Remcos Trojan (Remote Control and Surveillance) is frequently delivered by threat actors leveraging phishing attack vectors. The malware currently reemerges in the cyber threat arena to target Ukrainian government entities.
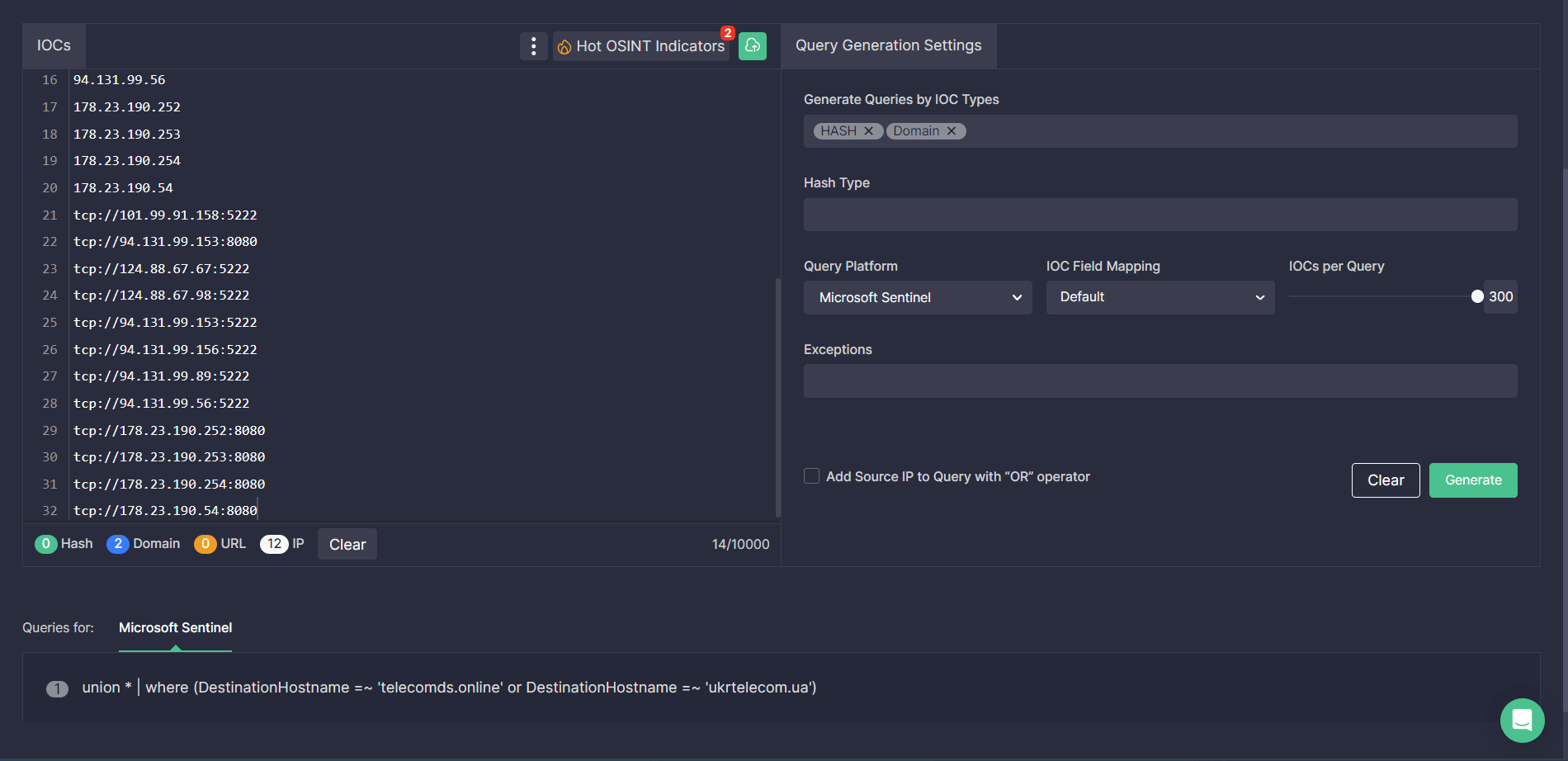
On February 6, 2023, cybersecurity researchers released a new CERT-UA#5926 alert detailing the mass email distribution impersonating the Ukrtelecom JSC aimed to spread Remcos malware on compromised systems. Attackers leveraged a malicious RAR attachment in phishing emails targeting Ukrainian state bodies. According to the investigation, the adversary activity is attributed to the hacking collective tracked as UAC-0050.
Malicious Activity by UAC-0050 Spreading Remcos Malware: Attack Analysis
Remcos is a remote access software developed by BreakingSecurity. Once installed, the tool opens a backdoor on the compromised system, enabling full access to the remote user. Since 2020, attackers have been actively leveraging Remcos RAT in phishing attacks exploiting the COVID-19 topic. The malware operators take advantage of multiple TTPs in their adversary campaigns, using Remcos to spy on its victims, for credential theft, data exfiltration, and command execution.
The latest CERT-UA#5926 alert warns cyber defenders of the newly observed malicious activity leveraging Remcos malware. In these attacks, threat actors exploit the phishing attack vector to spread emails masquerading the sender as the Ukrtelecom JSC. Adversaries aim to lure victims into opening emails with the demand letter subject and containing a RAR archive attachment impersonating the details of the required financial payment. The lure archive contains a text file with the personal access code and another password-protected RAR file. The latter includes an executable file that installs the remote administration Remcos malware on the victim’s computer.
CERT-UA researchers link the malicious activity to the UAC-0050 hacking collective, which has been in the spotlight since at least 2020. According to the investigation, threat actors launched their previous attacks leveraging another remote administration software known as RemoteUtilities. Based on the observed adversary behavior patterns and the malware offensive capabilities, the ongoing attacks targeting Ukrainian state bodies are highly likely linked to cyberespionage operations.
Detecting Cyber Attacks by UAC-0050 Against Ukrainian State Bodies Covered in the CERT-UA#5926 Alert
With the ever-growing volumes of phishing cyber attacks, defenders are striving to strengthen their capabilities to timely identify the infection. SOC Prime enables organizations to stay ahead of adversaries and proactively defend against cyber attacks of any scale leveraging multiple malware strains. SOC Prime’s Detection as Code Platform curates a set of Sigma rules for Remcos malware detection used in the ongoing phishing attacks and attributed to the adversary activity of the UAC-0050 hacking group. For a streamlined content search, all detection algorithms are filtered by the corresponding custom tags (“UAC-0050” or “CERT-UA#5926”) based on the group and CERT-UA alert IDs.
Click the Explore Detections button below to immediately reach the dedicated Sigma rules covered in the CERT-UA#5926 alert. All detections are ready-to-deploy to the industry-leading SIEM, EDR, BDP, and XDR solutions and are enriched with in-depth cyber threat context, like MITRE ATT&CK® references, CTI links, executable binaries along with operational metadata.
In addition, security engineers can streamline their search for indicators of compromise associated with the malicious activity of UAC-0050 by leveraging the Uncoder CTI tool. Just paste the file, host, or network IOCs provided by CERT-UA into the UI and instantly generate custom hunting queries ready to search for Remcos-related threats in your selected environment.
MITRE ATT&CK Context
To dive into the comprehensive context behind the adversary campaign of the UAC-0050 group covered in the latest CERT-UA alert, all above-mentioned Sigma rules are tagged with ATT&CK v12 addressing the corresponding tactics and techniques:
Browse SOC Prime’s Sigma Rules Search Engine to reach the entire detection stack against Remcos malware and learn about current & emerging threats faster than ever before, prioritize in minutes, and deploy your detection code on the fly.




