Purpose
The purpose of this post is to highlight the benefits of using SIGMA vs IOC based detections.
Introduction
Indicators of Compromise (IOCs) – ips, domains, hashes, filenames, etc as reported by security researchers are queried against systems and SIEMs to find intrusions. These indicators work against known attacks and have short useful lifespans and are most useful when examined retrospectively. This is because as indicators are burned in reporting, the malware and infrastructure they were written for are easily changed.
SIGMA, on the other hand, allows us to write and share rules that fall anywhere on David Bianco’s “Pyramid of Pain” and to write TTP/Behavior based detections on malware that hasn’t been written yet but use known behaviors. These SIGMA rules are platform agnostic and like IOCs their usefulness depends on what data sources are being collected. Additionally, by understanding and detecting how Threat Actors behave we can write detections that will work on malware that hasn’t been written yet by focusing on TTP/Behaviors.
Pyramid of Pain | IOC vs SIGMA
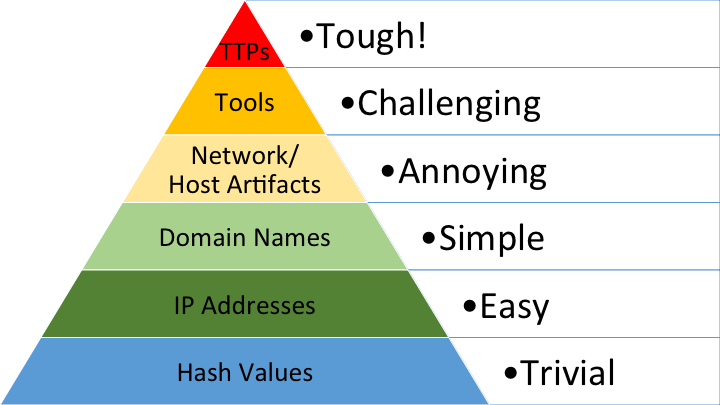
As analysts we can use the Pyramid of Pain to gauge the quality of detection content with regards to how easily an adversary can adapt to overcome them.
David Bianco’s Pyramid of Pain
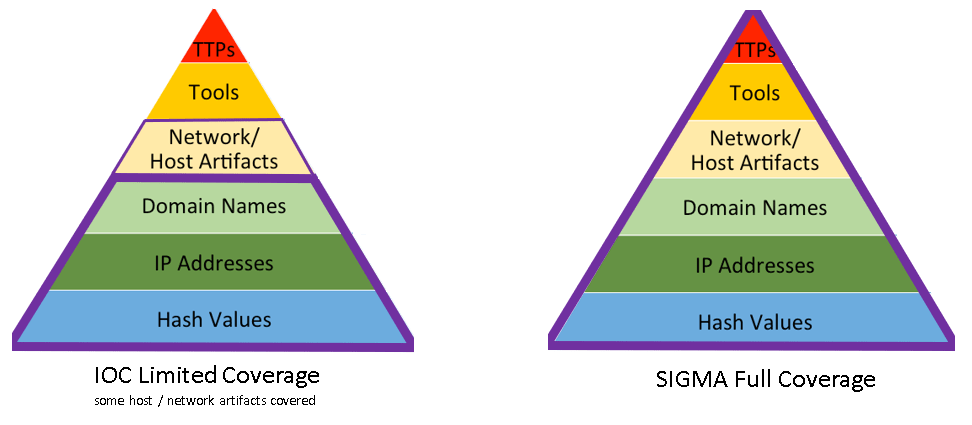
In the diagrams below, I have mapped where IOC based feeds fall vs SIGMA coverage.
IOC Coverage vs. SIGMA Coverage
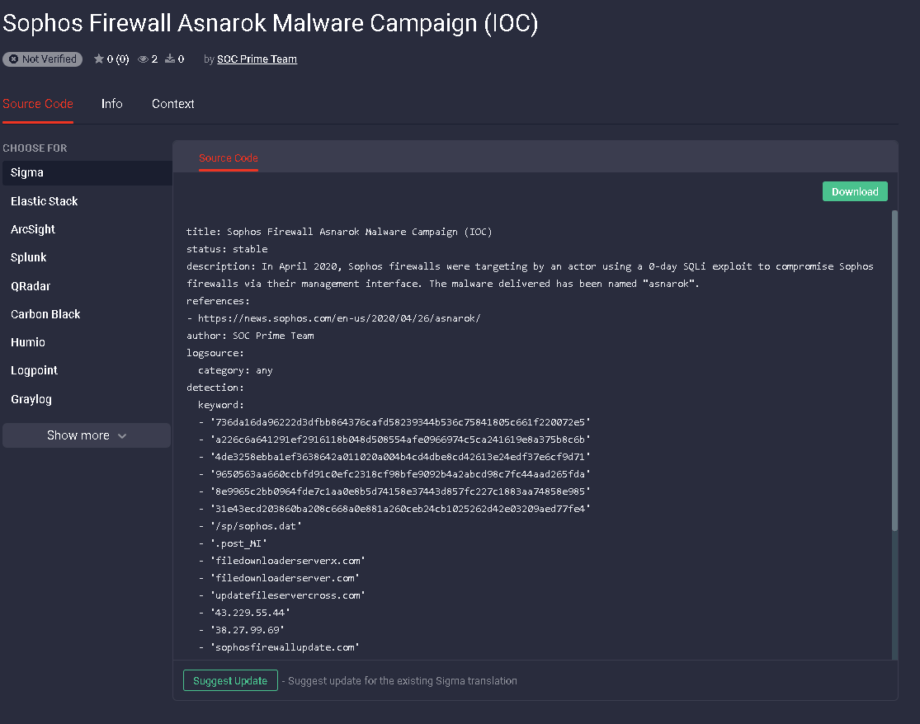
SIGMA enables defenders to write content for any datasource or backend platform (SIEM and others). This includes IOC based data such as IPs and Hashes. For instance, below is a SIGMA rule that will detect IOCs released for the April 2020 Asnarok campaign against Sophos firewalls as reported by Sophos.
IOC Rule for Asnorok Sophos Campaign (Link to rule in TDM)
However, as we will explore in the next section, SIGMA’s real power is in how it enables analysts to express TTP/Behavior based detections that can be shared and implemented as easily as IOC based data.
COVID-19 Example
As reported by many authorities, targeted attacks have continued during COVID-19 to include ransomware attacks against healthcare providers despite some criminals promising to “halt” such targeting during this critical time. Additionally, ransomware groups have used COVID-19 and related subjects (such as working from home) as phishing lures.
Ransomware attacks must be identified and remediated before encryption takes place. Typically with ransomware attacks against an organization’s infrastructure the time to encryption is just a few days at most.
Luckily, security researchers from around the world have banded together in multiple efforts to help fight COVID-19 related scams and phishing to include ransomware. Many of these are focused on revealing adversary infrastructure and either taking them down, or reporting IOCs to be used by the security community. One such praiseworthy effort that has received a lot of attention are the IOCs provided by the Cyber Threat Coalition, a group of researchers that have been releasing magnitudes of IOCs based on URLs, IPs, Domains, and hashes for free.
However, Indicators in these forms have a limited lifespan and are best put in place with more advanced logic that detects TTPs/Behaviors. At SOC Prime we provide this detection content in the form of SIGMA rules.
As an example, on April 14th 2020 Palo Alto’s Unit 42 reported a ransomware attack using COVID-19 as a lure. A technique the criminals used involved masquerading (T1036) their malware as svchost.exe (a common windows binary, used to host services). This is a common TTP/Behavior used by many threat actors, and a TTP/Behavior that we can detect using SIGMA.
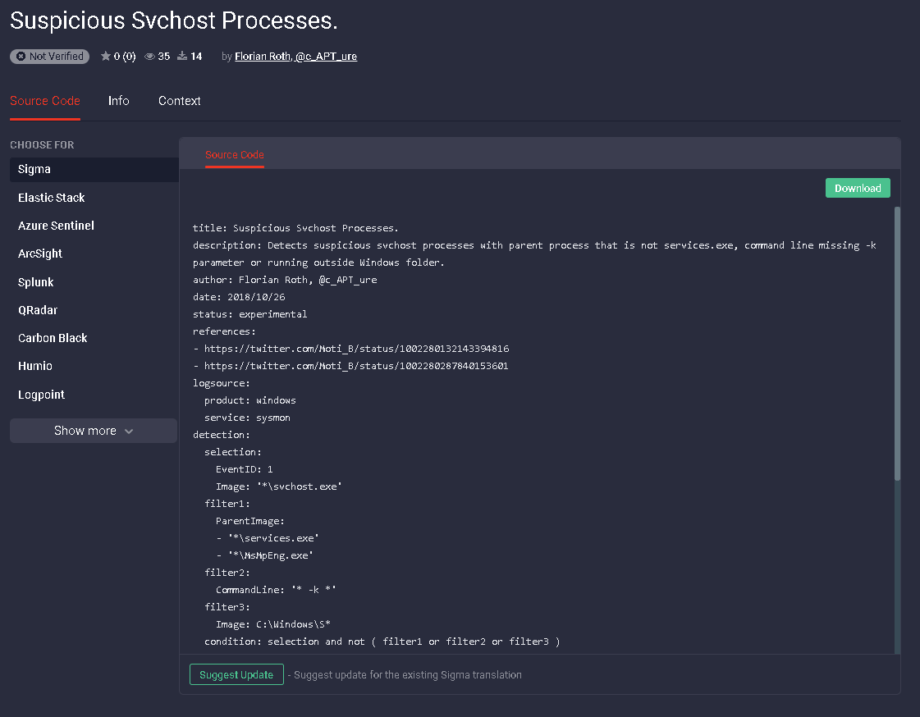
A SIGMA Rule written by Florian Roth, has been available to detect malware masquerading as svchost.exe since 2018.
SIGMA Rule For Detecting svchost masquerade in TDM (Link to rule in TDM)
So, as defenders we don’t have to wait for lists of hashes, ips, or domains to detect threats on our systems. Instead by having a feed of SIGMA rules from researchers who focus on behaviors, we can detect this kind of malware attack before it was ever conceived.
About SOC Prime and TDM
SOC Prime provides both free and exclusive SIGMA content. Community content in the form of SIGMA rules are available to anyone who uses a free account. For healthcare providers, SOC Prime is offering access to premium content for free during the COVID-19 outbreak.
Create a free account here:
https://tdm.socprime.com
Additionally, many rules are available in the public SIGMA repo available here: https://github.com/Neo23x0/sigma
META
Published – May 2020
Last Updated – May 6, 2020