A quote of a famous professor “Good news everyone!” would be best fit to the recent events when the Internet of sheit Things has set the hell loose in the whole digital world, with Mirai botnet being one of its infamous minions. In before broken sarcasm-detectors: the situation is indeed tense, reputable researchers in the security field believe that we are now at 2 minutes to midnight. Regardless, I’ll try to save you some time by quickly sharing facts, analytics & conclusions made by our friends in security field and our security team with some background in forensics & incident detection.
Timeline: back in August, Flashpoint together with Level 3 Threat Research Labs actually predicted that an Attack of Things will happen and it is only a matter of time. In October, the source code of Mirai was released. To the date confirmed attacks attributed with Mirai include attempt to takedown internet access in entire Liberia, a 620+ GB DDoS on Brian Krebs, DDoS during US election, Dyn attack that caused a massive internet outage, and now an incident with 900K+ routers at Deutsche Telekom.
Attack vectors are evolving and so do the DDoS botnets as described in case study of Mirai by MalwareTech. Even though 2016 is almost over, we have tons of devices (more than ever?) that use clear-text protocols, so initial compromise started with a distributed telnet port scan with leaked hard-coded credentials. This has later evolved into SSH scan, and of course, other brute-force techniques were added along the way. Mirai botnet activities keep coming up, meaning that it is a running business (and operation?), someone got the capital and can invest into next more sophisticated techniques. A bright example is a proof-of-concept exploit shared by independent security researcher kenzo in his blog and more details on the attack & exploit also revealed by BadCyber. The root cause of such exploits are the “best” practices used by IoT manufactures such as hardcoded passwords and other cool features, and we all know how “easy” it is to go out and patch all those IoT devices when they are already out. In less than a month from kenzo’s post, we see an attack on Deutsche Telekom routers leveraging an exploit (modem vendor is different and so is the exploit but technique and purpose are likely the same). Some quotes from the date of the attack on 28th of November:
“Mirai Botnet attack is surfacing in Germany and hit more than 900,000 Routers from Telekom last night and today, targeting what we suspect Busybox linux type IoT / devices that in this case were routers”
HakDefNet, November 28,2016
“The botnet mass exploiting Deutsche Telekom routers is the same one which was responsible for the Liberian ISP DDoS.”
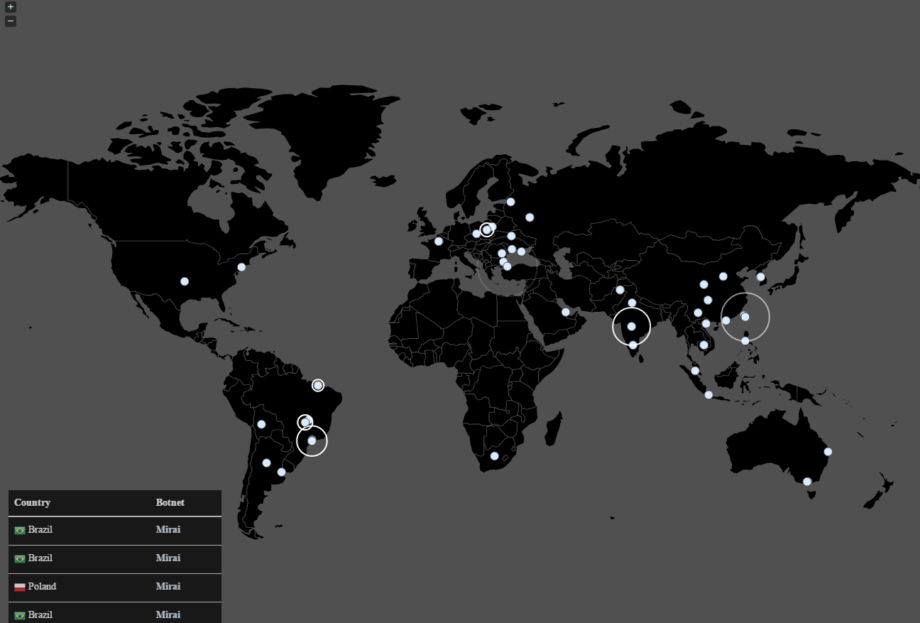
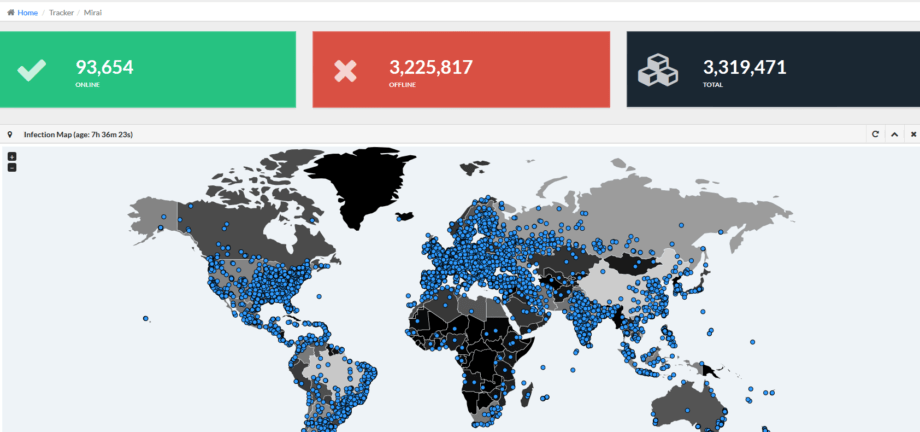
Speaking of MalwareTech, there’s a live map of Mirai connections available:
A quick OSINT analysis of data provided by the live tracker by MalwareTech with GEO-tagging and time-window filtering confirms yet again that problem is global, there are 93K+ active (compromised) devices.
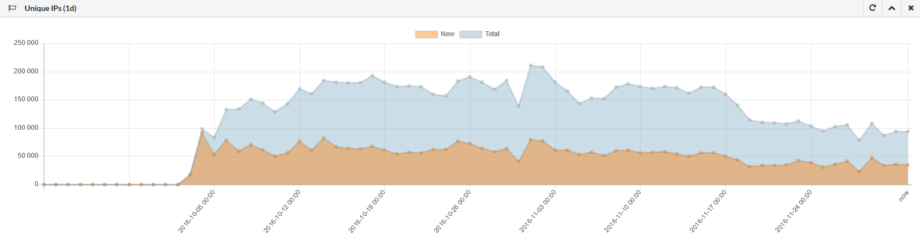
If we aggregate IP’s on daily basis, one can see that overall botnet size has currently declined, yet the story may be far from over, as new methods of attack keep coming up. Amount of “new” IP’s is hard to rely on as we need to consider dynamic address space (which is most common for home IoT devices).
On November 24th we’ve published a ETC (Emergency Threat Counter) SIEM use case for Mirai Detection for ArcSight, QRadar and Splunk, based on a free threat intelligence sample provided by our friends at HakDefNet. We are constantly in touch with our colleagues, they report an overall 1M+ IP’s that are either already spotted as a part of Mirai or are exploitable (compromised?) and can be used in future attacks.
Detection & Response advisory
SOC use cases. Monitoring for usage of clear-text protocols, traffic spikes per port, port-scan detection and brute-force detection across all technology stacks is highly recommended.
Mitigation for telecom & ISP’s. Patch compromised devices that are managed by your organization; implement ACL for remote access to management ports (only allow access from your admin’s IP’s), while at it check security of admin workstations (when was the last time they had a pentest or security audit? Make an unscheduled one). And one advise from captain obvious: change them passwords!
Any organization. Check if your corporate network has any Mirai infected devices. You can use ETC for Mirai detection available at https://ucl.socprime.com, or run a port scan on your own network for 7547 port to find exploitable devices. Another way to find compromised assets is to leverage Shodan engine without and with registration (example is a search IP’s with port 7547 reachable from Internet in Ireland).
Security awareness. It has never been a better time to check out the 8 best practices to secure IoT by Layer3
Notify end customers on the threat and include the link above, as any security and privacy conscious and savvy tech user can secure their own IoT themselves (update firmware, close ports & services). This is super-easy & low-cost solution that can be done with any of those email-campaign automation platforms out there.
/Stay safe