Dridex Malware Detection: Proactively Defend With SOC Content
Table of contents:
Dridex malware has been attacking banks and financial institutions for almost a decade. In 2019, the US Department of Justice brought charges against Russian nationals who stood behind the creation of the Dridex malware and were leading criminal activities that delivered them about $100 million. Even back in 2015, Dridex was responsible for roughly $30.5 million in the UK and $10 million in losses in the United States.
According to Unit 42 reports, a new iteration of Dridex attacks was spotted again in September 2020 after a one-month period of the malware inactivity.
Dridex Malware Analysis
First malspam attacks delivering the Dridex trojan (also known as “Cridex” or “Burgat”) were spotted back in 2011, and within several years the malware established itself as one of the most infamous trojans targeting the financial sector. Dridex spyware attacks are focused on EU and Asia-Pacific regions and mainly high-income organizations. Various modifications of Dridex applied configuration files in the XML or binary formats, becoming more sophisticated over the years. The fourth more advanced version of Dridex uses RC4 encryption and a much more stringent loader authorization protocol as compared to its previous modifications.
There have been cases of spreading Dridex Trojan along with other malware through the exploit kits. In 2019, the notorious Spelevo exploit kit was distributing banking Trojans via a compromised contact website. The malicious script on the compromised website pages, including the homepage, redirected users to an exploit for either CVE-2018-15982 or CVE-2018-8174 depending on the user operating system, Adobe Flash version, plugins, available patches, and other environment characteristics. Both exploits were used to deploy Dridex as a final payload.
Dridex Malspam Attacks and Phishing Emails
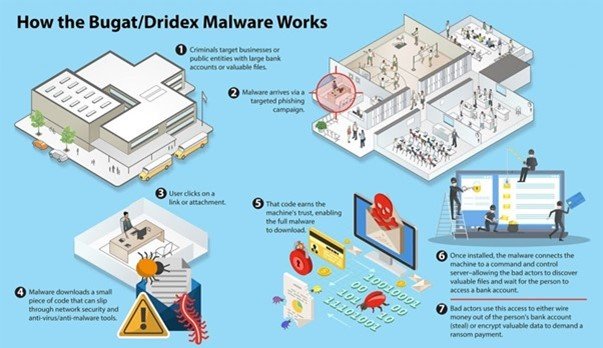
The malware is active and dangerous for bank institutions and their clients, as phishing emails represent one of the easiest ways to deliver a malicious code to a victim. Phishing emails are properly compiled leveraging professional language and terminology, and quite often they are built as messages requiring immediate attention to lure potential victims into a trap. They often look like legitimate business email addresses. Dridex malspam attacks deliver an attachment that may include the names of financial records containing obfuscated macros. Once enabled, the malicious macro triggers download of the banking trojan which would harvest credentials and then perform fraud financial transactions.
In 2018, there was a surge in spreading the Dridex banking trojan through a notorious spam campaign. Compromised users received over 10,000 emails with links to infected FTP servers. Attackers took advantage of both MS Word files that abused the DDE feature to download Dridex and Excel files containing the malicious macro. Therefore, the mature behavior of the company’s personnel drastically decreases chances to infect the system with the Dridex trojan.
Picture by Spambrella:
Dridex Malware Prevention and Detection Content
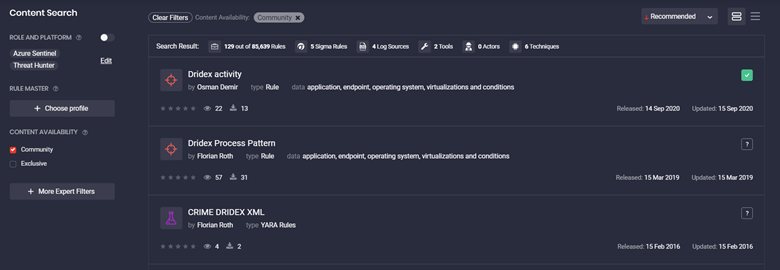
SOC Prime Threat Detection Marketplace enables Detection as a Code operations by delivering 85,000+ SOC content items to 5,500+ organizations in various industries, including the financial sector. Security performers can find the “Dridex activity” Community Sigma rule by Osman Demir to detect the latest Dridex attack in your system.
This Sigma rule also offers translations for the following 15 platforms:
- SIEMs: Azure Sentinel, Humio, Splunk, Sumo Logic, ELK Stack, ArcSight, QRadar, Graylog, RSA NetWitness, LogPoint
- EDR: Carbon Black
- Chronicle Security
- Apache Kafka ksqIDB
- Microsoft PowerShell
- Regex Grep
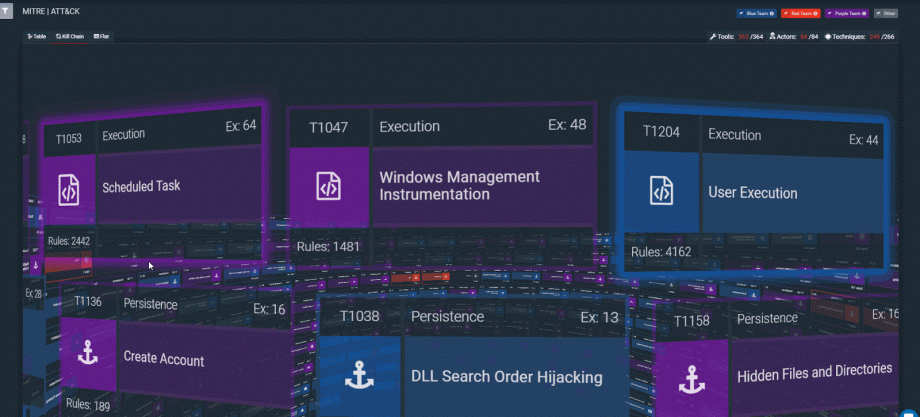
The rule addresses the following ATT&CK Techniques:
- Spearphishing Attachment Technique (T1193) of the Initial Access Tactics
- User Execution Technique (T1204) of the Execution Tactics
Looking for more threat detection content on Dridex attacks? Threat Detection Marketplace offers 200+ SOC content items targeted at Dridex malware, and over one hundred Community rules among them.
Ready to try out SOC Prime Threat Detection Marketplace? Sign up for free. Or join the Threat Bounty Program to craft your own SOC content and make your own contribution to the world’s largest threat detection community.