SOC Prime is always striving to extend the support for the most popular SIEM, EDR, NSM and other security tools, including cloud-native solutions, to add more flexibility to Threat Detection Marketplace. This enables security performers to use the tools they prefer most and solves the problem of migration to another back-end environment.
We are thrilled to announce the release of our integration with Sumo Logic cloud-native SIEM offering enhanced search and deployment capabilities that enable security practitioners to drill down to your Sumo Logic or Cloud Security Enterprise (CSE) instance on the fly.
Sumo Logic is a cloud-native platform that helps supercharge your security analytics and enables reducing MTTI and MTTR through real-time monitoring.
Integration with the Sumo Logic cloud-native platform is one more step toward proactive cyber defense by leveraging the platform real-time analytics with machine learning and threat intelligence capabilities.
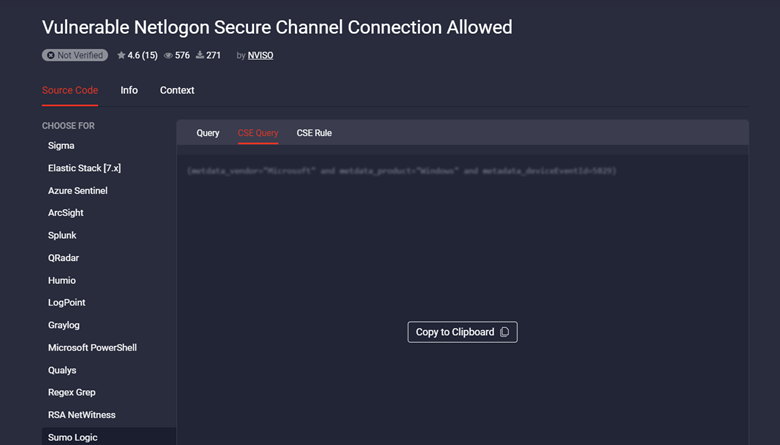
Threat Detection Marketplace currently offers 6,000+ content items for Sumo Logic and Sumo Logic CSE that address the latest exploits, CVE, malware, and TTPs and cover 216 out of 249 MITRE ATT&CK® techniques:
- Queries
- CSE queries
- CSE rules
Configuring Sumo Logic Integration
Searching or deploying threat detection content tailored to this cloud-native solution requires proper Sumo Logic configuration. To set up Sumo Logic integration, select Platform Integration Configuration from the user settings menu.
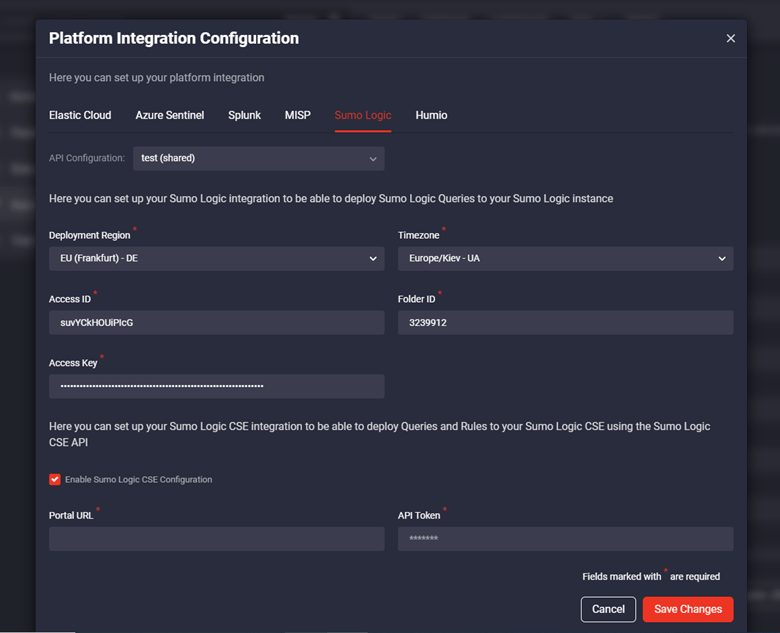
In the Platform Integration Configuration settings, you can set up two different integrations depending on the Sumo Logic content type you want to deploy:
- For queries, you need to set up Sumo Logic integration
- For CSE queries and rules, you need to set up integration with the Sumo Logic CSE
To set up integration for Sumo Logic CSE, select the Enable Sumo Logic CSE Configuration checkbox, and fill in the required Portal URL and API Token fields, and then click the Save Changes button.
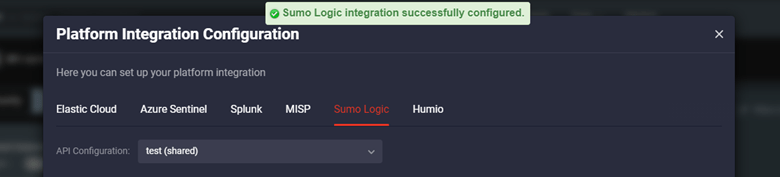
Once configured, you will see the success notification, and you’re all set to kick off your threat detection experience!
Deploying Sumo Logic Content, CSE Rules and Queries to Your Instance
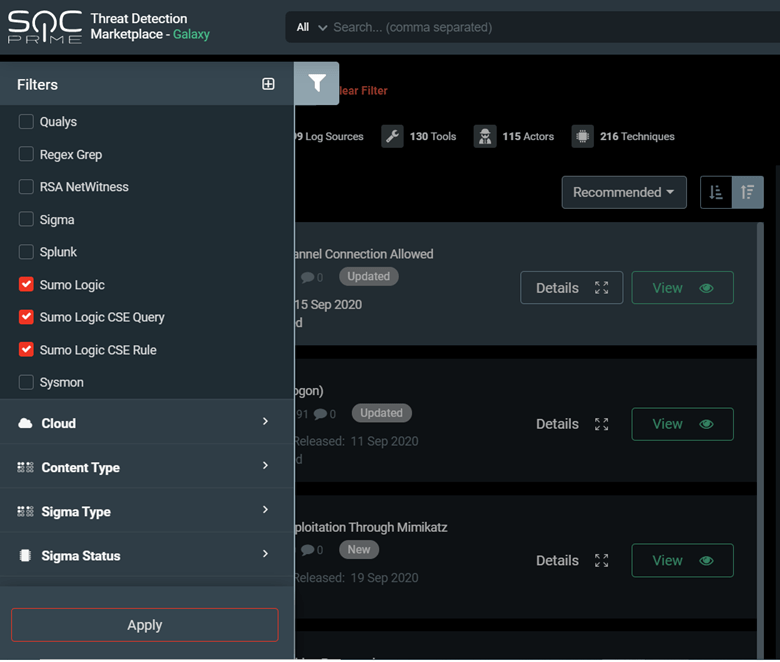
You can filter all Threat Detection Marketplace content by the Sumo Logic queries and CSE rules and queries using the Filters panel to get more targeted platform-specific content.
By selecting the specific rule that can be adjusted to the Sumo Logic or Sumo Logic CSE SIEM format, you can get the most of the streamlined content deployment right into your SIEM instance.
Searching and Deploying Queries
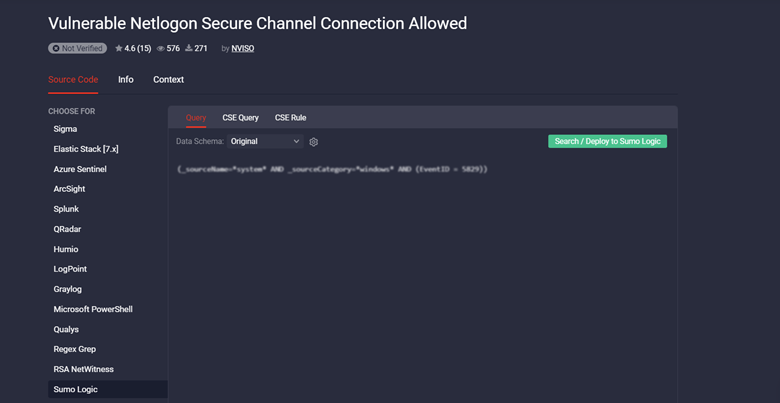
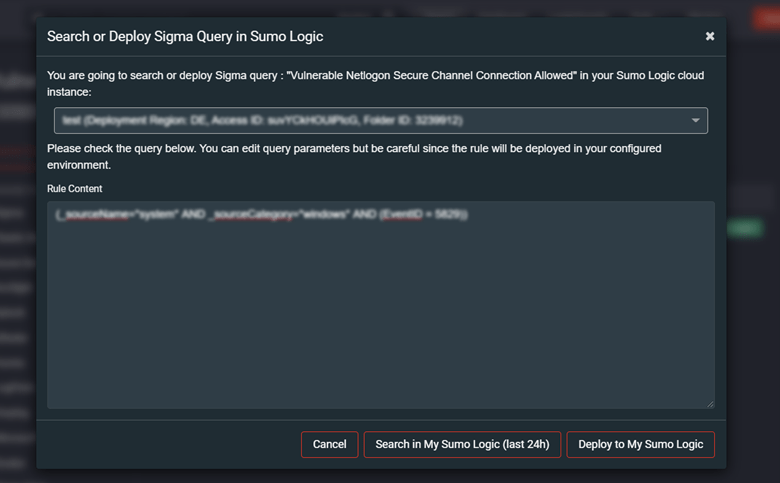
Threat Detection Marketplace allows searching or deploying Sigma queries into your Sumo Logic instance. Select the Query tab on the rule page, and then click the Search/Deploy to Sumo Logic button.
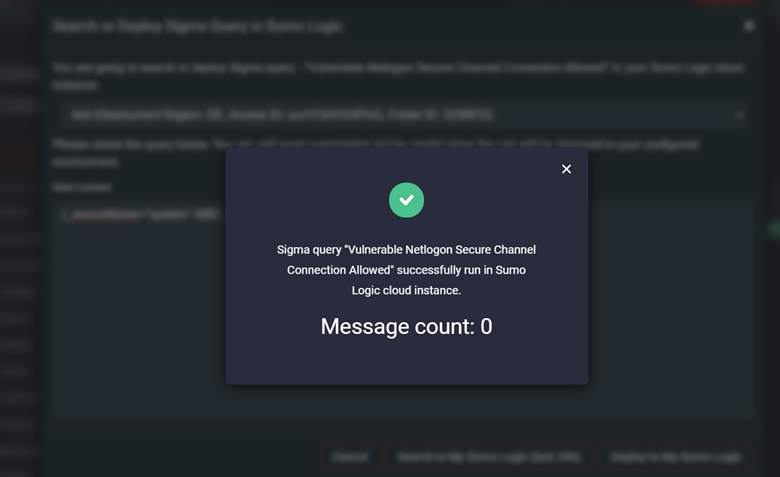
On the pop-up window that appears, check the query you are going to search or deploy, and make changes to it if needed. Select the action your are going to perform with the query by clicking the corresponding button:
- Search in My Sumo Logic (covers the period of 24 hours)
- Deploy in My Sumo Logic
Once the query deployment or search is successful, you will see a success notification that allows drilling down to your Sumo Logic instance with the deployed or executed query.
The successful deployment notification will also include a link that leads you to the directory within your Sumo Logic instance with the deployed query.
Deploying CSE Rules and Queries
Enhanced Sumo Logic integration with Threat Detection Marketplace enables deploying CSE rules on the fly right into your Sumo Logic CSE instance. The automated rule deployment is possible with the enabled CSE API integration for CSE rules.
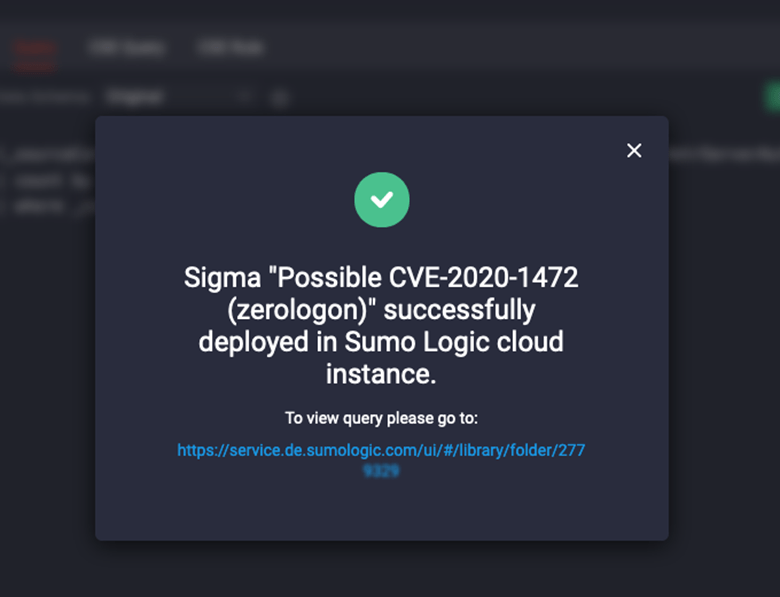
To try out the streamlined rule deployment, select the CSE Rule tab and click the Deploy to Sumo Logic CSE button.
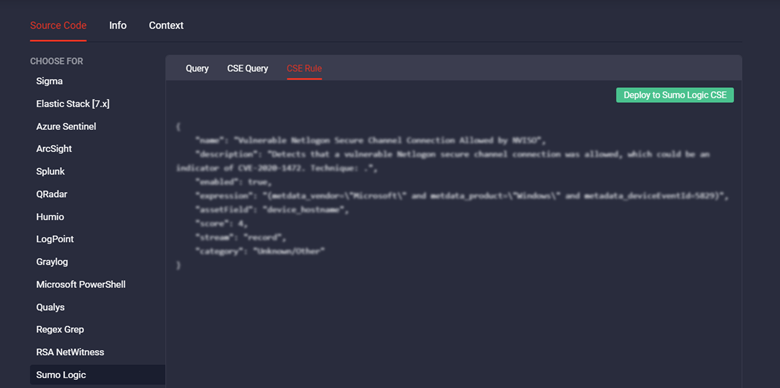
You will then move right to your Sumo Logic CSE instance where you can view and manage your deployed content items.
CSE queries can be deployed only manually since there is no API configuration available for this type of content. To deploy CSE queries, select the CSE Query tab, click the Copy to Clipboard button, and then paste the code right into your Sumo Logic CSE instance to the new Rule condition.
Looking for more threat detection content? Sign up for Threat Detection Marketplace to leverage 70,000+ rules, queries, playbooks, and other curated content items addressing the latest attacks and customized to your environment.