Hot on the heels of the newly identified BQTLOCK ransomware distributed through a full RaaS model, security researchers have detected another major ransomware operation. A previously unknown group, dubbed The Gentlemen, has quickly gained attention for using highly specialized tools and conducting thorough reconnaissance to target critical infrastructure across 17+ regions and multiple sectors. Their campaign employs a mix of legitimate driver abuse, Group Policy manipulation, custom anti-AV tools, privileged account compromise, and encrypted data exfiltration channels.
Gentlemen Ransomware Detection
In the first quarter of 2025, Check Point observed a surge in ransomware attacks, climbing 126% compared to the previous year, with organizations facing an average of 275 incidents daily. The State of Ransomware 2025 report by Sophos highlights the main factors behind these attacks: 40.2% of affected organizations lacked sufficient in-house expertise, 40.1% had unidentified security gaps, and 39.4% struggled with limited personnel or capacity, leaving them vulnerable to increasingly sophisticated threats.
While novel ransomware strains, like Gentlemen, continue to emerge, cyber defenders must rely on timely, high-quality detection content and advanced cybersecurity tools to keep pace with the rapidly evolving threat landscape.
Register for the SOC Prime Platform and obtain timely threat intelligence and actionable detection content, backed by a complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection. Click the Explore Detections button below to access a curated stack of Sigma rules designed to identify and respond to Gentlemen ransomware activity.
All the rules in the SOC Prime Platform are compatible with multiple SIEM, EDR, and Data Lake solutions and mapped to the MITRE ATT&CK® framework. Additionally, each rule is packed with detailed metadata, including CTI references, attack timelines, triage recommendations, and more.
Optionally, cyber defenders can apply the broader “Ransomware” tag to access a wider range of detection rules covering ransomware attacks globally.
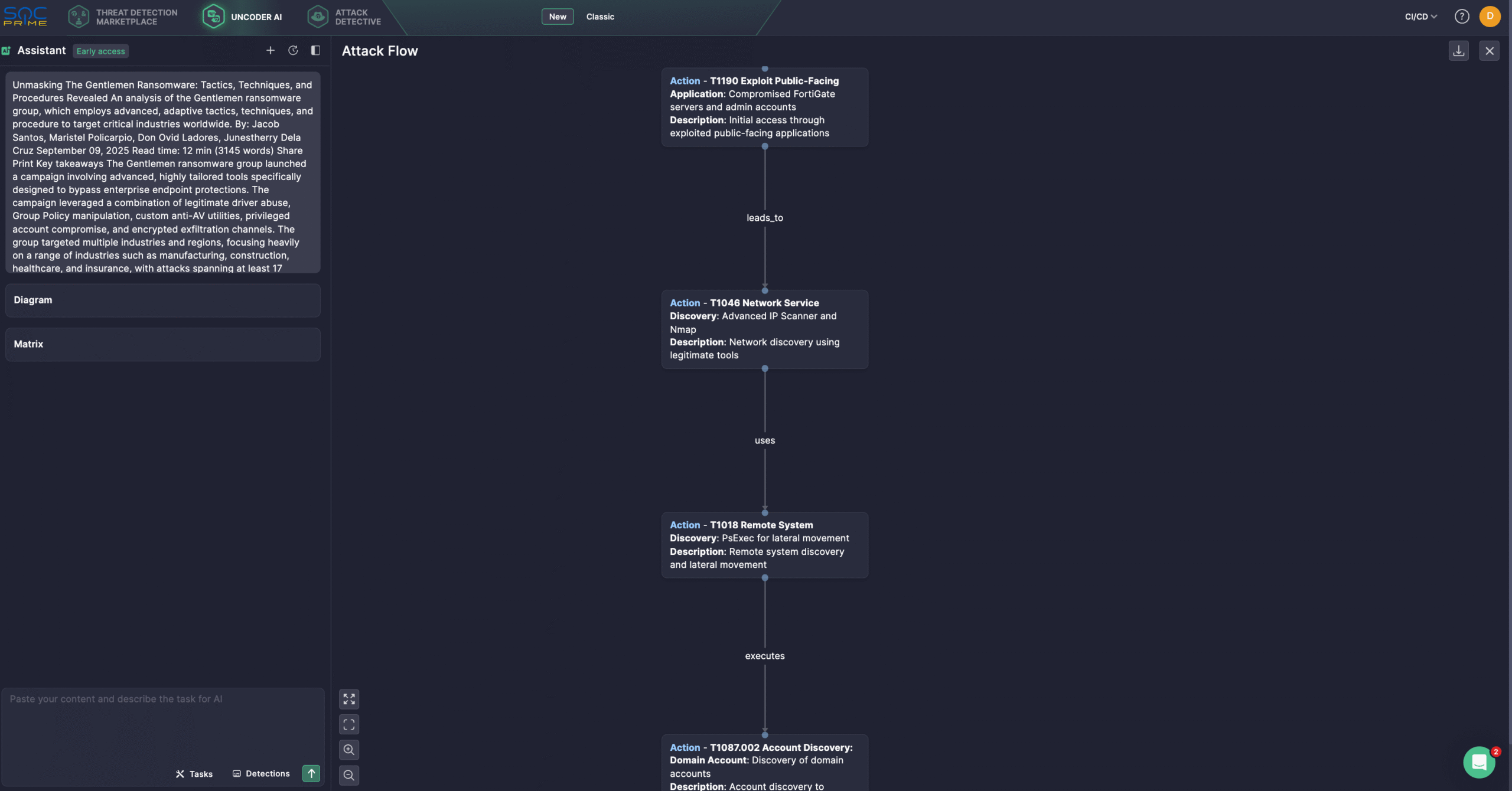
Security experts might streamline threat investigation using Uncoder AI, a private IDE & co-pilot for detection engineering. The latest Uncoder AI update introduces a new AI Chat Bot mode and MCP tools to help cyber defenders manage detection engineering tasks end-to-end. Enter a custom prompt in any language or choose from pre-built tasks in a dialogue-based, user-friendly interface while keeping AI grounded in your environment and threat landscape. For instance, cyber defenders can use Trend Micro’s latest report on Gentlemen ransomware to generate Attack Flow in a single click.
The Gentlemen Ransomware Analysis
In August 2025, Trend Micro researchers investigated a new ransomware campaign launched by The Gentlemen, an emerging and previously unknown threat group. Adversaries behind this campaign have swiftly made their mark on the threat landscape by systematically compromising enterprise environments and showcasing advanced operational capabilities. Notably, the Gentlemen ransomware group adapted its tools mid-campaign, evolving from generic anti-AV utilities to tailored, highly targeted variants while highlighting its versatility and persistence.
The Gentlemen primarily targeted organizations across the manufacturing, construction, healthcare, and insurance sectors, conducting attacks in at least 17 countries. They also leveraged privileged domain accounts for ransomware deployment and developed sophisticated evasion techniques to bypass security defenses and maintain persistence.
The Gentlemen likely exploited exposed internet-facing services or compromised credentials to gain their foothold. Early signs of network reconnaissance, such as the use of Advanced IP Scanner, indicate a deliberate, premeditated entry strategy rather than opportunistic exploitation. Adversaries used the tool to map infrastructure and probe Active Directory, paying particular attention to domain and enterprise administrator accounts, as well as custom privileged groups like itgateadmin.
A batch script (1.bat) was executed to enumerate more than 60 user accounts across the domain, and the attackers also queried both standard administrative groups and virtualization-related groups (e.g., VMware), signaling preparation for lateral movement across hybrid environments.
For initial defense evasion, the group deployed All.exe alongside ThrottleBlood.sys, abusing a legitimate signed driver to perform kernel-level process termination of protected security tools. After recognizing its limitations, the Gentlemen ransomware group conducted detailed reconnaissance of existing endpoint protections and shifted to using PowerRun.exe for privilege escalation, attempting to disable security services. They then introduced a custom tool (Allpatch2.exe) specifically designed to kill security agent processes, demonstrating their ability to tailor techniques to the victim’s environment. To move laterally, adversaries used PsExec and manipulated critical registry settings to weaken authentication and remote access defenses. They maintained persistent C2 access via legitimate remote tools, underscoring their expertise in blending living-off-the-land techniques with custom evasion utilities.
The Gentlemen ransomware aggressively targets and shuts down critical services tied to backup, database, and security operations to maximize disruption. It systematically kills processes via specific commands and goes further by executing additional commands to obstruct recovery efforts and hinder forensic analysis. As a final step, it deploys a cleanup batch script that introduces a short delay using a ping command, deletes the ransomware binary, and then removes itself, ensuring all traces are erased once the encryption process concludes.
The Gentlemen ransomware campaign illustrates the rapid evolution of modern threats, combining advanced techniques with persistent, targeted operations. By using custom defense-evasion tools, adapting to existing security controls, and exploiting both legitimate and vulnerable components, the group effectively bypasses layered defenses. Its focus on critical infrastructure and use of double extortion highlights the growing shift from generic ransomware to highly targeted attacks, significantly raising the challenges for detection, prevention, and response.Due to the Gentlemen ransomware group’s exploitation of internet-facing systems and VPNs, enforcing Zero Trust is crucial to block initial access and contain potential impact. As potential Gentlemen ransomware mitigation measures, organizations should limit and closely monitor domain controller share access while auto-isolating hosts that show signs of driver exploits or anti-AV activity. Applying time-bound privileged access with automatic de-escalation, detecting mass Active Directory queries and bulk group changes, and deploying deception on critical shares to catch reconnaissance early are also key measures to reduce the attack surface. SOC Prime curates a complete product suite for enterprise-ready security protection backed by AI, automated capabilities, real-time threat intelligence, and built on zero-trust principles to help global organizations elevate their defenses at scale.




