Phishing attacks on Ukrainian state bodies spreading diverse malware strains have not been a rarity throughout 2022. Hard on the heels of a phishing cyber attack against Ukraine distributing DolphinCape malware, another phishing campaign is causing a stir in the cyber threat arena.
On December 18, 2022, CERT-UA researchers issued the latest alert tracked as CERT-UA#5709, warning cyber defenders of phishing attacks against Ukrainian state bodies, specifically targeting the DELTA system users. In this ongoing campaign, compromised users received a notification prompting them to update their certificates in the DELTA system, a cloud solution for real-time situational awareness on the battlefield. Opening a PDF lure attachment disguised as legitimate digest content triggers an infection chain, which further spreads FateGrab/StealDeal malicious software on the affected systems.
FateGrab/StealDeal Malware Distribution: The Phishing Campaign Analysis Covered by CERT-UA#5709
The latest CERT-UA#5709 alert covers the details of the ongoing phishing attacks targeting the Ukrainian users of the state-based military system DELTA. On November 18, 2022, CERT-UA researchers were notified by the Center for Innovation and Development of Defense Technologies of the Ministry of Defense of Ukraine of the malicious campaign leveraging fake notifications of the DELTA certification updates used as phishing lures.
DELTA (also Delta) is the national cloud-based platform for situational awareness on the battlefield developed by NATO standards, which provides a holistic understanding of the battle space in real time and integrates all the data about the enemy from multiple sensors and sources into a digital map.
In the ongoing adversary campaign, threat actors tracked as UAC-0142 spread PDF attachments via email and messengers that can potentially trigger an infection chain and distribute FateGrab/StealDeal malware on the targeted computers of the DELTA users. These PDF attachments masquerade as legitimate digests and trick the victims into following a link to a malicious ZIP archive. Opening this link leads to downloading the certificates_rootca.zip archive, which contains an executable file protected based on obfuscation via VMProtect. Running the latter triggers the creation of multiple VMProtect-based DLL files along with another executable file, which simulates the process of certificate installation. As a result, the compromised systems can be infected with FateGrab based on the malicious FileInfo.dll and ftp_file_graber.dll DLL files and StealDeal malware samples. The latter can exfiltrate data leveraging multiple Internet browsers.
Detecting the UAC-0142 Malicious Activity
To help cyber defenders timely identify an infection triggered by the FateGrab/StealDeal malware and attributed to the adversary activity of the UAC-0142 group, SOC Prime Platform curates a list of dedicated Sigma rules. For a streamlined search for relevant detections, they are filtered by the corresponding custom tag “UAC-0142” based on the group identified. The above-mentioned Sigma rules are aligned with the MITRE ATT&CK® framework and are instantly convertible to the industry-leading SIEM, EDR, and XDR language formats.
Click the Explore Detections button to immediately drill down to the curated list of Sigma rules related to the adversary activity of the UAC-0142 group. Security engineers can also gain insights into the comprehensible cyber threat context enriched with MITRE ATT&CK and CTI references, mitigations, relevant executable binaries, and more metadata to shave seconds of threat research.
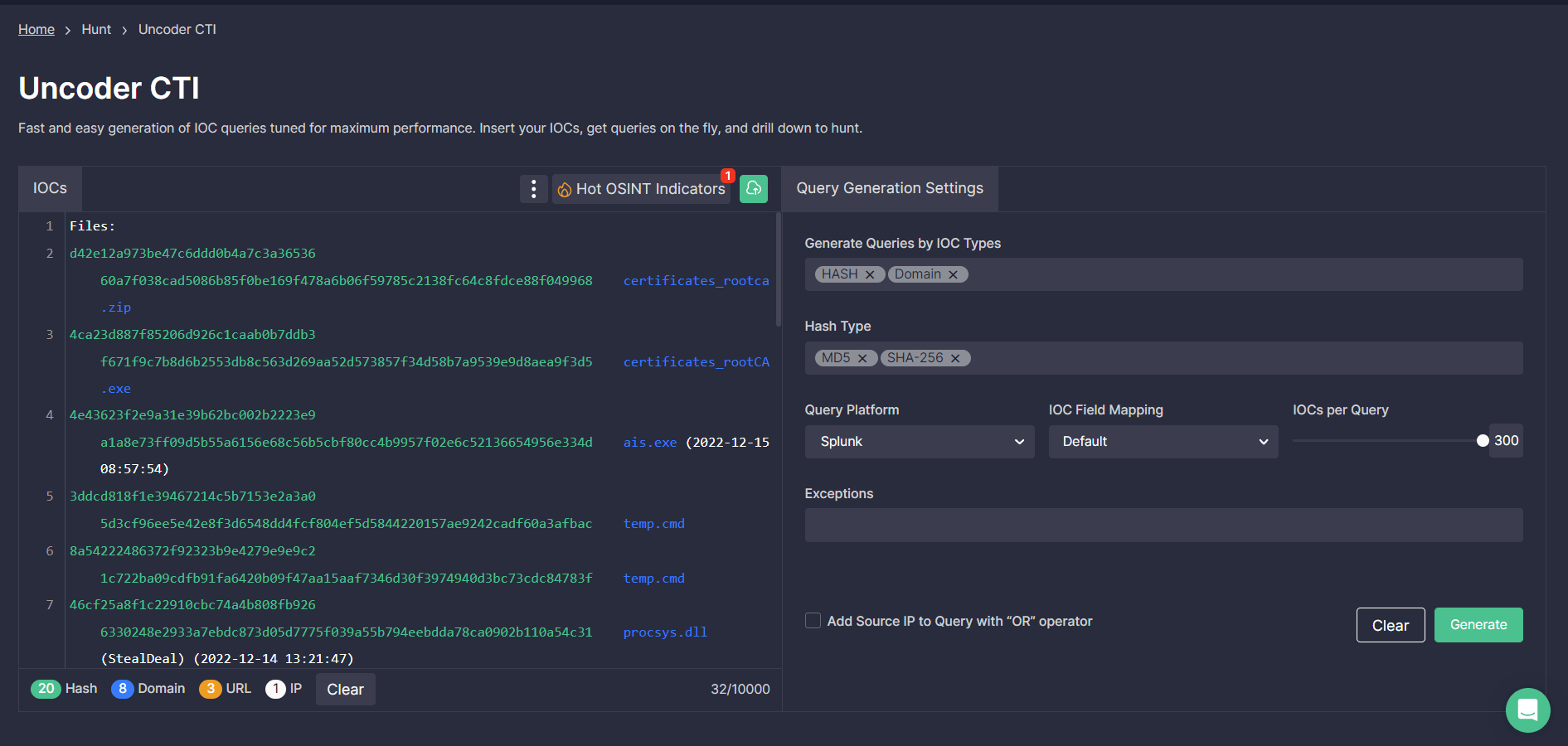
Security teams can also search for relevant IOCs covered in the latest CERT-UA#5709 alert via Uncoder CTI. Use the tool to automatically generate performance-optimized IOC queries customized to security needs and drill to hunt for threats attributed to the malicious activity of the UAC-0142 directly in your SIEM or XDR environment.
MITRE ATT&CK®Context
To explore the MITRE ATT&CK context linked to the malicious activity of the UAC-0142 threat actors targeting Ukrainian DELTA users and spreading FateGrab/StealDeal malware, check out the table below. Provided Sigma rules are mapped to ATT&CK v12 addressing the corresponding tactics and techniques:




