+30% bonus on Threat Bounty Payout for March and Steady Income Generation on Threat Research in times of WFH and COVID19
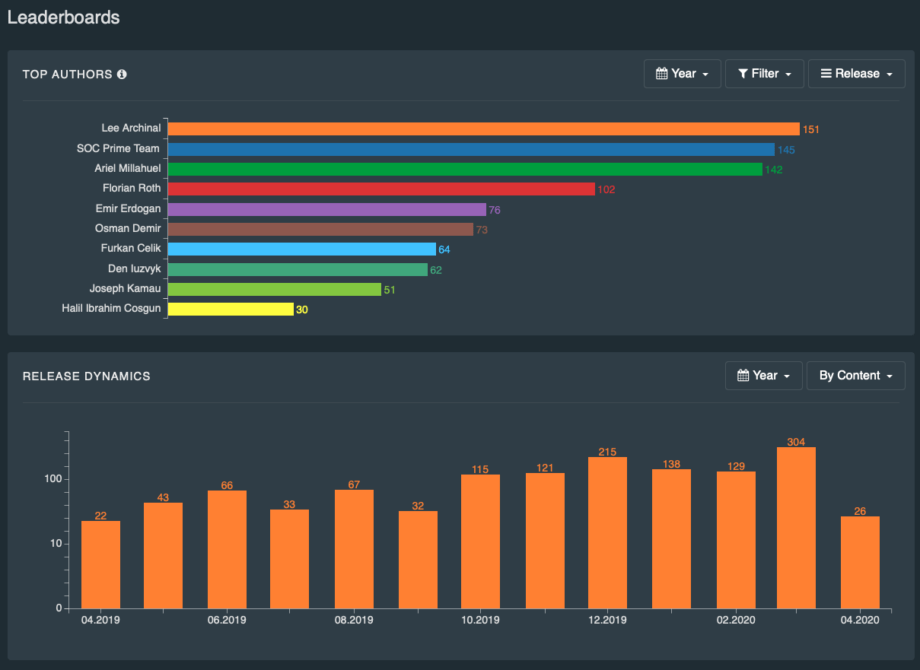
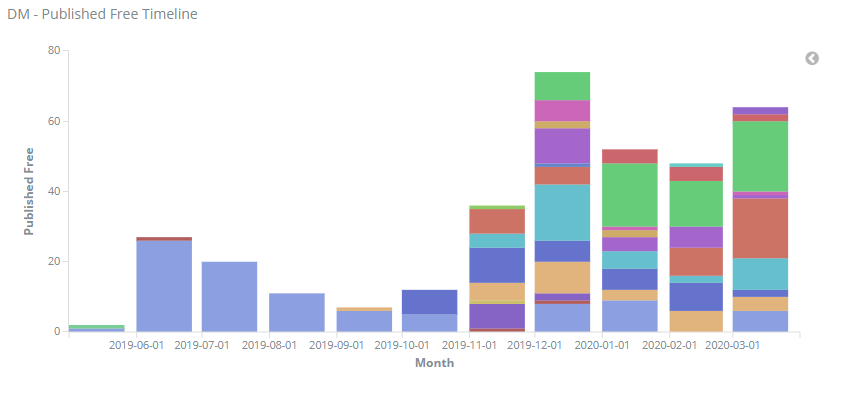
“We are witnessing the cyber security industry transformation. Software has progressed from waterfall and kanban to agile processes and CI/CD. The discipline of threat detection engineering has evolved too. This became possible due to Sigma language, MITRE ATT&CK, and the evolution of SIEM platforms API’s. I foresee this evolving even further with cloud-native SIEM technologies, allowing us to rapidly deploy and update sophisticated threat detection and analysis algorithms as they become available and needed. SOC Prime is committed to lead the charge of innovation to enable agile cyber defense capabilities on the global scale, improving every major SIEM and EDR technology. And we are most grateful to our Threat Bounty Program members. As a start, I am glad to share that we increased the March 2020 payouts by 30% for everyone who contributed content last month. We live in times when the detection engineer, the author, has the middle role. Together, we have just broken a new record releasing the 300 new detections in March 2020! And the best is yet to come.” – Andrii Bezverkhyi, CEO, SOC Prime
Centralized Cyber Defense Coordination
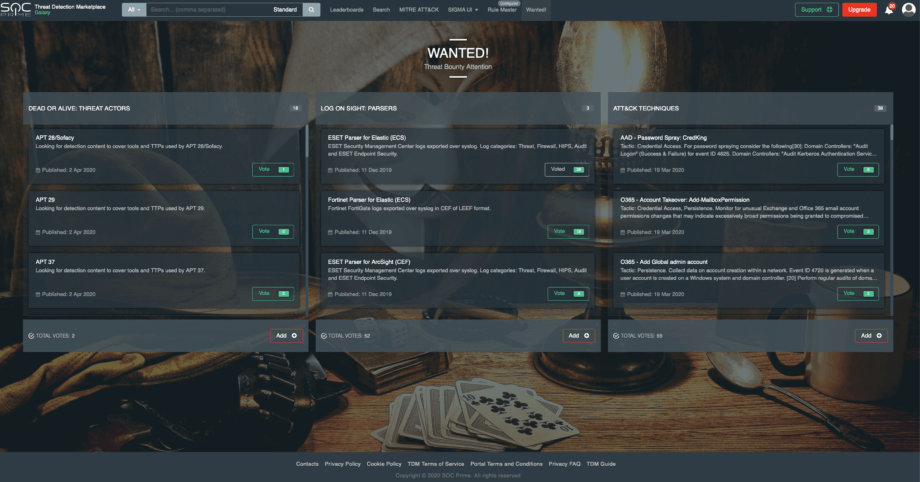
To align the Threat Bounty Hunters with their Analyst counterparts we now made the Wanted! Page the starting one at the Threat Detection Marketplace. Any member of the 8000+ community can cast their votes on what threats and risks need more attention.
Bounty Rating and Community Relationships, by Alla Yurchenko
Uniting the cybersecurity community has always been the mission of SOC Prime. The Threat Bounty Developer Program for TDM was created as a means to bring face to face the cybersecurity researchers, threat hunters, detection engineers and security analysts who are always searching for the most relevant content to defend against emerging threats.
At the very beginning of the Program evolution, we used to interview each Program participant. During Zoom sessions, we learned about the content author’s experience, their technology toolset, content creation approach, as well as their suggestions and expectations about the Threat Bounty program. As Threat Bounty’s popularity grew, we shifted from calls to chats, messengers and emails, however, we always keep in mind that our mission is a better and stronger community of cybersecurity specialists.
By easy stages, back in May 2019, we started delivering the 3rd party developers’ content to the TDM users, alongside studying the clients’ behavior, as well as their needs and requests that further resulted in the creation of the Threat Bounty Wanted List.
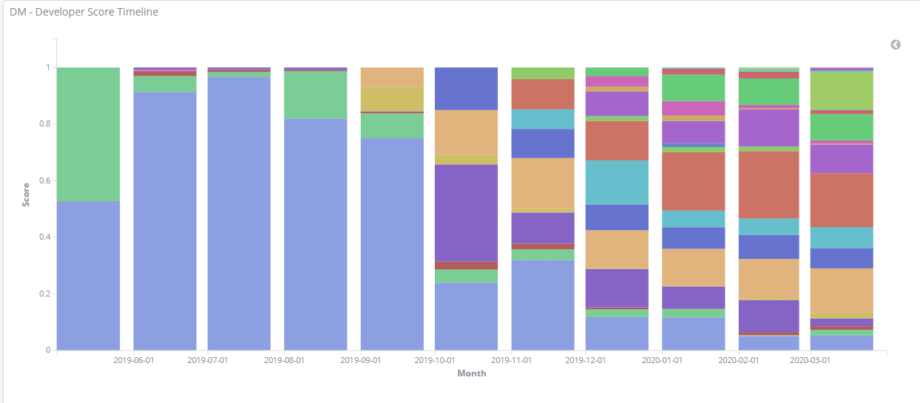
The content author’s rating is probably the most frequent subject of questions that we’re asked by the Threat Bounty developers. To make it clear, SOC Prime doesn’t buy the developed content at the moment of publishing, neither do we pay it per item or any large quantity. In simple terms, the content author gains rewards as long as their content meets the cybersecurity needs of the TDM clients; and what we calculate is the shared part of the total measured engagement of the TDM clients with the content ever published by a particular Threat Bounty developer for a calendar month.
Having studied the traction of the published content, we validated and established the current method of counting the meaningful TDM clients’ actions on the website with a certain weight assignment of each action and every published content type.
Another most frequently asked question is the content rejection reason. Bearing in mind our role in delivering actionable content to the TDM cybercommunity, our team keeps the dialogue with content creators whenever iterations of content development occur.
Protect the Cloud and Work From Home lifestyle
Needless to say, everyone is now focused on the WFH threats and technologies that make this possible. Zoom, Microsoft Teams and O365, Slack, ZScaler, AWS, Azure, G Suite and GCP need the most attention. It is no longer nice to have initiative, but a business continuity task for every major enterprise and public sector organization. Together, we can predict and outpace the adversaries, so every emerging threat, RCE vulnerability, and security misconfiguration are critical to address.
“It has become obvious that 2020 will be a very challenging year in economic terms. Many people are experiencing job shortage and uncertain prospects of steady income. This causes additional stress in times when caring for your own physical and mental health is paramount. From the very beginning we have founded the program on the value it creates for the cybersecurity community and not on empty slogans and hollow ideas. Which means that we are fully committed to run the program and payouts uninterruptedly despite the economic downturn. Additionally our program has always been envisioned as a remote operation so working from home is a regular course of action for its members. Luckily for us we have come to this storm prepared and are eager to welcome you onboard.” – Oleg Pasichnyk, CFO, SOC Prime.