AI-driven cyber-attacks are rapidly reshaping the threat landscape for businesses, introducing a new level of sophistication and risk. Cybercriminals are increasingly using artificial intelligence to power financially motivated attacks, with cyber threats like FunLocker ransomware and Koske malware as the most recent examples.
In a recent discovery, Microsoft’s Detection and Response Team (DART) identified a highly advanced backdoor that leverages the OpenAI Assistants API in a completely novel way—as a command-and-control (C2) communication channel. This method allows attackers to discreetly manage and coordinate malicious operations within infected systems, avoiding traditional security defenses. The discovery highlights how AI is being used in cybercrime, underscoring the need for businesses to remain vigilant and adapt their security strategies.
Detect SesameOp Backdoor Attacks
Organizations are entering a new era of cyber risk as attackers increasingly harness artificial intelligence to target critical business systems. Generative AI is not only creating new vulnerabilities but also enabling more sophisticated and adaptive attack methods. The Splunk State of Security 2025 Report finds that security leaders anticipate threat actors will use generative AI to make attacks more effective (32%), increase their frequency (28%), invent entirely new attack techniques (23%), and conduct detailed reconnaissance (17%). These trends underscore the urgent need for organizations to rethink cybersecurity strategies and adopt more intelligent, proactive defenses against AI-powered threats.
Register for the SOC Prime Platform to benefit from the defensive capabilities of AI and detect SesameOp backdoor attacks at the earliest stages of development. The Platform delivers timely threat intelligence and actionable detection content, backed by a complete product suite for real-time cyber defense. Click Explore Detections below to access detection rules specifically addressing SesameOp malware activity, or use the “SesameOp” tag in the Threat Detection Marketplace.
All detections are compatible with multiple SIEM, EDR, and Data Lake solutions and mapped to the MITRE ATT&CK® framework. Additionally, each rule is packed with detailed metadata, including threat intel references, attack timelines, triage recommendations, and more.
Security engineers can also leverage Uncoder AI, an IDE and co-pilot for detection engineering. With Uncoder, defenders can instantly convert IOCs into custom hunting queries, craft detection code from raw threat reports, generate Attack Flow diagrams, enable ATT&CK tags prediction, leverage AI-driven query optimization, and translate detection content across multiple platforms. For instance, security professionals can use Microsoft’s DART research details to generate an Attack Flow diagram in several clicks.
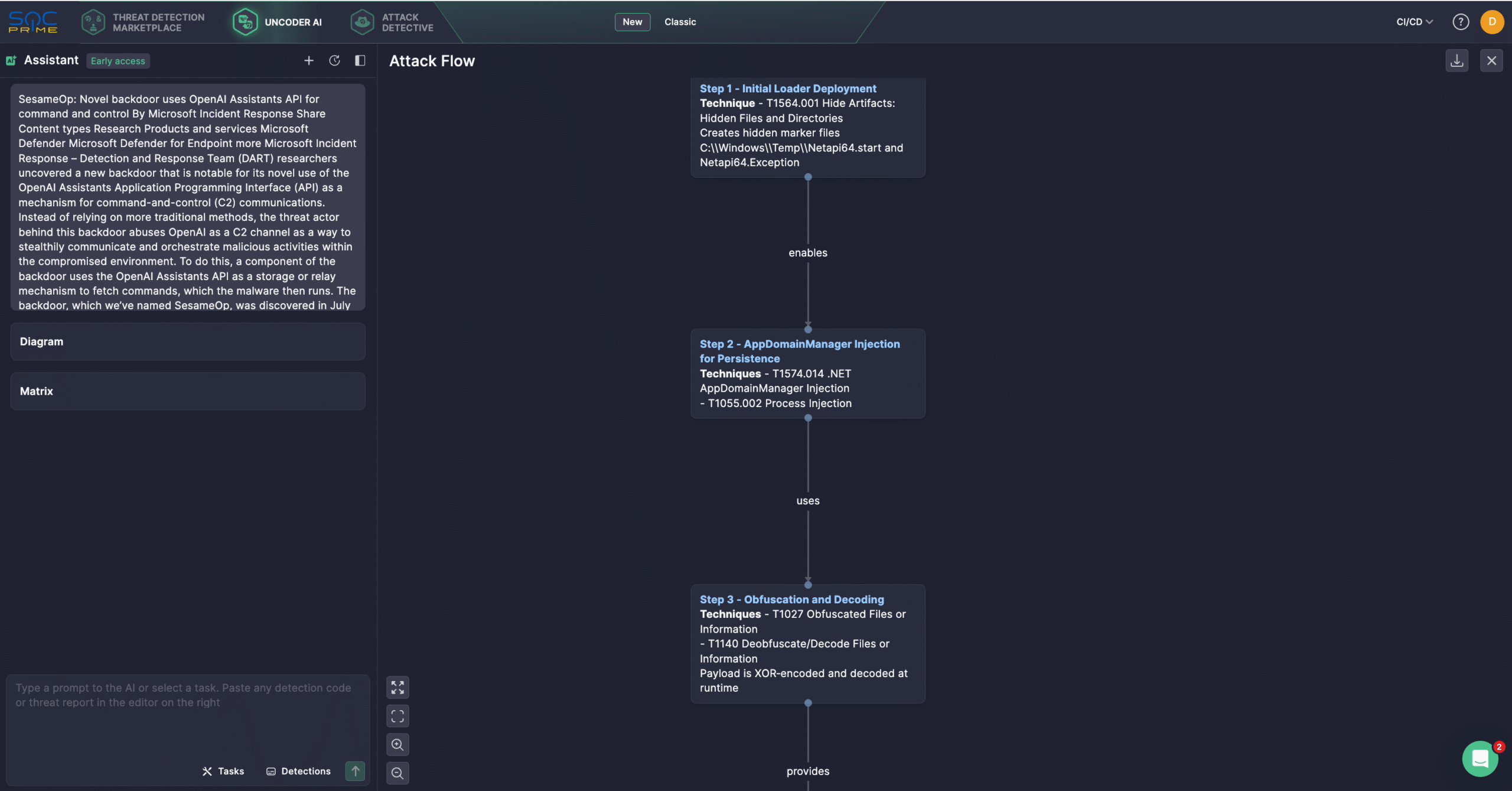
SesameOp Malware Attacks Analysis
Microsoft researchers have recently identified a novel backdoor dubbed SesameOp, distinguished by its innovative use of the OpenAI Assistants API for C2 operations. Unlike conventional methods, adversaries leveraged the OpenAI API as a covert communication channel to issue and manage commands within compromised environments. A component of the malware used the API as a relay mechanism to retrieve instructions and execute them on infected systems. The OpenAI Assistants API, used by the backdoor for C2 operations, lets developers embed AI-powered agents into applications and workflows.
Discovered in July 2025 during Microsoft’s investigation of a long-term intrusion, SesameOp was found within a network where attackers had maintained persistence for several months. The analysis revealed a tricky structure of internal web shells linked to persistent malicious processes embedded in compromised Microsoft Visual Studio utilities via .NET AppDomainManager injection, a known defense evasion tactic.
Further hunting for similarly altered Visual Studio utilities uncovered additional components designed to support communication with the internal web shell network. One such component was identified as the new SesameOp malware. SesameOp is a custom backdoor built for long-term persistence, allowing attackers to stealthily control compromised systems, suggesting the operation’s main objective was prolonged espionage.
The infection chain includes a loader (Netapi64.dll) and a .NET backdoor (OpenAIAgent.Netapi64) that uses the OpenAI Assistants API as its C2 channel. The DLL, heavily obfuscated with Eazfuscator.NET, is built for stealth, persistence, and encrypted communication. At runtime, Netapi64.dll is injected into the host process via .NET AppDomainManager injection, triggered by a specially crafted a .config file bundled with the host executable.
OpenAIAgent.Netapi64 houses the backdoor’s core functionality. Despite its name, it does not use OpenAI SDKs or run models locally; rather, it polls the OpenAI Assistants API to retrieve compressed, encrypted commands, decrypts and executes them on the host, and then returns the results as API messages. Compression and encryption are used to keep both incoming payloads and outgoing responses under the radar.
Malicious messages use three description types: SLEEP (pause the thread), Payload (extract instructions from the message and run them in a separate thread), and Result (return execution output to OpenAI with the description set to “Result”). Although the identities of the adversaries linked to the offensive campaign remain unknown, the case highlights the continued abuse of legitimate services to hide malicious activity. To raise awareness, Microsoft shared its findings with OpenAI, which disabled the suspected API key and account. OpenAI plans to deprecate this API in August 2026, replacing it with the new Responses API.
As potential mitigation steps to preempt SesameOp backdoor attacks, the vendor recommends regularly auditing firewalls and web server logs, securing all Internet-facing systems, and using endpoint and network protections to block C2 communications. It’s essential to ensure that tamper protection and real-time protection are enabled in Microsoft Defender, run endpoint detection in block mode, and configure automated investigation and remediation to quickly address the potential threat. Additionally, teams should enable cloud-delivered protection and block potentially unwanted applications to reduce the risk posed by evolving attacks.The growing use of cyber-attacks employing innovative methods and AI technology demands heightened vigilance from defenders to stay ahead of adversaries.
The emergence of SesameOp, a backdoor that uniquely exploits the OpenAI API as a C2 channel to covertly coordinate malicious activity, reflects the trend of increasingly sophisticated tactics employed by threat actors. By relying on AI-Native Detection Intelligence Platform for SOC teams, which provides real-time, cross-platform detection intelligence to anticipate, detect, validate, and respond to cyber threats faster and more effectively, global organizations can build a resilient cybersecurity ecosystem and preempt attacks that matter most.




