The cybersecurity landscape is constantly changing, and understanding complex attack scenarios is now critical for protecting organizations. One of the most effective tools for visualizing and simulating cyber attacks is Attack Flow v3.0.0.
Developed as an open-source project by the MITRE Center for Threat-Informed Defense, Attack Flow allows cybersecurity teams to model sequences of adversary actions, called attack flows, that lead to security incidents. By focusing on the relationships between tactics, techniques, and procedures (TTPs), the framework offers a structured, intelligence-driven way to understand and defend against cyber threats.
Attack Flow goes beyond analyzing individual techniques in isolation. By illustrating how attackers chain techniques together, defenders can anticipate attack paths, identify vulnerabilities before they are exploited, and improve the overall security posture.
SOC Prime’s AI-Native Detection Intelligence Platform fully supports Attack Flow v3.0.0. Using a RAG LLM model and MITRE ATT&CK® framework, it can automatically generate attack flows from threat reports with AI. This reduces the time needed to understand attacks and helps translate complex sequences into detection logic. Integrated with telemetry and detection rules, this highlights gaps and prioritizes threats effectively.
By combining AI-driven automation with Attack Flow v3.0.0, SOC Prime equips security teams with the ability to anticipate threats, enhance defenses, and respond faster to advanced cyber attacks.
What Is Attack Flow v3.0.0?
Attack Flow v3.0.0 is a language and toolset for describing and visualizing sequences of adversary behaviors, built on the MITRE ATT&CK framework. It allows cybersecurity teams to model how attackers chain together offensive techniques to achieve their objectives, capturing the full sequence of actions from initial access, lateral movement, and persistence to ultimate impact. By visualizing these sequences, defenders gain a deeper understanding of how techniques interact, how some behaviors set up others, and how adversaries handle uncertainty or recover from failure.
At its core, Attack Flow is a structured, machine-readable framework that provides both operational and analytical clarity. It represents the attack through a combination of key components:
- Flow: the overall sequence of actions and outcomes.
- Actions: specific adversary behaviors or techniques, each with a name and description.
- Assets: systems, data, or entities affected by actions, optionally including details like state or configuration.
- Properties: contextual information describing the characteristics or effects of actions and assets.
- Relationships: links defining how actions and assets influence each other within the flow.
By combining machine-readable precision with visual representation, Attack Flow makes complex attack behavior easier to understand, communicate, and act upon. This approach helps organizations answer critical questions: Which assets are most at risk? How do attackers move through networks? Which mitigations will most effectively disrupt attack chains? Ultimately, Attack Flow v3.0.0 equips defenders with actionable insights that go beyond static threat intelligence, enabling proactive, adaptive, and intelligence-driven defense strategies.
What Is Attack Flow for?
Attack Flow v3.0.0 is designed for any cybersecurity professional seeking to understand how adversaries operate, assess the potential impact on their organization, and determine how to improve defensive posture most effectively. Attack Flow supports multiple cybersecurity roles by converting complex attacker behavior into actionable insights. Its core purpose is to help teams understand, anticipate, and mitigate adversary activity across diverse operational contexts.
It is particularly valuable for:
- Threat Intelligence Analysts to track adversary behavior across campaigns, incidents, and threat actors.
- SOC (Blue) Teams to assess defenses, simulate attacks, and prioritize mitigations.
- Incident Responders to reconstruct attacks to identify gaps and improve response plans.
- Red and Purple Teams to emulate adversary behavior realistically using modeled flows.
- Managers and Executives to visualize business impact without complex technical details.
The framework facilitates cross-team communication by creating a shared visual and machine-readable representation of attacks. SOC members can see how defensive controls interact with attacker sequences, executives can understand business risks in terms of impacted assets or potential financial losses, and IT teams can prioritize security improvements based on actual attack paths.
What are Use Cases for Attack Flow?
Attack Flow v3.0.0 offers practical value across several domains. Some of the most impactful use cases include the following mentioned below.
Threat Intelligence
By focusing on attacker actions rather than easily altered IOCs, threat intelligence teams produce more reliable, behavior-based insights. MITRE Attack Flow examples allow analysts to track adversary sequences at incident, campaign, or threat actor levels. Machine-readable formats ensure flows can be shared across organizations and integrated into the existing security stack for detection and response.
Defensive Posture
Blue Teams use MITRE Attack Flow to evaluate and improve defenses by simulating realistic attack scenarios. By analyzing sequences of TTPs, defenders can identify coverage gaps, prioritize mitigation strategies, and strengthen security controls based on observed attacker behavior. This enables targeted improvements rather than blanket controls.
Incident Response
Incident responders can use the MITRE Attack Flow to understand how attacks unfolded and where defenses succeeded or failed. This helps in after-action reviews, documenting incidents, and improving future response strategies.
Threat Hunting
Threat hunters can use MITRE Attack Flow examples to identify recurring patterns of TTPs in their environments. This helps to guide investigations, construct detailed timelines, and support detection rules development.
Adversary Emulation
Red and purple teams can use the framework to design realistic adversary emulation exercises. Using MITRE Attack Flow examples, they can model sequences of TTPs to ensure precise and effective security testing.
Executive Communication
Attack flows transform complex technical activities into visual narratives for leadership, helping non-technical stakeholders understand the impact of attacks and make informed decisions about resources, tools, and policies.
Malware Analysis
Analysts can document behaviors observed during static, dynamic, and reverse engineering analysis. MITRE Attack Flow examples can help illustrate findings, improving reporting, detection creation, and defensive improvements.
How to Get Started?
To use Attack Flow effectively, teams should begin by familiarizing themselves with the MITRE ATT&CK framework, as attack flows are built directly on its taxonomy of tactics, techniques, and procedures (TTPs). A solid understanding of ATT&CK ensures that flows accurately reflect real-world adversary behavior.
Next, teams should explore the Attack Flow v3.0.0 project to understand its language, structure, and best practices for real-life application. This provides a foundation for building and interpreting attack flows effectively.
Additional resources to get started include:
- Exploring the corpus of Attack Flow examples provided by the MITRE Center for Threat-Informed Defense.
- Using the open-source Attack Flow Builder to create flows in a browser-based environment.
- Leveraging the SOC Prime Platform, which can help automatically generate attack flows from threat reports using Uncoder AI, or allow teams to review flows built from real-world threats in the Threat Detection Marketplace.
For a deeper technical understanding, developers and advanced users can refer to the language specification, developer guide, and GitHub repository, which provide comprehensive details for extending, integrating, or customizing Attack Flow for specialized use cases.
Core Structural Elements of Attack Flow v3.0.0
Attack Flow v3.0.0 relies on several core objects to represent adversary behavior:
- Actions: Adversary techniques that form the sequence of events.
- Assets: Systems, accounts, or data impacted by actions.
- Conditions: Clarify dependencies or decision points.
- Operators: Define logical relationships between paths (AND/OR).
- Additional STIX objects: Enrich flows with indicators, processes, and context.
These elements work together to depict success, failure, branching, and parallel attack paths, providing both operational and strategic insight.
Parallel Attack Paths
Attackers rarely follow a single route. The parallel attack paths model situations where multiple techniques are available for the same objective. For instance, after initial access, an attacker may attempt two different persistence methods; neither depends on the other. These paths show alternative routes without implying simultaneous execution.
Modeling parallel paths helps defenders identify choke points and coverage gaps. The Attack Flow allows cyber defenders to simulate “what-if” scenarios, compare mitigation effectiveness, and better understand attack divergence. At the incident level, parallel paths represent real attempted techniques, while at the campaign level, they summarize behavior across multiple events.
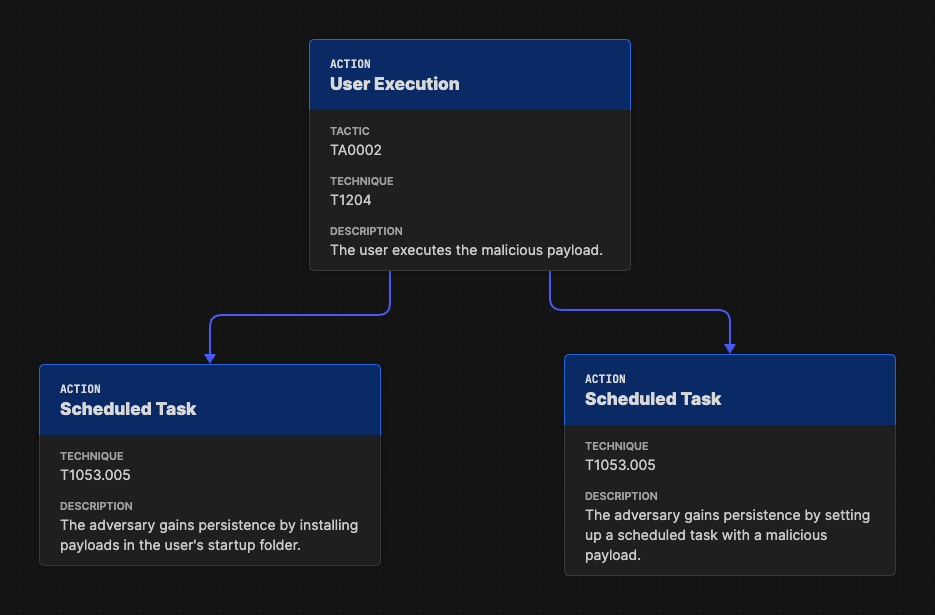
Visualization of multiple persistence techniques used by an adversary. The example is sourced from Attack Flow v3.0.0 documentation by the MITRE Center for Threat-Informed Defense.
Operator Objects
Operator objects define how multiple attack paths merge or interact, allowing cyber defenders to represent the logical structure of adversary decision-making. When an Attack Flow branches into several Parallel Attack Paths, operators bring those paths back together to show how success or failure in one or more actions affects what happens next.
There are two primary types of operators:
- OR: The attack continues if any of the incoming paths succeed. For instance, if an adversary uses two different techniques to pivot to another user account, the OR operator indicates that success in either technique enables the next step.
- AND: The attack proceeds only if all connected paths succeed, illustrating cases where multiple preconditions must be met before an action can occur.
Using operators provides clarity in complex MITRE Attack Flow examples, helping defenders understand dependencies and logical relationships between attack techniques.
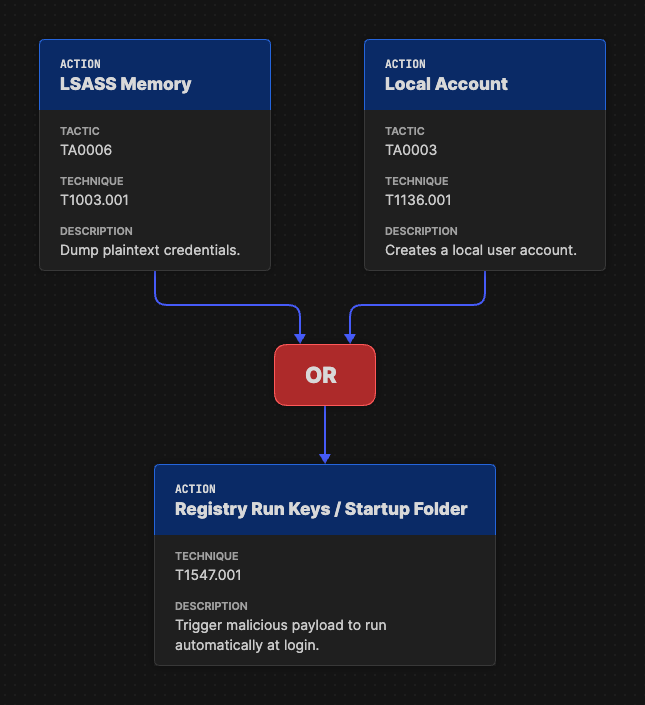
The OR operator indicates that the attacker can use either of two distinct techniques to pivot to a local user account. The example is sourced from Attack Flow v3.0.0 documentation by the MITRE Center for Threat-Informed Defense.
Asset Objects
Asset objects represent the systems, data, or entities that are affected during an attack. Each action within a flow impacts or depends on certain assets, providing crucial context about how adversary behaviors influence the environment. By linking Actions to Assets, analysts can see not just what an attacker did, but what those actions affected and why they mattered.
For example, if an attacker performs LSASS memory dumping, the corresponding asset might be a specific password hash extracted from system memory. Later, when the adversary uses that hash for credential cracking or lateral movement, the same asset remains connected to those actions, visually and logically showing the progression of the compromise.
Assets play a vital role in illustrating dependencies between attack techniques, highlighting which systems or data points are critical within an organization’s network. By mapping these relationships, asset objects turn abstract adversary actions into concrete, environment-specific insights.
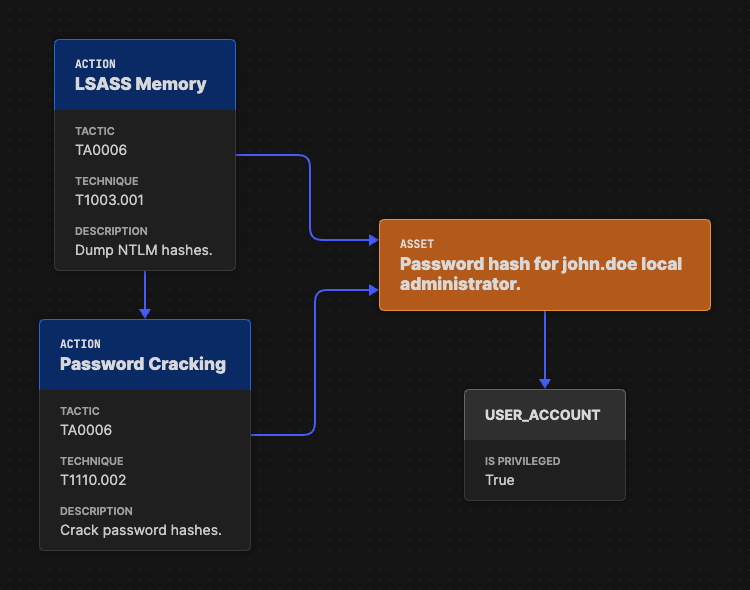
An asset defines how actions either affect the state of the environment or rely on its current state. The example is sourced from Attack Flow v3.0.0 documentation by the MITRE Center for Threat-Informed Defense.
Additional STIX Objects
Attack Flow v3.0.0 is built on the STIX (Structured Threat Information Expression) standard, which allows analysts to enrich their attack models with a wide range of contextual and technical details. While core Attack Flow objects, such as Actions, Assets, and Conditions, capture the sequence of adversary behaviors, additional STIX objects bring depth and clarity to those narratives.
STIX objects can include indicators of compromise (IOCs), such as file hashes, domains, or IP addresses, as well as entities like processes, user accounts, or malware families. For example, a process object might describe how a file discovery technique was executed during an intrusion, linking observable system activity directly to adversary behavior.
This integration makes Attack Flow highly adaptable for real-world cybersecurity operations. By embedding STIX objects, analysts can correlate behavioral intelligence with forensic artifacts, detection data, or vulnerability context—all within the same structured flow.
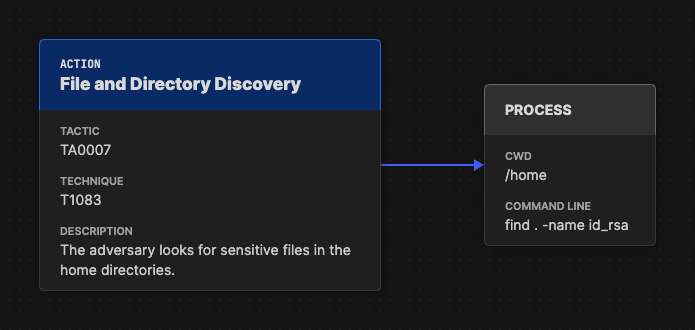
The process object captures the technical specifics of how the action was carried out. The example is sourced from Attack Flow v3.0.0 documentation by the MITRE Center for Threat-Informed Defense.
How Can Attack Flow Help Your Processes?
Attack Flow speeds up how teams turn raw incident narratives into operational decisions. By converting sequences of adversary behavior into a visual, machine-readable format, it reduces the time needed to interpret campaign behavior and highlights the logical relationships between techniques, prerequisites, and outcomes. That clarity makes it faster to extract lessons and act on them.
Empowering Detection Engineering effort, Attack Flow translates chained TTPs into precise detection logic, making it easier to write rules that look for behavior sequences rather than indicators of compromise. When flows are cross-referenced with telemetry and alerts, defenders can quickly assess coverage, spot gaps, and refine detections to close the most important blind spots.
Attack Flow also enables proactive defense. Visualizing full attack chains surfaces choke points where a single control can stop multiple paths, and it exposes weak links that attackers exploit. This shifts defensive planning from reactive patching of IOCs to strategic hardening of assets and controls that break entire classes of attacks.
Attack Flows empowers cross-functional teams by providing a common language: SOC analysts, threat hunters, red teamers, risk owners, and executives all read the same flow, but at different levels of detail. For example, an executive can see two outcome paths (cryptocurrency loss vs. large-scale data exfiltration) and make investment decisions based on business impact, while an analyst sees the exact techniques and assets to prioritize for detection and mitigation.
Attack Flow also excels for after-action learning and adversary emulation. Cyber defenders can reconstruct incidents to understand why defenses failed and what worked; this drives targeted improvements (for instance, hardening a Kubernetes dashboard or tailoring a detection rule to a specific cluster access behavior). Red teams use flows to build high-fidelity emulation plans or to replay incident sequences using the same action order and assets, even when low-level details are missing.
Pros and Cons of Using Attack Flow v3.0.0
Attack Flow v3.0.0 provides a structured, visual, and machine-readable way to model adversary behavior, offering both clear advantages and some limitations.
Advantages:
- Accelerates threat understanding by converting complex attacks into logical, actionable sequences.
- Improves detection engineering by translating chained TTPs into precise, behavior-based detection rules.
- Supports proactive defense by identifying choke points, critical assets, and coverage gaps.
- Enhances communication across teams and with executives, offering a shared, understandable view of attacks.
- Facilitates incident analysis, after-action review, and high-fidelity adversary emulation.
- Compatible with STIX and other structured intelligence standards, enabling integration with existing tools and telemetry.
- SOC Prime Platform integration allows teams to automatically generate Attack Flows from threat reports using Uncoder AI, or leverage real-world flows from the Threat Detection Marketplace, accelerating adoption and reducing manual effort.
Limitations:
- Requires familiarity with the MITRE ATT&CK framework and deep dive into Attack Flow v3.0.0 project.
- Complex Attack Flows may be difficult to interpret.
- High-fidelity modeling depends on the quality and completeness of intelligence; incomplete data can limit accuracy.
- Teams need to adopt a behavior-centric mindset, moving beyond traditional workflows, which may require training.
While Attack Flow v3.0.0 has a learning curve, the benefits outweigh the effort. By combining structured modeling, visual representation, and AI-driven tools like those provided by the SOC Prime Platform, organizations gain actionable insights that extend beyond static indicators, enhancing threat understanding, detection optimization, and cross-team collaboration for modern cybersecurity operations.
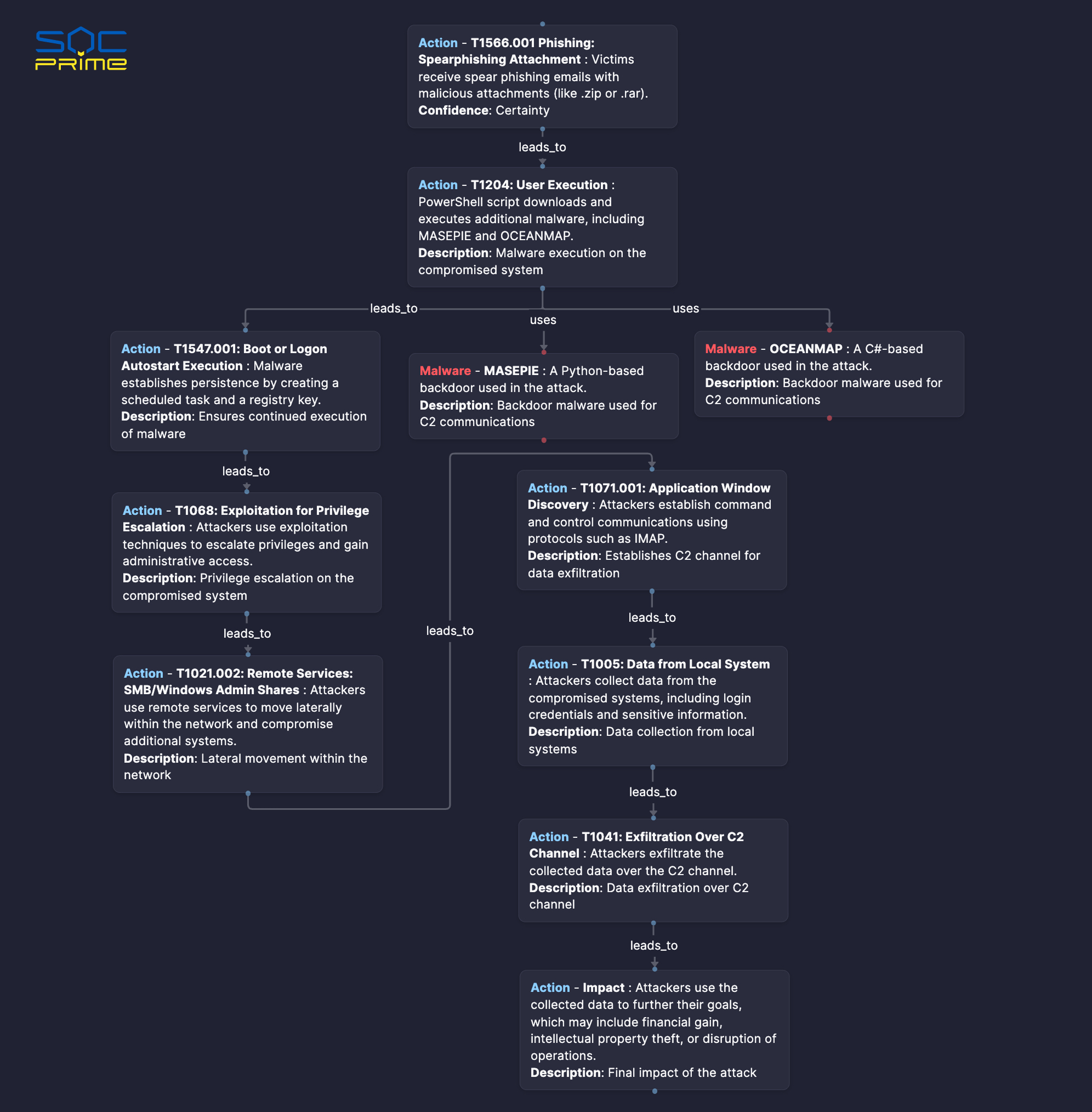
This attack flow was automatically generated in the SOC Prime Platform using Uncoder AI, based on the APT28: From initial compromise to domain controller threat creation within an hour (CERT-UA#8399) threat report.




