At SOC Prime, we are constantly expanding the list of supported SIEM, EDR, and NTDR solutions to add more flexibility to Threat Detection Marketplace and streamline the threat hunting experience for security performers regardless of their XDR stack.
We are glad to announce our partnership with SentinelOne to deliver curated content for this prominent security platform that enables full XDR protection for endpoint, IoT, and the cloud. SentinelOne was named a Leader in the 2021 Gartner Magic Quadrant for EEP and earned the highest score for all Use Cases within the 2021 Gartner Critical Capabilities for EPP report. Now, Threat Detection Marketplace ensures an even more powerful and versatile content base by enriching Sigma rules with translations to a new SentinelOne format.
Deploying SentineOne Queries to Your Instance
As of May 2021, Threat Detection Marketplace users can reach almost 2,000 SentinelOne Queries ready for seamless deployment directly to their instances. Alongside the Hunting Queries natively available in SentinelOne, security performers can use SOC content thoroughly mastered by SOC Prime’s community of cybersecurity experts to cover critical and specific threats challenging organizations globally.
Searching Queries
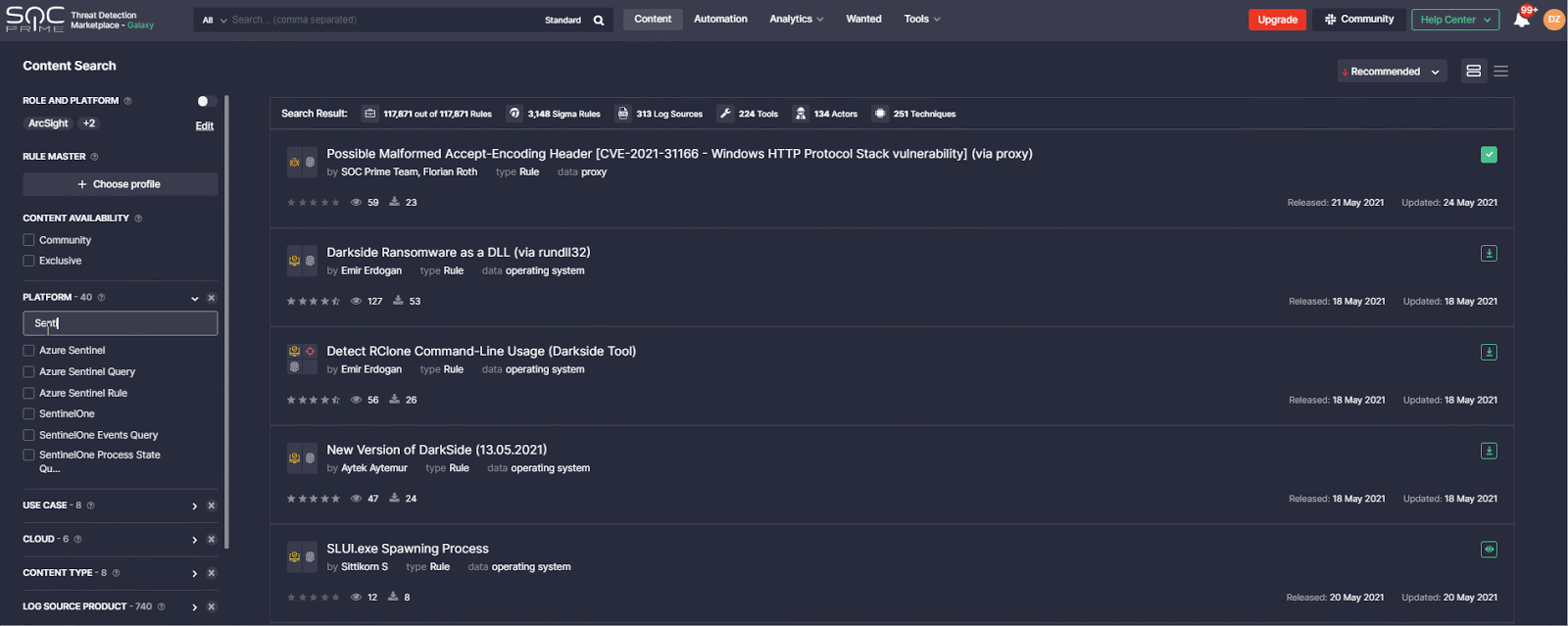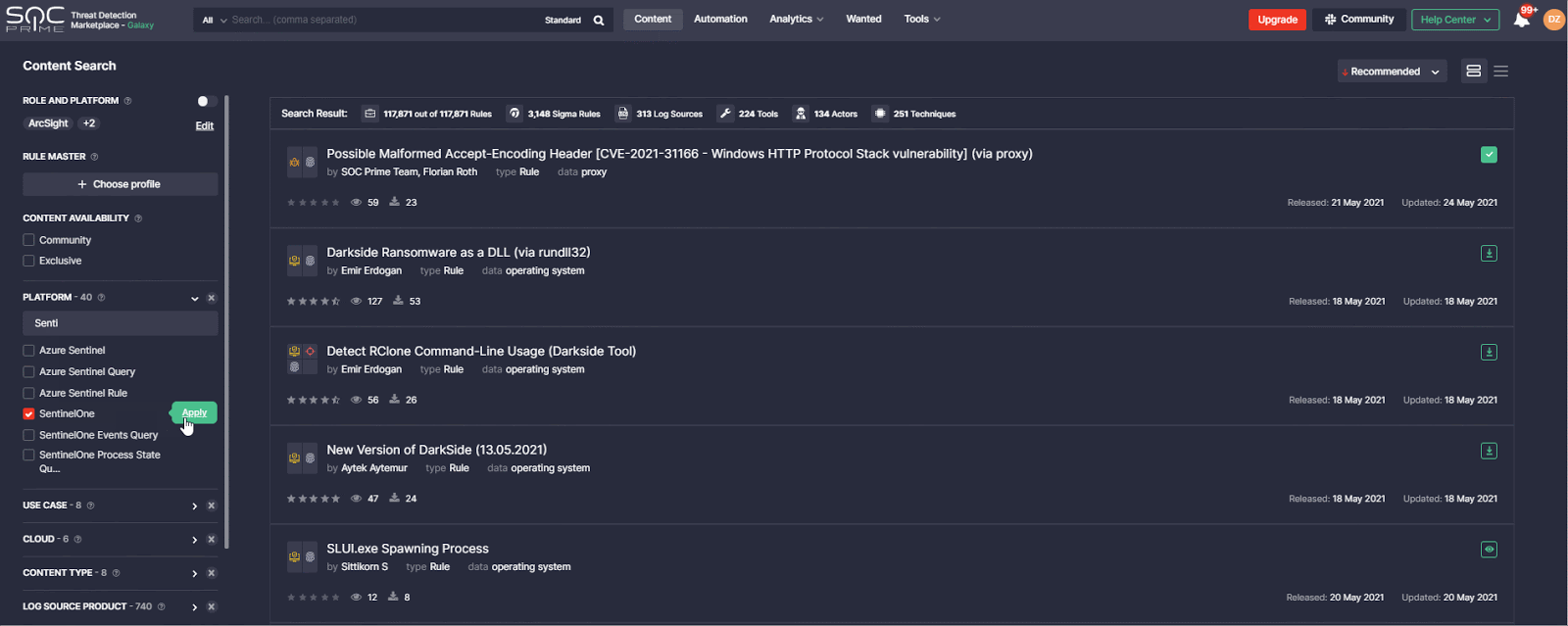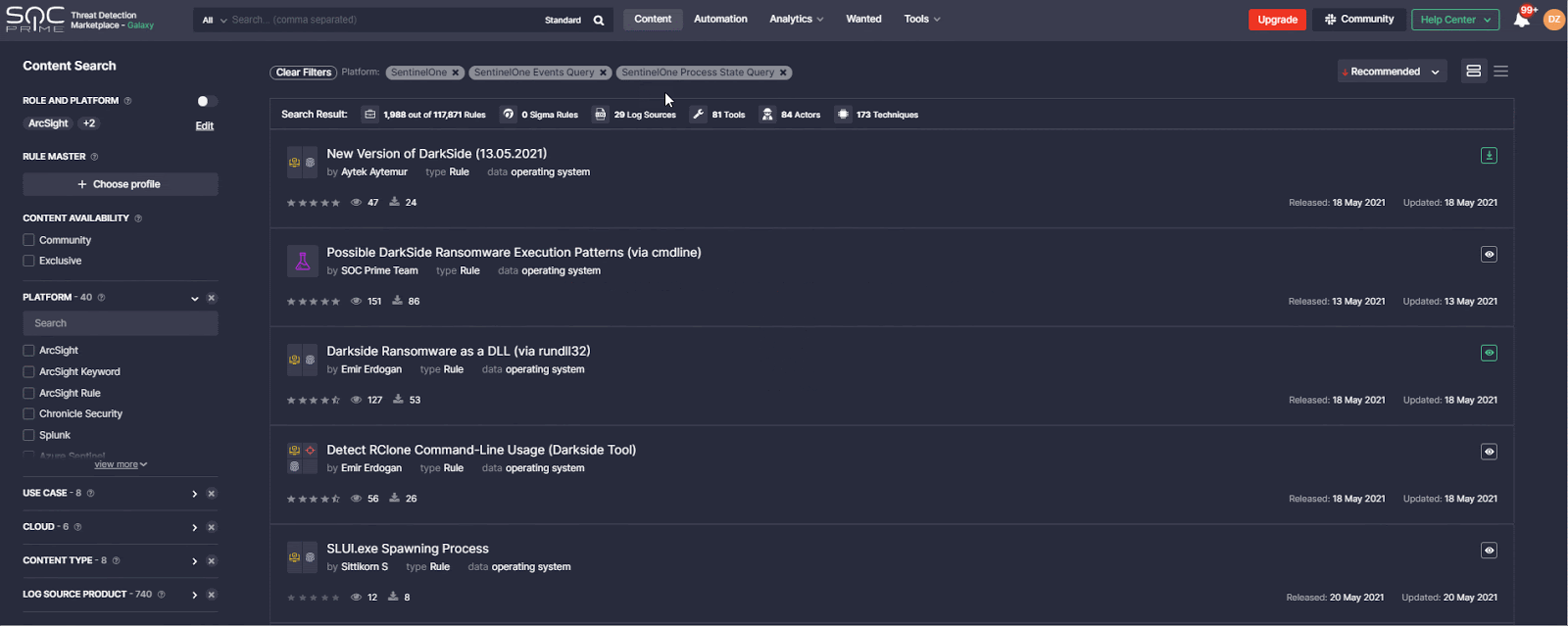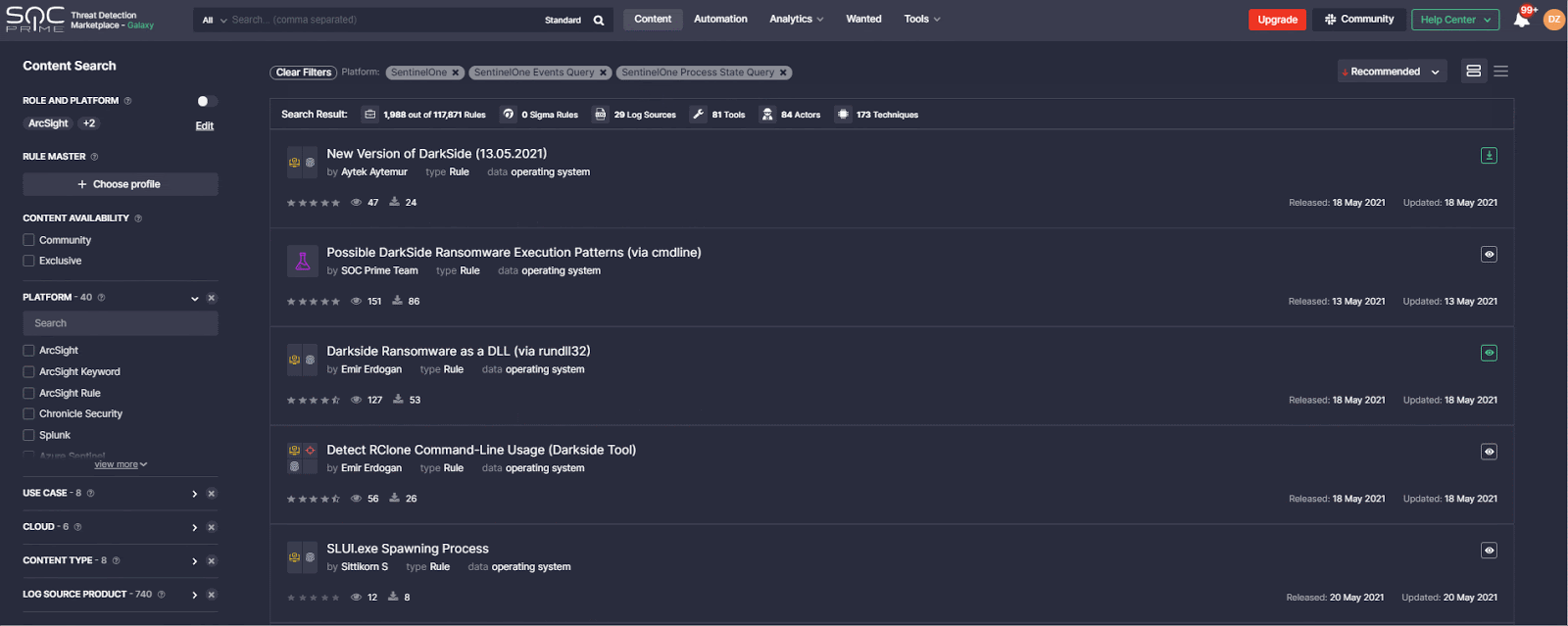
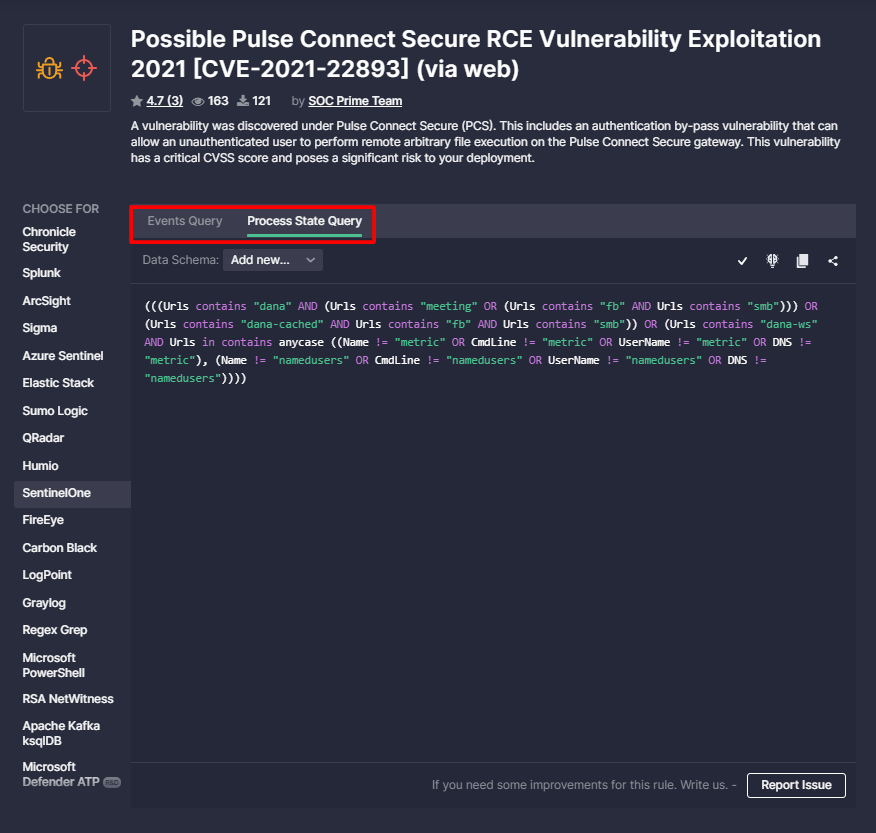
To find relevant detections matching your request, you can easily filter all SOC content available in Threat Detection Marketplace by the SentinelOne platform on the Content page. For more specific search results based on a certain content type, you can also filter detections by Sentinel Event Queries or Process State Queries.
Deploying Queries
Once filtered, you can drill down to the Content page and then copy the query source code to their SentinelOne instance on the fly. To сhoose the content relevant to your needs, you can switch between Event Queries and Process State Queries via corresponding content type tabs.
On-the-Fly Translations to SentinelOne
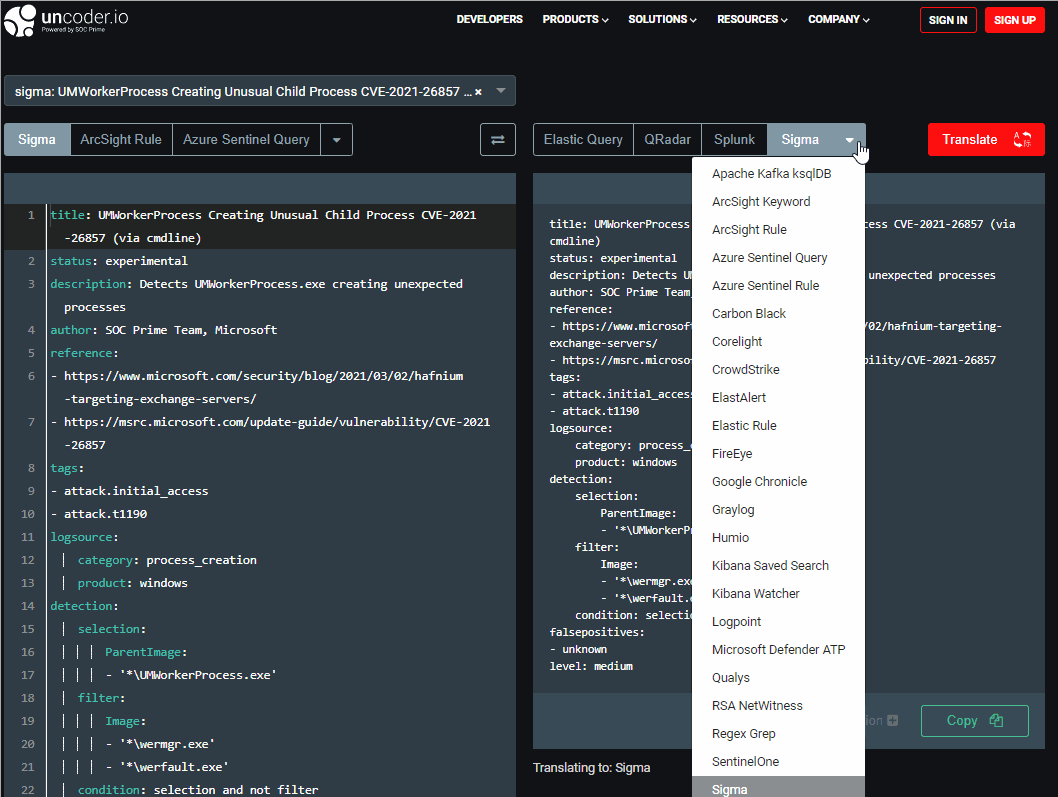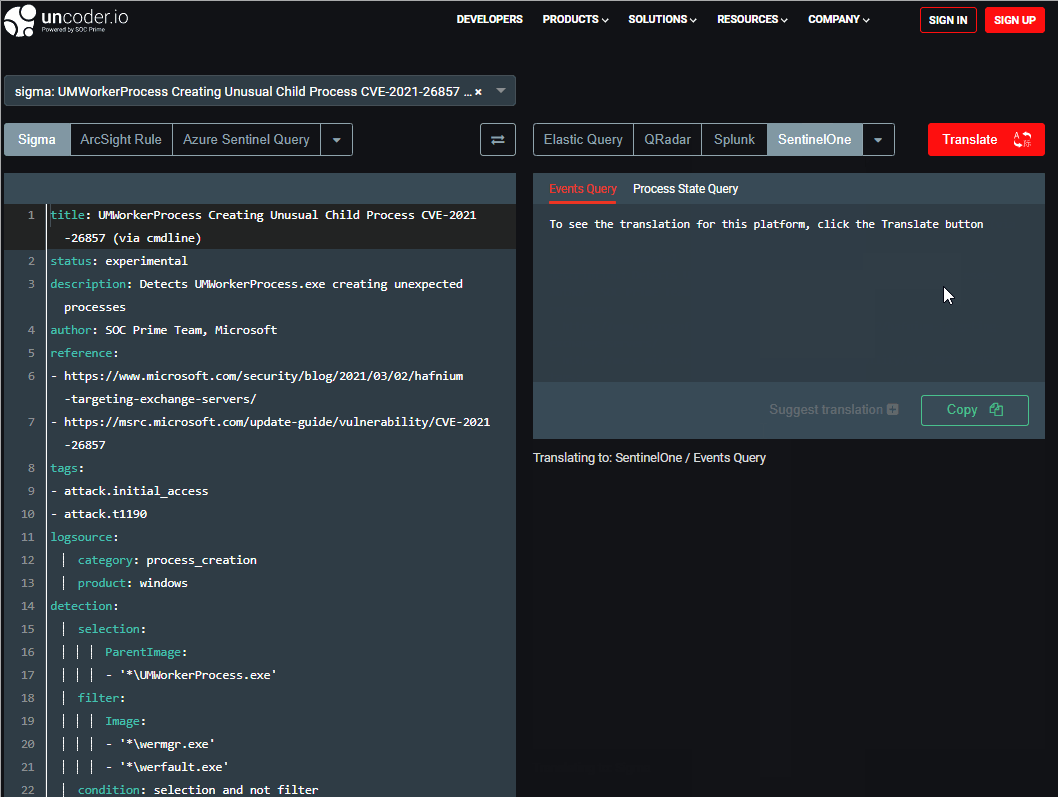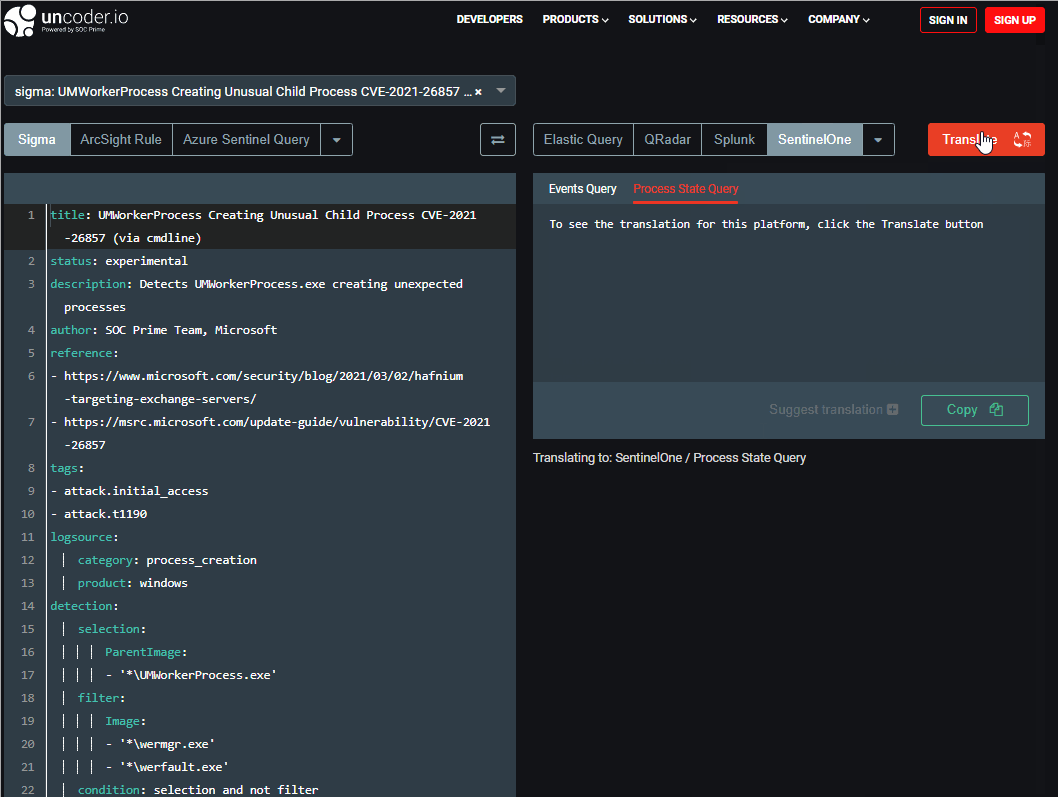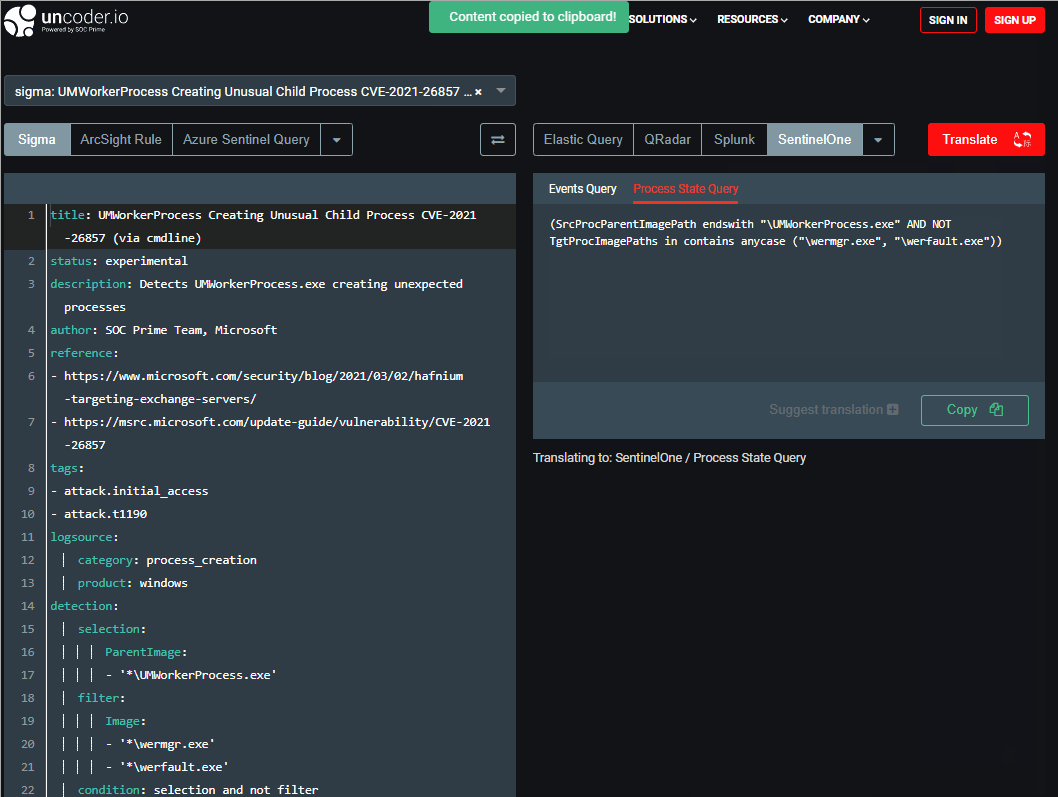
To help security performers expand their capabilities beyond a single technology, SOC Prime supports seamless translations from the generic Sigma language to other language formats using the Uncoder.IO. You can use our free online translator tool to convert detection rules of interest into SentinelOne Query formats.
To get the translation for the required detection content, paste a relevant item written in the Sigma rule format into the left text box. Then, you need to choose the SentinelOne as an output language from the dropdown menu list of supported platforms on the top right and select the desired content type. Uncoder.IO supports both Event Queries and Process State Queries translation formats. Finally, you can press the Translate button and copy your translated SentinelOne Query from the text box on the right.
To help security practitioners streamline their threat hunting activities, we continuously curate the Threat Detection Marketplace, an industry-leading Content-as-a-Service (CaaS) platform that powers complete CI/CD workflow for threat detection. Our platform provides qualified, cross-vendor, and cross-tool SOC content aggregating over 100K queries, parsers, SOC-ready dashboards, YARA, Machine Learning models, and Incident Response Playbooks tailored to 23 market-leading SIEM, EDR, NTDR, and now XDR technologies. Eager to participate in our threat hunting initiatives and craft your own detection content? Join SOC Prime’s Threat Bounty Program!




