Detecting Abused Legitimate Tools Applied by Hackers in the Human-Operated Ransomware Attacks

Table of contents:
With the constantly changing cyber threat landscape and the increasing sophistication of the adversary toolkit, information exchange between cybersecurity experts is of paramount value.
On January 25 and 26, 2023, the global cyber defender community welcomed the sixth JSAC2023 conference for security analysts aimed to boost their expertise in the field. This annual cybersecurity event brings engineers together in a single place to foster prolific knowledge sharing focused on incident analysis and response.
On the Conference Day 1, Toru Yamashige, Yoshihiro Nakatani, and Keisuke Tanaka, representing the Japanese cybersecurity software company, Trend Micro, talked about commercially developed and distributed tools for general IT operations exploited by human-operated ransomware. In this presentation, the Trend Micro team covered actual use cases, shed some light on what’s behind the abused legit tools and shared tips on how to prevent cyber attacks leveraging this toolkit.
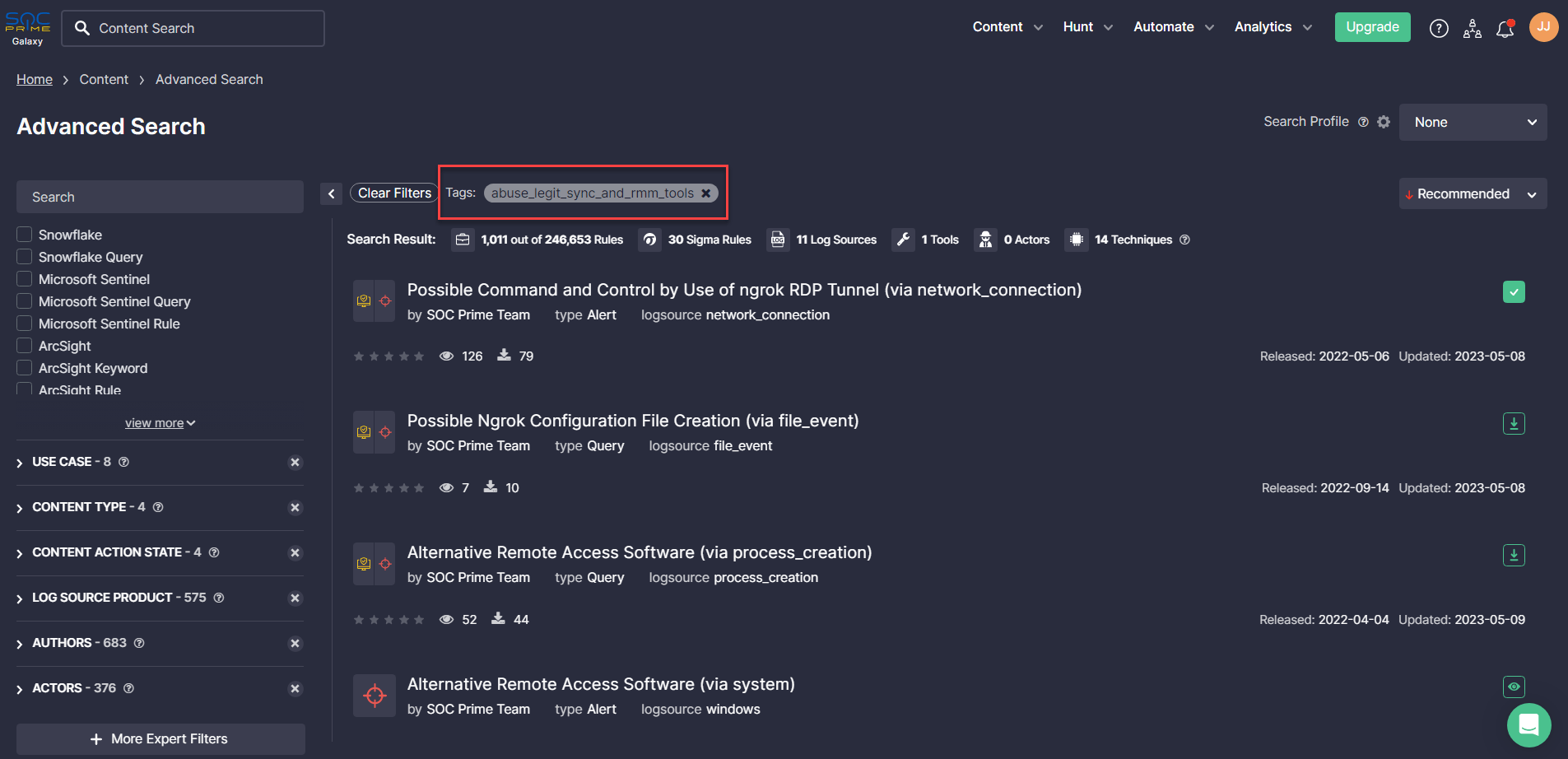
Sigma Rules to Detect Attacks Abusing Legitimate Tools
Adversaries behind human-operated ransomware often exploit legitimate tools as a means of evading defense mechanisms. SOC Prime Team curates a set of relevant Sigma rules to help organizations proactively detect cyber attacks abusing legitimate commercial tools, such as remote management software and backup/synchronization software. For streamlined detection content search, all the rules are filtered by the corresponding tag “abuse_legit_sync_and_rmm_tools”. The detections are aligned with the MITRE ATT&CK framework v12 addressing 14 adversary techniques and can be applied across 28+ SIEM, EDR, and XDR solutions.
Click the Explore Detections button below to reach the above-referenced Sigma rules and be fully equipped against cyber attacks of such kind. Dive into the cyber threat context, including ATT&CK and CTI references, mitigations, and executable binaries to stay always in the know.
Please note that the above-mentioned Sigma rules will be more effective and less likely to generate false positives when applying additional filters already set tailored to the company’s needs. For instance, for the company leveraging TeamViewer, it is necessary to make certain exceptions that may be acceptable for one organization but not relevant to another.
Analyzing Cyber Attacks Abusing Legitimate Tools in Human-Operated Ransomware Campaings
According to Check Point, ransomware operators have largely switched to human-operated ransomware due to its greater control and profitability. Human-operated ransomware is planted and executed on a targeted system by an attacker who gains access to the environment and deploys the ransomware at the chosen location for the greater impact. Therefore, human-operated ransomware attacks can be more impactful and targeted.
One of the examples of the human-operated ransomware can be Ransom X, which opens a console after the execution that displays information to adversaries while it is running and which is capable of disabling remote access tools, security software, databases, and mail servers to give attackers the green light to further compromise data on the targeted systems and spread the infection further.
On January 25, cybersecurity experts from Trend Micro shared their insights about cyber attacks abusing legitimate commercial tools and how to defend againt such intrusions during the annual JSAC2023 conference for security analysts held in Japan.
On March 13, 2023, JPCERT/CC issued an overview of presentations held at JSAC2023 from the first day of the event, including the highlights from the report by Trend Micro. The speakers shared examples of actual exploitation of legitimate remote management tools, like Atera, Remote Utilities, Ngrok, or AnyDesk, along with cloud-based file-sharing utilities similar to RCLONE and MEGA TOOLS that can be abused in human-operated ransomware campaigns.
According to Trend Micro, the most effective countermeasures against cyber attacks leveraging such a toolkit can be controlling the communication destination, as well as thoroughly monitoring and visualizing the application installation and execution.
Throughout 2021-2023, ransomware continues to be one of the dominant trends in the cyber threat landscape, illustrated by the increasing sophistication of intrusions and a rapidly growing number of ransomware affiliates. Therefore, proactive detection is key to strengthening the organization’s cybersecurity posture. Obtain 650+ Sigma rules to identify current and emerging ransomware attacks and always stay one step ahead of adversaries. Reach 30+ rules for free or gain the entire detection stack with On Demand at http://my.socprime.com/pricing.