SOC Prime’s Detection as Code platform for collaborative cyber defense, threat hunting, and discovery continuously evolves to empower the global community with more accessible and efficient cyber defense capabilities. Striving to unlock threat hunting to a wider cybersecurity audience, SOC Prime introduced Quick Hunt, a new cutting-edge module, enabling both newcomers and seasoned experts alike to search for the latest threats in their SIEM and EDR environments in three simple steps.
One-Time Configuration to Enable One-Click Hunting Experience
The initial use of the SOC Prime’s module requires configuring a hunting environment in the selected SIEM or EDR. By completing a one-time setup, Quick Hunt users can then single-click to hunt in the pre-configured environment on the available log data without integration hurdles and parsing issues.
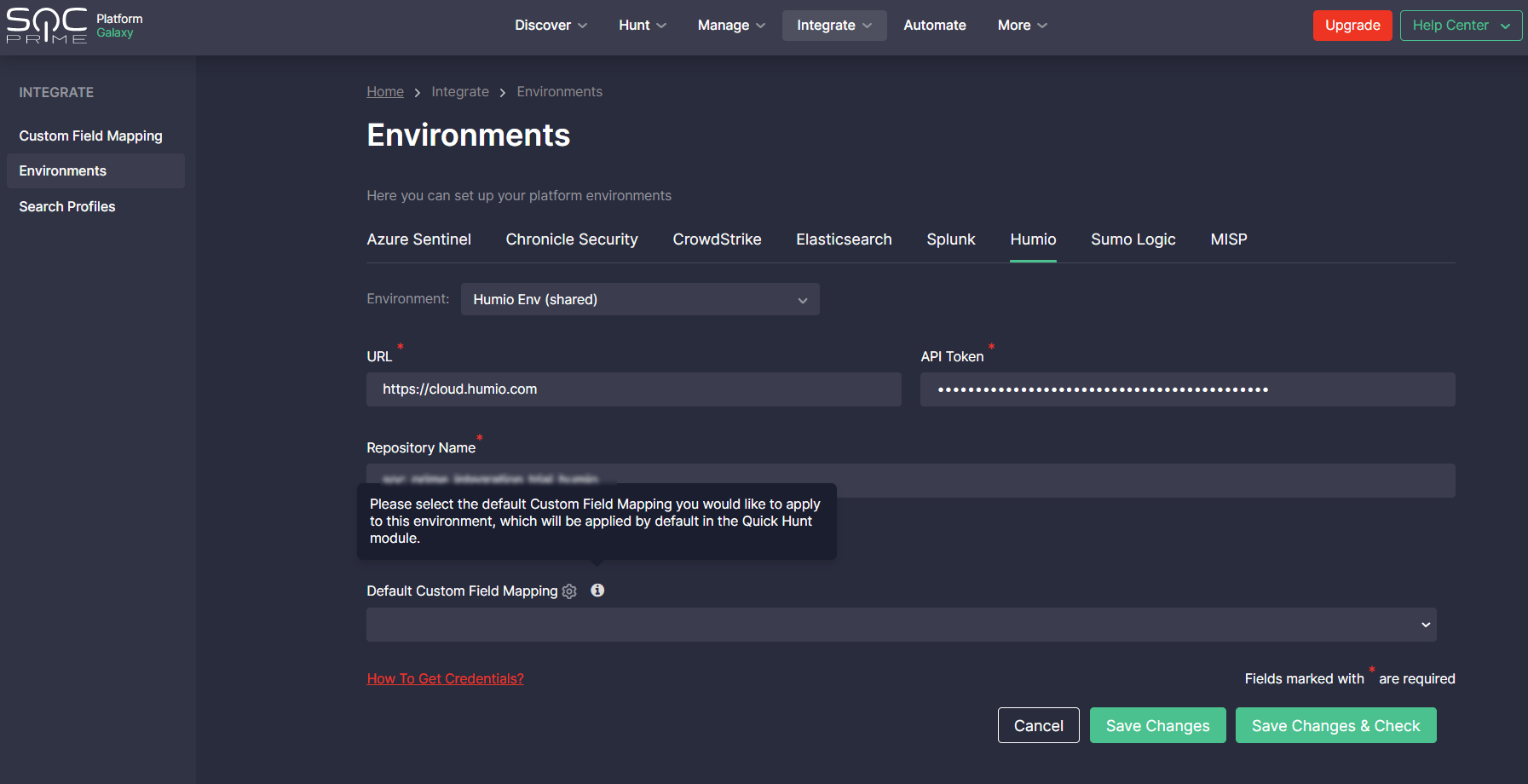
For initial configuration, go to Integrate > Environments in the SOC Prime’s Detection as Code platform, select the platform tab and environment, and then fill in the corresponding URL that will be used to drill down to hunt along with other required fields.
To overcome data schema complexity challenges when hunting on custom log data, apply the Default Custom Field Mapping profile or configure a new one for the selected environment.
Searching for the Most Relevant Threats in Three Simple Steps
Quick Hunt makes threat investigation more efficient than ever following three simple steps:
- Getting informed on the most anticipated threats
- Performing a hunt in the selected SIEM or XDR
- Sharing feedback with your peers
Getting Informed on Threats Most Relevant to Your Business
Powered by the Threat Detection Marketplace and the SOC Prime’s crowdsourcing initiative, Quick Hunt is based on 130,000+ detections aligned with the latest MITRE ATT&CK® framework version 10 with the amount of content growing exponentially year over year, addressing IT threats, edge, cloud, SaaS, IaaS, and PaaS use cases.
Backed by the feedback of over 20,000 cybersecurity professionals and SOC Prime’s recommendation engine, security teams can instantly identify threats that are most relevant to their business needs and the platform in use.
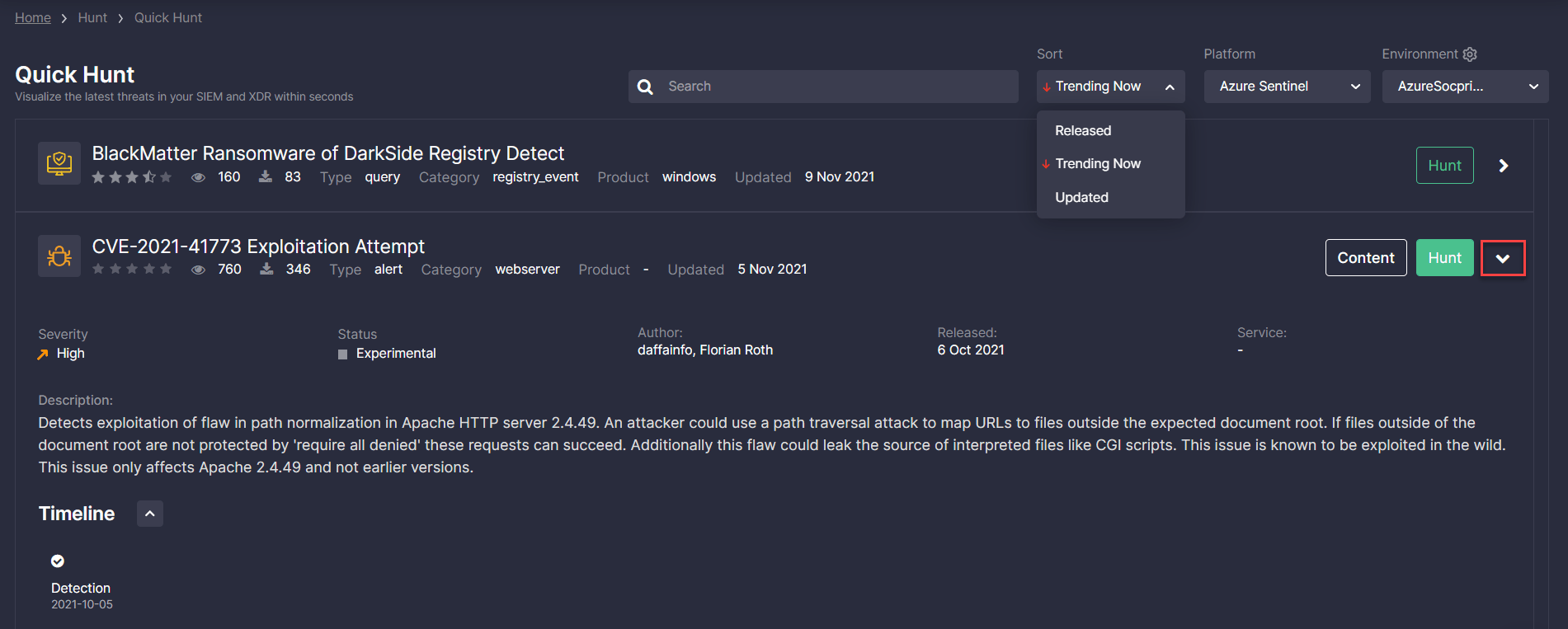
Note: To see the list of queries tailored to the specific platform and environment, select the SIEM or EDR platform on the list and then choose the pre-configured environment matching your security needs.
Security professionals can also sort content by the recently released or last updated detections.
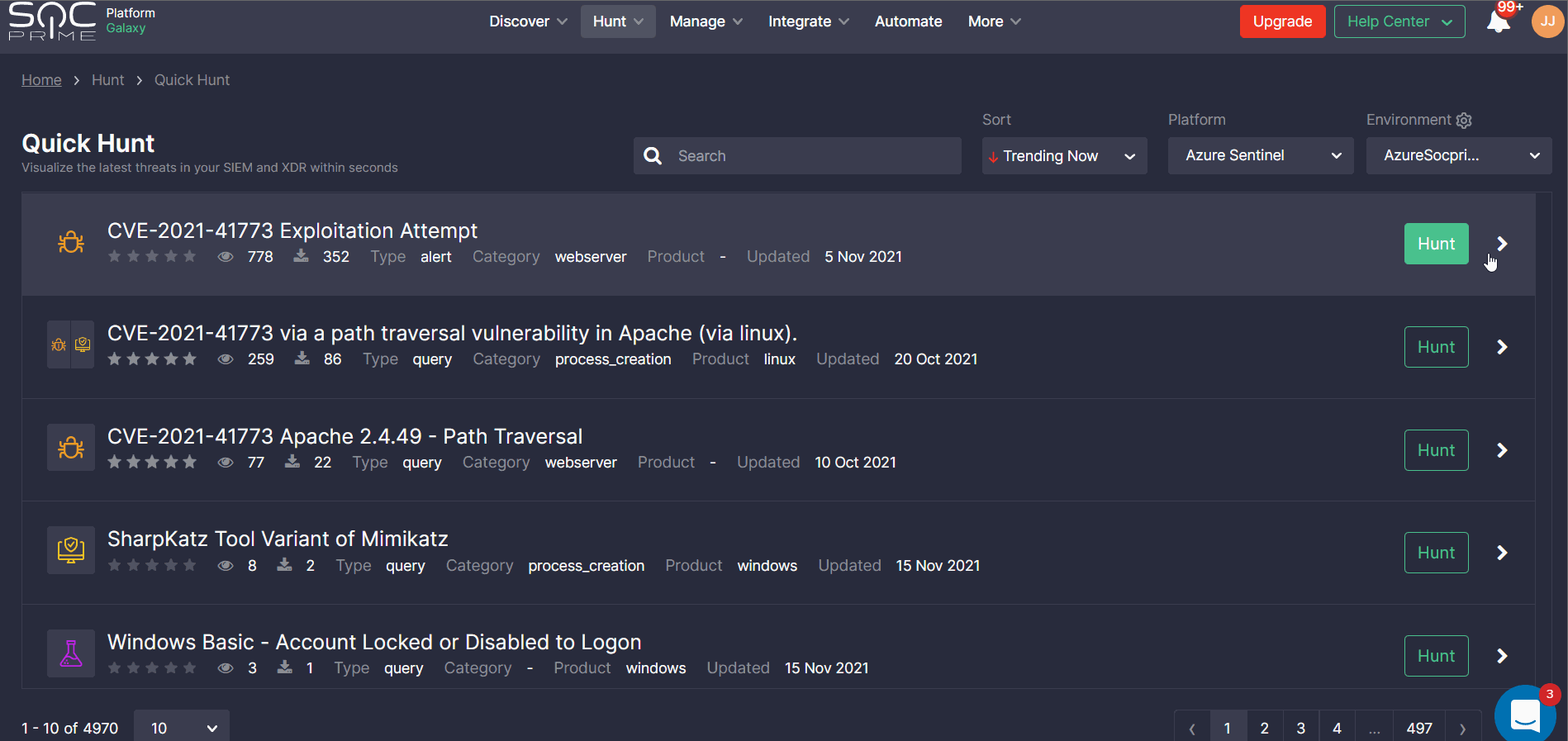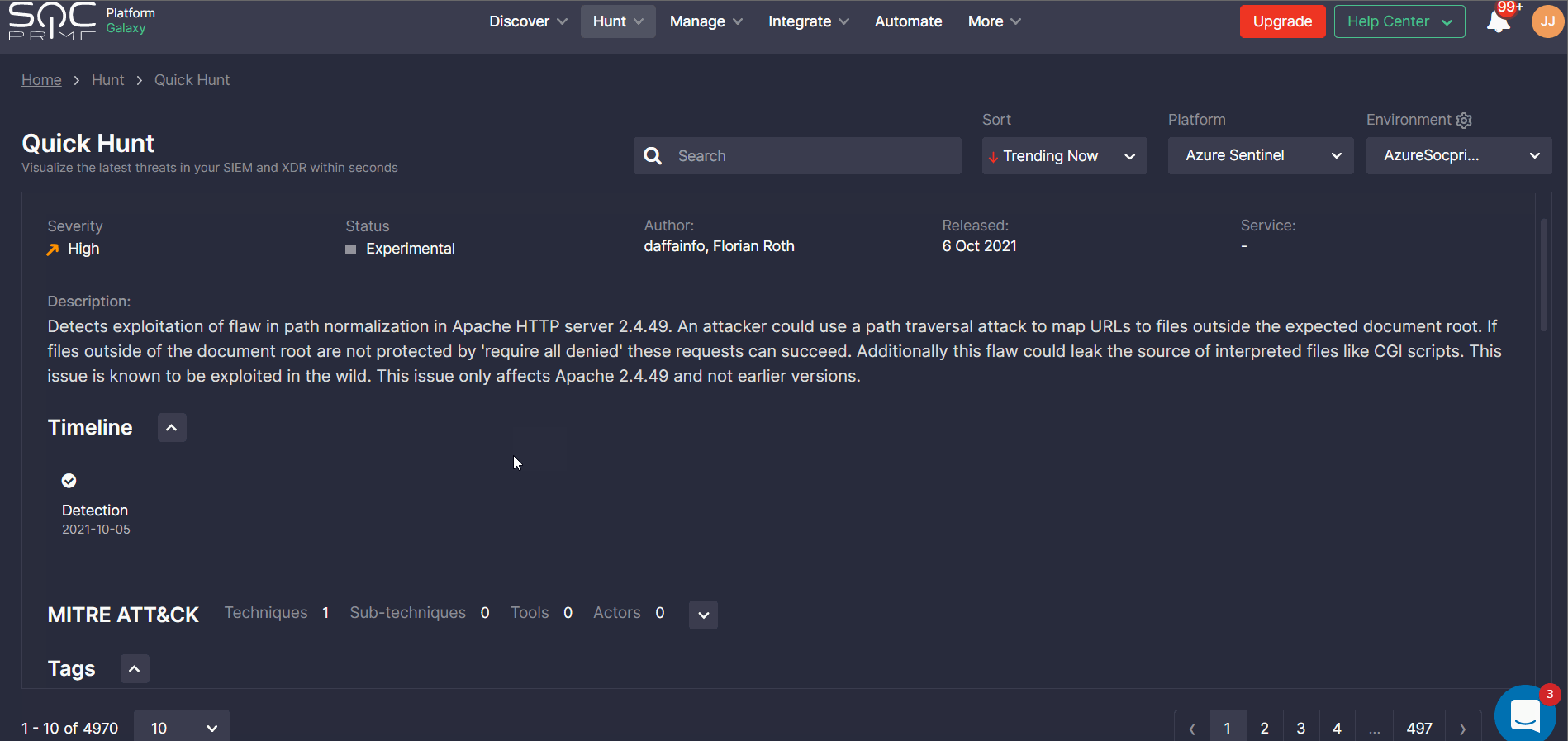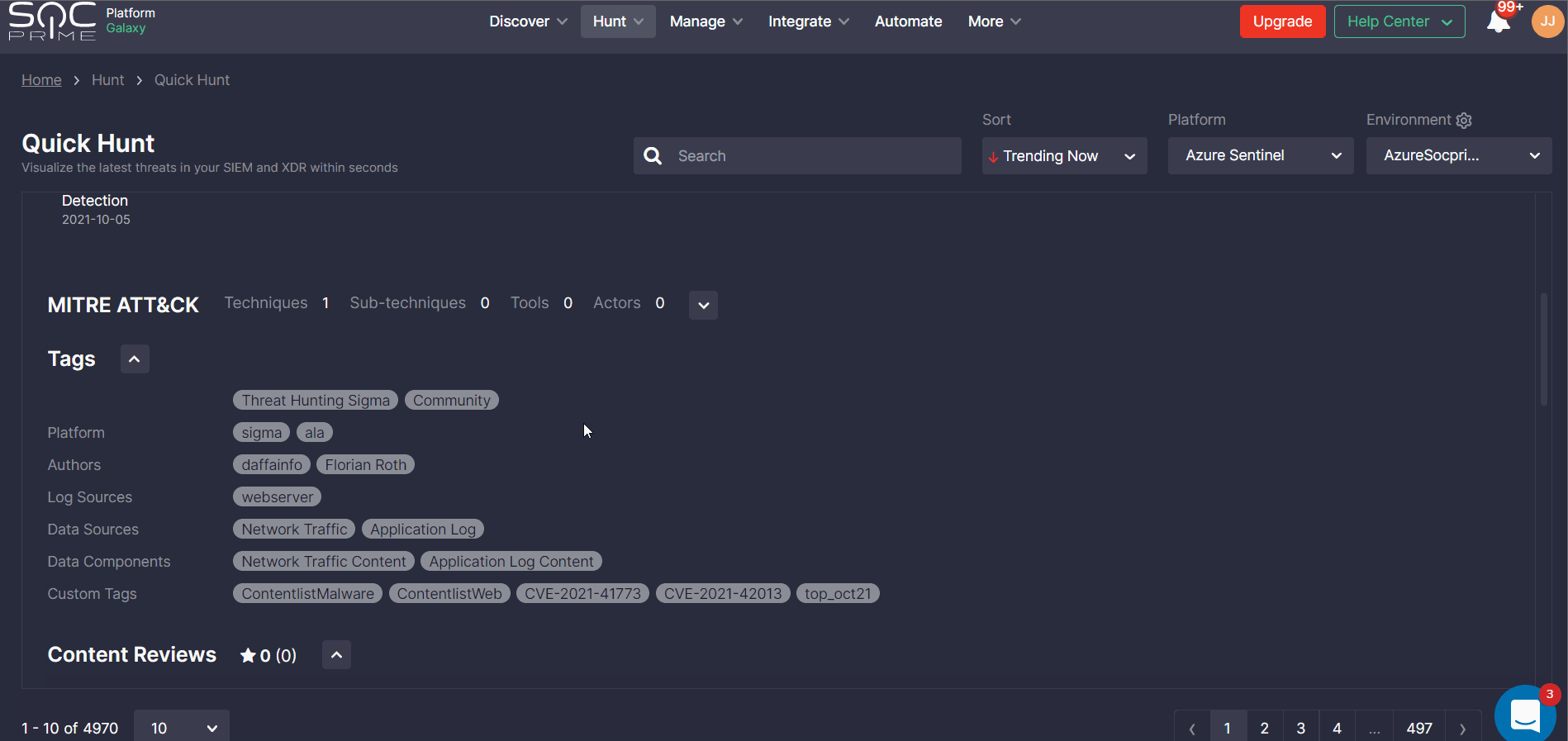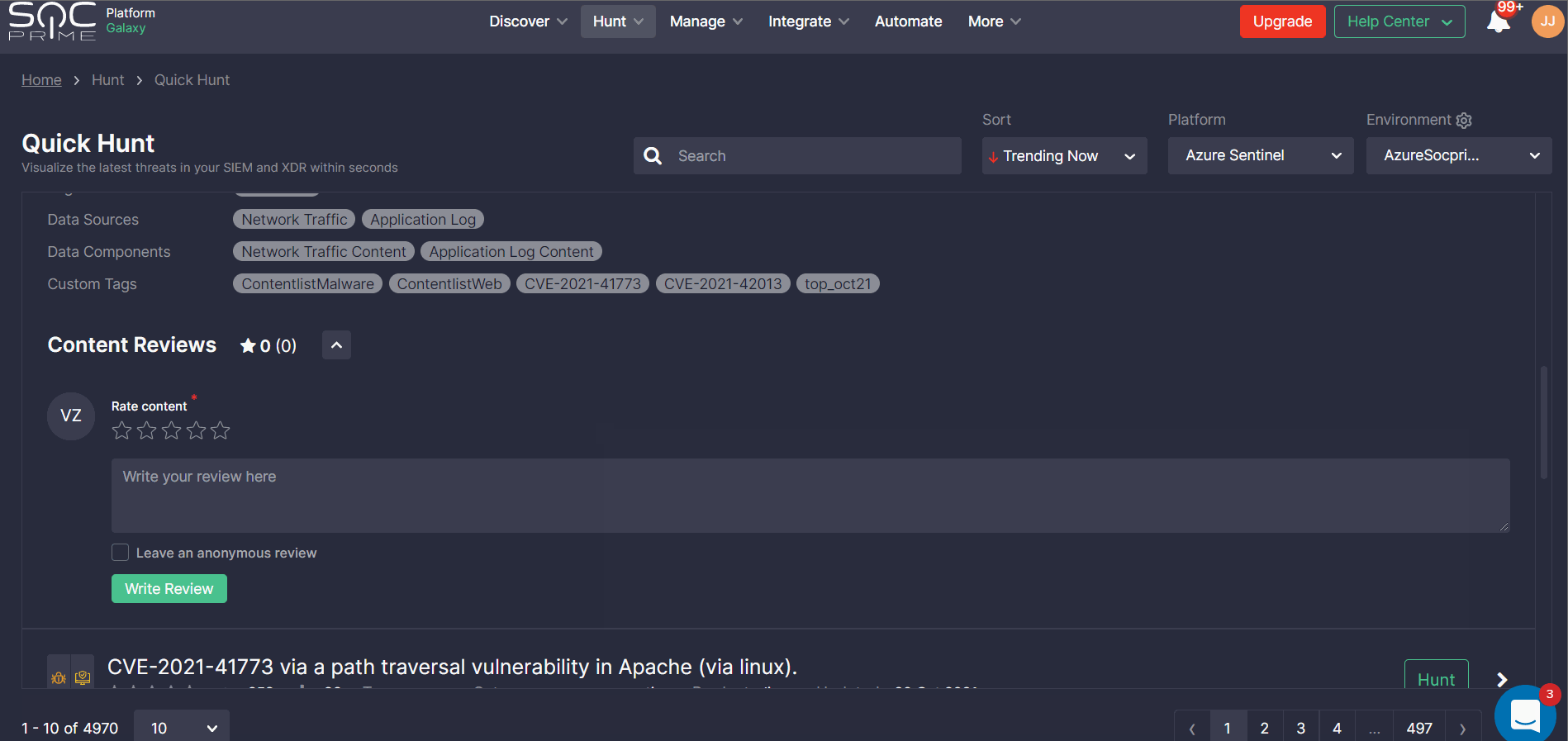
To delve into cyber threat intelligence linked to the specific content item, security teams can click an arrow icon next to the Hunt button and explore the rule severity, media mentions, CVE and ATT&CK links, log source types, and more content details.
Once you are ready to hunt, move to step 2.
Hunting in Your SIEM or XDR with a Single Click
To run a hunting session using a selected query, click the Hunt button. The system will instantly redirect you to the pre-configured SIEM or EDR environment getting a query pasted into your browser address bar. SOC Prime doesn’t store any hunting data, and authentication is performed locally to ensure data privacy protection. All the queries are launched during the current browser session and are not sent to the Quick Hunt server side.
Leaving Feedback on Your Hunt
Once the query produces results, Quick Hunt users can return to SOC Prime’s Detection as Code platform to share feedback with the global community and their peers. Security practitioners are prompted to rate their hunting experience by the number of hits and after leaving their own feedback, they can see input from other users.
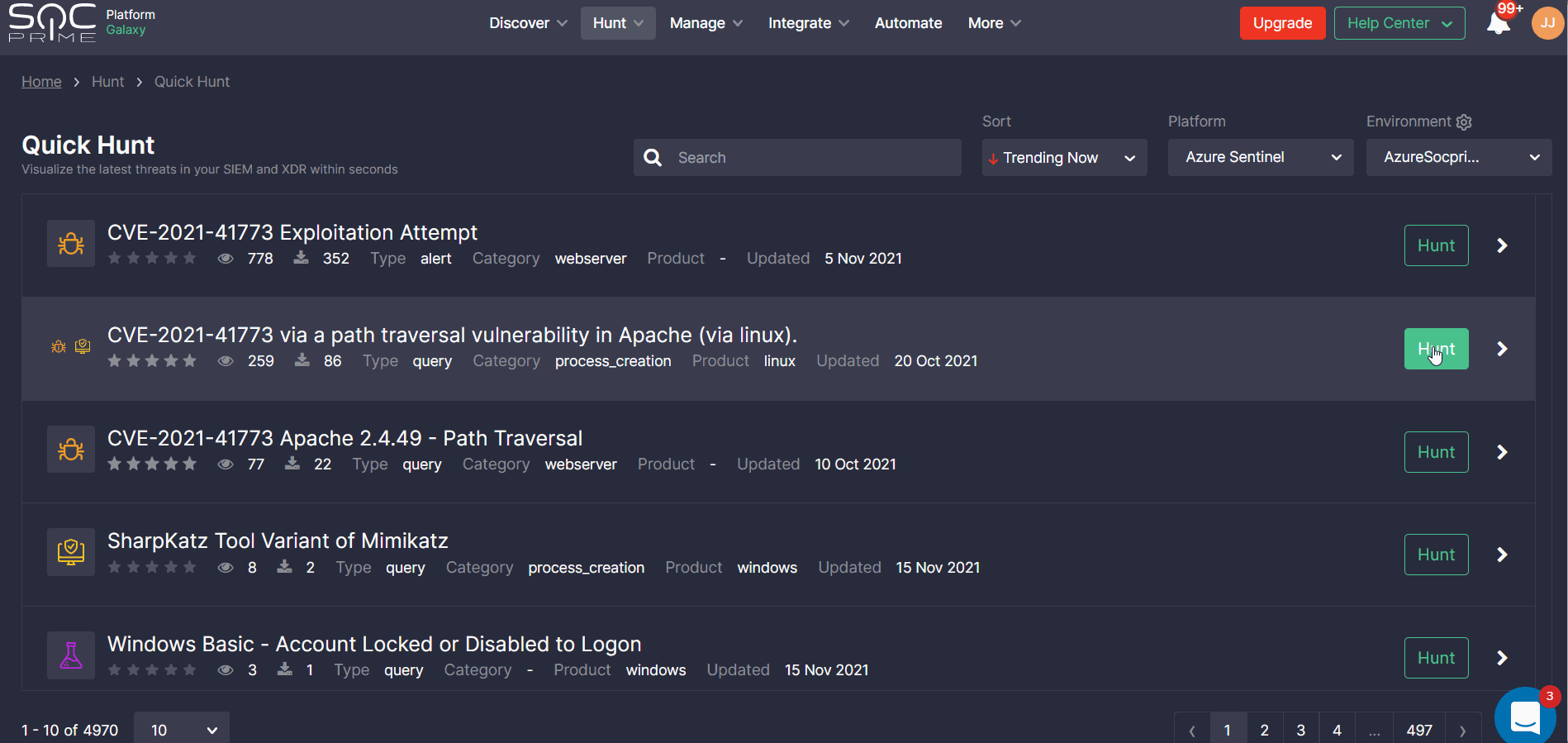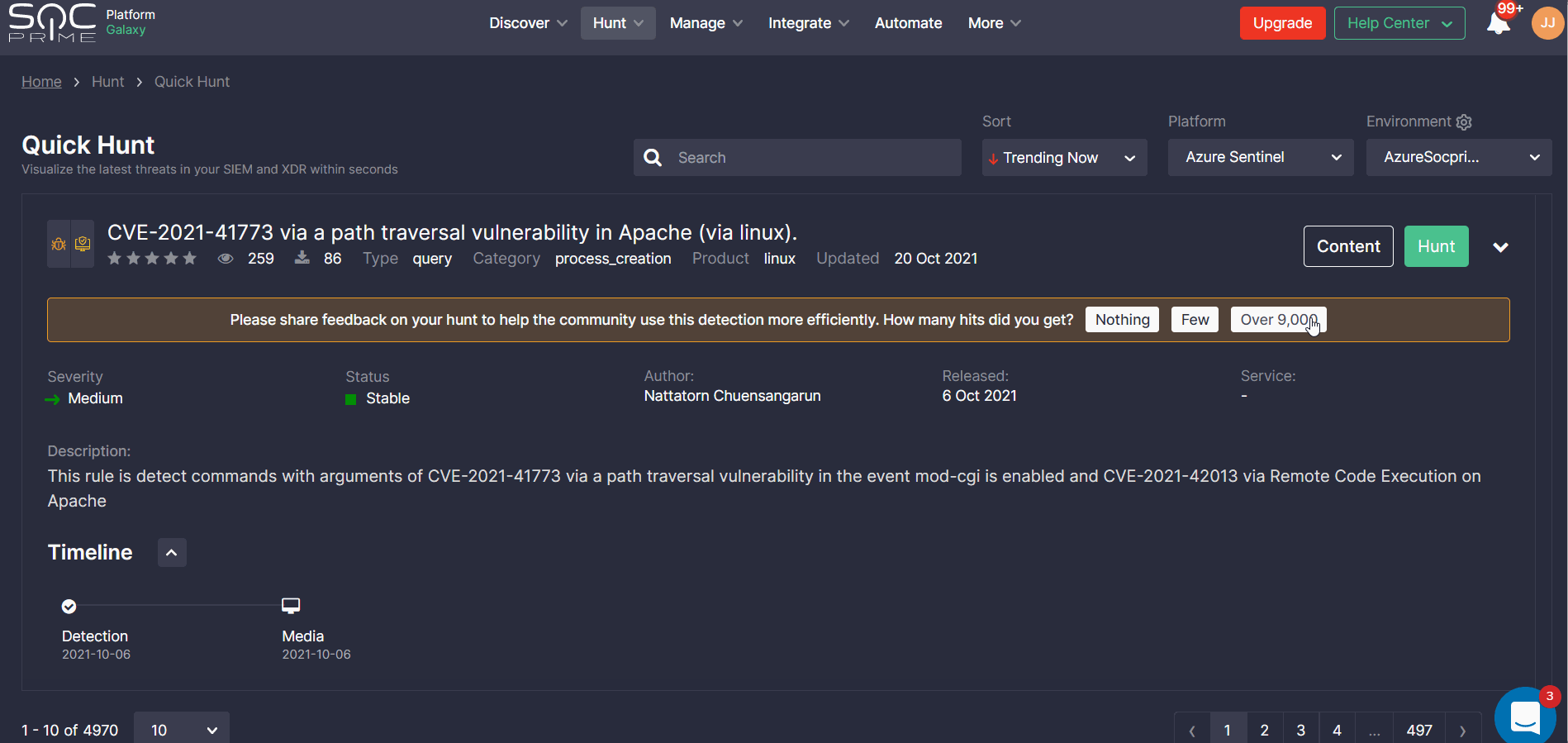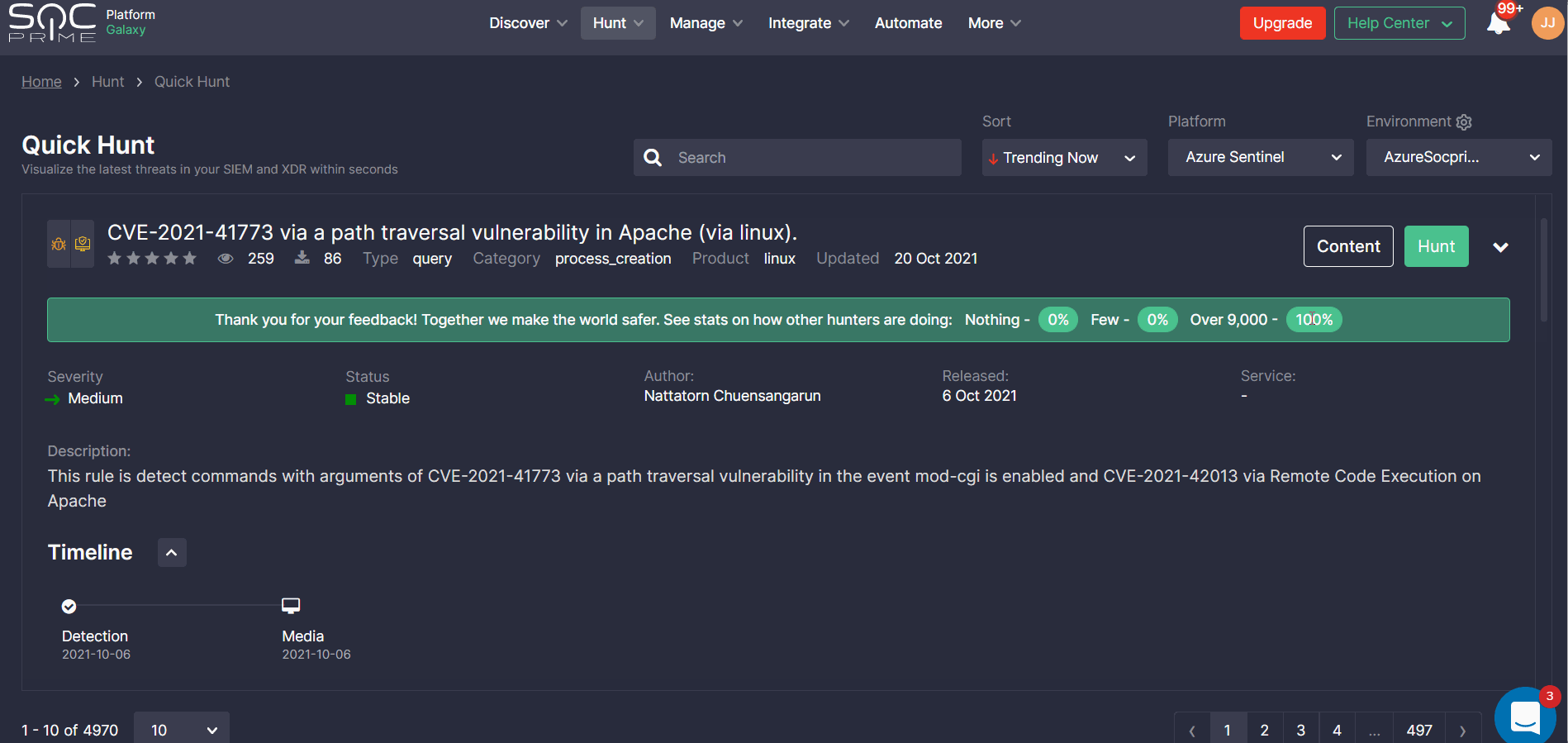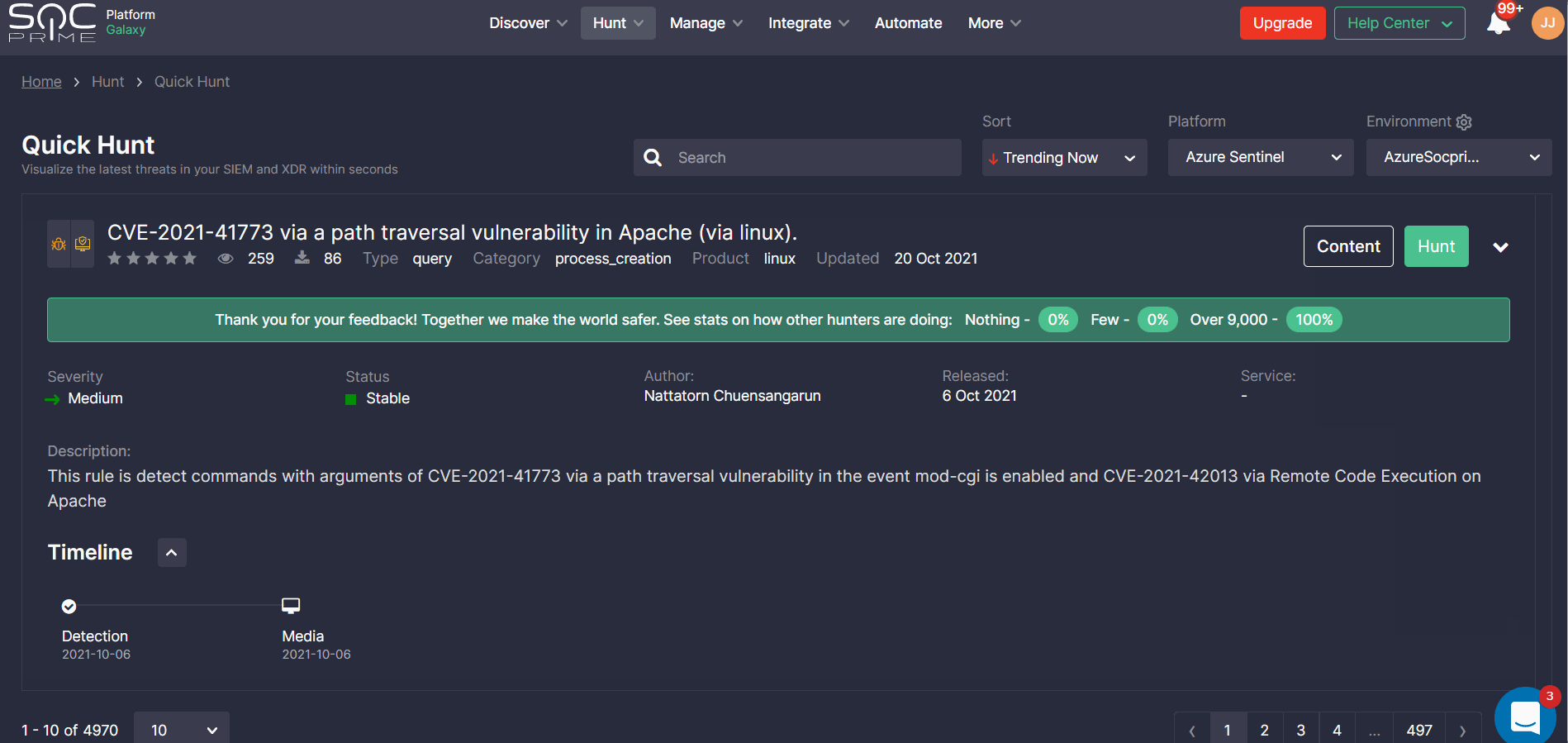
The provided feedback is anonymous and serves a single purpose — to help the global cybersecurity community and your peers understand the criticality of the query, thus making hunting more efficient. Collecting community-driven feedback helps the SOC Prime Team and the crowdsourcing Threat Bounty Program developers continuously improve the detection quality and ensure content is up-to-date with the latest threats.
Beginning on November, 22, 2021, the Quick Hunt module unlocks free unmetered hunts using top-rated and most trending Community queries from a wealth of Threat Detection Marketplace content base as part of SOC Prime’s Cyber Monday deal. By activating a promo code, SOC Prime users with a corporate email address can scan for threats free of charge in their SIEM or EDR environments by the end of December 2021. Participants of the Cyber Monday promotion can also book a guided session with SOC Prime experts, so they can easily set up a hunting environment to take advantage of the module. Stay tuned to our blog not to miss out on the Cyber Monday promo launch!
Check out the overview of Quick Hunt to learn more about one-click threat hunting capabilities powered by this module. Looking for ways to accelerate the organization’s cyber defense capabilities? Join SOC Prime’s Detection as Code platform for collaborative cyber defense, threat hunting and discovery enabling security teams to defend against attacks easier, faster and more efficiently than ever before.




