Cybersecurity risks are escalating in 2025, with data showing a surge in vulnerabilities, active exploitation, and major breaches. Most recently, CISA reported that attackers compromised a U.S. federal agency by exploiting an unpatched GeoServer instance affected by CVE-2024-36401, a critical RCE flaw addressed in June 2024. However, thousands of servers stayed exposed, with attacks spotted as early as July.
Detecting TTPs Described in CISA’s AA25-266A Alert
Exploiting software vulnerabilities remains one of the most common and dangerous ways attackers gain access to systems. This is especially true when the weaknesses are in widely used software that large organizations, including government agencies and critical infrastructure, rely on. Hackers often target these popular platforms to break in and take control of important systems.
The 2025 Data Breach Investigations Report (DBIR) from Verizon shows that using vulnerabilities to gain initial access increased by 34%, now accounting for 20% of all breaches. Data from Mandiant confirms that exploiting vulnerabilities has been the most common way attackers first compromise systems for the fifth year in a row. In cases where the entry point was identified, 33% of attacks started with exploiting a software vulnerability.
A recent case, highlighting the severity of this risk, involved a U.S. federal agency breach through an unpatched GeoServer instance affected by CVE-2024-36401. This critical remote code execution vulnerability was patched in June 2024 and later added by CISA to its catalog of actively exploited vulnerabilities. Despite these measures, many servers remained exposed into 2025, emphasizing CISA’s continued call for prioritized patching, monitoring for suspicious activity, and strengthening incident response plans.
Register now for the SOC Prime Platform to access an extensive library of context-enriched detection rules and AI-driven threat intelligence, helping you stay one step ahead of attacks leveraging emerging vulnerabilities. The platform features curated detections addressing TTPs described in the CISA’s AA25-266A alert, backed by a complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection. Click the Explore Detections button below to dive into the relevant detection stack.
Cyber defenders might also browse the Threat Detection Marketplace using the “CVE” tag to explore a wider set of detection rules related to vulnerability exploitation.
Additionally, security experts might streamline threat investigation using Uncoder AI, a private IDE & co-pilot for threat-informed detection engineering. Generate detection algorithms from raw threat reports, enable fast IOC sweeps, predict ATT&CK tags, optimize query code with AI tips, and translate it across multiple SIEM & EDR languages. For instance, security professionals can use the latest AA25-266A alert to generate an Attack Flow diagram in a few clicks. 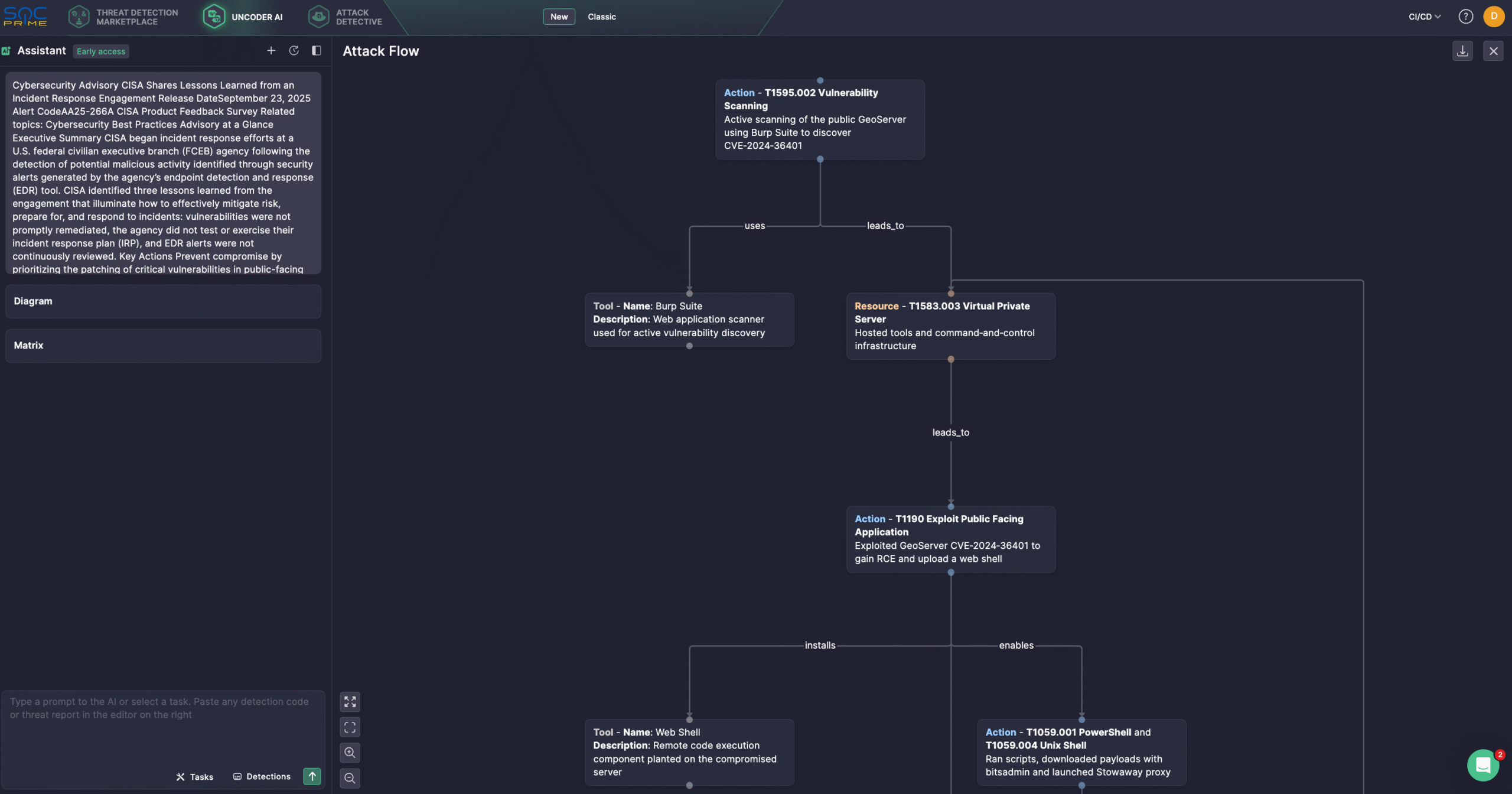
Federal Civilian Executive Branch (FCEB) Agency Breach Analysis Covered in CISA’s AA25-266A Alert
CISA began incident response efforts at a U.S. federal civilian executive branch (FCEB) agency after its EDR system flagged suspicious activity. In its alert AA25-266A from September 23, 2025, CISA shared lessons learned from the engagement, emphasizing the importance of timely patching, rehearsed response plans, and centralized log aggregation.
Defenders found that attackers had exploited a critical RCE flaw identified as CVE-2024-36401 roughly three weeks before the alerts appeared. CISA determined the intrusion began on July 11, 2024, when attackers weaponized CVE-2024-36401 in a public-facing GeoServer. Using this flaw, the attackers deployed open-source tools and scripts to maintain persistence, with the issue added to CISA’s KEV Catalog on July 15, 2024. On July 24, 2024, they also breached a second GeoServer using the same exploit and then moved laterally from the first GeoServer to a web server and an SQL server. Across these systems, hackers attempted to install web shells like China Chopper and deployed scripts for remote access, persistence, command execution, and privilege escalation, while also leveraging LOTL techniques.
The attackers identified CVE-2024-36401 in the agency’s public-facing GeoServer using Burp Suite Burp Scanner, with CISA detecting related activity in web logs, including traffic from Burp Collaborator domains tied to the same IP later used for exploitation.
Adversaries relied on publicly available tools and a commercial VPS for remote access. For initial access, threat actors exploited CVE-2024-36401 via eval injection by compromising GeoServers.
To maintain persistence, they deployed web shells, cron jobs, and valid accounts, though some accounts were deleted without evidence of further use. Adversaries also attempted to escalate using a DirtyCow utility applied to weaponize CVE-2016-5195, which affects older Linux kernels, and successfully transitioned from compromised service accounts. As for defense evasion methods, hackers employed indirect command execution via .php shells and xp_cmdshell, abuse of BITS jobs, and staging of the RingQ evasion tool. Once inside the organization’s network, adversaries relied on brute force to collect passwords alongside abuse of service accounts. After gaining initial access, they mapped the network with ping sweeps and used tools like fscan and linux-exploit-suggester2.pl, leaving behind evidence of scans.
In one case, attackers moved laterally from the web server to the SQL server by enabling xp_cmdshell on GeoServer 1 to achieve RCE. For command-and-control, they downloaded payloads with PowerShell and bitsadmin getfile.
Adversaries were observed deploying Stowaway, a multi-level proxy utility written to disk using a Tomcat service account, to tunnel traffic from their C2 server through the web server, bypassing intranet restrictions and reaching internal resources. After testing access with ping sweeps, they fetched a modified Stowaway via curl and established an outbound C2 channel over HTTP on TCP/4441. CISA also found numerous publicly available tools and scripts hosted on the C2 server.
The authoring agency highlighted three key lessons learnt from the incident, including the delayed patching of vulnerabilities, lack of incident response plan testing, and gaps in EDR alert monitoring. As key CVE-2024-36401 mitigation and remediation measures to reduce the risks of breaches, defenders recommend prioritizing the patching of critical vulnerabilities and known exploits on public-facing systems, maintaining and regularly testing incident response plans, as well as implementing detailed logging and centralizing logs in an out-of-band location. Leveraging SOC Prime’s complete product suite, built on zero-trust principles and backed by AI & top cybersecurity expertise, enables global organizations to strengthen their cybersecurity posture and minimize the risks of critical threats before they escalate into attacks.




