Defenders shed light on a set of vulnerabilities in Ivanti Cloud Service Appliances (CSA) that can be chained for further exploitation. The latest joint alert by CISA and FBI notifies the global defender community of at least two exploit chains using Invanti vulnerabilities tracked as CVE-2024-8963, CVE-2024-9379, CVE-2024-8190, and CVE-2024-9380. Adversaries can take advantage of exploit chains weaponizing the flas to achieve initial access, execute RCE, steal credentials, and deploy malware on targeted networks.
Detect CVE-2024-8963, CVE-2024-9379, CVE-2024-8190, and CVE-2024-9380 Exploit Chains
Ivanti Cloud Service Appliances (CSA) vulnerabilities represent a significant risk to enterprise security due to the crucial role these systems play in managing secure remote access and authentication. Commonly deployed as internet-facing systems, Ivanti CSAs are particularly attractive to attackers seeking to exploit weaknesses for unauthorized access to sensitive enterprise networks.
The latest exploit chains weaponizing CVE-2024-8963, CVE-2024-9379, CVE-2024-8190, and CVE-2024-9380 vulnerabilities are actively being used in the wild. These exploits enable attackers to execute various malicious actions taking control of enterprise systems. To address this growing threat, immediate action is essential for cyber defenders.
The SOC Prime Platform for collective cyber defense provides curated detection rules addressing exploitation attempts of the latest Ivanti CSA vulnerabilities. Backed by a complete toolkit for threat research and detection engineering, the platform empowers organizations to proactively defend against emerging threats. Just hit the Explore Detections button below and immediately access a relevant detection stack covering exploitation attempts described in the AA25-022A advisory.
All the rules are mapped to the MITRE ATT&CK® framework and compatible with 40+ SIEM, EDR, and Data Lake solutions. Each rule is enriched with extensive CTI, including media references, attack timelines, audit configurations, and other metadata.
Security experts seeking more detection content matching the proactive vulnerability exploitation detection use case can access the whole collection of Sigma rules by browsing the Threat Detection Marketplace via the CVE tag. Additionally, cyber defenders might always stay on top of the latest threats with our main Active Threats dashboard – now available for free with Personal Access to SOC Prime Platform.
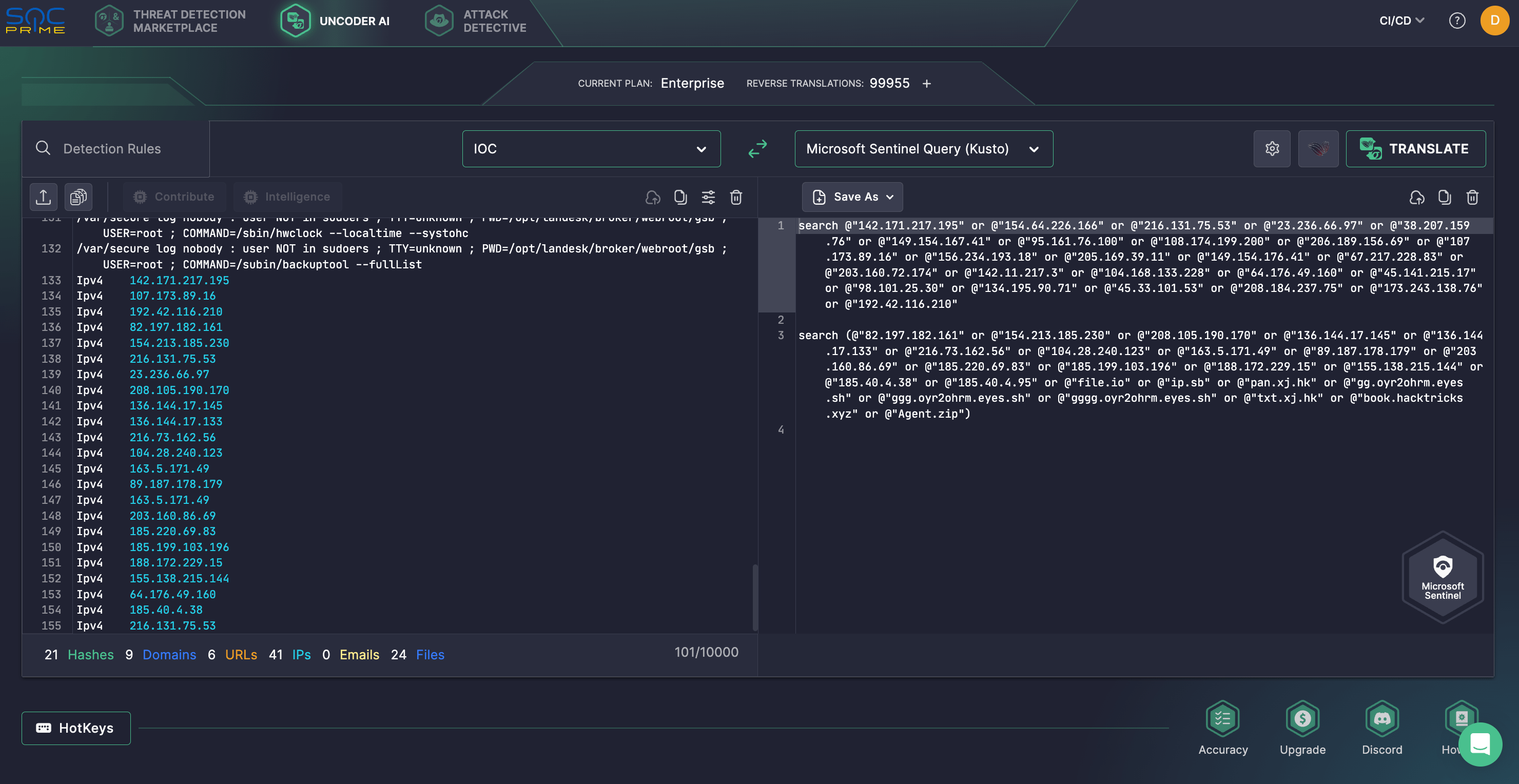
Also, to simplify threat research, security experts can seamlessly hunt for IOCs provided in the AA25-022A advisory by CISA. Rely on SOC Prime’s Uncoder AI to create custom IOC-based queries in a matter of seconds and automatically work with them in your chosen SIEM or EDR environment. Previously available only to corporate clients, Uncoder AI is now accessible to individual researchers, offering its full capabilities. Check out the details here.
Critical Ivanti CSA Vulnerabilities Analysis
On January 22, 2025, CISA and FBI issued a joint cybersecurity alert AA25-022A following the exploitation of critical Ivanti CSA vulnerabilities, including CVE-2024-8963, an administrative bypass flaw, CVE-2024-9379, an SQL injection vulnerability, along with RCE flaws tracked as CVE-2024-8190 and CVE-2024-9380.
Adversaries weaponized the above-mentioned vulnerabilities in exploit chains for initial access, RCE, credential theft, and further webshell deployment on compromised networks. The attackers primarily used two vulnerability exploit chains: one combining CVE-2024-8963 with CVE-2024-8190 and CVE-2024-9380, and another linking CVE-2024-8963 with CVE-2024-9379. In one confirmed incident, the attackers laterally moved to two additional servers.
In September 2024, the vendor issued two security advisories revealing the exploitation of CVE-2024-8190 and CVE-2024-8963. In October 2024, Ivanti followed up with another advisory about the exploitation of CVE-2024-9379, CVE-2024-9380, and CVE-2024-9381.
According to the vendor advisories, all four security issues impact Ivanti CSA version 4.6x prior to build 519, while CVE-2024-9379 and CVE-2024-9380 also affect CSA versions 5.0.1 and earlier. According to Ivanti, these vulnerabilities have not been exploited in version 5.0.
Cybersecurity reports indicate that these vulnerabilities were exploited as zero days. Due to evidence of active exploitation, CISA included them in its Known Exploited Vulnerabilities (KEV) Catalog.
In the first exploit chain, hackers weaponized CVE-2024-8963 along with RCE security flaws CVE-2024-8190 and CVE-2024-9380. They initially sent a GET request to acquire session and CSRF tokens, followed by a POST request to manipulate the setSystemTimeZone function and execute code. In some cases, they used base64-encoded Python scripts to steal encrypted admin credentials. After obtaining credentials, adversaries logged in and used CVE-2024-9380 to execute commands with elevated privileges. They implanted webshells for persistence and, in some cases, created a reverse TCP C2 channel. In another incident, they maintained access by disabling the DateTimeTab.php vulnerability, removing webshells, and clearing traces of exploitation using sudo commands.
In the second exploit chain, adversaries took advantage of CVE-2024-8963 and CVE-2024-9379 to gain initial access via a specific GET request. Once inside the targeted network, they attempted to exploit CVE-2024-9379 to create a web shell by sending GET and POST requests with an SQL injection in the lockout attempts input. The injection gave attackers the green light to insert a user into the user_info table, with bash code embedded in the entry. Though the login attempt failed, the application mistakenly processed the bash code, allowing the adversaries to use echo commands to build a webshell. However, there is no indication that they succeeded in creating a functional one.
Since Ivanti CSA version 4.6 is considered end-of-life and no longer receives patches, which makes it highly prone to cyber-attacks, organizations require ultra-responsiveness to timely defend against intrusions. To reduce the risks of Ivanti CSA vulnerability exploitation, network administrators are strongly advised to upgrade to the latest supported version of Ivanti CSA. Organizations are recommended to gather and analyze logs and artifacts for any signs of malicious activity and follow the incident response guidance outlined in the CISA & FBI advisory. To elevate defenses at scale and implement a proactive cybersecurity strategy, SOC Prime Platform offers a complete product suite for advanced threat detection, automated threat hunting, and intelligence-driven detection engineering as a highly feasible and innovative solution against ever-increasing vulnerability exploitation attempts.




