Hard on the heels of a new wave of cyber-attacks by UAC-0050 involving cyber espionage and financial thefts and relying on a diverse number of tools, including MEDUZASTEALER, another suspicious activity comes to the spotlight in the Ukrainian cyber threat arena. CERT-UA recently launched a new alert covering spoofed phishing attacks spreading MEDUZASTEALER via Telegram and impersonating the sender as Reserve+ technical support, the app from the Ministry of Defense of Ukraine.
Detect MEDUZASTEALER Infections Covered in the CERT-UA#11603 Alert
To stay on top of possible intrusions and proactively defend against novel malicious TTPs, SOC Prime Platform for collective cyber defense serves a dedicated Sigma rule stack addressing MEDUZASTEALER attacks. Rely on SOC Prime’s complete product suite for advanced threat detection, automated threat hunting, and AI-powered detection engineering to spot potential intrusions at the earliest stages.
To dive into a tailored detection stack, hit the Explore Detections button below. All the Sigma rules are mapped to the MITRE ATT&CK® framework, enriched with tailored intelligence, and convertible to 30+ SIEM, EDR, and Data Lake language formats.
Cyber defenders can further bolster their defenses against cyber attacks related to the mentioned adversary activity by leveraging additional detection content available on the SOC Prime Platform. To analyze UAC-0050 attacks retrospectively, apply the “CERT-UA#11603” tag based on the corresponding CERT-UA report identifier or filter content with “MEDUZASTEALER” for a more targeted search.
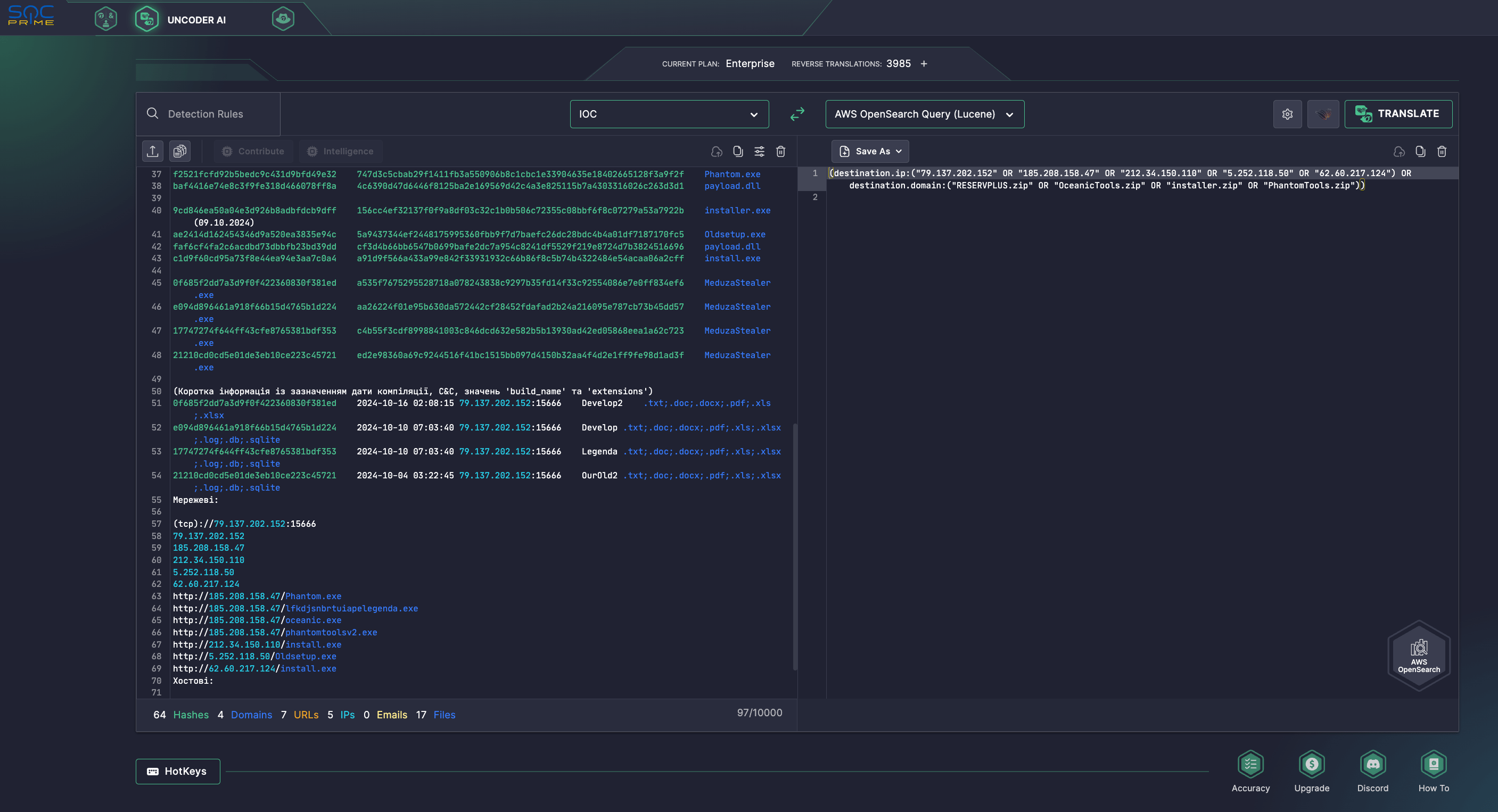
Security engineers can also take advantage of Uncoder AI to accelerate IOC packaging and retrospective hunting for MEDUZASTEALER-related threats using IOCs from the corresponding CERT-UA#11603 alert by instantly converting them into custom queries matching specific SIEM, EDR, and Data Lake languages.
MEDUZASTEALER Malware Description
CERT-UA has recently issued a novel heads-up CERT-UA#11603 notifying cyber defenders of ongoing cyber attacks distributing MEDUZASTEALER. On October 15, 2024, CERT-UA received information regarding the distribution of suspicious messages through the Telegram account @reserveplusbot, which had been identified in May 2024 as one of the contact methods for the “Reserve+” technical support team.
Notably, at the end of December 2023, the nefarious UAC-0050 group attacked the Ukrainian and Polish government institutions, employing MEDUZASTEALER in addition to Remcos RAT.
In the latest attacks, the malicious messages prompt targeted users to install “special software” and contain an archive named “RESERVPLUS.zip.” The distributed ZIP archive contains an executable file, which, when executed, downloads another file, “install.exe.” The latter infects the computer with the MEDUZASTEALER malware.
According to its configuration file, the stealer was set up to exfiltrate files with the extensions “.txt, .doc, .docx, .pdf, .xls, .xlsx, .log, .db, .sqlite” and then delete itself. To bypass security software, the directory where the malware was stored was added to Microsoft Defender’s exclusions list using a PowerShell cmdlet.
To stay ahead of attackers and minimize the risks of MEDUZASTEALER infections, organizations can rely on SOC Prime’s complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection, while building a future-proof cybersecurity posture.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK gains detailed insight into the context of the latest offensive operations leveraging MEDUZASTEALER malware. Refer to the table below to view the comprehensive set of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques.




