At SOC Prime, we are constantly looking for ways to encourage the growth of our SaaS content community by enabling more security practitioners to join Threat Detection Marketplace: https://tdm.socprime.com/
We believe in the power of community that connects almost 10,000+ security specialists from 5,000 organizations across the globe and is expanding at a dynamic pace to serve as a tremendous source against cyber attacks.
Check out what’s new from SOC Prime.
Simplified Registration Flow & Free Access with Your Personal Email
We’re thrilled to introduce our simplified registration flow for your streamlined Threat Detection Marketplace experience. You can now sign up for the platform using an OTP sent to your email address as an alternative to the password hassle to shave seconds off the kickoff platform experience.
We’re always adding flexibility to the majority of the platform features for your most customized Threat Detection Marketplace experience. Users who wish to set up their secure password for the login flow can now do this right from their Profile settings, as well as change their password to a new one.
What’s more, we’re excited to reveal more opportunities for free access to Threat Detection Marketplace. We’ve recently introduced the ability to sign up for the community using your personal email address rather than a corporate one. Free users who have registered with their personal emails, get the Limited Community Access subscription that has certain limitations to the Threat Detection Marketplace functionality and content views, but still can be an option to get an idea of the platform capabilities. You can always switch to a corporate email address in a matter of clicks and upgrade for free to the Community subscription.
Role-Based Platform Experience
This month, we’ve come up with improvements that will help security professionals get targeted content relevant to their role that includes their role-based use cases. The newly released enhanced registration flow enables users to specify their professional role from the 15 most common in the cybersecurity field, including CISOs, SOC Managers, InfoSec / Cyber Team Leads, Red Team Specialists, Threat Hunters, Vulnerability Management Specialists, SOC Analysts, SIEM Content Developers, and more.
To get a clear picture of available roles and what use cases and platform capabilities can add to your role-based Threat Detection Marketplace experience, check out here.
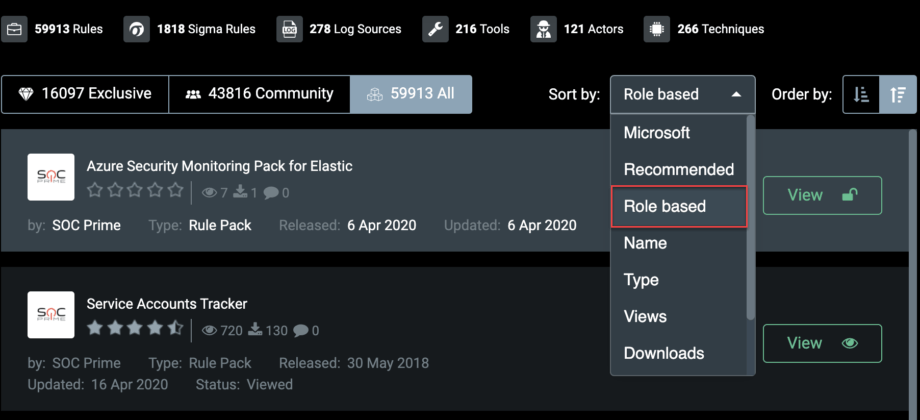
Based on this professional profile, we’ve enhanced the content boosting functionality of Threat Detection Marketplace. Now users who have identified themselves as Cyber Threat Intelligence Analysts will see content boosted according to their professional needs, such as queries for historical IOC matching and TTP-based detections. The selected sorting option on the Search page will be displayed as Role-based.
For an even more personalized search experience, the updated boosting functionality will also display content sorted by the user’s platform preferences specified during the registration flow.
New Integrations & Integration Enhancements at Threat Detection Marketplace
Sysmon Integration
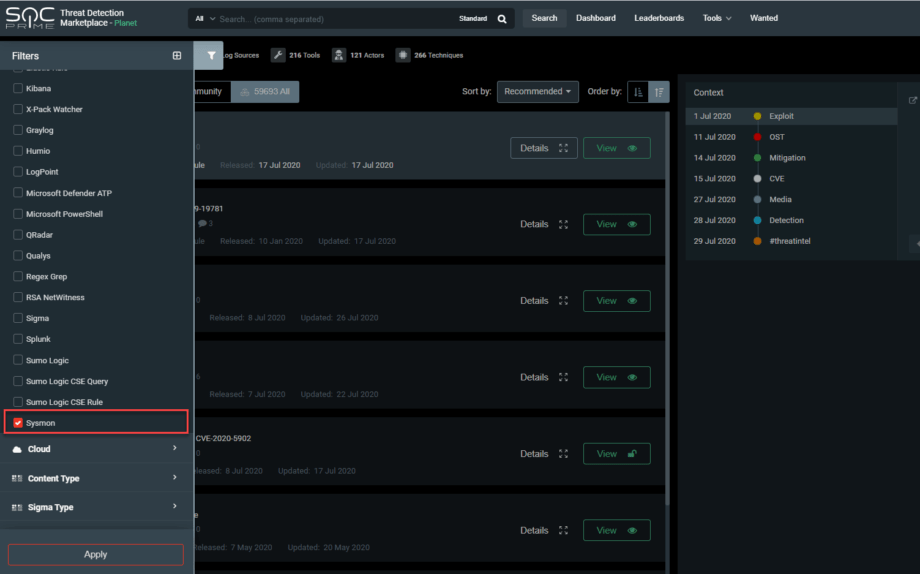
SOC Prime is constantly expanding its support for various SIEM, EDR, and NSM solutions to add even more flexibility to the Threat Detection Marketplace platform. We’ve recently added support for Sysmon, so security specialists can leverage the threat detection content for this platform. You can now select Sysmon from the Platform parameters in the Filters panel, click the Apply button, and enjoy your platform-specific threat detection content that you can apply directly to your Sysmon configuration file.
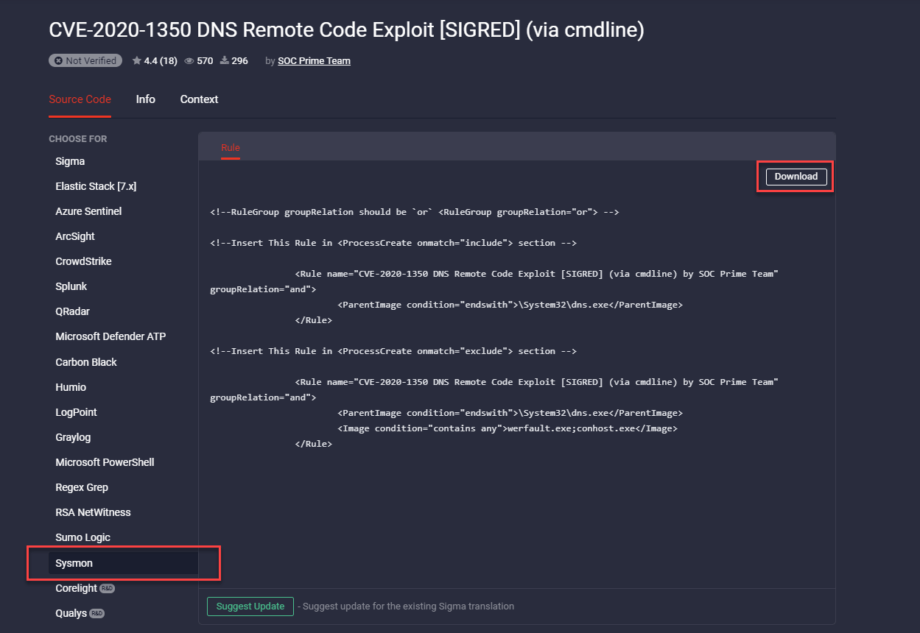
By adding the Download button to the rule page, we’ve added to the streamlined deployment of platform-specific threat detection content to your Sysmon configuration file.
Elastic Cloud Integration
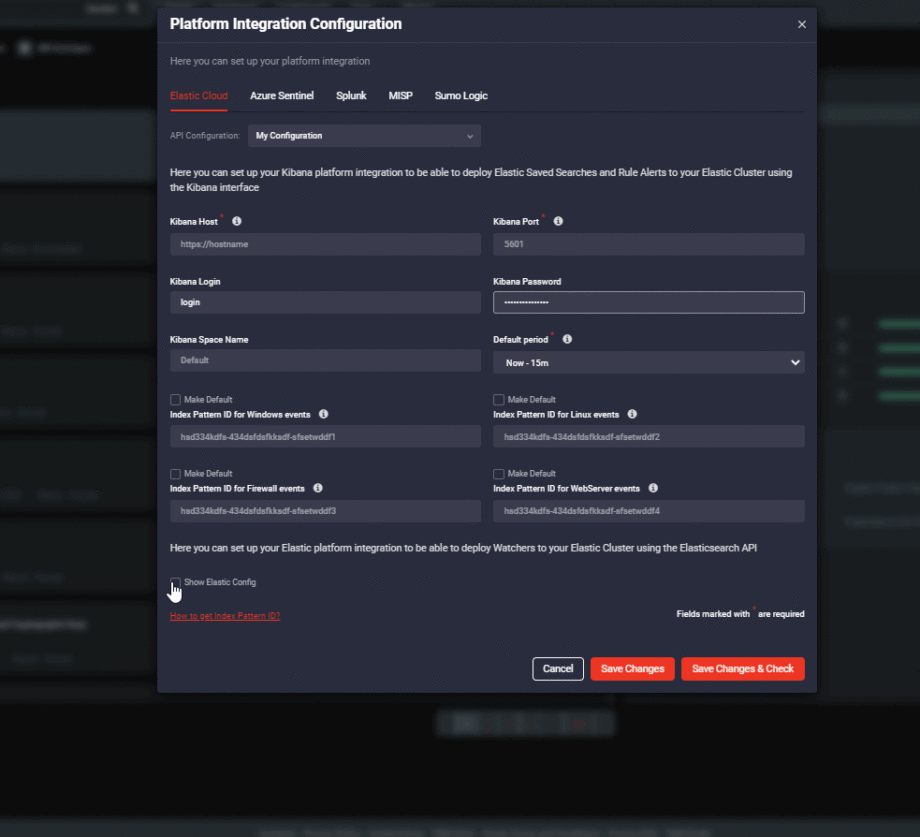
In August, we enriched the Threat Detection Marketplace platform with the Elastic Cloud integration. You can now set up your Kibana and Elasticsearch integration in one place to streamline your Elastic Cloud implementation workflow and deploy Threat Detection Marketplace rules to your environment with just a single click. To configure your Elastic Cloud profile, select the corresponding tab in the Platform Integration Configuration settings.
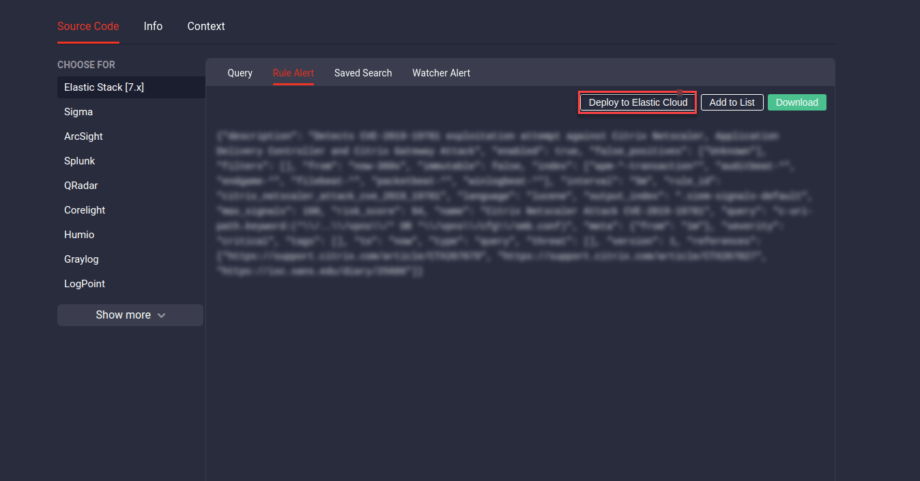
For a more streamlined threat detection experience, you can now deploy content to your Elastic Cluster with a single click right from the rule page for the following content types:
- Rule Alert
- Saved Search
- Watcher Alert
Platform Integration Configuration: API Profile Sharing Settings for Azure Sentinel, Elastic Cloud, and Sumo Logic
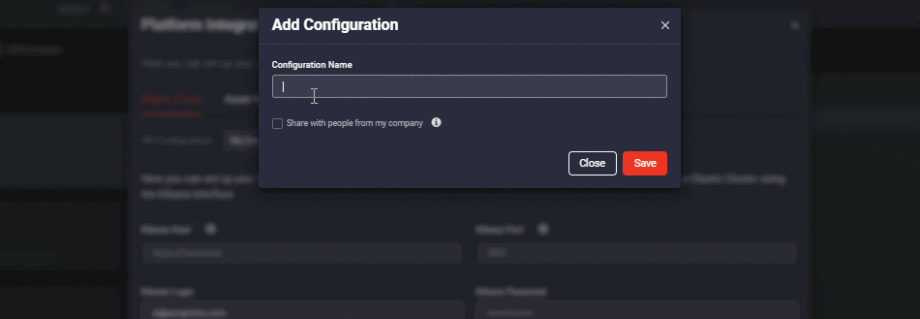
We’ve also extended the Platform Integration Configuration settings for Azure Sentinel, Elastic Cloud, and Sumo Logic platforms. These newly added sharing settings enable you to switch between the company-wide and individual access levels of the configured API profile for one of these SIEMs. By default, the API configuration profile is visible only to its author, but these settings can now be changed to enable a company-wide access to the configured profile. By selecting the Share with people from my company checkbox, the API configuration profile will be available across the entire company.
Join SOC Prime Threat Detection Marketplace now to boost your proactive exploit detection and keep abreast of the latest cybersecurity news: https://tdm.socprime.com/