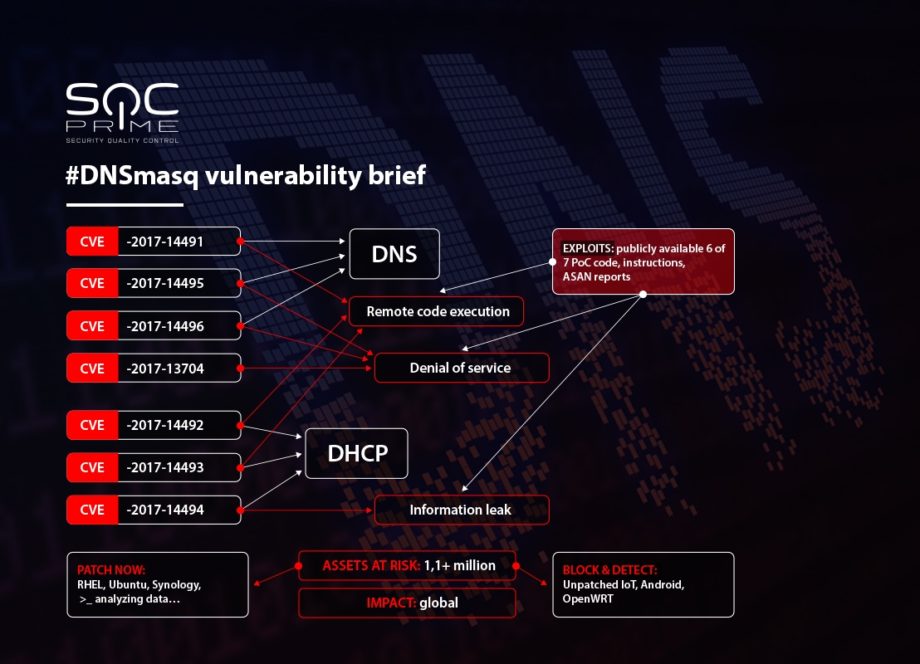
Good news everyone! It has now been 10 days since Google Security released 7 critical vulnerabilities along with PoC exploit code for popular dnsmasq service and the world is still alive as we know it. How long will this last? If we refer to WannaCry outbreak it takes a while from public exploit being released to a global outbreak. Or does it? EternalBlue exploit was released on January 7th along with other “Lost in translation” leaks so that’s 5 months prior WCry attack. However, if we recall the exact timeline we can note that by end of April there were over 1,7M hosts infected with DoublePulsar backdoor traceable online by scanning port 445 or just looking through Shodan data. I’d like to refer to Dan Tentler of PhobosGroup reporting massive DoublePulsar infection back on April 19th, starting the scanning efforts and reporting the findings. And since WannaCry struck on May 12th it took exactly 24 days from the moment of public disclosure on tens of thousands backdoored machines to the day when attack happened. How does this relate to the Dnsmasq situation? This time I had a little freedom to make a pretty picture describing the threat:
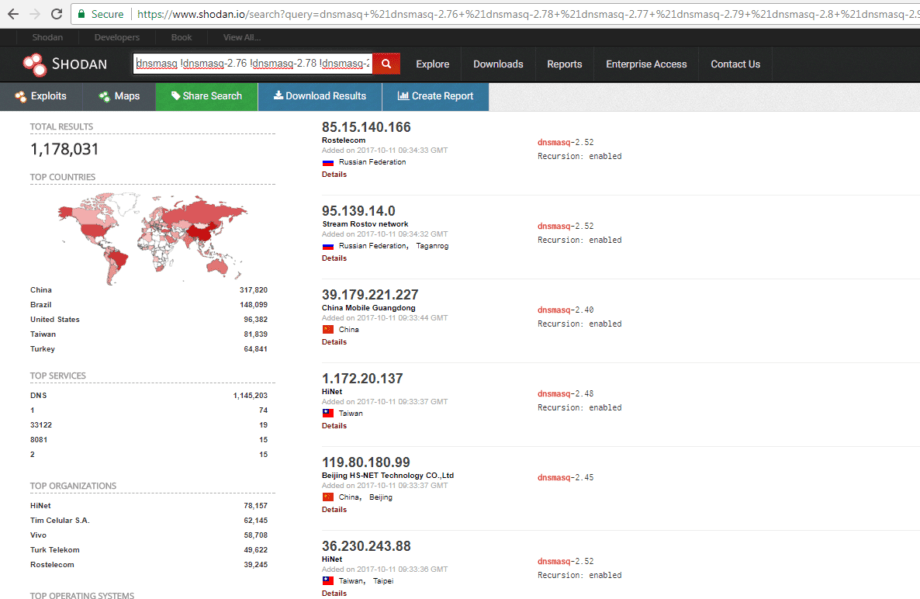
With 3 RCE vulnerabilities we have to treat all those machines running unpatched dnsmasq as already compromised and likely backdoored. And since we’ve seen adversaries’ capabilities of executing global WannaCry attack in 24 days we can foresee that something big and bad can already go off as early as October 26. Or 27th to bring another fun Friday for us infosec folks. It may also happen faster since as they say “attackers always evolve”. A scan and verification would be nice to confirm the backdoor hypothesis, but first lets measure the size of the incoming disaster by asking Shodan. Here’s a query if you’d like to verify the accuracy: https://www.shodan.io/search?query=dnsmasq+%21dnsmasq-2.76+%21dnsmasq-2.78+%21dnsmasq-2.77+%21dnsmasq-2.79+%21dnsmasq-2.8+%21dnsmasq-2.9
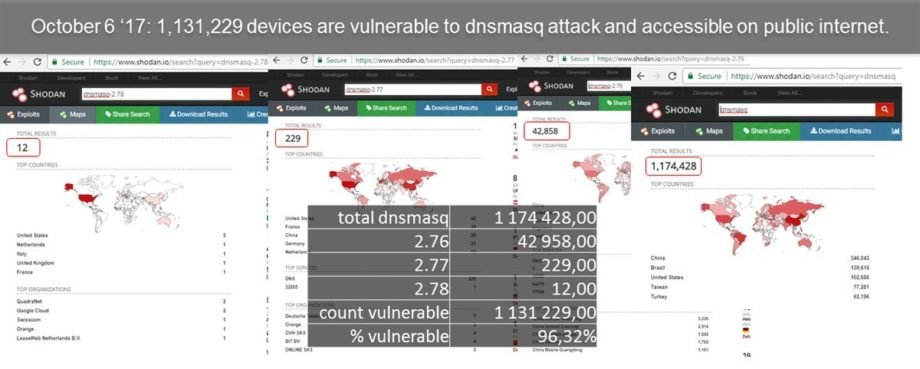
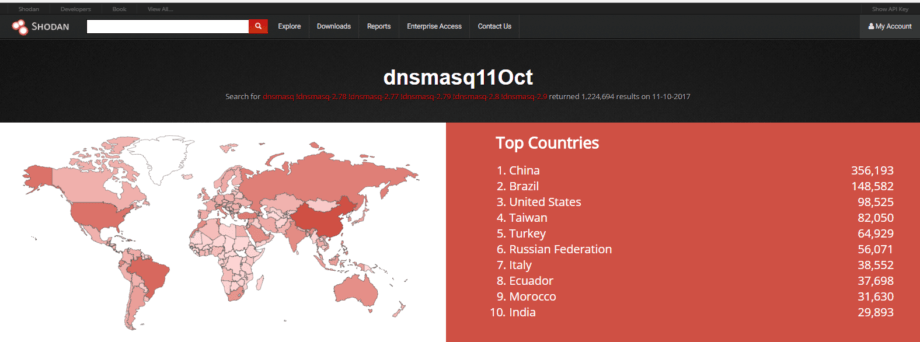
As of October 11th, there are total of 1,178,031 devices running vulnerable version of dnsmasq and that is if you do not consider version 2.76 vulnerable or likely targetable by a mass-scale attack. I’ve previously reported the numbers on patching on October 6th and the amount of vulnerable devices was 1,131,229, so the amount of unpatched devices discovered by Shodan keeps going up!
Maybe Google Security’s warning has fallen on deaf ears? It may seem like it has, however if we take into account long patch-management cycles in the enterprise (do they exist for IoT at all?) and massive number of Android devices that are out of support the situation seems reasonable. Is the impact global? You may find answers in this report from Shodan:
So why do we mention Mirai? It was an infamous botnet built of scanning and making a bot army of insecure IoT devices leveraging clear-text protocols like telnet and hardcoded credentials. An adeversary with such capabilities will have little trouble of upgrading from a Brute Force attack to an RCE with publicly available exploit code. However, if nothing happens by October 27 it would mean that dnsmasq will be leveraged by APT actors who would make sure to secure their positions by establishing persistence (see ways to do it at MITRE ATT&CK) and operate in stealth. If we see a sudden spike in dnsmasq being patched I’d spell APT all over the place. It is a lucrative way in (and out) for the APT actors as DNS traffic still remains insecure and uncontrolled in majority of organizations and can be easily exploited for Command & Control, Delivery and Data Exfiltration. Come whatever may, just block those assets to be on the safe side and deploy some detection controls as there are many other wonderful things to do in cyber security. And if you’re a proud owner of a dnsmasq device as part of your IoT project at work or as your home router – upgrade that firmware today!
/Stay safe
p.s. we just finished cross-checking all 1,17K+ devices vs our Tor feed and got just 1 hit. We started checking IP’s vs IPVoid and VirusTotal and already have some IP’s confirmed as malicious. Updates are coming up.
SIEM content