New day, new malware causing menace for cyber defenders. Hot on the heels of the novel MoonPeak Trojan, security experts have uncovered yet another malicious sample actively used in the ongoing attacks. Dubbed PEAKLIGHT, the novel memory-only threat applies a sophisticated, multi-stage attack chain to infect Windows instances with a variety of infostealers and loaders.
Detect PEAKLIGHT Malware
The latest stats highlight that in 2023, adversaries deployed an average of 200,454 unique malware scripts per day, equating to roughly 1.5 new samples per minute. To stay ahead of emerging threats like the newly discovered PEAKLIGHT malware, security researchers need reliable tools for threat detection and hunting.
SOC Prime’s Platform for collective cyber defense offers a curated set of Sigma rules specifically targeting PEAKLIGHT-related activity, alongside a comprehensive suite for AI-powered Detection Engineering, Automated Threat Hunting, and Advanced Threat Detection. Just press the Explore Detections button below and immediately drill down to a curated content collection.
All the rules are mapped to the MITRE ATT&CK framework and compatible with 30+ SIEM, EDR, and Data Lake solutions. Additionally, the detections are enriched with extensive metadata, including CTI references, attack timelines, and triage recommendations.
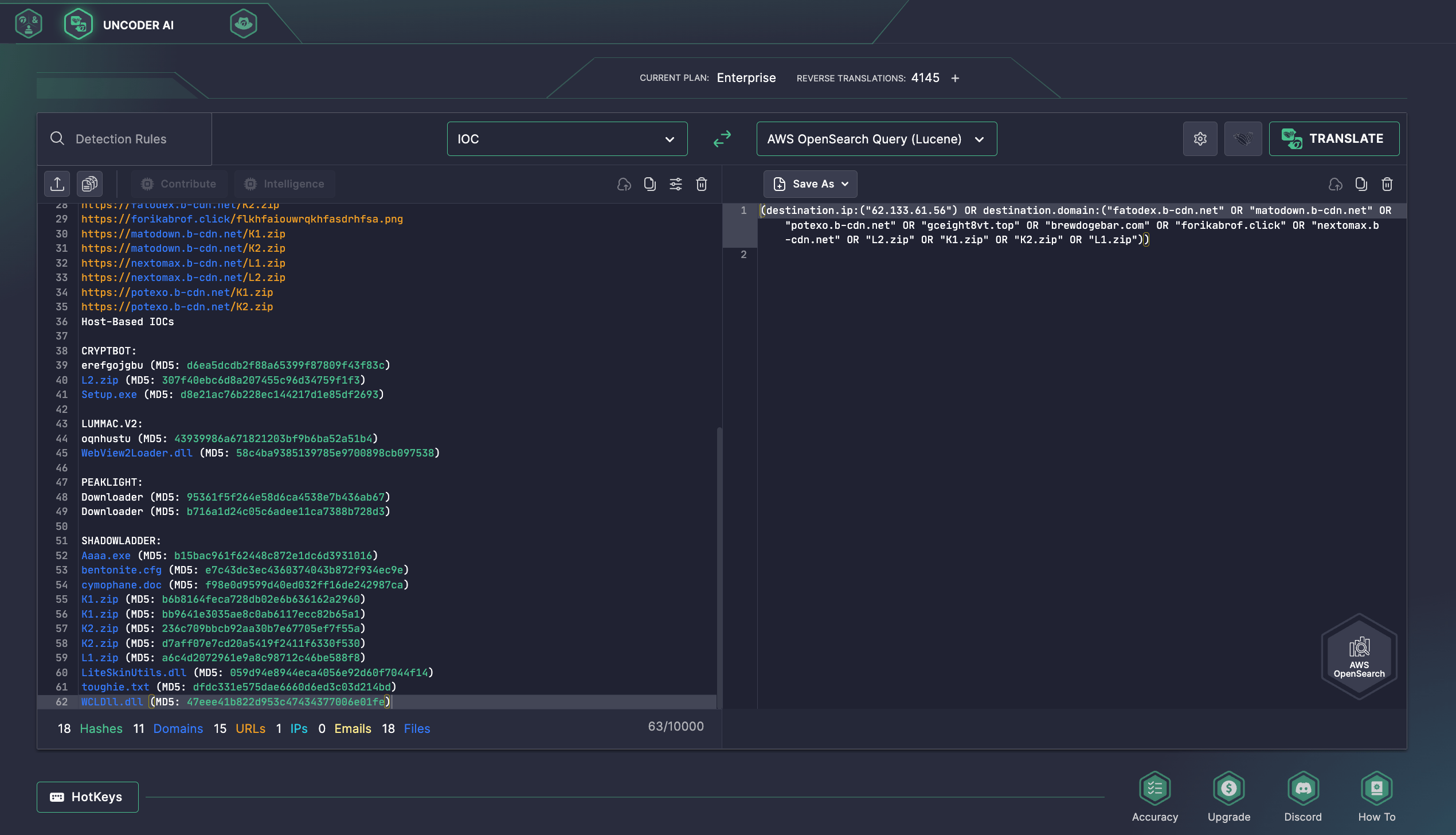
Additionally, security professionals might use Uncoder AI, the industry-first AI co-pilot for Detection Engineering, to instantly hunt for indicators of compromise provided in the report by Mandiant. Uncoder AI acts as an IOC packager, letting CTI and SOC analysts and Threat Hunters seamlessly parse IOCs and convert them into custom hunting queries ready to run in the SIEM or EDR of their choice.
PEAKLIGHT Malware Analysis
Mandiant researchers unveiled a novel PowerShell-based memory-only dropper tracked as PEAKLIGHT. The newly identified malware leverages a sophisticated multi-stage infection chain to deliver multiple payloads. Notably, in the newly identified adversary campaign, attackers take advantage of LNK files that are frequently used for offensive purposes and are often disguised as legitimate, making them effective at staying under the radar.
The attack chain starts with the download of weaponized ZIP files masquerading as pirated movies. These archives contain a harmful LNK file that connects to a content delivery network (CDN) hosting an obfuscated memory-only JavaScript dropper. The dropper then runs the PEAKLIGHT PowerShell downloader script on the host, which establishes the connection with the C2 server to retrieve additional payloads, including LummaStealer (aka LUMMAC.V2 or LUMMAC2), SHADOWLADDER, and CRYPTBOT infostealers operating under the malware-as-a-service model. During the infection process, PEAKLIGHT verifies the availability of ZIP archives in hard-coded file paths and, in case they do not exist, downloads them from a remote CDN.
Defenders identified various versions of the LNK files, some of which use asterisks (*) as wildcards to covertly launch the legitimate mshta.exe binary and execute malicious code from a remote server. Similarly, the droppers were discovered to contain both hex-encoded and Base64-encoded PowerShell payloads. These are eventually unpacked to run PEAKLIGHT, which is engineered to deliver further malware onto a compromised system while also downloading a legitimate movie trailer, likely as a distraction.
The emergence of diverse versions of the PEAKLIGHT downloader, each with its unique capabilities and the use of sophisticated obfuscation and evasion methods by malware maintainers, such as system binary proxy execution and CDN misuse, underscores the need for enhancing cyber resilience to minimize the risks of infections. By leveraging SOC Prime’s complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection, organizations can proactively defend against sophisticated attacks and emerging threats while building a robust cybersecurity posture.




