interesting sample names: Kaspersky Trojan.Win32.Zapchast.aews |
48 / 56 |
| 3 | Hash: cf29a099172755733aeb7a0b9eeeacb3f5b02ea833c5010c2ee2ed85fa07e698 Name: Win32/AutoRun.Agent.AFJ File submission: 07.03.2016 20:31:02 Interesting sample names: Kaspersky Trojan.Win32.Zapchast.aews |
48 / 56 |
Of course, I do realize that Yara-signature I have developed is not a silver bullet, but it does help to conduct an interesting observation where such a simple method can reveal whole patters, a kind of litmus test.