The nefarious cyber-espionage hacking collective tracked as EarthKapre or RedCurl APT has resurfaced to target legal sector organizations using Indeed-themed phishing. In the latest attack, adversaries notorious for highly sophisticated offensive capabilities applied reconnaissance commands and tools, exfiltrated data, and deployed the EarthKapre/RedCurl loader.
Detect RedCurl/EarthKapre APT Attacks
In 2024, state-sponsored cyber groups from China, North Korea, Iran, and russia significantly enhanced their offensive capabilities, showcasing increased sophistication and adaptability. These threat actors remained among the most active in the cyber domain, employing advanced techniques to further their geopolitical agendas. Cyber espionage emerged as a primary focus, with campaigns growing more targeted and covert. A notable example is the latest operation by RedCurl (aka EarthKapre APT), which demonstrates a highly sophisticated approach to infiltrating organizations within the legal sector.
To outscale emerging threats and stay on top of the potential RedCurl APT attacks, SOC Prime Platform offers a set of curated Sigma rules addressing TTPs leveraged in the latest offensive operation. Just hit the Explore Detections button below and immediately drill down to the relevant detection stack for RedCurl attacks detection.
The rules are compatible with multiple SIEM, EDR, and Data Lake solutions and mapped to MITRE ATT&CK® to streamline threat investigation. Detections are also enriched with extensive metadata, including CTI links, attack timelines, triage recommendations, and more.
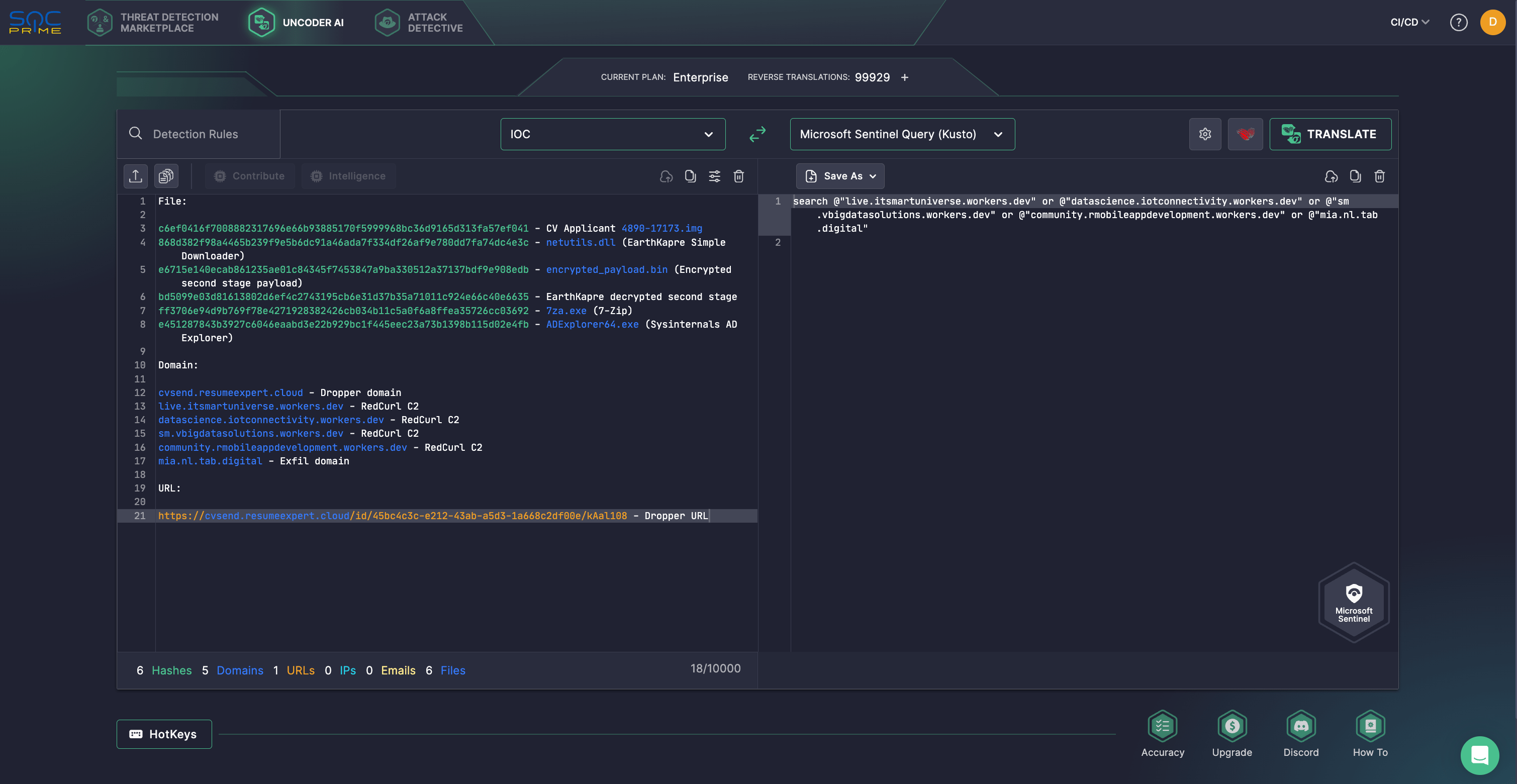
Additionally, security professionals can hunt for IOCs from eSentire’s Threat Response Unit analysis of the latest RedCurl campaign. With Uncoder AI, security experts can effortlessly parse these IOCs and transform them into custom queries tailored for the chosen SIEM or EDR platform. Previously exclusive to corporate clients, Uncoder AI is now available to individual researchers, providing full access to its powerful capabilities. Learn more here.
Cyber defenders seeking more detection content on TTPs used in APT attacks can explore the Threat Detection Marketplace using the “APT” tag. This provides access to a comprehensive collection of rules and queries designed to detect malicious activities associated with state-sponsored groups.
RedCurl/EarthKapre APT Attack Analysis
In January 2025, eSentire’s Threat Response Unit (TRU) team spotted EarthKapre (aka RedCurl) APT using a legitimate Adobe executable, ADNotificationManager.exe, to drop its malicious loader. The group has been active in cyber threats since 2018, with a broad geographical reach spanning Ukraine, the U.S., the UK, and Canada, and targeting various industries. In the latest offensive campaign, the cyber espionage group, known for targeting primarily private-sector firms, has set its eyes on the organizations in the legal sector exploiting job-themed phishing. EarthKapre employed SysInternals AD Explorer for reconnaissance, 7-Zip to archive data with a password, and PowerShell PUT requests to exfiltrate it to a cloud storage provider.
The infection chain starts with a spam email containing a malicious PDF disguised as a CV or cover letter. The PDF includes a link to a ZIP archive with a mountable ISO (IMG) file. When opened, the IMG file is mounted to an external drive, showing a single file, “CV Applicant *.scr,” as a signed Adobe executable. Running the letter drops the EarthKapre loader (netutils.dll) on the compromised system, completing the attack chain.
After extracting the zip archive and mounting the IMG file, only a file explorer window is visible with a single available *.scr file. When the victim opens the latter, the RedCurl/EarthKapre malware is sideloaded, along with legitimate C runtime libraries.
The initial attack stage aims to download and execute the next phase. RedCurl/EarthKapre makes use of a string decryption function that leverages various APIs from bcrypt.dll. At the subsequent attack stage, the same string decryption method is used, but the AES decryption key is derived differently. The first part is obtained through XOR decryption, then combined with a GUID passed during execution, which makes it harder for sandboxes to trigger this stage correctly. After decoding from base64 and applying the XOR decryption to the HTTP request payload, adversaries obtain the victim’s username, computer name, and a list of files/directories from the affected victim’s system.
RedCurl uses a batch file at the final attack stage to automate system info collection and data archiving for exfiltration. It executes commands to gather user account details, system data, disk information, and more. The adversary C2 infrastructure is hosted on Cloudflare using Cloudflare Workers.
Organizations should consider mitigating the risks of RedCurl/EarthKapre APT attacks by implementing Group Policy measures to prevent the automatic mounting of ISO/IMG files, deploying EDR solutions across all workstations and servers, and maintaining continuous cyber vigilance. Progressive organizations can also minimize the risks of emerging threats of any size, scope, or sophistication, including highly evolving APT attacks, using SOC Prime’s enterprise-ready complete product suite that equips security teams with future-proof technologies to adopt a resilient cybersecurity strategy while driving the maximum value of security investments.




