In May 2022, Cuba ransomware maintainers resurfaced marking their loud entrance into the cyber threat arena by leveraging a novel custom remote access Trojan called ROMCOM (or RomCom) RAT.
On October 22, 2010, CERT-UA warned the global cyber defender community of the ongoing phishing campaigns targeting Ukrainian officials with the email sender masquerading as the General Staff of the Armed Forces of Ukraine. The phishing emails contain a link to an external web resource offering to download a lure attachment, which triggers an infection chain and deploys the malicious RomCom backdoor on the compromised systems. According to the specific behavior patterns, which include the use of common adversary techniques and tools like the above-mentioned RomCom backdoor, the malicious activity can be attributed to the Tropical Scorpius aka UNC2596 group, also known to be behind Cuba Ransomware distribution.
Tropical Scorpius aka UNC2596/UAC-0132 Malicious Activity: Analysis of Cyber Attacks Covered by CERT-UA#5509 Alert
Starting from May 2022, a wave of new adversary campaigns distributing Cuba ransomware caused a stir in the cyber threat arena with targeted attacks linked to the Tropical Scorpius hacking collective (according to the Unit42 naming scheme). In these attacks, the infamous Cuba ransomware maintainers leveraged novel TTPs and more advanced adversary tools, including a new malware family dubbed ROMCOM ((or RomCom) RAT and weaponized the ZeroLogon tool to exploit the CVE-2020-1472 vulnerability.
Cuba ransomware maintainers also identified as UNC2596 by Mandiant have been in the spotlight since 2019. In 2021, the group reemerged spreading SystemBC malware in their adversary campaigns, along with other infamous RaaS operators, including DarkSide and Ryuk.
CERT-UA team has recently issued an alert CERT-UA#5509 warning of ongoing cyber attacks spreading phishing emails targeted at Ukrainian government agencies. The infection chain is triggered by following a link to an external webpage that contains a malicious attachment. The webpage includes a notification that lures compromised uses into upgrading their PDF Reader software. By clicking the button with the fake software update, the system downloads an executable file, which leads to decoding and launching the malicious “rmtpak.dll” file identified as RomCom backdoor.
According to the analysis of adversary behavior patters, the malicious activity can attributed to the Cuba ransomware operators tracked as Tropical Scorpius aka UNC2596 or UAC-0132 (by CERT-UA).
Detecting RomCom Backdoor Spread by UAC-0132 and Linked to Cuba Ransomware Operators
The ongoing attacks by Tropical Scorpius aka UNC2596 targeting Ukrainian state bodies illustrate that advesrary campaings launched by this infamous hacking collective still pose a significant threat. Coupled with a wealth of advanced tools and sophisticated adversary techniques, the group’s malicious activity requires ultra-responsiveness from cyber defenders. To help organizations timely identify the malicious presence of RomCom backdoor used in the latest attacks of threat actors who are also behind Cuba ransomware distribution, SOC Prime Platform has released a set of relevant Sigma rules. All detection content is available for streamlined search by two custom tags based on the group’s identifier “UAC-0132” and “CERT-UA#5509” according to the corresponding CERT-UA alert.
Click the Explore Detections button to obtain Sigma rules for proactive detection of the UAC-0132 malicious activity. All detection algorithms are aligned with MITRE ATT&CK® and are enriched with comprehensive cyber threat context, icluding relevant CTI links, mitgations, executable binaries, and more actionable metadata. Along with Sigma rules, teams can instantly reach rule translations to the industry-leading SIEM, EDR, and XDR solutions.
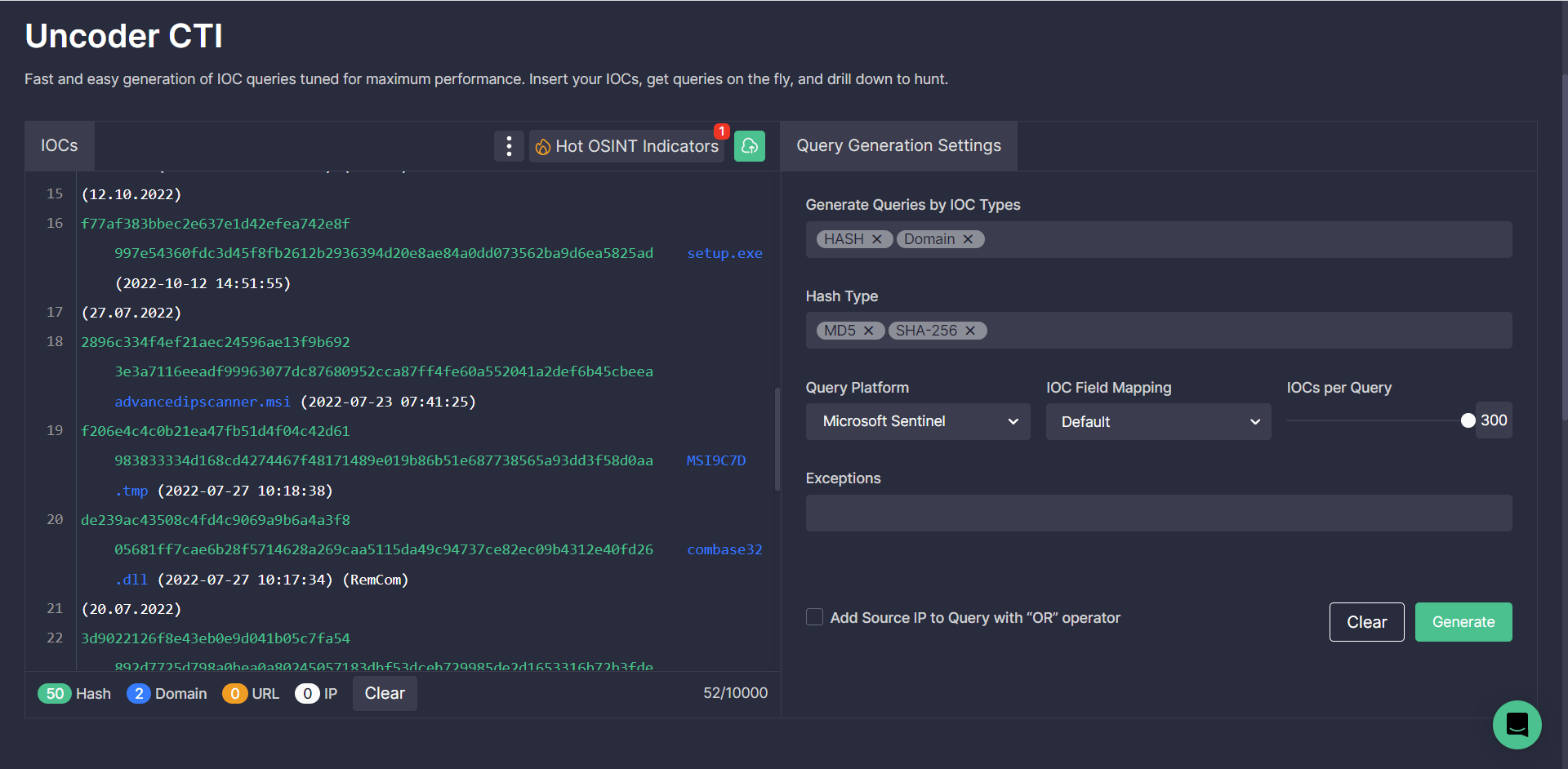
In addition, cybersecurity professionals can search for IOCs associated with the malicious activity of the UAC-0132 threat actors covered in the CERT-UA#5509 alert. By leveraging Uncoder CTI, teams can instantly generate custom IOC queries ready to run in the selected SIEM or XDR environment.
MITRE ATT&CK® Context
To delve into the MITRE ATT&CK context related to the malicious activity of the Tropical Scorpius aka UNC2596 threat actors (UAC-0132) targeting Ukrainian state bodies with the RomCom backdoor, check the table below. All Sigma rules within the above-mentioned detection stack are aligned with MITRE ATT&CK® framework addressing the corresponding tactics and techniques:MITRE ATT&CK® Context




