Today, we want to introduce to the SOC Prime’s community a talented and devoted member of the Threat Bounty Program and detection content author – Phyo Paing Htun, who has been publishing detections to the SOC Prime Platform since December 2022.
- Tell us about yourself and why you decided to become a cybersecurity specialist.
My name is Phyo Paing Htun, and you can call me Chi Lai. I was born in Myanmar, and I have Burmese citizenship. But these days, I relocated to the city of Bangkok, Thailand, and I am currently working in Bangkok. My current position is Cybersecurity Incident Responder L2 at one of the Managed Security Service Providers in Thailand. My responsibility is to respond to every incident and every threat that is escalated by SOC analysts, as well as research CVE attack behaviors. The main focus point is how to understand and mitigate potential attack behaviors using Security Information and Event Management (SIEM).
- What are your professional education and certifications, and how did you develop professionally?
I’ve already got the BlueTeam Level 1 (BTL1) by the Security Blue Team and also passed the Threat Hunting Professional exam by INE Security in 2023.
- How did you learn about the Threat Bounty Program? Why did you decide to join?
I learned about it from my senior friends (Ko Kyaw Pyiyt Htet, Ko Zaw Min Htun, and Ko Aung Kyaw Min Naing) from Myanmar, who are also members of the Program. They contributed Sigma rules to SOC Prime, and they supported me in how to write a Sigma rule, how to search for cybersecurity news, and other things like that. Also, I would like to write threat-detection queries in Splunk SPL, Kibana queries, KQL, etc, but it is hard to learn and understand all the languages in detail. So, I’ve chosen the Sigma language to learn it further. Sigma can be converted in any SIEM or EDR rule with uncoder.io.
- Is it difficult for you now to write a rule?
I have a Software Developer background, and I am familiar with multiple query languages like YAML. It is not difficult for me now. I started learning from the article Sigma Rule for Beginners by Adam Swan. It gave me an understanding of the basics, such as how to write a condition, how to identify log sources, what kinds of logsource Sigma can support, etc.
- And when you write rules for Threat Bounty, how long does it take you from the idea to the moment of publication?
I think it will probably take up to two hours. From threat reports, I need to understand what kind of tactics and techniques I can write for detection purposes. I must find the critical artifacts, read the report, and understand it clearly. After that, I write the Sigma rule.
- Can you please describe your rule creation process using the example of one of your recently published rules? From the research to the publication, including the review process?
This is my latest rule for now – “Possible BlotchyQuasar RAT [aka Hive0129’s Banking Trojan] Defense Evasion Activities Detected By Modified Registry Values. (via Registry_Event)”. I decided to write about the defense evasion activity. I started by reading the report. This report is about the BlotchyQuasar malware, and the activity is already associated with the Hive0129 APT group. The report gave me several ideas for writing the detection chain, such as detection for initial access, defense evasion, C2 communication, and others.
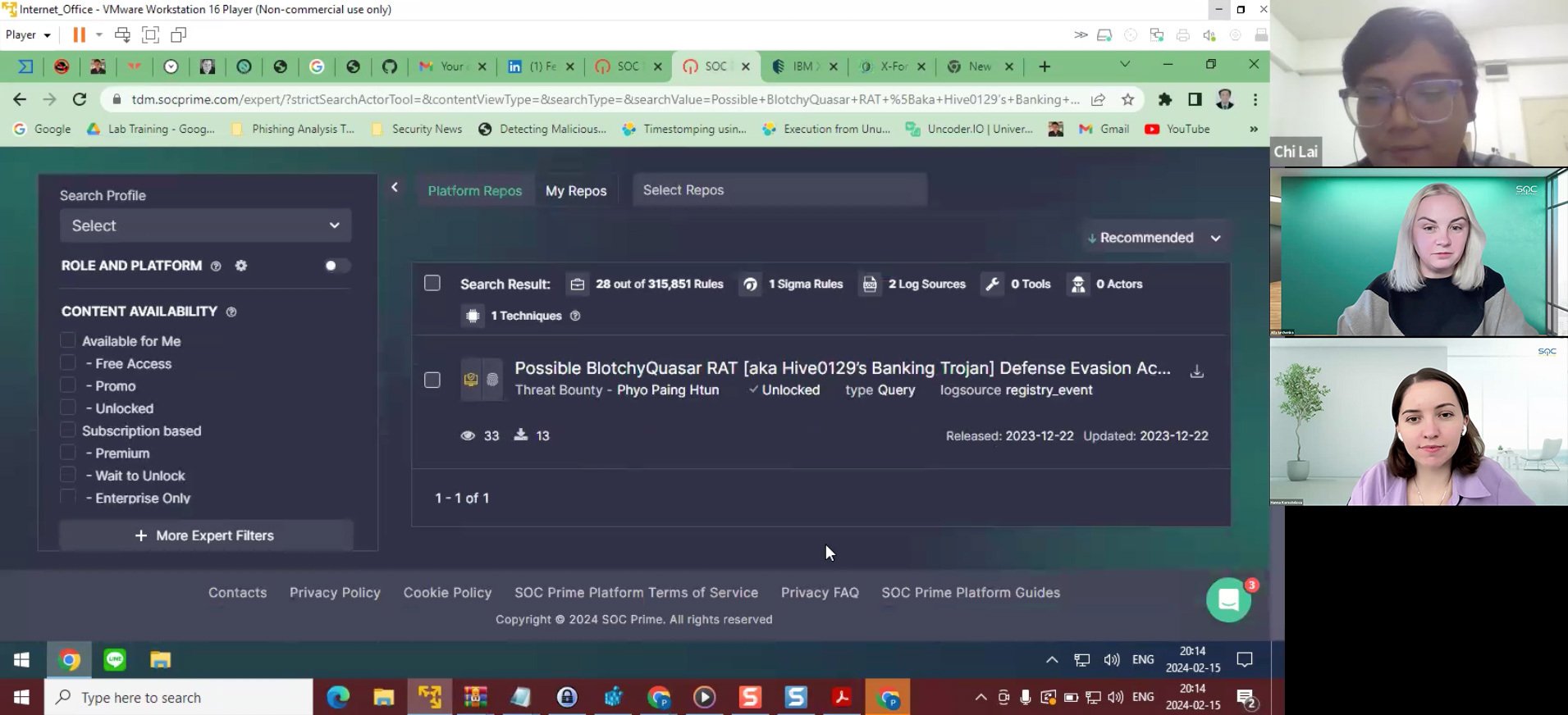
I chose the defense evasion technique for the registry value-changing process, based on one of the report parts. But before writing the rule, I need to search for the existing rule on the SOC Prime Platform using the Lucene search. First of all, I need to make sure I am not going to write a duplicate rule. As my search with Lucene returned several rules for “TamperProtection”, I decided to choose another one and create a rule.
At first, my rule was rejected because the details of the value parts were wrong. But I quickly made the needed changes, and the rule was published.
I use IBM X-Force Exchange Osint Advisory to search for new threat reports.
- What is the most frequent reason for content rejection that you personally receive?
It is probably “low resilience rules” because sometimes the reports have behavior IOCs, and if I write a rule based on them, it will be rejected. We need to create robust detection rules to get them accepted.
- Being a part of the big professional community, what do you think is the biggest value of the rules that you publish to the Platform?
When organizations refer to SOC Prime for detection content, they can be sure that the detection rules are not just “any” rules, or IOC rules, or behavior-IOC rules. For organizations, it is very important to have robust detection, like generic detection rules.
- What is your recommendation for the new members of the Threat Bounty program, new content developers who just started their path with the program?
I would definitely recommend all new members check the SOC Prime Platform for the existing content. Also, please don’t write low-level IOC rules. These rules are not efficient after a short time. Also, SigmaHQ may be a good resource for learning some general basics on how to create a Sigma rule.
- What is your motivation for participating in the Program after receiving a lot of content publication rejections?
If I get too many rejection messages, I usually go ask on the Discord channel for the Threat Bounty program. For example, I could not understand why they kept rejecting my rule, saying it was low-resiliency. On the Discord channel, I asked the team to explain it to me. It all became very clear to me, and I just had to redo the rule. I sent the rule for review, and it was rejected again! It was a really hard time for me, but I took some time to analyze the rule, I made some changes again, and after the review, my rule was finally published. It is very helpful when the verification team provides some details in cases when a rule can be modified to perform better.
- Do you find it helpful when we reply to other authors on Discord? For example, when other authors have questions about their rules being rejected.
That is very helpful for me. In particular, I learned why rules are rejected from the conversations on Discord. Also, those conversations gave me an understanding of what kind of mistake (low resiliency) I need to avoid and what kind of robust detection rules I can create.
- You mentioned that you started participating in the Threat Bounty Program with the help of your friends, who started publishing rules first. It is a great example of a local professional community that supports new members in growing their cyber defense potential. How did you meet the guys? Is there a competition between you?
We used Discord and other channels to chat about threat detection ideas that were interesting to us. We ( Myanmar Threat Detection Developer Community ) don’t have competition within the group, we help and support each other, and that is what helps each of us grow.
Thank you for your time and such an insightful conversation! We wish Phyo Paing Htun success with his further content publications!
Do you want to join the SOC Prime Threat Bounty Program? Don’t hesitate to apply for participation now!




