Update: This article has been updated to reflect ESET research insights from August 11, 2025, covering the emerging attack flow details.
As summer reaches its peak, the cyber threat landscape is heating up just as fast. Following the recent disclosure of CVE-2025-8292, a use-after-free vulnerability in Chrome’s Media Stream, security researchers have uncovered active exploitation of a novel WinRAR zero-day to deliver RomCom malware.
Tracked as CVE-2025-8088, this path traversal flaw in the Windows version of WinRAR allows attackers to execute arbitrary code by crafting malicious archive files. While the exact methods and threat actors behind the campaign remain unknown, the use of RomCom backdoor suggests potential involvement of the hacking groups of russian origin.
Detect CVE-2025-8088 Exploitation Attempts for RomCom Delivery
With over 29,000 new vulnerabilities logged by NIST this year, the race is on for cybersecurity teams. While vulnerability exploitation remains the leading attack vector, and as cyber threats grow more sophisticated, proactive detection is essential to reducing the attack surface and mitigating risk.
Register now for the SOC Prime Platform to access an extensive library of context-enriched detection rules and AI-driven threat intelligence, helping you stay one step ahead of attacks leveraging emerging vulnerabilities. The platform features curated detections addressing the latest WinRAR zero-day exploitation for RomCom delivery, backed by a complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection. Click the Explore Detections button below to dive into the relevant detection stack.
Cyber defenders might also browse the Threat Detection Marketplace using “RomCom” for more tailored content. To explore a wider set of detection rules related to vulnerability exploitation, simply apply the “CVE” tag to view the whole collection.
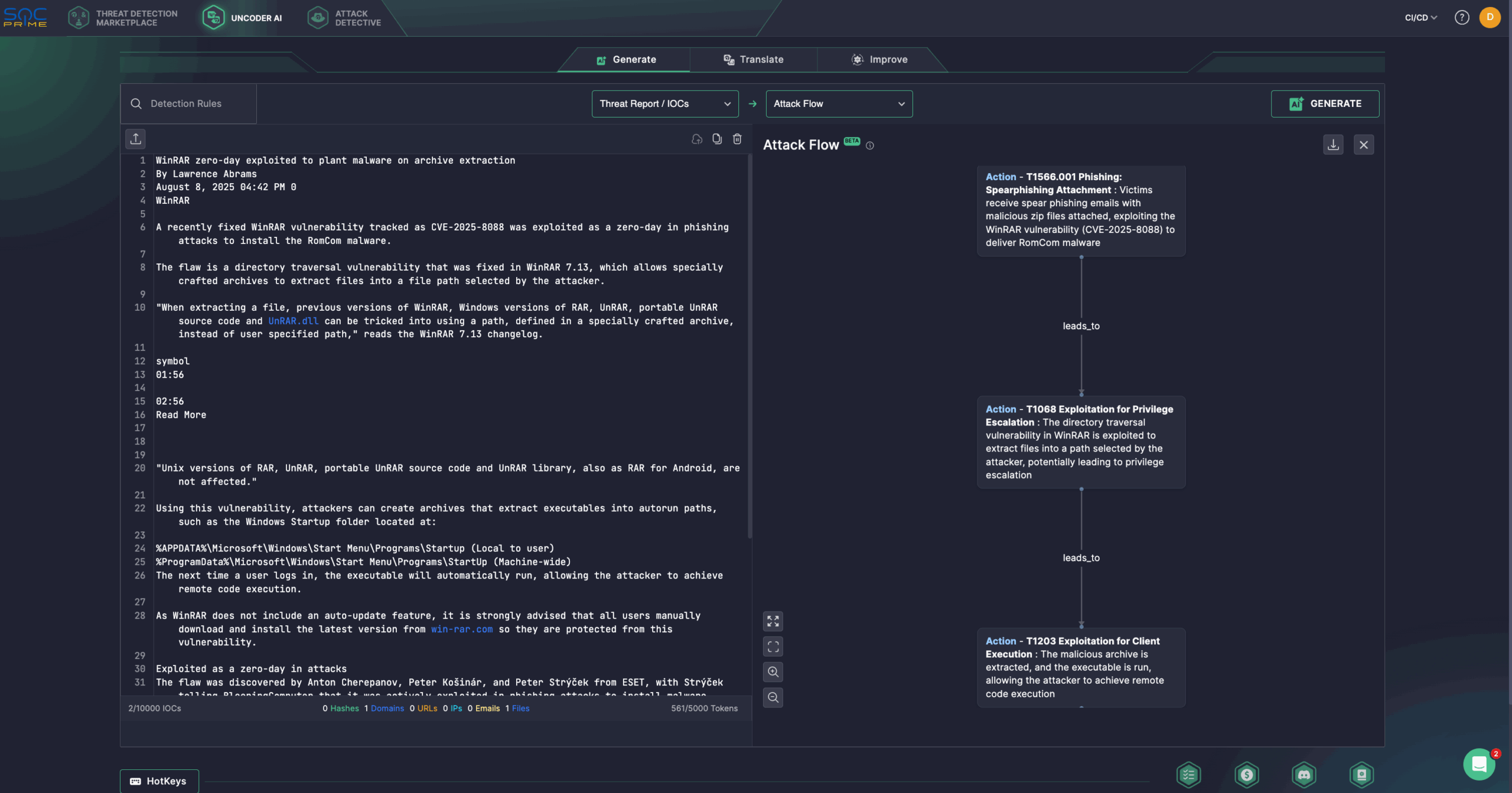
Additionally, security experts might streamline threat investigation using Uncoder AI, a private IDE & co-pilot for threat-informed detection engineering. Generate detection algorithms from raw threat reports, enable fast IOC sweeps, predict ATT&CK tags, optimize query code with AI tips, and translate it across multiple SIEM, EDR, and Data Lake languages. For instance, security professionals can use the latest Bleeping Computer article on CVE-2025-8088 to generate an Attack Flow diagram in a few clicks. Alternatively, security engineers can rely on Uncoder AI to convert IOCs from the ESET GitHub repo into custom IOC queries ready to run in the chosen SIEM or EDR environment to instantly hunt for RomCom-related threats.
CVE-2025-8088 Analysis
Security researchers have uncovered that the WinRAR vulnerability, tracked as CVE-2025-8088, was actively exploited as a zero-day in targeted phishing campaigns to spread RomCom malware. This path traversal flaw affects the Windows version of WinRAR and allows attackers to execute arbitrary code by crafting malicious archive files.
According to the advisory, earlier versions of WinRAR (including Windows RAR, UnRAR, the portable UnRAR source code, and UnRAR.dll) could be tricked during file extraction into using a maliciously crafted path instead of the intended one. This allows attackers to place files in unauthorized locations.
Specifically, threat actors can create archive files that extract malicious executables into autorun folders, such as user-specific %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup or machine-wide %ProgramData%\Microsoft\Windows\Start Menu\Programs\StartUp. This enables the malware to run automatically the next time the user logs in, enabling attackers to achieve remote code execution for RomCom backdoor installation.
Notably, Unix versions of RAR, UnRAR, the portable UnRAR source code, UnRAR library, and RAR for Android are not affected by this flaw.
The RomCom malware family is linked to a russian-origin hacking collective, known by several aliases, including UAT-5647, Storm-0978, Tropical Scorpius, UAC-0180, and UNC2596. This group is also believed to be behind the infamous Cuba ransomware operations. Known for advanced hacking techniques, they have been active since at least 2019 and are notorious for deploying various malware families, including RomCom RAT and SystemBC. In 2022, threat actors used RomCom backdoor to target Ukrainian state bodies, indicating their possible ties to cyber espionage operations in favor of the Moscow government.
The vulnerability was discovered by ESET researchers Anton Cherepanov, Peter Košinár, and Peter Strýček, who reported it to the vendor. The latest ESET report has identified three separate attack chains delivering known RomCom malware iterations: Mythic Agent, SnipBot, and MeltingClaw. Mythic Agent execution chain is triggered via Updater.lnk, which adds msedge.dll to a COM hijack registry location. This DLL decrypts AES shellcode and executes only if the system’s domain matches a hardcoded value, launching the Mythic agent for C2 communications, command execution, and payload delivery.
Another infection chain causing the SnipBot malware variant distribution is triggered by launching via Display Settings.lnk, which runs ApbxHelper.exe (a tampered PuTTY CAC build with an invalid certificate). It checks for at least 69 recently opened documents before decrypting shellcode that retrieves more payloads from attacker-controlled servers.
The third execution flaw linked to the delivery of MeltingClaw malware is initiated by Settings.lnk, which further runs Complaint.exe (RustyClaw). This downloads a MeltingClaw DLL that pulls and runs additional malicious modules from the adversary’s infrastructure.
The issue was addressed in WinRAR version 7.13, released on July 30, 2025, so users are urged to promptly upgrade to the safe version. Also, to stay ahead of attackers and proactively detect potential vulnerability exploitation attempts, security teams can rely on SOC Prime’s complete product suite backed by AI, automation capabilities, and real-time threat intel, while strengthening the organization’s defenses at scale.




